OpenID Protocol Explained
•
1 like•9,239 views
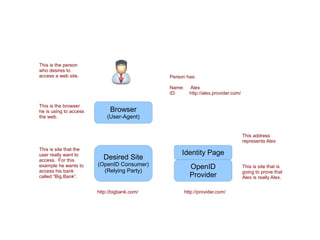
This document outlines the OpenID authentication process. It shows how a user named Alex, with the OpenID http://alex.provider.com/, is able to log into their bank account at Big Bank by authenticating once with their OpenID provider. The OpenID provider verifies Alex's identity and sends authentication responses to Big Bank, allowing Alex to access the bank's site without needing to log in a second time.
Report
Share
Report
Share
Download to read offline
Recommended
Webinar: OpenAM 12.0 - New Featurs

OpenAM product manager Andy Hall covers some of the major new components in OpenAM 12.0, such as the Scripting Engine, Policy Editor, XUI user interface framework, and Secure Token transformation service.
The webinar can be watched here: http://go.forgerock.com/webinar-openam-12.html
PEHRS Presentation on ACM

This presentation given to the Professional Exchange of HR Solutions in September 2012 covers the basics of ACM and the management shift we are seeing around us today.
AssureBridge - SSO to Many B2B Service Providers - Marketing presentation

A popular growth strategy for many companies is to broaden their online offerings by making other B2B providers' services accessible to their customer on their Web Sites. To make the customer online experience pleasant and secure, these companies are required to implement complex Internet Single Sign-On (SSO) integration with many B2B partners. AssureBridge solutions help to deliver these integrations quickly, painlessly, and efficiently.
CIS 2015 SSO for Mobile and Web Apps Ashish Jain

In the past Enterprise Mobility Management (EMM) has focused primarily on MDM, MAM and MCM. Recently there has been a lot of focus on the fourth pillar of EMM - Mobile Identity Management (MIM). This session will cover the primary use cases and discuss current solutions available for managed/un-managed, internal/public and mobile/web apps for iOS/Android devices.
Engineering Cryptographic Applications: Symmetric Encryption

First class of four-part series developed for introducing engineers to cryptography.
Delivered at AMC Theater in Tyson's Corner for Microstrategy, 4 October 2013.
A CONTEMPLATION OF OPENIG DEEP THOUGHTS

LUDOVIC POITOU, Director of ForgeRock France & OpenIG Product Manager, at the European IRM Summit 2014.
OpenIG Webinar: Your Swiss Army Knife for Protecting and Securing Web Apps, A...

Description:
This webinar will explore how to improve security by enforcing identity, ensuring the requests are correctly authorized to access the resources it’s requesting. How to leverage standards based identity, such as OAuth2, SAML or OpenID Connect or even social login, to make it easier for users, devices, things and API’s to interact with your digital services while improving security.
Webinar Highlights:
Overview of OpenIG
Demo on the power of OpenIG’s gateway integration capabilities
Demo of upcoming features in OpenIG 4.0, including throttling
Q&A
Join ForgeRock’s Product Manager of OpenDJ and OpenIG, Ludovic Poitou and Senior Product Marketing Manager, Justin Pirie, to discuss OpenIG.
Recommended
Webinar: OpenAM 12.0 - New Featurs

OpenAM product manager Andy Hall covers some of the major new components in OpenAM 12.0, such as the Scripting Engine, Policy Editor, XUI user interface framework, and Secure Token transformation service.
The webinar can be watched here: http://go.forgerock.com/webinar-openam-12.html
PEHRS Presentation on ACM

This presentation given to the Professional Exchange of HR Solutions in September 2012 covers the basics of ACM and the management shift we are seeing around us today.
AssureBridge - SSO to Many B2B Service Providers - Marketing presentation

