First Quarter 2017 Top-Clicked Phishing Tests [INFOGRAPHIC]
•
1 like•527 views
What are the most frequently clicked phishing email subjects out there? We gathered data from our Phish Alert Button to show you what users fell for in Q1 2017.
Report
Share
Report
Share
Download to read offline
Recommended
Q4 2018 Top-Clicked Phishing Email Subjects

KnowBe4 reports every quarter on the top-clicked phishing email subjects, here we have the results for Q4 2018. We track three different categories: general email subjects, those related to social media and 'in the wild' attacks. Find out what your users are most likely to click on! See the full post here: https://blog.knowbe4.com/infographic-q4-2018-top-clicked-phishing-email-subjects-from-knowbe4
Phishing attack till now

Phishing basics: include its history
Introduction: phishing in detail
Techniques: Techniques used like link manipulation,web forgery
New phish: spear phishing
reason behind phishing
latest case study
survey: on top hosting and victim countries
Examples: popular website and email examples
Phishing

In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic attempting to acquire sensitive information such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic communication. Phishing is a fraudulent e-mail that attempts to get you to divulge personal data that can then be used for illegitimate purposes.
Cyber Response and Planning for SMBs

Every business is vulnerable to cyber threats and increasingly small and mid-size companies (SMBs) are targets. Yet most know little about what or how to communicate if faced with a breach. This slide presentation addresses the reputation risks for SMBs in today's digital landscape and resources to deal with the threat.
Preventing Nonprofit Banking Fraud and the Tools You Can Use!

Preventing Nonprofit Banking Fraud and the Tools You Can Use!
Recommended
Q4 2018 Top-Clicked Phishing Email Subjects

KnowBe4 reports every quarter on the top-clicked phishing email subjects, here we have the results for Q4 2018. We track three different categories: general email subjects, those related to social media and 'in the wild' attacks. Find out what your users are most likely to click on! See the full post here: https://blog.knowbe4.com/infographic-q4-2018-top-clicked-phishing-email-subjects-from-knowbe4
Phishing attack till now

Phishing basics: include its history
Introduction: phishing in detail
Techniques: Techniques used like link manipulation,web forgery
New phish: spear phishing
reason behind phishing
latest case study
survey: on top hosting and victim countries
Examples: popular website and email examples
Phishing

In the field of computer security, phishing is the criminally fraudulent process of attempting to acquire sensitive information such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic attempting to acquire sensitive information such as usernames, passwords and credit card details, by masquerading as a trustworthy entity in an electronic communication. Phishing is a fraudulent e-mail that attempts to get you to divulge personal data that can then be used for illegitimate purposes.
Cyber Response and Planning for SMBs

Every business is vulnerable to cyber threats and increasingly small and mid-size companies (SMBs) are targets. Yet most know little about what or how to communicate if faced with a breach. This slide presentation addresses the reputation risks for SMBs in today's digital landscape and resources to deal with the threat.
Preventing Nonprofit Banking Fraud and the Tools You Can Use!

Preventing Nonprofit Banking Fraud and the Tools You Can Use!
Info Session on Cybersecurity & Cybersecurity Study Jams

In an era where digital threats are ever-evolving, understanding the fundamentals of cybersecurity is crucial.
Highlights of the Event:
💡 Google Cybersecurity Certification Scholarship.
🎭 Cloning and Phishing Demystified
🚨 Unravelling the Depths of Database Breaches
🛡️ Digital safety 101
🧼 Self-Check for Cyber Hygiene
⏺️ Event Details:
Date: 18th December 2023
Time: 6:00 PM to 7:00 PM
Venue: Online
Check, Please! Alzheimer’s Association’s Early Success with Mobile Check Depo...

