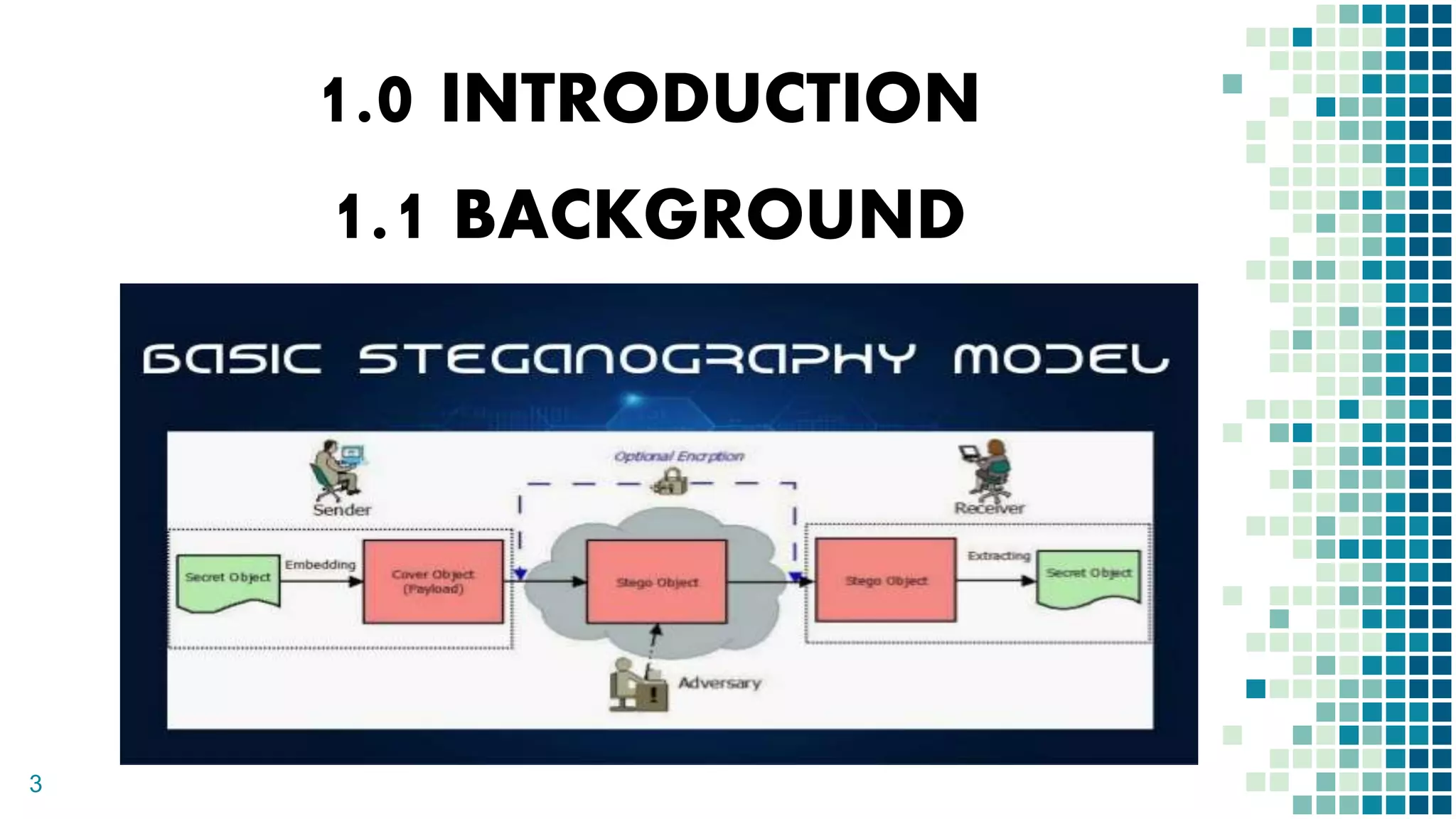
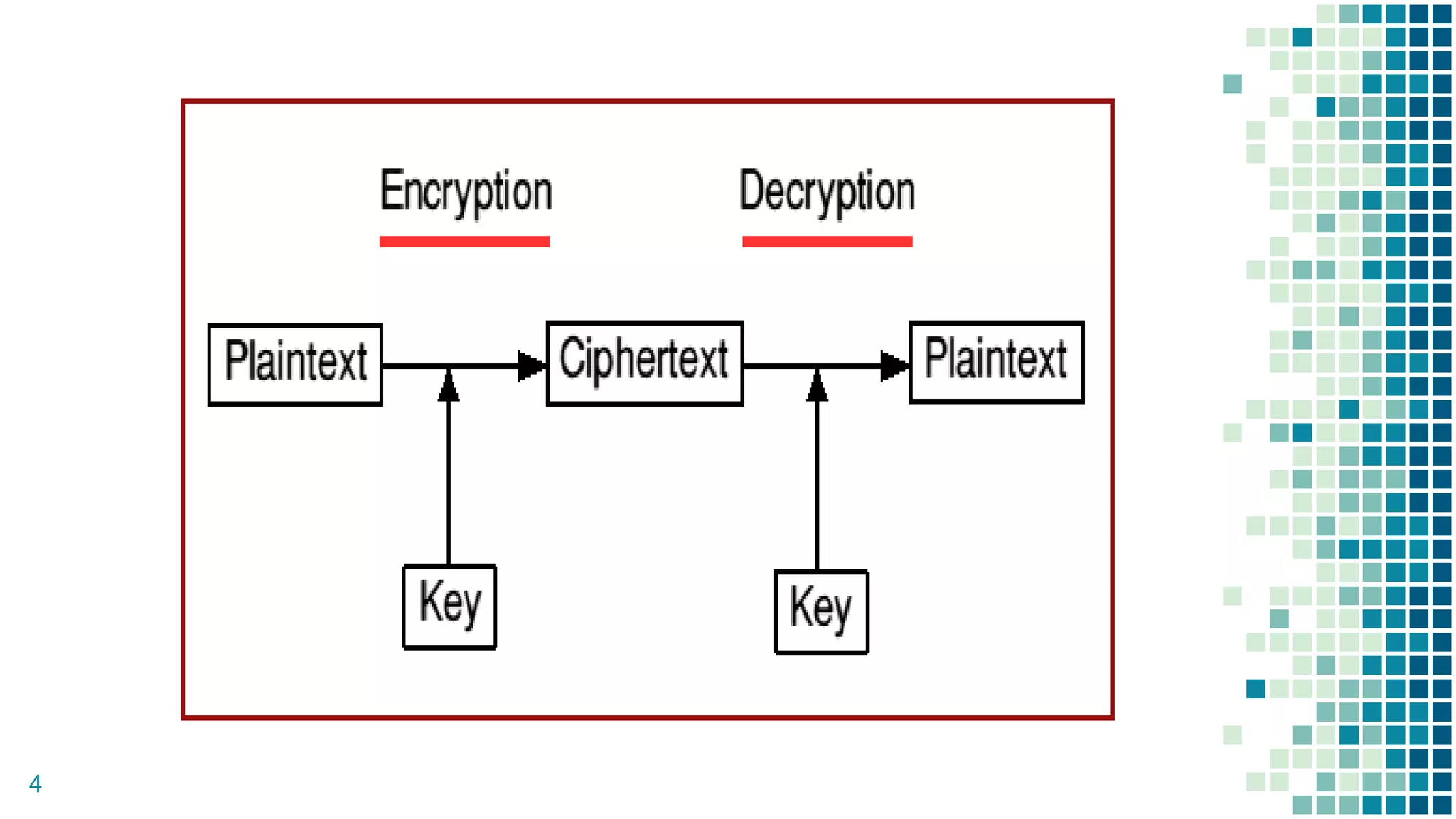
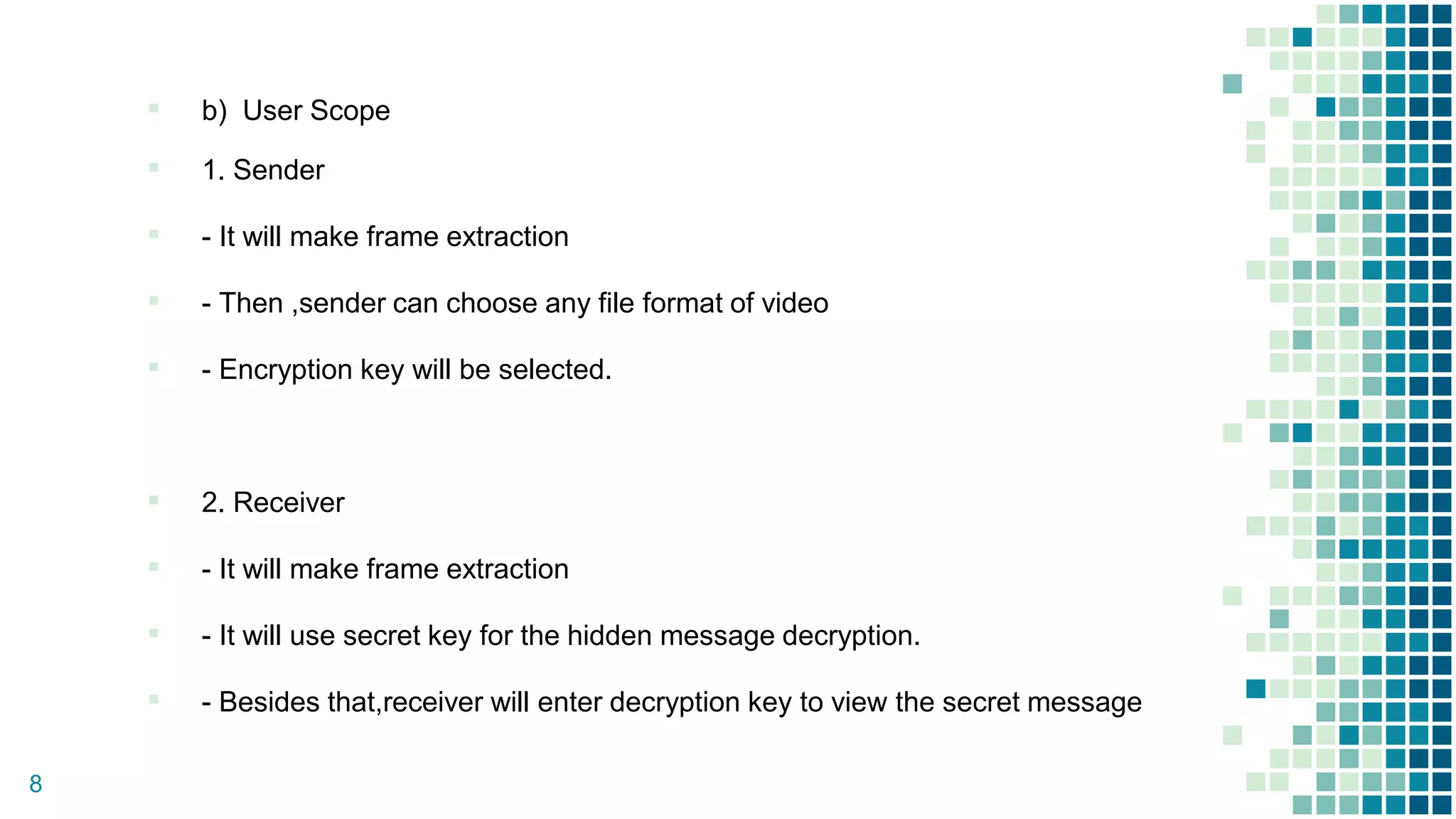
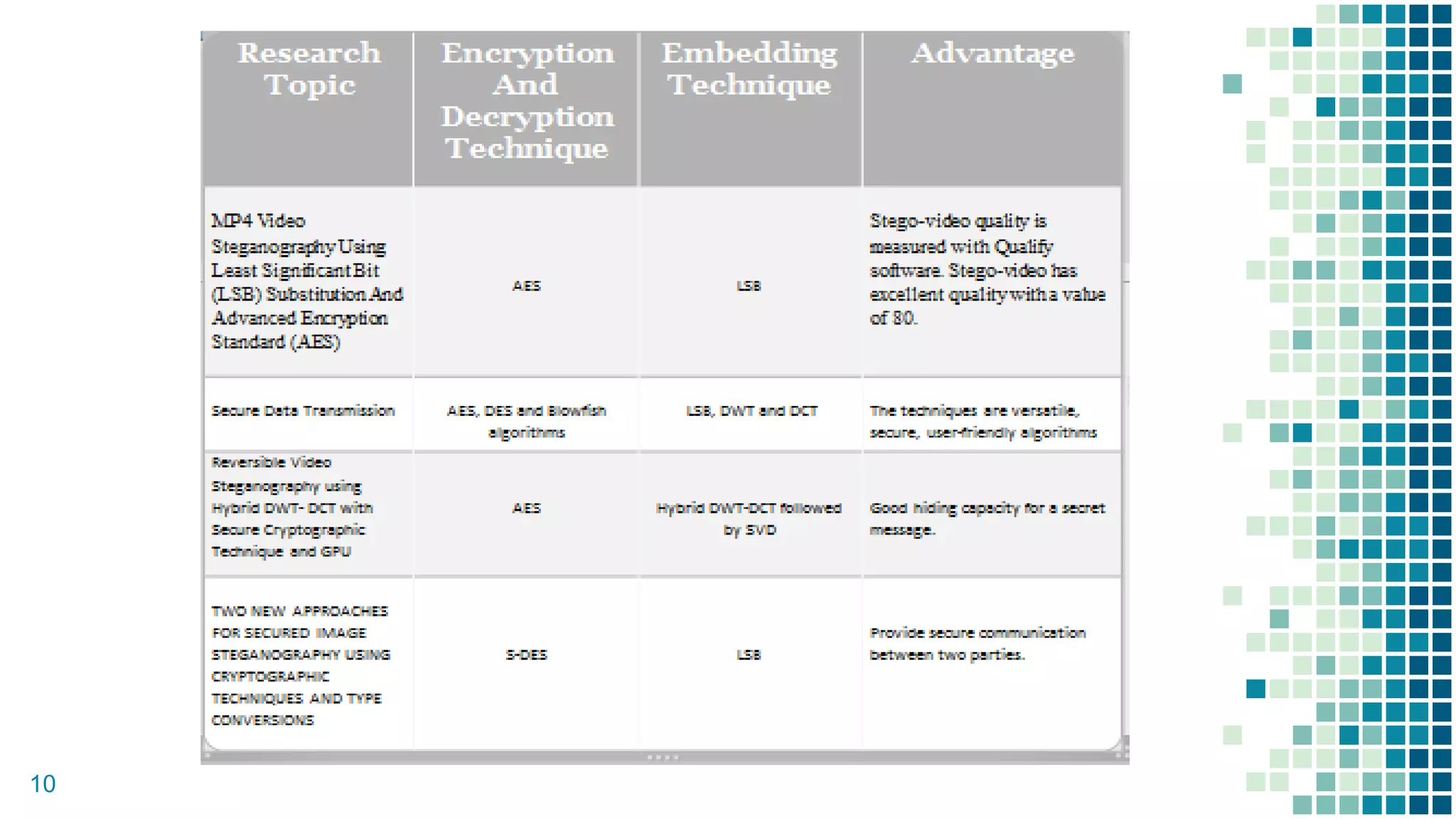
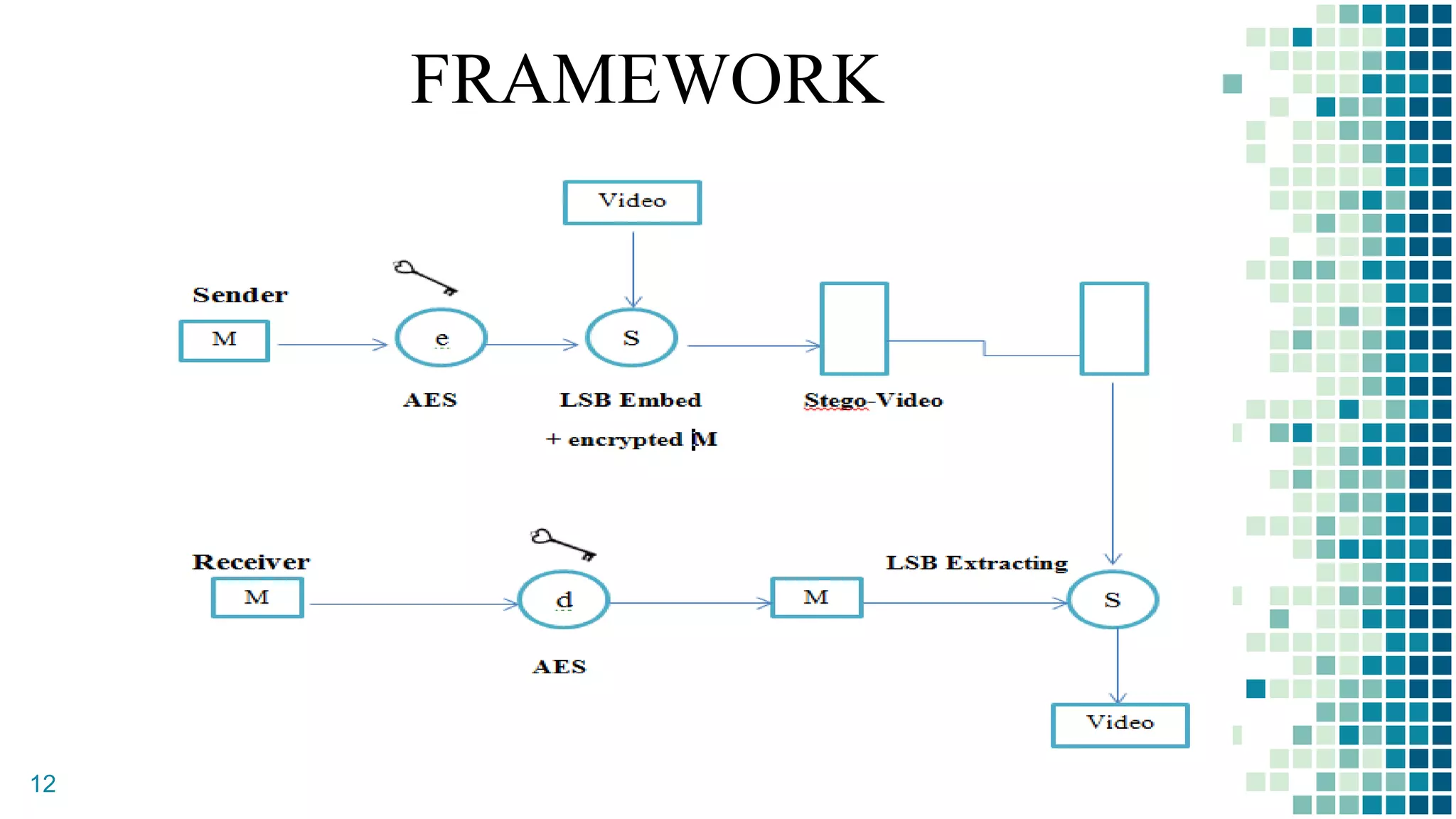
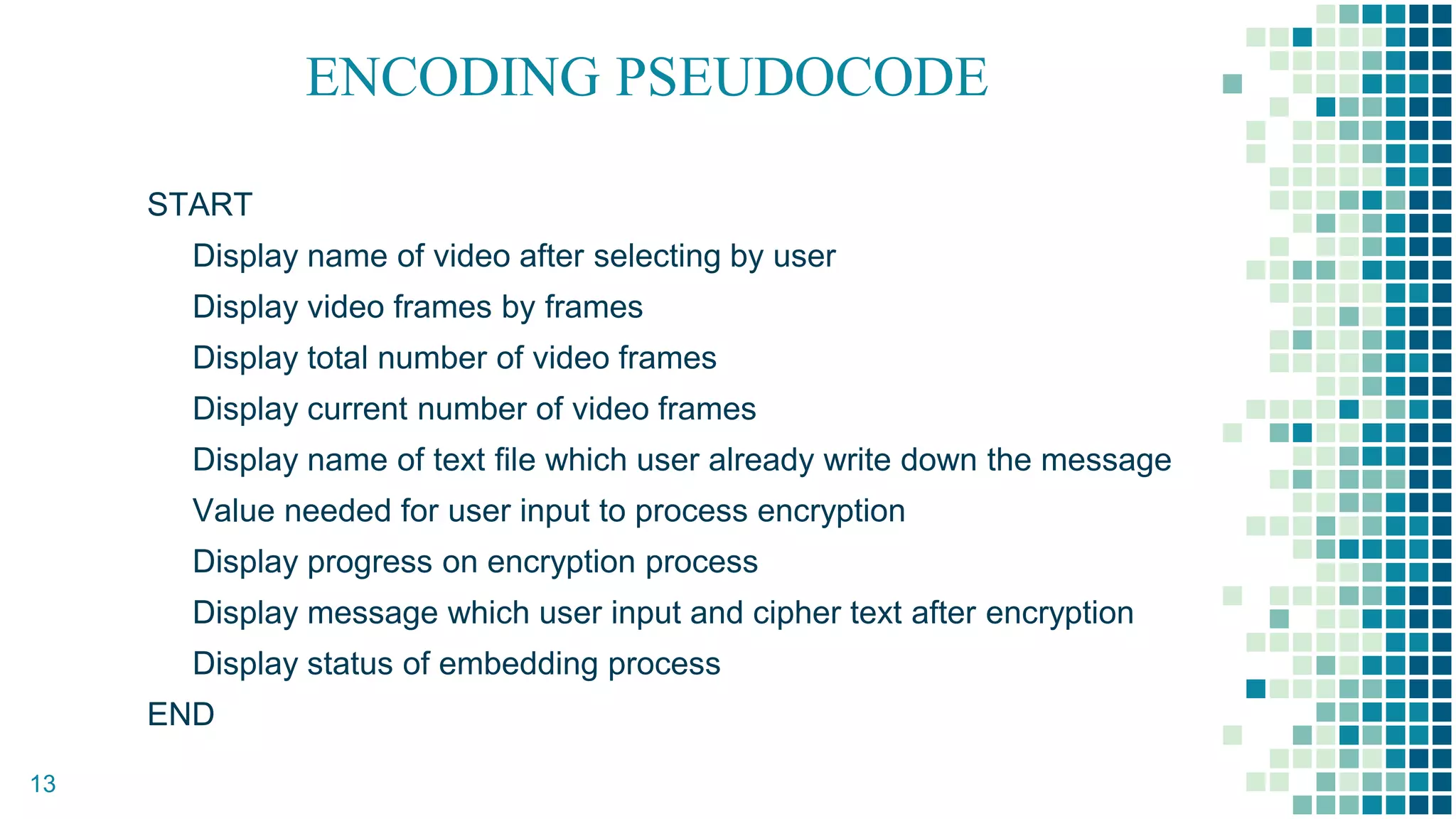
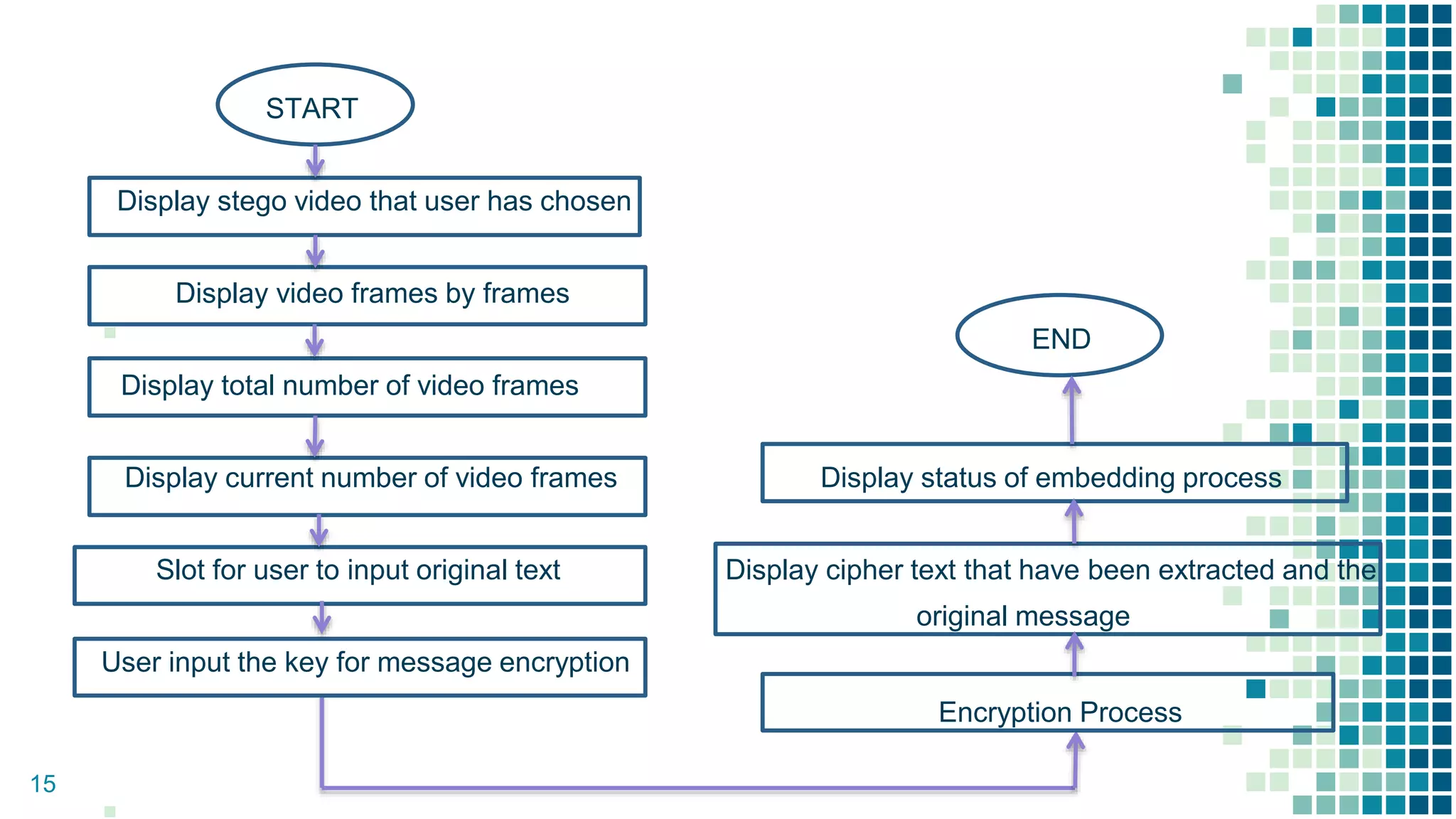