A popular growth strategy for many companies is to broaden their online offerings by making other B2B providers' services accessible to their customer on their Web Sites. To make the customer online experience pleasant and secure, these companies are required to implement complex Internet Single Sign-On (SSO) integration with many B2B partners. AssureBridge solutions help to deliver these integrations quickly, painlessly, and efficiently.
CIS 2015 SSO for Mobile and Web Apps Ashish Jain

In the past Enterprise Mobility Management (EMM) has focused primarily on MDM, MAM and MCM. Recently there has been a lot of focus on the fourth pillar of EMM - Mobile Identity Management (MIM). This session will cover the primary use cases and discuss current solutions available for managed/un-managed, internal/public and mobile/web apps for iOS/Android devices.
Engineering Cryptographic Applications: Symmetric Encryption

First class of four-part series developed for introducing engineers to cryptography.
Delivered at AMC Theater in Tyson's Corner for Microstrategy, 4 October 2013.
A CONTEMPLATION OF OPENIG DEEP THOUGHTS

LUDOVIC POITOU, Director of ForgeRock France & OpenIG Product Manager, at the European IRM Summit 2014.
OpenIG Webinar: Your Swiss Army Knife for Protecting and Securing Web Apps, A...

Description:
This webinar will explore how to improve security by enforcing identity, ensuring the requests are correctly authorized to access the resources it’s requesting. How to leverage standards based identity, such as OAuth2, SAML or OpenID Connect or even social login, to make it easier for users, devices, things and API’s to interact with your digital services while improving security.
Webinar Highlights:
Overview of OpenIG
Demo on the power of OpenIG’s gateway integration capabilities
Demo of upcoming features in OpenIG 4.0, including throttling
Q&A
Join ForgeRock’s Product Manager of OpenDJ and OpenIG, Ludovic Poitou and Senior Product Marketing Manager, Justin Pirie, to discuss OpenIG.
Securing Access Through a Multi-Purpose Credential and Digital ID

Breakout Session at the 2014 IRM Summit in Phoenix, Arizona by Stephan Papadopulos, Managing Director at the Triage Group.
Information Security Lesson 9 - Keys - Eric Vanderburg

Information Security Lesson 9 - Keys - Eric Vanderburg
Cryptography and PKI

- Cryptography and Security
- Methods of Encryption and Decryption
- What is an Algorithm?
- Symmetric Algorithm
- Asymmetric Algorithm
- Hybrid Encryption
- Hashing Algorithm
- Securing the Algorithm or the Key
- Hash Value and Rainbow Table
- Digital Signature
- PKI
OpenDJ - An Introduction

An IAM for Beginners session led by Dr. Matthias Tristl, Senior Instructor, ForgeRock
Learn more about ForgeRock Access Management:
https://www.forgerock.com/platform/access-management/
Learn more about ForgeRock Identity Management:
https://www.forgerock.com/platform/identity-management/
OAuth for your API - The Big Picture

OAuth is taking off as a standard way for apps and websites to handle authentication. But OAuth is a fast moving spec that can be hard to pin down.
Why should you use OAuth and what are the business and operational benefits? What's the story with all of the different versions and which one should you choose?
Watch this webinar with Apigee's CTO Gregory Brail and Sr. Architect Brian Pagano for 'big picture straight talk' on these OAuth questions and more.
Opendj - A LDAP Server for dummies

My presentation at H2HC 2014
A brief description about OpenDJ, how to install and how it works.
OpenID Connect: An Overview

Brief overview of OpenID Connect - presented at Bay Area Identity Developers Meetup, Dec 2 2013.
Virtual-HSM: Virtualization of Hardware Security Modules in Linux Containers

In the report the technology of virtual security modules will be presented. It rely on Linux containers. The report should be interesting for those people who are planning (or already using) could services for building IT-infrastructure.
Federation in Practice

A Development session led by Technical Enablement Lead Bert Van Beeck
Learn more about ForgeRock Access Management:
https://www.forgerock.com/platform/access-management/
Learn more about ForgeRock Identity Management:
https://www.forgerock.com/platform/identity-management/
OpenID Authentication by example

OpenID is a new way to identify yourself all over the web. With your own personal OpenID you can login to any OpenID-enabled site (there are over 1,000 of them and that number is growing everyday) and identify yourself as you.
This is a short by-example talk about OpenID, what it does and can provide for your website. The talk includes a sample implementation in perl.
(talk given at Belgian Perl Workshop, 27 November 2007)
Identity Gateway with the ForgeRock Identity Platform - So What’s New?