While most aspects of P2P fundraising have transitioned to the digital age, the standard procedure for receiving and processing offline donations has remained frozen in time – many nonprofits still require checks to be mailed in after collection.
To streamline gift processing and ease frustration on the part of chapters, participants, and staff, the Alzheimer’s Association chose to implement Boundless Fundraising Mobile Check Deposit earlier this year.
Join us as Noel Beebe, National Director of Digital Fundraising at Alzheimer’s Association, shares some early results that the organization has seen for The Longest Day event program and why they are excited to launch Mobile Check Deposit for Walk to End Alzheimer’s this fall.
Phishing attack, with SSL Encryption and HTTPS Working

This presentation contains Introduction of Phishing attack, its types and Various techniques, their impact with real live example, after that its Avoidance, Prevention and Solution. Also it contains brief introduction of SSL and HTTPS with their working.
Anti phishing

It is contain knowledge about Phishing and how it happen. It also contain knowledge about how we can prevent that. So this slide contain all the basic knowledge about phishing and anti-phishing.
CCIAOR Cyber Security Forum

View the latest trends from experts at the FBI, in cyber security and cyber insurance on real estate fraud.
Unveiling the dark web. The importance of your cybersecurity posture

We live in the cyberspace but nobody talked us about cybersecurity. The web , deep web and the dark web. The different vectors of cyberattacks. Recommendations to stay protected.
Webinar - Cyber Hygiene: Stay Clean at Work and at Home

Learn more about the growing menace of cybersecurity threats and how to reduce your risk.
Jax london2016 cybercrime-and-the-developer

In the emerging world of DevOps and the Cloud, most developers are trying to learn new technologies and methodologies. The focus tends to be on adding capabilities such as resiliency and scaling to an application. Still, one critical item consistently overlooked is security.
The world of the Cyber Criminal is closer than you realize. Watch a real man-in-the-middle demonstration and learn just how simple it can be for others to steal your secrets. In this talk you’ll learn about other practical examples of how you can inadvertently leave the doors open and what you can do to keep your system secure. In the end, security is everyone’s concern and this talk will teach you a few of simple actions you can take (and some behaviours you must change) to create a more secure application in the Cloud.
Kaseya Kaspersky Breaches

Join Kaseya and guest cybersecurity expert from Kaspersky, Cynthia James, to hear how companies like Target, eBay, and Home Depot are losing data, and how you can protect your company from suffering the same fate.
• The latest cybersecurity threats and vectors putting organizations at risk
• How your organization can avoid falling victim to a data breach
• Additional strategies to secure your organization and its data
Unit iii: Common Hacking Techniques

offline credential stealing, phishing, malware, pharming, online credential stealing, spyware, worms, trojans.
Simple Training for Information Security and Payment Fraud

The frequency of financial scams and payment fraud have been increasing substantially. We put these simple training slides together as a way to help our clients and friends.
Id theft avoiding and detecting

December is Identity Theft Prevention and Awareness Month - Identity theft is a serious crime. This is the month to educate yourself on how to prevent identity theft. Join us for an important webinar with staff members from the SC Department of Consumer Affairs on how to prevent ID theft and know what to do if it happens to you. Open to library staff, state government employees, general public.
Securing the Virtual Branch

The virtual branch is the financial institution’s franchise. But satisfying the experience of your valuable customers while protecting against the latest threats brings new challenges in securing this critical channel. Cybercrime has transformed into a sophisticated, billion-dollar industry, and high-risk targets need to develop a security posture that can scale to the volume and maturity of cyber-attacks being carried out. Multi-layered security solutions are needed to protect your virtual branch from fraud - but what does this even mean? This presentation highlights tools and best practices on pressing issues - account takeover, social engineering, neural network monitoring, and emerging payments.
McKonly & Asbury Webinar - Fraud Not If, But When

Our experts help you to understand the lessons learned from over 50 combined years of fraud experiences. Learn how good processes and internal controls can protect not only your organization, but also you as an individual. Obtain some practical tips on how you might prevent fraud in the future. Remember, it is not a question of “IF” fraud will occur in your organization, it is a question of “WHEN”. Are you prepared?
Check out our Upcoming Events page for news and updates on our future seminars and webinars at http://www.macpas.com/events/.
View a full recap of this webinar at http://www.macpas.com/webinar-cover-your-assets-asset-protection-trusts-and-the-vital-importance-of-trust-jurisdiction/
Why Do Some People Fall for Phishing Scams and What Do I Do About it?

