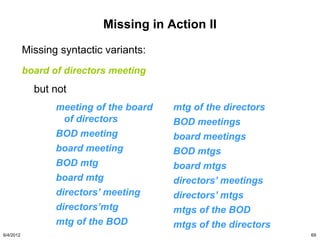
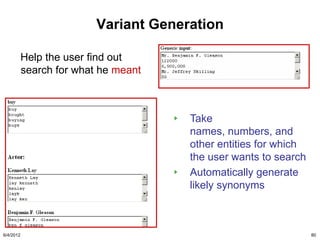
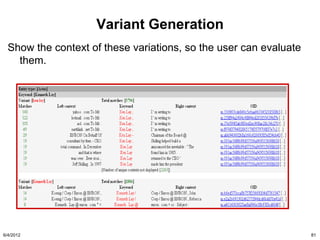
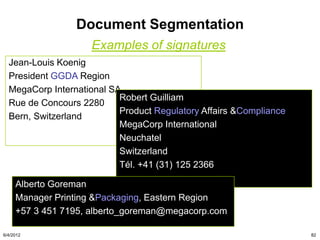
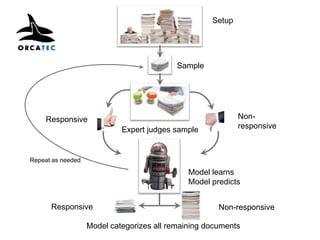
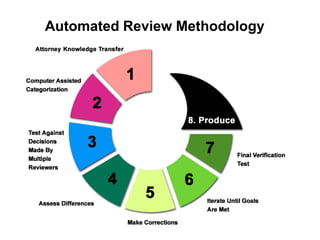
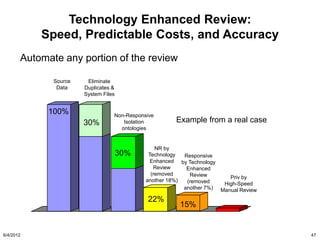
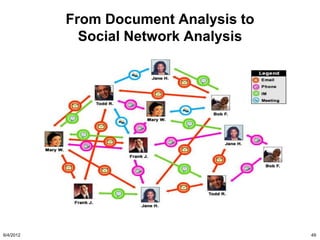
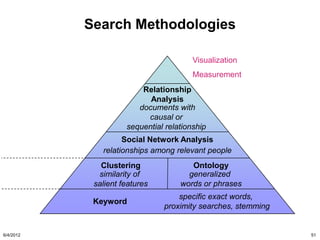
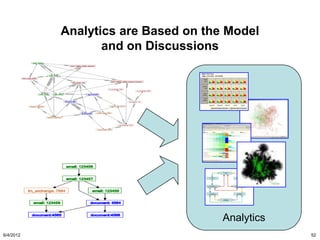
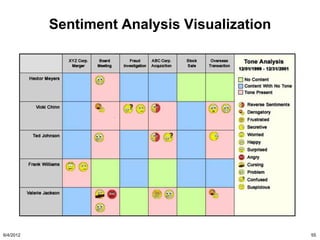
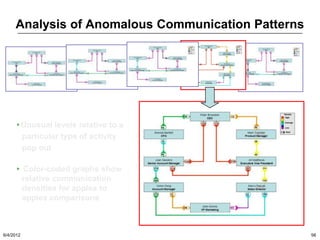
The document discusses the concepts of triggers, data preservation, and search methodologies related to litigation and e-discovery. It emphasizes the importance of properly identifying and managing data to prevent spoliation while examining the limitations of keyword searches and advocating for more advanced search techniques. Additionally, it highlights the evolving expectations of legal practices regarding defensibility and the establishment of best practices in data handling.














































![Search Under Scrutiny
Facciola’s Opinions - United States v. O’Keefe
“for lawyers and judges to dare opine that a certain
search term or terms would be more likely to produce
information than [other] search terms … is truly to go
where angels fear to tread.”
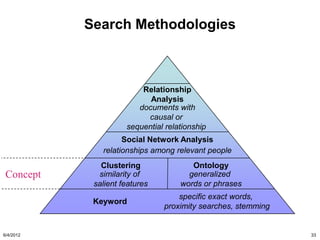
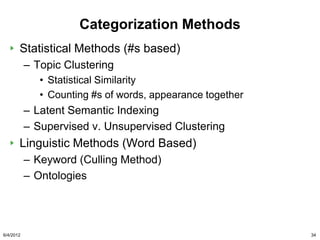
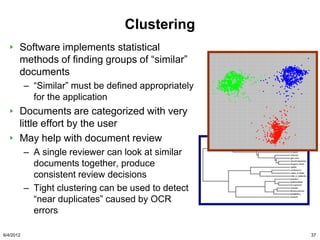
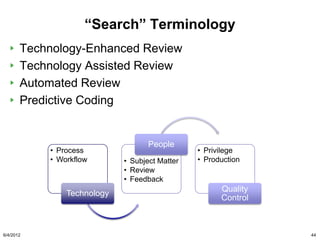
He has also suggested that litigants take a good look at
more advanced search methodologies, including the use
of computational linguistics and technology assisted
review
6/4/2012 65](https://image.slidesharecdn.com/georgetownlecture201262-120604123708-phpapp02/85/Georgetown-Law-Guest-Lecture-2012-6-2-65-320.jpg)