Identity Gateway with the ForgeRock Identity Platform - So What’s New?
Devices, and Things: Better Than a Fish in Your Ear
In the Hitchhiker’s Guide to the Galaxy they have a handy little thing called a Babel Fish. Put it in your ear and you can instantly communicate with anything, anywhere in the galaxy. It’s quick and painless and works great. And that’s exactly how the ForgeRock Identity Gateway works too. It’s a simple, standards-based approach to extend access to web applications, application programming interfaces (APIs), and devices and things. The ForgeRock Identity Gateway, provides a flexible policy enforcement point to support your current environment while migrating towards a modern, standards-based platform. So you can connect digital assets across your ecosystem, with minimal-to-no changes. And no slimy little fish required!
Highlights:
- Intro to the ForgeRock Identity Platform
- New features available in this release
- Maintaining existing infrastructure through password replay
- Gateway and a Mobile device walk into a bar….
- Federating services
- Mobilizing those apps
Learn more about ForgeRock Access Management:
https://www.forgerock.com/platform/access-management/
Learn more about ForgeRock Identity Management:
https://www.forgerock.com/platform/identity-management/
SAML and Other Types of Federation for Your Enterprise

SAML and Other Types of Federation for Your Enterprise, session from BriForum London 2014
SAML Protocol Overview

Because the SAML Protocol is so foundational to the cloud identity software as a service Gluu provides, we wanted to lay out the basics of SAML for those interested.
The following can be thought of as a basic guide to getting you conversational with the SAML protocol.
Finding documents in Cognoscenti

This describes the mechanisms to easily find and organize documents in a Cognoscenti workspace.
mcetech2015

Robots Don't Innovate: Innovation vs. Automation in BPM. Ideas from the book: "When Thinking Matters in the Workplace"
mri-bp2015

Keynote presentation for
Workshop on Methodologies for Robustness Injectioninto Business Processes, May 2015
More Related Content
Viewers also liked
Securing Access Through a Multi-Purpose Credential and Digital ID

Breakout Session at the 2014 IRM Summit in Phoenix, Arizona by Stephan Papadopulos, Managing Director at the Triage Group.
Information Security Lesson 9 - Keys - Eric Vanderburg

Information Security Lesson 9 - Keys - Eric Vanderburg
Cryptography and PKI

- Cryptography and Security
- Methods of Encryption and Decryption
- What is an Algorithm?
- Symmetric Algorithm
- Asymmetric Algorithm
- Hybrid Encryption
- Hashing Algorithm
- Securing the Algorithm or the Key
- Hash Value and Rainbow Table
- Digital Signature
- PKI
OpenDJ - An Introduction

An IAM for Beginners session led by Dr. Matthias Tristl, Senior Instructor, ForgeRock
Learn more about ForgeRock Access Management:
https://www.forgerock.com/platform/access-management/
Learn more about ForgeRock Identity Management:
https://www.forgerock.com/platform/identity-management/
OAuth for your API - The Big Picture

OAuth is taking off as a standard way for apps and websites to handle authentication. But OAuth is a fast moving spec that can be hard to pin down.
Why should you use OAuth and what are the business and operational benefits? What's the story with all of the different versions and which one should you choose?
Watch this webinar with Apigee's CTO Gregory Brail and Sr. Architect Brian Pagano for 'big picture straight talk' on these OAuth questions and more.
Opendj - A LDAP Server for dummies

My presentation at H2HC 2014
A brief description about OpenDJ, how to install and how it works.
OpenID Connect: An Overview