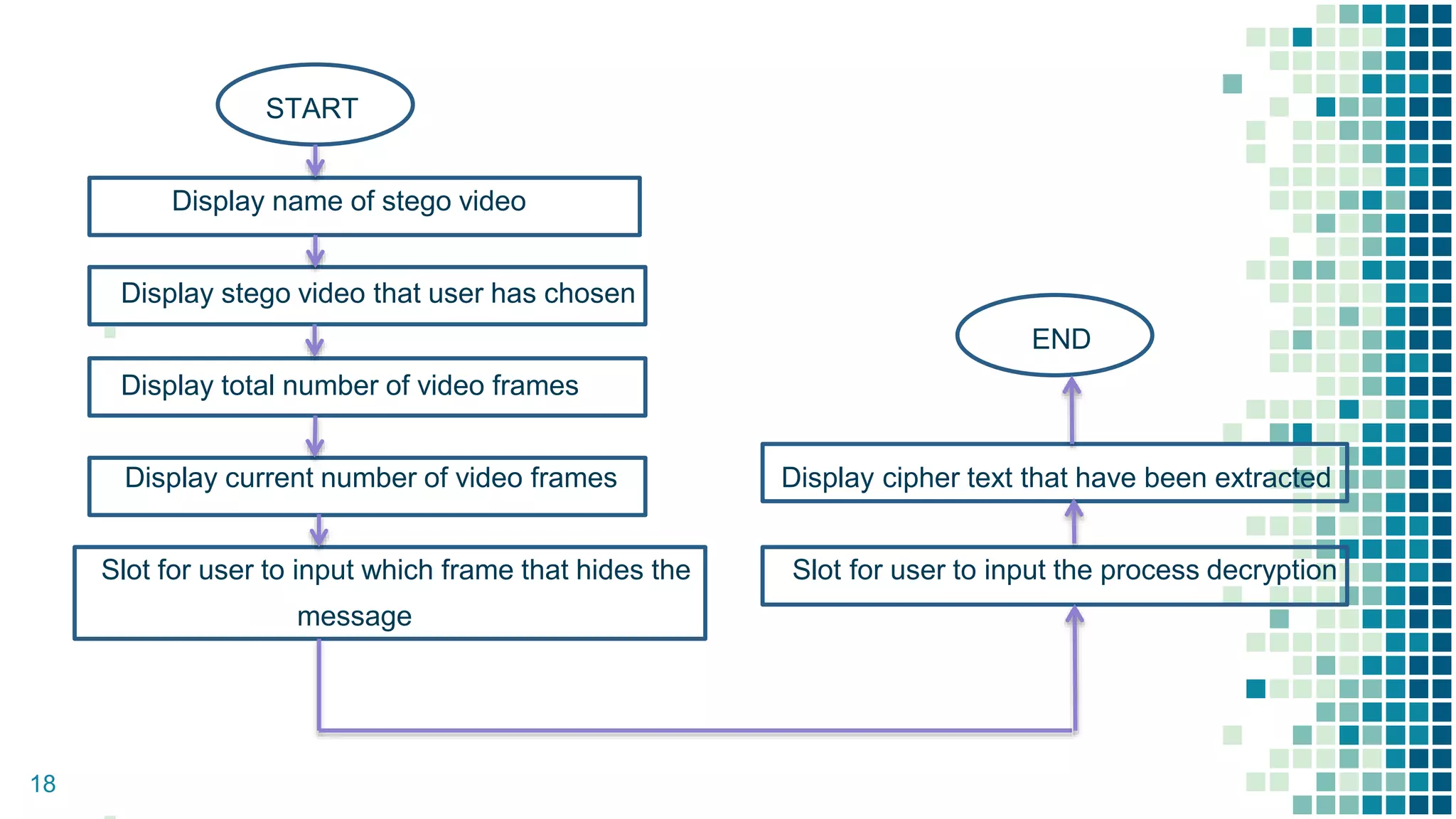
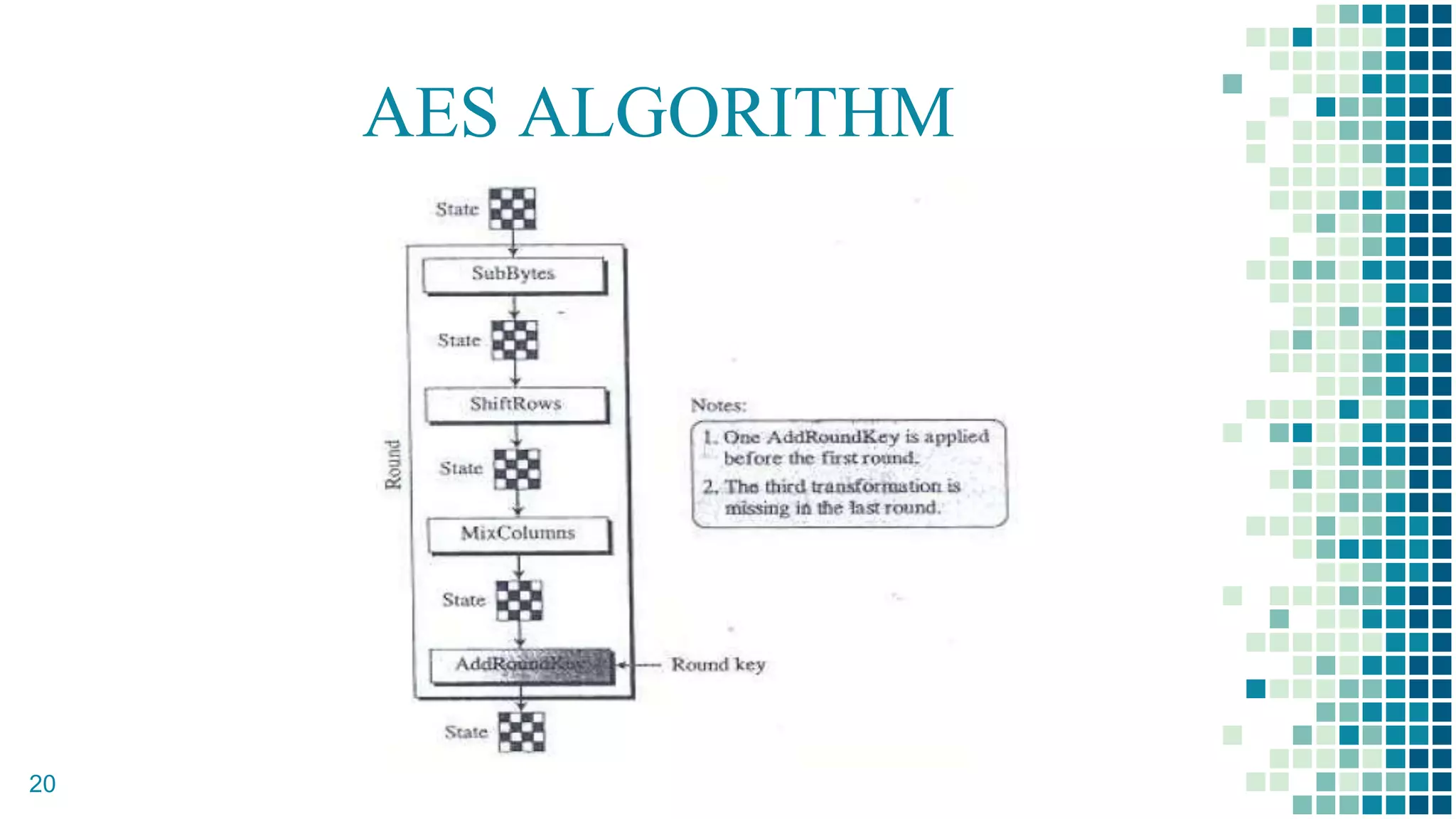
This document proposes a method for securing video transmission using steganography and cryptography. The method has three objectives: 1) To combine steganography and cryptography techniques to provide authentication and confidentiality