Why do certain users fall for phishing attacks? What's going on? Are they on auto-pilot, not fully engaged in their online activities? Are they lacking critical thinking abilities? The short answer is no, they are in fact fully aware of what they are doing and reading but lack the experience to know they are being scammed. There are also several personality traits that contribute to their increased likelihood of victimization.
Dyre Malware infographic

The Dyre malware evolved quickly following its initial discovery in the summer of 2014. This infographic details Dyre's tactics and its very rapid development throughout late 2014 and early 2015. IBM Security can help protect banks and banking customers against Dyre with its endpoint protection and fraud detection solutions. To learn more, visit http://ibmsec.co/Th8Ad.
Adjusting primitives for graph : SHORT REPORT / NOTES

Graph algorithms, like PageRank Compressed Sparse Row (CSR) is an adjacency-list based graph representation that is
Multiply with different modes (map)
1. Performance of sequential execution based vs OpenMP based vector multiply.
2. Comparing various launch configs for CUDA based vector multiply.
Sum with different storage types (reduce)
1. Performance of vector element sum using float vs bfloat16 as the storage type.
Sum with different modes (reduce)
1. Performance of sequential execution based vs OpenMP based vector element sum.
2. Performance of memcpy vs in-place based CUDA based vector element sum.
3. Comparing various launch configs for CUDA based vector element sum (memcpy).
4. Comparing various launch configs for CUDA based vector element sum (in-place).
Sum with in-place strategies of CUDA mode (reduce)
1. Comparing various launch configs for CUDA based vector element sum (in-place).
做(mqu毕业证书)麦考瑞大学毕业证硕士文凭证书学费发票原版一模一样

原版定制【Q微信:741003700】《(mqu毕业证书)麦考瑞大学毕业证硕士文凭证书》【Q微信:741003700】成绩单 、雅思、外壳、留信学历认证永久存档查询,采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【Q微信741003700】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信741003700】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
More Related Content
Similar to First Quarter 2017 Top-Clicked Phishing Tests [INFOGRAPHIC]
Info Session on Cybersecurity & Cybersecurity Study Jams

In an era where digital threats are ever-evolving, understanding the fundamentals of cybersecurity is crucial.
Highlights of the Event:
💡 Google Cybersecurity Certification Scholarship.
🎭 Cloning and Phishing Demystified
🚨 Unravelling the Depths of Database Breaches
🛡️ Digital safety 101
🧼 Self-Check for Cyber Hygiene
⏺️ Event Details:
Date: 18th December 2023
Time: 6:00 PM to 7:00 PM
Venue: Online
Check, Please! Alzheimer’s Association’s Early Success with Mobile Check Depo...

While most aspects of P2P fundraising have transitioned to the digital age, the standard procedure for receiving and processing offline donations has remained frozen in time – many nonprofits still require checks to be mailed in after collection.
To streamline gift processing and ease frustration on the part of chapters, participants, and staff, the Alzheimer’s Association chose to implement Boundless Fundraising Mobile Check Deposit earlier this year.
Join us as Noel Beebe, National Director of Digital Fundraising at Alzheimer’s Association, shares some early results that the organization has seen for The Longest Day event program and why they are excited to launch Mobile Check Deposit for Walk to End Alzheimer’s this fall.
Phishing attack, with SSL Encryption and HTTPS Working

This presentation contains Introduction of Phishing attack, its types and Various techniques, their impact with real live example, after that its Avoidance, Prevention and Solution. Also it contains brief introduction of SSL and HTTPS with their working.
Anti phishing

It is contain knowledge about Phishing and how it happen. It also contain knowledge about how we can prevent that. So this slide contain all the basic knowledge about phishing and anti-phishing.
CCIAOR Cyber Security Forum

View the latest trends from experts at the FBI, in cyber security and cyber insurance on real estate fraud.
Unveiling the dark web. The importance of your cybersecurity posture

We live in the cyberspace but nobody talked us about cybersecurity. The web , deep web and the dark web. The different vectors of cyberattacks. Recommendations to stay protected.
Webinar - Cyber Hygiene: Stay Clean at Work and at Home

Learn more about the growing menace of cybersecurity threats and how to reduce your risk.
Jax london2016 cybercrime-and-the-developer