Brief overview of OpenID Connect - presented at Bay Area Identity Developers Meetup, Dec 2 2013.
Virtual-HSM: Virtualization of Hardware Security Modules in Linux Containers

In the report the technology of virtual security modules will be presented. It rely on Linux containers. The report should be interesting for those people who are planning (or already using) could services for building IT-infrastructure.
Federation in Practice

A Development session led by Technical Enablement Lead Bert Van Beeck
Learn more about ForgeRock Access Management:
https://www.forgerock.com/platform/access-management/
Learn more about ForgeRock Identity Management:
https://www.forgerock.com/platform/identity-management/
OpenID Authentication by example

OpenID is a new way to identify yourself all over the web. With your own personal OpenID you can login to any OpenID-enabled site (there are over 1,000 of them and that number is growing everyday) and identify yourself as you.
This is a short by-example talk about OpenID, what it does and can provide for your website. The talk includes a sample implementation in perl.
(talk given at Belgian Perl Workshop, 27 November 2007)
Identity Gateway with the ForgeRock Identity Platform - So What’s New?

Identity Gateway with the ForgeRock Identity Platform - So What’s New?
Devices, and Things: Better Than a Fish in Your Ear
In the Hitchhiker’s Guide to the Galaxy they have a handy little thing called a Babel Fish. Put it in your ear and you can instantly communicate with anything, anywhere in the galaxy. It’s quick and painless and works great. And that’s exactly how the ForgeRock Identity Gateway works too. It’s a simple, standards-based approach to extend access to web applications, application programming interfaces (APIs), and devices and things. The ForgeRock Identity Gateway, provides a flexible policy enforcement point to support your current environment while migrating towards a modern, standards-based platform. So you can connect digital assets across your ecosystem, with minimal-to-no changes. And no slimy little fish required!
Highlights:
- Intro to the ForgeRock Identity Platform
- New features available in this release
- Maintaining existing infrastructure through password replay
- Gateway and a Mobile device walk into a bar….
- Federating services
- Mobilizing those apps
Learn more about ForgeRock Access Management:
https://www.forgerock.com/platform/access-management/
Learn more about ForgeRock Identity Management:
https://www.forgerock.com/platform/identity-management/
SAML and Other Types of Federation for Your Enterprise

SAML and Other Types of Federation for Your Enterprise, session from BriForum London 2014
SAML Protocol Overview

Because the SAML Protocol is so foundational to the cloud identity software as a service Gluu provides, we wanted to lay out the basics of SAML for those interested.
The following can be thought of as a basic guide to getting you conversational with the SAML protocol.
Viewers also liked (19)
Securing Access Through a Multi-Purpose Credential and Digital ID

Securing Access Through a Multi-Purpose Credential and Digital ID
Information Security Lesson 9 - Keys - Eric Vanderburg

Information Security Lesson 9 - Keys - Eric Vanderburg
Virtual-HSM: Virtualization of Hardware Security Modules in Linux Containers

Virtual-HSM: Virtualization of Hardware Security Modules in Linux Containers
Identity Gateway with the ForgeRock Identity Platform - So What’s New?

Identity Gateway with the ForgeRock Identity Platform - So What’s New?
SAML and Other Types of Federation for Your Enterprise

SAML and Other Types of Federation for Your Enterprise
More from Keith Swenson
Finding documents in Cognoscenti

This describes the mechanisms to easily find and organize documents in a Cognoscenti workspace.
mcetech2015

Robots Don't Innovate: Innovation vs. Automation in BPM. Ideas from the book: "When Thinking Matters in the Workplace"
mri-bp2015

Keynote presentation for
Workshop on Methodologies for Robustness Injectioninto Business Processes, May 2015
Adaptive Case Management Workshop 2014 - Keynote

This is the first talk from the 3rd International Workshop on Adaptive Case Management and Non-Workflow BPM. conference overview at: http://acm2014.blogs.dsv.su.se/
Seven Domains of Predictability - BPMCM 2014