of secret data, 2) To design the techniques to protect data secrecy, and 3) To implement and test if the cover media quality is lost after an encrypted message is hidden. The proposed method uses AES encryption to encrypt a message, which is then hidden in video frames using least significant bit steganography. It is implemented using MATLAB with the goal of minimizing quality loss to the cover video.









![THANKS!
▪ [1] Yi-Tu.Wu, F.Y. Shih, Genetic algorithm based methodology for breaking the steganalytic systems,
Systems, Man and Cybernetics, Part B: Cybernetics, IEEE Transactions on,36(1),Feb 2006,24-31.
▪ [2] M. Kharrazi, H.T. Cover Selection for Steganographic Embedding, Image Processing, IEEE International
Conference, Oct 2006, Atlanta, GA
▪ [3] Al- Ethawi G. A. Salman, "Text hiding in image border" Dean of the Military College of Engineering,
MsC. Thesis, 2002.
▪ [4] J. Ashok, Y. Raju, S. Munishankaralah and K. Srinnivas," Steganography : An Overview ", International
Journal of Engineering Science and Technology, Vol. No 2(10), pp: 5985-5992, 2010.
▪ [5] S. Katzenbeisser, F. A.P. Petitcolas, " Information hiding techniques for steganography and digital
watermarking ", pp: 20 - 23, June, 1999.
▪ [6] B.G.AAGARSANA, ANJALI, T.K.KIRTHIKA, Mr. S. SIVAKUMAR,(2018), IMAGE STEGANOGRAPHY
USING SECURED FORCE ALGORITHM FOR HIDING AUDIO SIGNAL INTO COLOUR IMAGE,
International Research Journal of Engineering and Technology (IRJET) , 5:1224-1228
▪ [7] Bharti Chandel, Dr.Shaily Jain, " Video Steganography: A Survey ",OSR Journal of Computer
Engineering (IOSR-JCE) e-ISSN: 2278-0661,p-ISSN: 2278-8727, Volume 18, Issue 1, Ver. III (Jan – Feb.
2016)
21
REFERENCES](https://image.slidesharecdn.com/fyp1slidepresentation2-180521151334/75/Fyp1-slide-presentation-2-1-21-2048.jpg)