In the emerging world of DevOps and the Cloud, most developers are trying to learn new technologies and methodologies. The focus tends to be on adding capabilities such as resiliency and scaling to an application. Still, one critical item consistently overlooked is security.
The world of the Cyber Criminal is closer than you realize. Watch a real man-in-the-middle demonstration and learn just how simple it can be for others to steal your secrets. In this talk you’ll learn about other practical examples of how you can inadvertently leave the doors open and what you can do to keep your system secure. In the end, security is everyone’s concern and this talk will teach you a few of simple actions you can take (and some behaviours you must change) to create a more secure application in the Cloud.
Kaseya Kaspersky Breaches

Join Kaseya and guest cybersecurity expert from Kaspersky, Cynthia James, to hear how companies like Target, eBay, and Home Depot are losing data, and how you can protect your company from suffering the same fate.
• The latest cybersecurity threats and vectors putting organizations at risk
• How your organization can avoid falling victim to a data breach
• Additional strategies to secure your organization and its data
Unit iii: Common Hacking Techniques

offline credential stealing, phishing, malware, pharming, online credential stealing, spyware, worms, trojans.
Simple Training for Information Security and Payment Fraud

The frequency of financial scams and payment fraud have been increasing substantially. We put these simple training slides together as a way to help our clients and friends.
Id theft avoiding and detecting

December is Identity Theft Prevention and Awareness Month - Identity theft is a serious crime. This is the month to educate yourself on how to prevent identity theft. Join us for an important webinar with staff members from the SC Department of Consumer Affairs on how to prevent ID theft and know what to do if it happens to you. Open to library staff, state government employees, general public.
Securing the Virtual Branch

The virtual branch is the financial institution’s franchise. But satisfying the experience of your valuable customers while protecting against the latest threats brings new challenges in securing this critical channel. Cybercrime has transformed into a sophisticated, billion-dollar industry, and high-risk targets need to develop a security posture that can scale to the volume and maturity of cyber-attacks being carried out. Multi-layered security solutions are needed to protect your virtual branch from fraud - but what does this even mean? This presentation highlights tools and best practices on pressing issues - account takeover, social engineering, neural network monitoring, and emerging payments.
McKonly & Asbury Webinar - Fraud Not If, But When

Our experts help you to understand the lessons learned from over 50 combined years of fraud experiences. Learn how good processes and internal controls can protect not only your organization, but also you as an individual. Obtain some practical tips on how you might prevent fraud in the future. Remember, it is not a question of “IF” fraud will occur in your organization, it is a question of “WHEN”. Are you prepared?
Check out our Upcoming Events page for news and updates on our future seminars and webinars at http://www.macpas.com/events/.
View a full recap of this webinar at http://www.macpas.com/webinar-cover-your-assets-asset-protection-trusts-and-the-vital-importance-of-trust-jurisdiction/
Why Do Some People Fall for Phishing Scams and What Do I Do About it?

Why do certain users fall for phishing attacks? What's going on? Are they on auto-pilot, not fully engaged in their online activities? Are they lacking critical thinking abilities? The short answer is no, they are in fact fully aware of what they are doing and reading but lack the experience to know they are being scammed. There are also several personality traits that contribute to their increased likelihood of victimization.
Dyre Malware infographic

The Dyre malware evolved quickly following its initial discovery in the summer of 2014. This infographic details Dyre's tactics and its very rapid development throughout late 2014 and early 2015. IBM Security can help protect banks and banking customers against Dyre with its endpoint protection and fraud detection solutions. To learn more, visit http://ibmsec.co/Th8Ad.
Similar to First Quarter 2017 Top-Clicked Phishing Tests [INFOGRAPHIC] (20)
Info Session on Cybersecurity & Cybersecurity Study Jams

Info Session on Cybersecurity & Cybersecurity Study Jams
Check, Please! Alzheimer’s Association’s Early Success with Mobile Check Depo...

Check, Please! Alzheimer’s Association’s Early Success with Mobile Check Depo...
Phishing attack, with SSL Encryption and HTTPS Working

Phishing attack, with SSL Encryption and HTTPS Working
2017-01-23-Regulatory Compliance Watch - 6 Cybersecurity for Financial Servic...

