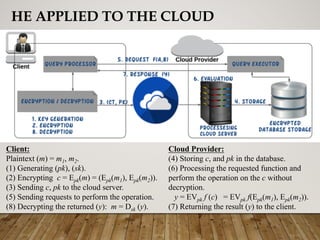
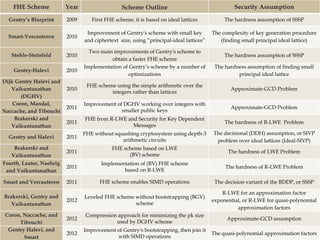
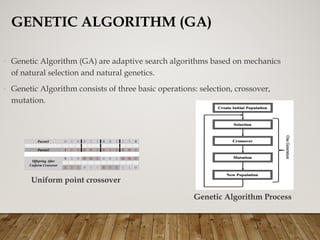
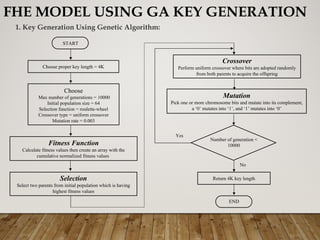
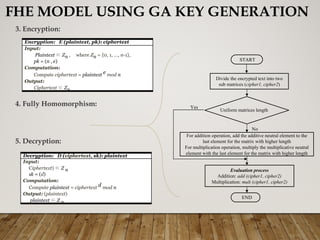
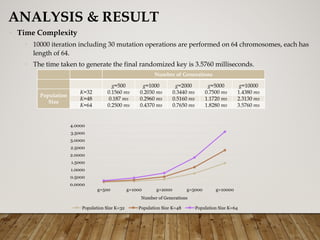
The document presents a genetic algorithm-based key generation approach for fully homomorphic encryption (FHE) aimed at enhancing data security in cloud computing. It outlines the motivation, problem statement, objectives, and proposed methodology for secure outsourcing of computations while preserving client confidentiality. The results demonstrate the effectiveness and efficiency of the proposed scheme, alongside future work suggestions for further improvements.






![• Based on the hardness of ideal lattices.
• Given m = m1, …, mt , c = E [f (m1, …, mt)],
for any function f (+, ✕, ⊕).
• Given a key pair (sk, pk), FHE scheme must have Evaluate function.
• Calculations: performed on E (m1) and E (m2)
Add: E (m1+ m2). Multiply: E (m1 ✕ m2).
• Circular security - The process of sk encryption under pk.
• Re-crypt algorithm - that takes a ciphertext E(m1) or E(m2) with noise N'< N
and provide a “new” ciphertext.
Gentry's Steps: Constructing a SWHE scheme, Squashing the decryption scheme,
then Bootstrapping.
GENTRY -](https://image.slidesharecdn.com/geneticalgorithmbasedkeygenerationforfullyhomomorphicencryption-180318015404/85/Presentation-Slides-Genetic-algorithm-based-key-generation-for-fully-homomorphic-encryption-9-320.jpg)




![[1] C. Gentry, “Fully homomorphic encryption using ideal lattices,” STOC'09 Proceedings of the forty-first
annual ACM symposium on Theory of computing, 2009, pp. 169–178.
[2] S. Mishra, and S. Bali, “Public Key Cryptography Using Genetic Algorithm,” International Journal of
Recent Technology and Engineering (IJRTE), 2013, vol. 2, pp. 150-54.
[3] A. Soni, and S. Agrawal, “Key Generation Using Genetic Algorithm for Image Encryption,”
International Journal of Computer Science and Mobile Computing (IJCSMC), 2013, Vol. 2, pp. 376 – 383.
[4] S. Jawaid, A. Saiyeda, and N. Suroor, “Selection of Fittest Key Using Genetic Algorithm and
Autocorrelation in Cryptography,” Journal of Computer Sciences and Applications (JCSA), 2015, vol. 3, pp.
46-51.
[5] Z. Brakerski, and V. Vaikuntanathan, “Efficient Fully Homomorphic Encryption from (Standard)
LWE,” FOCS’11 Proceedings of the 2011 IEEE 52nd Annual Symposium on Foundations of Computer
Science, 2011, pg. 97-106.
[6] M. van Dijk, C. Gentry, S. Halevi, and V. Vaikuntanathan, “Fully Homomorphic Encryption over the
Integers,” Advances in Cryptology – EUROCRYPT, 2010, vol. 6110, pp. 24-43.
BIBLIOGRAPHY](https://image.slidesharecdn.com/geneticalgorithmbasedkeygenerationforfullyhomomorphicencryption-180318015404/85/Presentation-Slides-Genetic-algorithm-based-key-generation-for-fully-homomorphic-encryption-18-320.jpg)
