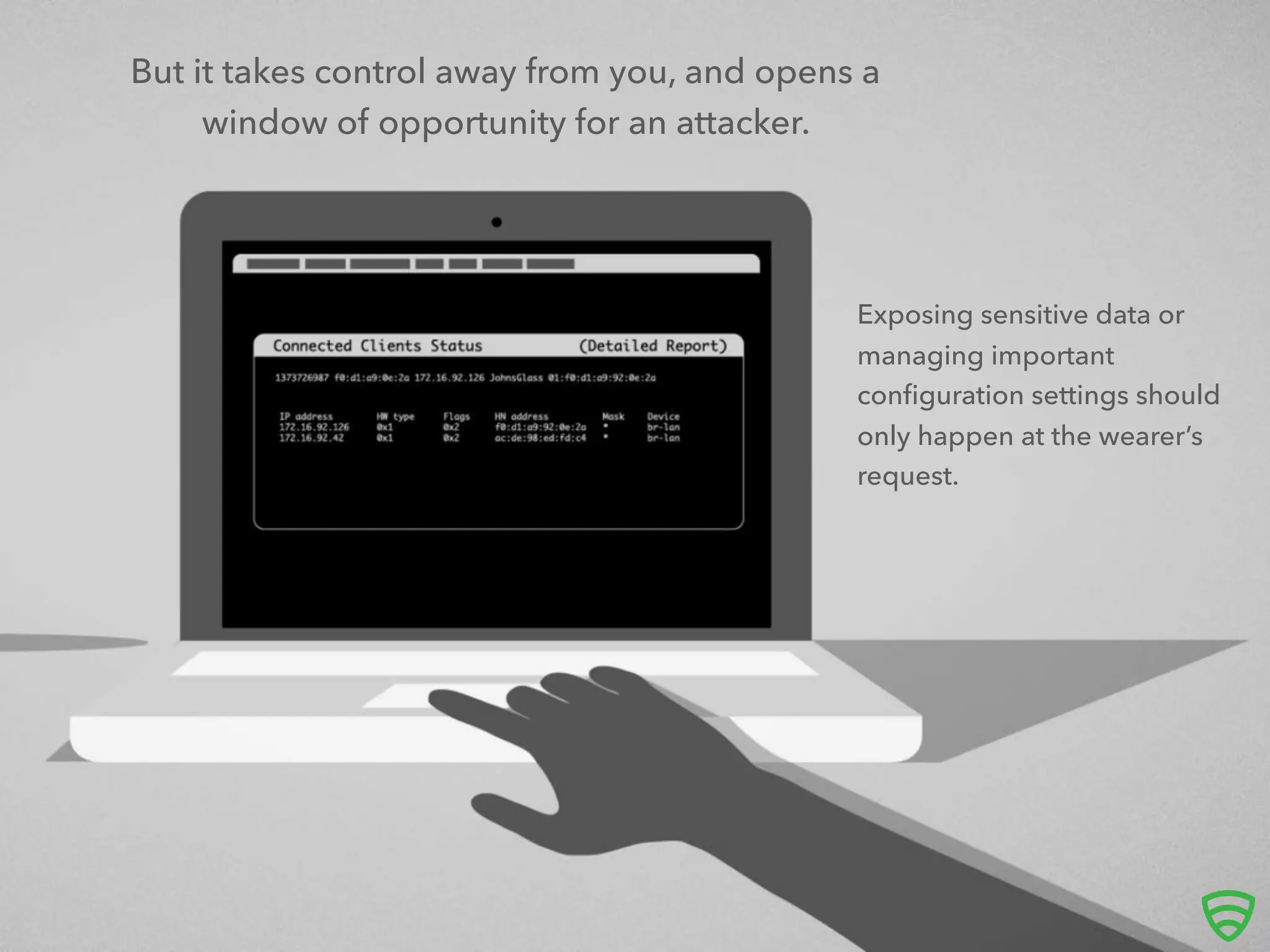
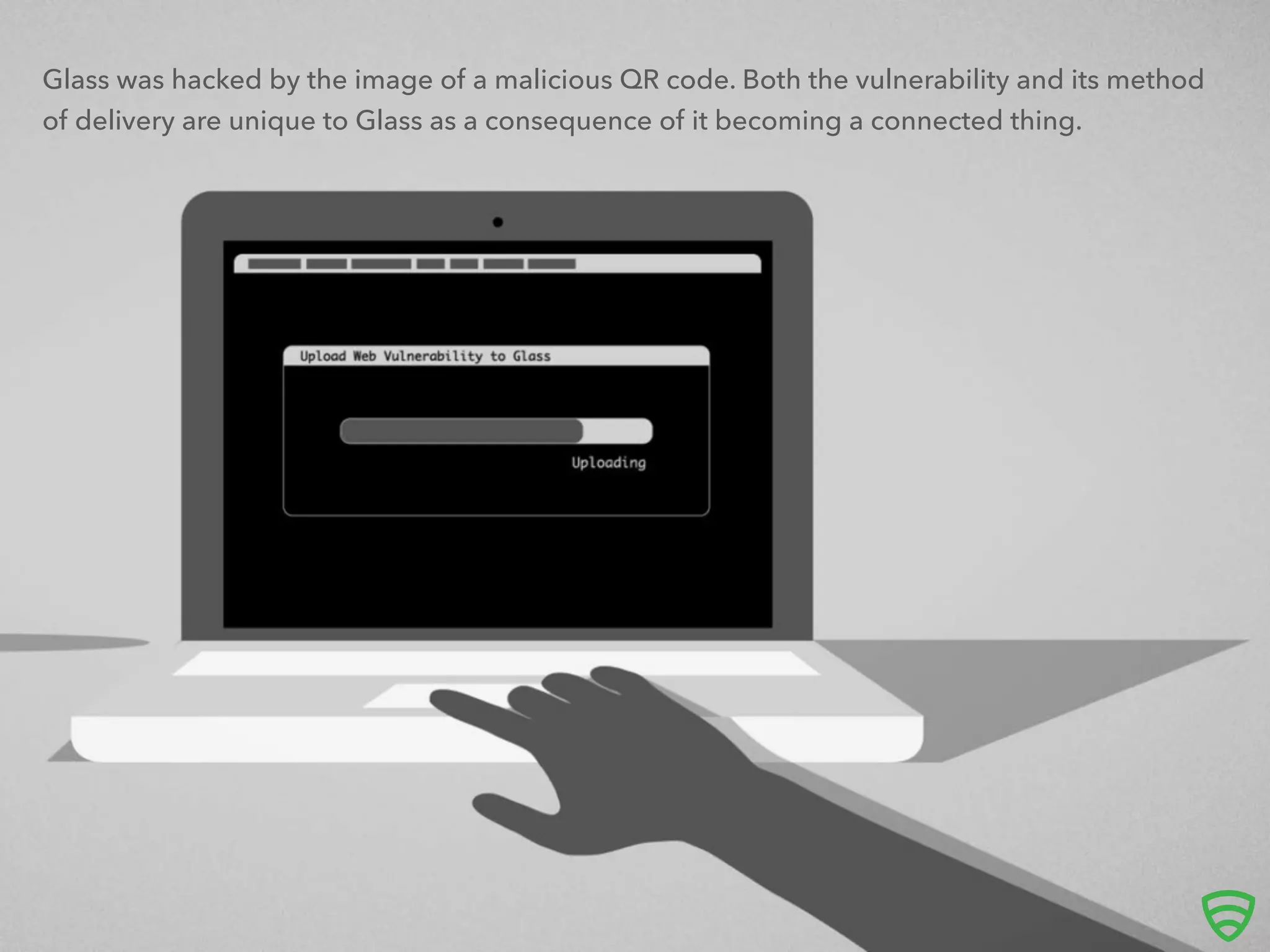
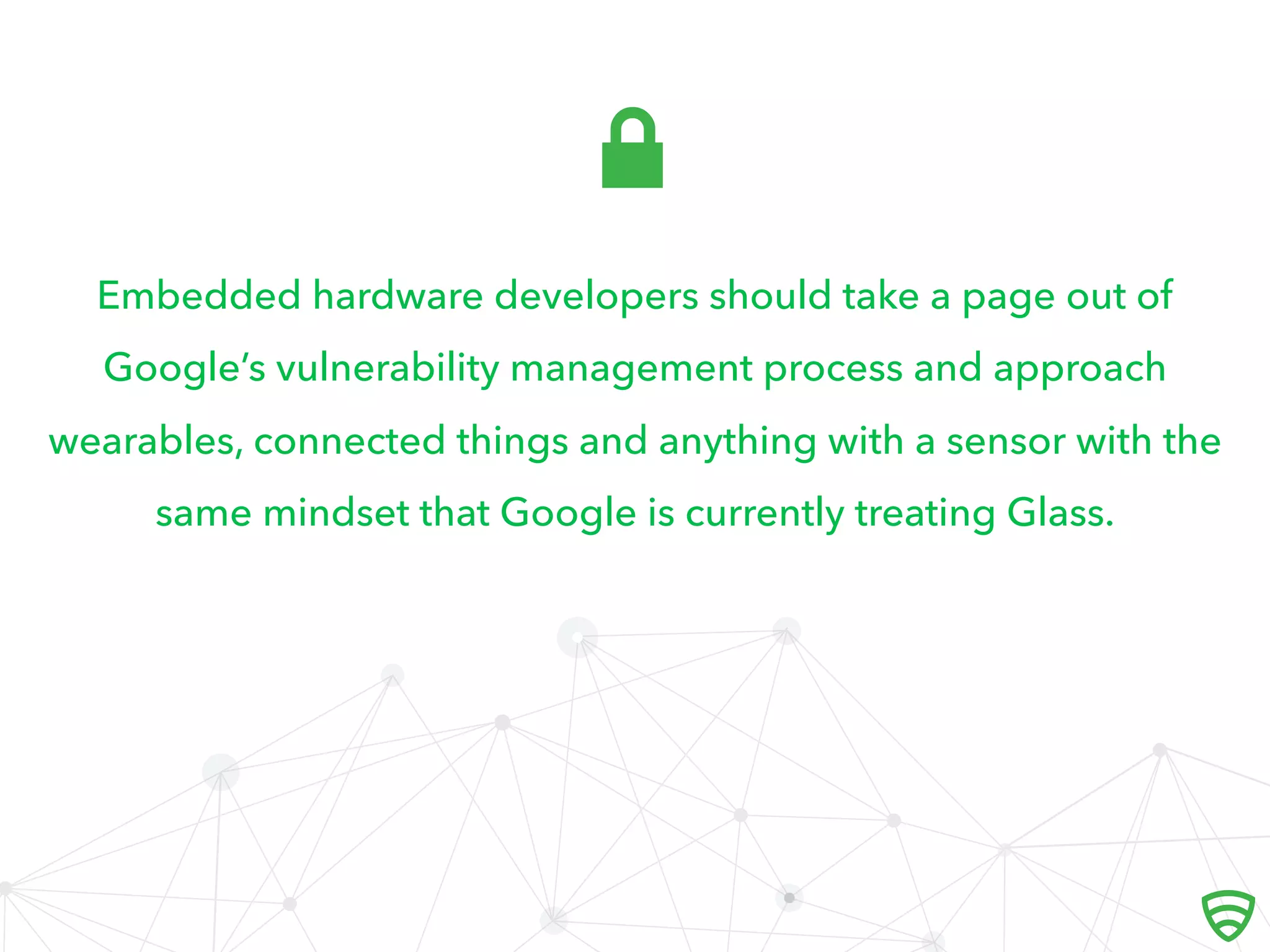
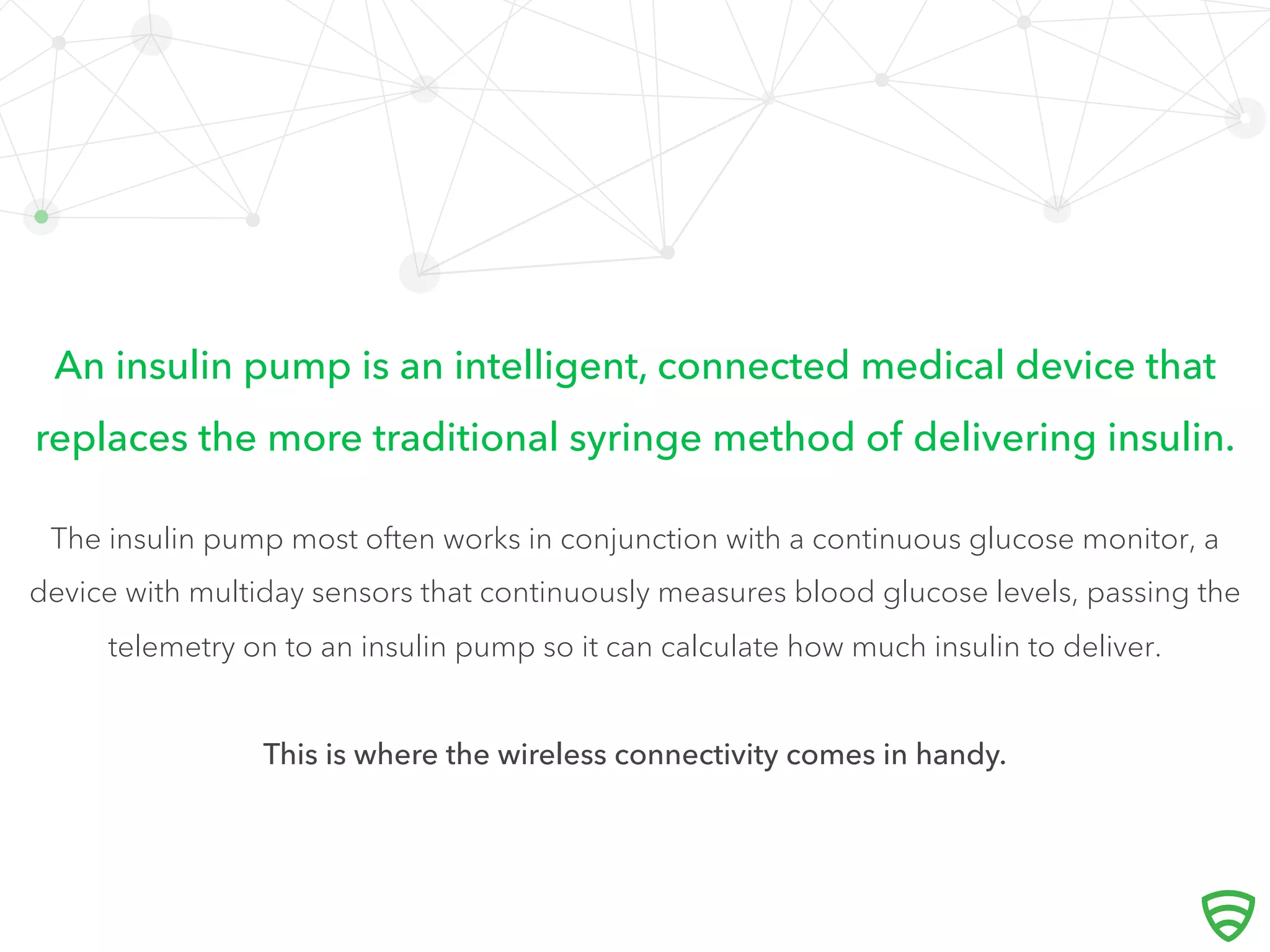
The document discusses the implications of the Internet of Things (IoT) on security, highlighting the vulnerabilities of connected devices that once had minimal risks. It emphasizes the necessity for companies to integrate security measures and manage vulnerabilities effectively, using examples like Google Glass and Medtronic insulin pumps. The text advocates for a proactive approach in designing connected devices to balance convenience with security.