2017-01-23-Regulatory Compliance Watch - 6 Cybersecurity for Financial Servic...
Unveiling the dark web. The importance of your cybersecurity posture

Unveiling the dark web. The importance of your cybersecurity posture
Webinar - Cyber Hygiene: Stay Clean at Work and at Home

Webinar - Cyber Hygiene: Stay Clean at Work and at Home
Simple Training for Information Security and Payment Fraud

Simple Training for Information Security and Payment Fraud
Why Do Some People Fall for Phishing Scams and What Do I Do About it?

Why Do Some People Fall for Phishing Scams and What Do I Do About it?
Recently uploaded
Adjusting primitives for graph : SHORT REPORT / NOTES

Graph algorithms, like PageRank Compressed Sparse Row (CSR) is an adjacency-list based graph representation that is
Multiply with different modes (map)
1. Performance of sequential execution based vs OpenMP based vector multiply.
2. Comparing various launch configs for CUDA based vector multiply.
Sum with different storage types (reduce)
1. Performance of vector element sum using float vs bfloat16 as the storage type.
Sum with different modes (reduce)
1. Performance of sequential execution based vs OpenMP based vector element sum.
2. Performance of memcpy vs in-place based CUDA based vector element sum.
3. Comparing various launch configs for CUDA based vector element sum (memcpy).
4. Comparing various launch configs for CUDA based vector element sum (in-place).
Sum with in-place strategies of CUDA mode (reduce)
1. Comparing various launch configs for CUDA based vector element sum (in-place).
做(mqu毕业证书)麦考瑞大学毕业证硕士文凭证书学费发票原版一模一样

原版定制【Q微信:741003700】《(mqu毕业证书)麦考瑞大学毕业证硕士文凭证书》【Q微信:741003700】成绩单 、雅思、外壳、留信学历认证永久存档查询,采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【Q微信741003700】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信741003700】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
Quantitative Data AnalysisReliability Analysis (Cronbach Alpha) Common Method...

Quantitative data Analysis
Overview
Reliability Analysis (Cronbach Alpha)
Common Method Bias (Harman Single Factor Test)
Frequency Analysis (Demographic)
Descriptive Analysis
一比一原版(BCU毕业证书)伯明翰城市大学毕业证如何办理

原版定制【微信:41543339】【(BCU毕业证书)伯明翰城市大学毕业证】【微信:41543339】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信41543339】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信41543339】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
【社内勉強会資料_Octo: An Open-Source Generalist Robot Policy】

一般的なロボットポリシーモデルであり、トランスフォーマーベースの拡散ポリシーとして実装されているOctoについて紹介しています。
一比一原版(NYU毕业证)纽约大学毕业证成绩单

NYU毕业证【微信95270640】《如何办理NYU毕业证纽约大学文凭学历》【Q微信95270640】《纽约大学文凭学历证书》《纽约大学毕业证书与成绩单样本图片》毕业证书补办 Fake Degree做学费单《毕业证明信-推荐信》成绩单,录取通知书,Offer,在读证明,雅思托福成绩单,真实大使馆教育部认证,回国人员证明,留信网认证。网上存档永久可查!
【本科硕士】纽约大学纽约大学毕业证学位证(GPA修改);学历认证(教育部认证);大学Offer录取通知书留信认证使馆认证;雅思语言证书等高仿类证书。
办理流程:
1客户提供办理纽约大学纽约大学毕业证学位证信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)
真实网上可查的证明材料
1教育部学历学位认证留服官网真实存档可查永久存档。
2留学回国人员证明(使馆认证)使馆网站真实存档可查。
我们对海外大学及学院的毕业证成绩单所使用的材料尺寸大小防伪结构(包括:纽约大学纽约大学毕业证学位证隐形水印阴影底纹钢印LOGO烫金烫银LOGO烫金烫银复合重叠。文字图案浮雕激光镭射紫外荧光温感复印防伪)都有原版本文凭对照。质量得到了广大海外客户群体的认可同时和海外学校留学中介做到与时俱进及时掌握各大院校的(毕业证成绩单资格证结业证录取通知书在读证明等相关材料)的版本更新信息能够在第一时间掌握最新的海外学历文凭的样版尺寸大小纸张材质防伪技术等等并在第一时间收集到原版实物以求达到客户的需求。
本公司还可以按照客户原版印刷制作且能够达到客户理想的要求。有需要办理证件的客户请联系我们在线客服中心微信:95270640 或咨询在线已转到了尽头他的城市生活也将划上一个不很圆满的句号了值得庆幸的是山娃早记下了他们的学校和联系方式说也奇怪在山娃离城的头一天父亲居然请假陪山娃耍了一天那一天父亲陪着山娃辗转长隆水上乐园疯了一整天水上漂流高空冲浪看大马戏大凡里面有的父亲都带着他去疯一把山娃算了算这一次足足花了老爸元够他挣上半个月的山娃很不解一向节俭的父亲啥时变得如此阔绰大方大把大把掏钱时居然连眉头也不皱一下车票早买好了直达卧铺车得经子
一比一原版(UPenn毕业证)宾夕法尼亚大学毕业证成绩单