This is an updated version of the seven domains of predictability that define the different types of process technology given at the BPM & Case Management summit in Washington DC Jun e2014
2014 bpm next_slide_share

A presentation on a type of agent, I call a "personal assistant" and a specific vision of how those agents might allow for processes that cross organizations, and for processes that emerge from the interactions of knowledge workers.
New Tools: ACM for Human Resources

This is a discussion of Adaptive Case Management for the Professional Exchange of Human Resources Solutions
Seven Domains of Predictability

Complete descriptions of the seven domains of process technology where different approaches so supporting process are laid out according to how they predictable the underlying business problem is.
Smart Process Apps on Interstage BOP

Smart Process Apps and a description of the capabilities needed to support them in Interstage Business Operations Platform (BOP).
Taming The Unpredictable: Real-World Adaptive Case Management

In this fast-paced and informative session, best-selling authors Nathaniel Palmer and Keith Swenson present findings and highlights from their latest book on adaptive case management, debuting this week at the Business Process Forum. Learn the best ways to make sure your process management initiatives keep pace with the mobile and social workforce of the 21st century. Key takeaways of the session include:
* Why empowering knowledge workers is the management challenge of the 21st century.
* How adaptive case management offers sanity in a Dropbox, App Store, LinkedIn world.
* Why decisions must be made with increasing autonomy in unforeseen, unplanned, and impromptu ways.
* How mobile computing will crush corporate IT, and what you can do about it.
Figures for Mastering the Unpredictable

These are the figures from the book "Mastering the Unpredictable" so that people with the electronic copies can see a higher resolution version of the graphics.
The Nature of Knowledge Work

This talks about knowledge workers, what they look like, what the qualities of knowledge work are, some background in where mass production and scientific management came from, and then ultimately what technology that will support knowledge work will need to look like.
Sap Tech Ed06 Asug Wf

Presentation from Edwin Mukusha about his use of Wf-XML to connect two SAP systems
Large-Scale Federated BPM / Workflow

This presentation introduced the concept of large scale distributed federated business processes or workflow. This is a process architecture where a single process is implemented across many process sites. Thee key standards are introduced that enable this federation to work across different vendor products.
BPM Model Preserving Strategy vs. Model Transforming Strategy

This presentation was given at the 2009 Process.gov conference in Washinton DC on June 19, and covers the concept of how different BPM products differ based on how they handle the process models.
More from Keith Swenson (19)
Taming The Unpredictable: Real-World Adaptive Case Management

Taming The Unpredictable: Real-World Adaptive Case Management
BPM Model Preserving Strategy vs. Model Transforming Strategy

BPM Model Preserving Strategy vs. Model Transforming Strategy
Recently uploaded
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

The choice of an operating system plays a pivotal role in shaping our computing experience. For decades, Microsoft's Windows has dominated the market, offering a familiar and widely adopted platform for personal and professional use. However, as technological advancements continue to push the boundaries of innovation, alternative operating systems have emerged, challenging the status quo and offering users a fresh perspective on computing.
One such alternative that has garnered significant attention and acclaim is Nitrux Linux 3.5.0, a sleek, powerful, and user-friendly Linux distribution that promises to redefine the way we interact with our devices. With its focus on performance, security, and customization, Nitrux Linux presents a compelling case for those seeking to break free from the constraints of proprietary software and embrace the freedom and flexibility of open-source computing.
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Join Maher Hanafi, VP of Engineering at Betterworks, in this new session where he'll share a practical framework to transform Gen AI prototypes into impactful products! He'll delve into the complexities of data collection and management, model selection and optimization, and ensuring security, scalability, and responsible use.
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

