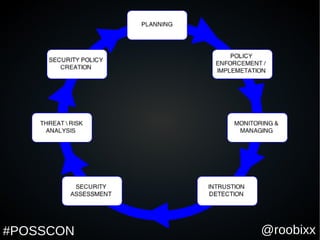
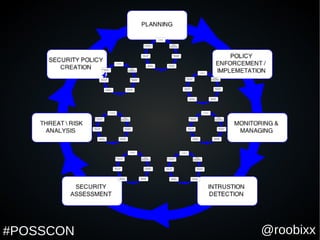
This document appears to be a slide presentation about fostering security maturity through a security lifecycle. Some key points made in the slides include that compliance does not equal security, gaining insight is important for security, and that open source tools can help organizations gain insight into their systems in a cost effective way without disrupting business. The presentation discusses doing an inventory of all systems and assets as the first step to develop a baseline understanding of normal activity to detect any suspicious activity.