UPenn毕业证【微信95270640】办理宾夕法尼亚大学毕业证原版一模一样、UPenn毕业证制作【Q微信95270640】《宾夕法尼亚大学毕业证购买流程》《UPenn成绩单制作》宾夕法尼亚大学毕业证书UPenn毕业证文凭宾夕法尼亚大学
本科毕业证书,学历学位认证如何办理【留学国外学位学历认证、毕业证、成绩单、大学Offer、雅思托福代考、语言证书、学生卡、高仿教育部认证等一切高仿或者真实可查认证服务】代办国外(海外)英国、加拿大、美国、新西兰、澳大利亚、新西兰等国外各大学毕业证、文凭学历证书、成绩单、学历学位认证真实可查。
办国外宾夕法尼亚大学宾夕法尼亚大学硕士学位证成绩单教育部学历学位认证留信认证大使馆认证留学回国人员证明修改成绩单信封申请学校offer录取通知书在读证明offer letter。
快速办理高仿国外毕业证成绩单:
1宾夕法尼亚大学毕业证+成绩单+留学回国人员证明+教育部学历认证(全套留学回国必备证明材料给父母及亲朋好友一份完美交代);
2雅思成绩单托福成绩单OFFER在读证明等留学相关材料(申请学校转学甚至是申请工签都可以用到)。
3.毕业证 #成绩单等全套材料从防伪到印刷从水印到钢印烫金高精仿度跟学校原版100%相同。
专业服务请勿犹豫联系我!联系人微信号:95270640诚招代理:本公司诚聘当地代理人员如果你有业余时间有兴趣就请联系我们。
国外宾夕法尼亚大学宾夕法尼亚大学硕士学位证成绩单办理过程:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)。我们在哪里父母对我们的爱和思念为我们的生命增加了光彩给予我们自由追求的力量生活的力量我们也不忘感恩正因为这股感恩的线牵着我们使我们在一年的结束时刻义无反顾的踏上了回家的旅途人们常说父母恩最难回报愿我能以当年爸爸妈妈对待小时候的我们那样耐心温柔地对待我将渐渐老去的父母体谅他们以反哺之心奉敬父母以感恩之心孝顺父母哪怕只为父母换洗衣服为父母喂饭送汤按摩酸痛的腰背握着父母的手扶着他们一步一步地慢慢散步.娃
一比一原版(UniSA毕业证书)南澳大学毕业证如何办理

原版定制【微信:41543339】【(UniSA毕业证书)南澳大学毕业证】【微信:41543339】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信41543339】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信41543339】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
一比一原版(爱大毕业证书)爱丁堡大学毕业证如何办理

毕业原版【微信:41543339】【(爱大毕业证书)爱丁堡大学毕业证】【微信:41543339】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信41543339】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信41543339】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
一比一原版(Deakin毕业证书)迪肯大学毕业证如何办理

