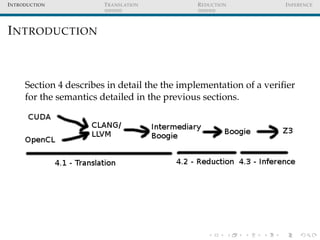
The document provides an in-depth overview of a verifier implementation for GPU semantics, focusing on translation reduction inference and specific challenges related to GPU languages and Boogie. Key topics include handling floating point numbers, pointers, race and barrier divergence checks, and the use of different abstraction strategies for shared-state management. The paper also discusses limitations of the approaches, such as the inability to verify complex shared-state manipulations and the need for invariant inference for race-free code verification.




![I NTRODUCTION T RANSLATION R EDUCTION I NFERENCE
P OINTER S EMANTICS
Translation rules of pointer model are straightforward:
Source Generated Boogie
p = A; p = int_ptr(A_base, 0);
p = q; p = q;
foo(p); foo(p);
p = q + 1; p = int_ptr(q.base, q.offset + 1);
if (p.base == A_base)
A[p.offset + e] = d;
p[e] = d; else if (p.base == B_base)
B[p.offset + e] = d;
else assert(false);
if (p.base == A_base)
x = A[p.offset + e];
x = p[e]; else if (p.base == B_base)
x = B[p.offset + e];
else assert(false);](https://image.slidesharecdn.com/presentation-121128061730-phpapp01/85/GPUVerify-Implementation-7-320.jpg)
![I NTRODUCTION T RANSLATION R EDUCTION I NFERENCE
B UT...
...if the program manipulates pointer in loops, the if...else if
clauses make determining the loop invariants hard.
One solution is to use points-to analysis (Steensgaard’s
algorithm) to determine which arrays a pointer can possibly
point to, and eliminate the impossible branches
if (p.base == A_base)
A[p.offset + e] = d; if (p.base == A_base)
else if (p.base == B_base) → A[p.offset + e] = d;
B[p.offset + e] = d; else assert(false);
else assert(false);](https://image.slidesharecdn.com/presentation-121128061730-phpapp01/85/GPUVerify-Implementation-8-320.jpg)


![I NTRODUCTION T RANSLATION R EDUCTION I NFERENCE
Recall: Consider:
if (A[0]) {
Stmt translate(Stmt, P) A[tid + 1] = tid;
LOG_READ_A(P$1, e$1); } else {
CHECK_READ_A(P$2, e$2); A[tid + 2] = tid;
x = A[e]; x$1 = P$1 ? * : x$1; }
x$2 = P$2 ? * : x$2;](https://image.slidesharecdn.com/presentation-121128061730-phpapp01/85/GPUVerify-Implementation-11-320.jpg)
![I NTRODUCTION T RANSLATION R EDUCTION I NFERENCE
Thread 0: Thread 1:
if (false) { if (true) {
... A[2] = 1;
} else { } else {
A[2] = 0; ...
} }
Because we’ve havoced away the shared state!](https://image.slidesharecdn.com/presentation-121128061730-phpapp01/85/GPUVerify-Implementation-12-320.jpg)

![I NTRODUCTION T RANSLATION R EDUCTION I NFERENCE
E QUALITY A BSTRACTION
Both threads keep a shadow copy of the shared-state
At a barrier, the shadow copies are set to be arbitrary, but
equal
On leaving the barrier, all threads have a consistent view
of the shared state
Stmt translatea (Stmt, P) translatee (Stmt, P)
LOG_READ_A(P$1, e$1);
LOG_READ_A(P$1, e$1); CHECK_READ_A(P$2, e$2);
CHECK_READ_A(P$2, e$2); x$1 = P$1 ? A$1[e$1] :
x = A[e]; x$1 = P$1 ? * : x$1; x$1;
x$2 = P$2 ? * : x$2; x$2 = P$2 ? A$2[e$2] :
x$2;
LOG_WRITE_A(P$1, e$1);
CHECK_WRITE_A(P$2, e$2);
LOG_WRITE_A(P$1, e$1); A$1[e$1] = P$1 ? x$1 :
A[e] = x; CHECK_WRITE_A(P$2, e$2); A$1[e$1];
A$2[e$2] = P$2 ? x$2 :
A$2[e$2];](https://image.slidesharecdn.com/presentation-121128061730-phpapp01/85/GPUVerify-Implementation-14-320.jpg)
![I NTRODUCTION T RANSLATION R EDUCTION I NFERENCE
L IMITATIONS
Unfortunately, Equality Abstraction is far less efficient
than Adversarial Abstraction
GPUVerify only uses Equality Abstraction with the arrays
that require it, this is determined using control
dependence analysis
More complicated uses of the shared-state, such as
A[B[lid]] = ... cannot be verified
This is because B[i] != B[j] cannot be verified, as the
side-effecting actions of other (prior) threads are not
modelled.](https://image.slidesharecdn.com/presentation-121128061730-phpapp01/85/GPUVerify-Implementation-15-320.jpg)

![I NTRODUCTION T RANSLATION R EDUCTION I NFERENCE
M EMORY S TRUCTURE H EURISTICS
The set of invariant heuristics discussed in the paper are for
common data structurings in arrays.
For example, if A[lid + C] = ... occurs in a loop, then a
candidate invariant is
WR EXISTS A ⇒ WR ELEM A − C == lid.](https://image.slidesharecdn.com/presentation-121128061730-phpapp01/85/GPUVerify-Implementation-17-320.jpg)