Do you want to learn how to model and simulate an electrical network from scratch in under an hour?
Then welcome to this PowSyBl workshop, hosted by Rte, the French Transmission System Operator (TSO)!
During the webinar, you will discover the PowSyBl ecosystem as well as handle and study an electrical network through an interactive Python notebook.
PowSyBl is an open source project hosted by LF Energy, which offers a comprehensive set of features for electrical grid modelling and simulation. Among other advanced features, PowSyBl provides:
- A fully editable and extendable library for grid component modelling;
- Visualization tools to display your network;
- Grid simulation tools, such as power flows, security analyses (with or without remedial actions) and sensitivity analyses;
The framework is mostly written in Java, with a Python binding so that Python developers can access PowSyBl functionalities as well.
What you will learn during the webinar:
- For beginners: discover PowSyBl's functionalities through a quick general presentation and the notebook, without needing any expert coding skills;
- For advanced developers: master the skills to efficiently apply PowSyBl functionalities to your real-world scenarios.
Mind map of terminologies used in context of Generative AI

Mind map of common terms used in context of Generative AI.
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

Neha Bajwa, Vice President of Product Marketing, Neo4j
Join us as we explore breakthrough innovations enabled by interconnected data and AI. Discover firsthand how organizations use relationships in data to uncover contextual insights and solve our most pressing challenges – from optimizing supply chains, detecting fraud, and improving customer experiences to accelerating drug discoveries.
Pushing the limits of ePRTC: 100ns holdover for 100 days

At WSTS 2024, Alon Stern explored the topic of parametric holdover and explained how recent research findings can be implemented in real-world PNT networks to achieve 100 nanoseconds of accuracy for up to 100 days.
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

Maruthi Prithivirajan, Head of ASEAN & IN Solution Architecture, Neo4j
Get an inside look at the latest Neo4j innovations that enable relationship-driven intelligence at scale. Learn more about the newest cloud integrations and product enhancements that make Neo4j an essential choice for developers building apps with interconnected data and generative AI.
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

As the digital landscape continually evolves, operating systems play a critical role in shaping user experiences and productivity. The launch of Nitrux Linux 3.5.0 marks a significant milestone, offering a robust alternative to traditional systems such as Windows 11. This article delves into the essence of Nitrux Linux 3.5.0, exploring its unique features, advantages, and how it stands as a compelling choice for both casual users and tech enthusiasts.
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

In this session I delve into the encryption technology used in Microsoft 365 and Microsoft Purview. Including the concepts of Customer Key and Double Key Encryption.
The Art of the Pitch: WordPress Relationships and Sales

Clients don’t know what they don’t know. What web solutions are right for them? How does WordPress come into the picture? How do you make sure you understand scope and timeline? What do you do if sometime changes?
All these questions and more will be explored as we talk about matching clients’ needs with what your agency offers without pulling teeth or pulling your hair out. Practical tips, and strategies for successful relationship building that leads to closing the deal.
Removing Uninteresting Bytes in Software Fuzzing

Imagine a world where software fuzzing, the process of mutating bytes in test seeds to uncover hidden and erroneous program behaviors, becomes faster and more effective. A lot depends on the initial seeds, which can significantly dictate the trajectory of a fuzzing campaign, particularly in terms of how long it takes to uncover interesting behaviour in your code. We introduce DIAR, a technique designed to speedup fuzzing campaigns by pinpointing and eliminating those uninteresting bytes in the seeds. Picture this: instead of wasting valuable resources on meaningless mutations in large, bloated seeds, DIAR removes the unnecessary bytes, streamlining the entire process.
In this work, we equipped AFL, a popular fuzzer, with DIAR and examined two critical Linux libraries -- Libxml's xmllint, a tool for parsing xml documents, and Binutil's readelf, an essential debugging and security analysis command-line tool used to display detailed information about ELF (Executable and Linkable Format). Our preliminary results show that AFL+DIAR does not only discover new paths more quickly but also achieves higher coverage overall. This work thus showcases how starting with lean and optimized seeds can lead to faster, more comprehensive fuzzing campaigns -- and DIAR helps you find such seeds.
- These are slides of the talk given at IEEE International Conference on Software Testing Verification and Validation Workshop, ICSTW 2022.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
Recently uploaded (20)
Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...