原版定制【微信:41543339】【(Deakin毕业证书)迪肯大学毕业证】【微信:41543339】成绩单、外壳、offer、留信学历认证(永久存档真实可查)采用学校原版纸张、特殊工艺完全按照原版一比一制作(包括:隐形水印,阴影底纹,钢印LOGO烫金烫银,LOGO烫金烫银复合重叠,文字图案浮雕,激光镭射,紫外荧光,温感,复印防伪)行业标杆!精益求精,诚心合作,真诚制作!多年品质 ,按需精细制作,24小时接单,全套进口原装设备,十五年致力于帮助留学生解决难题,业务范围有加拿大、英国、澳洲、韩国、美国、新加坡,新西兰等学历材料,包您满意。
【我们承诺采用的是学校原版纸张(纸质、底色、纹路),我们拥有全套进口原装设备,特殊工艺都是采用不同机器制作,仿真度基本可以达到100%,所有工艺效果都可提前给客户展示,不满意可以根据客户要求进行调整,直到满意为止!】
【业务选择办理准则】
一、工作未确定,回国需先给父母、亲戚朋友看下文凭的情况,办理一份就读学校的毕业证【微信41543339】文凭即可
二、回国进私企、外企、自己做生意的情况,这些单位是不查询毕业证真伪的,而且国内没有渠道去查询国外文凭的真假,也不需要提供真实教育部认证。鉴于此,办理一份毕业证【微信41543339】即可
三、进国企,银行,事业单位,考公务员等等,这些单位是必需要提供真实教育部认证的,办理教育部认证所需资料众多且烦琐,所有材料您都必须提供原件,我们凭借丰富的经验,快捷的绿色通道帮您快速整合材料,让您少走弯路。
留信网认证的作用:
1:该专业认证可证明留学生真实身份
2:同时对留学生所学专业登记给予评定
3:国家专业人才认证中心颁发入库证书
4:这个认证书并且可以归档倒地方
5:凡事获得留信网入网的信息将会逐步更新到个人身份内,将在公安局网内查询个人身份证信息后,同步读取人才网入库信息
6:个人职称评审加20分
7:个人信誉贷款加10分
8:在国家人才网主办的国家网络招聘大会中纳入资料,供国家高端企业选择人才
留信网服务项目:
1、留学生专业人才库服务(留信分析)
2、国(境)学习人员提供就业推荐信服务
3、留学人员区块链存储服务
→ 【关于价格问题(保证一手价格)】
我们所定的价格是非常合理的,而且我们现在做得单子大多数都是代理和回头客户介绍的所以一般现在有新的单子 我给客户的都是第一手的代理价格,因为我想坦诚对待大家 不想跟大家在价格方面浪费时间
对于老客户或者被老客户介绍过来的朋友,我们都会适当给一些优惠。
选择实体注册公司办理,更放心,更安全!我们的承诺:客户在留信官方认证查询网站查询到认证通过结果后付款,不成功不收费!
06-04-2024 - NYC Tech Week - Discussion on Vector Databases, Unstructured Dat...

06-04-2024 - NYC Tech Week - Discussion on Vector Databases, Unstructured Data and AI
Round table discussion of vector databases, unstructured data, ai, big data, real-time, robots and Milvus.
A lively discussion with NJ Gen AI Meetup Lead, Prasad and Procure.FYI's Co-Found
Ch03-Managing the Object-Oriented Information Systems Project a.pdf