Why You Should Replace Windows 11 with Nitrux Linux 3.5.0 for enhanced perfor...
Monitoring Java Application Security with JDK Tools and JFR Events

Monitoring Java Application Security with JDK Tools and JFR Events
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
Generative AI Deep Dive: Advancing from Proof of Concept to Production

Generative AI Deep Dive: Advancing from Proof of Concept to Production
Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx

Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx
LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...

LF Energy Webinar: Electrical Grid Modelling and Simulation Through PowSyBl -...
Mind map of terminologies used in context of Generative AI

Mind map of terminologies used in context of Generative AI
FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf

FIDO Alliance Osaka Seminar: The WebAuthn API and Discoverable Credentials.pdf
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024

GraphSummit Singapore | The Art of the Possible with Graph - Q2 2024
Pushing the limits of ePRTC: 100ns holdover for 100 days

Pushing the limits of ePRTC: 100ns holdover for 100 days
GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024

GraphSummit Singapore | Neo4j Product Vision & Roadmap - Q2 2024
Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!

Goodbye Windows 11: Make Way for Nitrux Linux 3.5.0!
Encryption in Microsoft 365 - ExpertsLive Netherlands 2024

Encryption in Microsoft 365 - ExpertsLive Netherlands 2024
The Art of the Pitch: WordPress Relationships and Sales

The Art of the Pitch: WordPress Relationships and Sales
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
OpenID Protocol Explained
- 1. This is the person who desires to access a web site. Person has: Name: ID: This is the browser he is using to access the web. Alex http://alex.provider.com/ Browser (User-Agent) This address represents Alex This is site that the user really want to access. For this example he wants to access his bank called “Big Bank”. Desired Site (OpenID Consumer) (Relying Party) http://bigbank.com/ Identity Page OpenID Provider http://provider.com/ This is site that is going to prove that Alex is really Alex.
- 3. I will log In ONCE UserName: aallen321 Password: ************** LOGIN Browser (User-Agent) http://alex.provider.com/ Identity Page OpenID Provider
- 4. OK! OK, You are logged in to the OpenID service. Browser (User-Agent) http://alex.provider.com/ Identity Page OpenID Provider
- 5. Need to access the bank. Big Bank Enter your OpenID: http://alex.provider.com LOGIN Browser (User-Agent) http://bigbank.com/ Desired Site (OpenID Consumer) (Relying Party) Identity Page OpenID Provider
- 6. I clicked “Login” Headers: openid.server = http://provider.com/a.cgi openid.delegate = http://provider.com/a.cgi Browser (User-Agent) http://bigbank.com/ Desired Site Identity Page (OpenID Consumer) (Relying Party) http://alex.provider.com/
- 7. I am waiting Parameters: openid.mode = checkid_setup openid.identity = http://alex.provider.com/ openid.return_to = http://bigbank.com/... Browser (User-Agent) Send redirect http://provider.com/a.cgi Desired Site (OpenID Consumer) (Relying Party) OpenID Provider
- 8. I am waiting Additional Parameters: openid.mode = id_res openid.identity = http://alex.provider.com/ openid.return_to = http://bigbank.com/... openid.signed = mode,identity,return_to openid.assoc_handle = XXXXX openid.sig = YYYYY Browser (User-Agent) http://bigbank.com/... Send redirect Desired Site (OpenID Consumer) (Relying Party) OpenID Provider
- 9. I am waiting Same parameters as request except openid.mode = check_authentication Response in body: is_valid:true Browser (User-Agent) Desired Site (OpenID Consumer) (Relying Party) OpenID Provider
- 10. OK! Now I can get things done. Big Bank You are logged in! What would you like to do? Browser (User-Agent) Finally … generate page for display Desired Site (OpenID Consumer) (Relying Party) Identity Page OpenID Provider