Object oriented system analysis and design
一比一原版(UIUC毕业证)伊利诺伊大学|厄巴纳-香槟分校毕业证如何办理

UIUC毕业证offer【微信95270640】☀《伊利诺伊大学|厄巴纳-香槟分校毕业证购买》GoogleQ微信95270640《UIUC毕业证模板办理》加拿大文凭、本科、硕士、研究生学历都可以做,二、业务范围:
★、全套服务:毕业证、成绩单、化学专业毕业证书伪造《伊利诺伊大学|厄巴纳-香槟分校大学毕业证》Q微信95270640《UIUC学位证书购买》
(诚招代理)办理国外高校毕业证成绩单文凭学位证,真实使馆公证(留学回国人员证明)真实留信网认证国外学历学位认证雅思代考国外学校代申请名校保录开请假条改GPA改成绩ID卡
1.高仿业务:【本科硕士】毕业证,成绩单(GPA修改),学历认证(教育部认证),大学Offer,,ID,留信认证,使馆认证,雅思,语言证书等高仿类证书;
2.认证服务: 学历认证(教育部认证),大使馆认证(回国人员证明),留信认证(可查有编号证书),大学保录取,雅思保分成绩单。
3.技术服务:钢印水印烫金激光防伪凹凸版设计印刷激凸温感光标底纹镭射速度快。
办理伊利诺伊大学|厄巴纳-香槟分校伊利诺伊大学|厄巴纳-香槟分校毕业证offer流程:
1客户提供办理信息:姓名生日专业学位毕业时间等(如信息不确定可以咨询顾问:我们有专业老师帮你查询);
2开始安排制作毕业证成绩单电子图;
3毕业证成绩单电子版做好以后发送给您确认;
4毕业证成绩单电子版您确认信息无误之后安排制作成品;
5成品做好拍照或者视频给您确认;
6快递给客户(国内顺丰国外DHLUPS等快读邮寄)
-办理真实使馆公证(即留学回国人员证明)
-办理各国各大学文凭(世界名校一对一专业服务,可全程监控跟踪进度)
-全套服务:毕业证成绩单真实使馆公证真实教育部认证。让您回国发展信心十足!
(详情请加一下 文凭顾问+微信:95270640)欢迎咨询!的鬼地方父亲的家在高楼最底屋最下面很矮很黑是很不显眼的地下室父亲的家安在别人脚底下须绕过高楼旁边的垃圾堆下八个台阶才到父亲的家很狭小除了一张单人床和一张小方桌几乎没有多余的空间山娃一下子就联想起学校的男小便处山娃很想笑却怎么也笑不出来山娃很迷惑父亲的家除了一扇小铁门连窗户也没有墓穴一般阴森森有些骇人父亲的城也便成了山娃的城父亲的家也便成了山娃的家父亲让山娃呆在屋里做作业看电视最多只能在门口透透气间
Algorithmic optimizations for Dynamic Levelwise PageRank (from STICD) : SHORT...

Techniques to optimize the pagerank algorithm usually fall in two categories. One is to try reducing the work per iteration, and the other is to try reducing the number of iterations. These goals are often at odds with one another. Skipping computation on vertices which have already converged has the potential to save iteration time. Skipping in-identical vertices, with the same in-links, helps reduce duplicate computations and thus could help reduce iteration time. Road networks often have chains which can be short-circuited before pagerank computation to improve performance. Final ranks of chain nodes can be easily calculated. This could reduce both the iteration time, and the number of iterations. If a graph has no dangling nodes, pagerank of each strongly connected component can be computed in topological order. This could help reduce the iteration time, no. of iterations, and also enable multi-iteration concurrency in pagerank computation. The combination of all of the above methods is the STICD algorithm. [sticd] For dynamic graphs, unchanged components whose ranks are unaffected can be skipped altogether.
Recently uploaded (20)
Adjusting primitives for graph : SHORT REPORT / NOTES

Adjusting primitives for graph : SHORT REPORT / NOTES
Quantitative Data AnalysisReliability Analysis (Cronbach Alpha) Common Method...

Quantitative Data AnalysisReliability Analysis (Cronbach Alpha) Common Method...
Data_and_Analytics_Essentials_Architect_an_Analytics_Platform.pptx

Data_and_Analytics_Essentials_Architect_an_Analytics_Platform.pptx
【社内勉強会資料_Octo: An Open-Source Generalist Robot Policy】

【社内勉強会資料_Octo: An Open-Source Generalist Robot Policy】
Best best suvichar in gujarati english meaning of this sentence as Silk road ...

Best best suvichar in gujarati english meaning of this sentence as Silk road ...
06-04-2024 - NYC Tech Week - Discussion on Vector Databases, Unstructured Dat...

06-04-2024 - NYC Tech Week - Discussion on Vector Databases, Unstructured Dat...
Ch03-Managing the Object-Oriented Information Systems Project a.pdf

Ch03-Managing the Object-Oriented Information Systems Project a.pdf
Machine learning and optimization techniques for electrical drives.pptx

Machine learning and optimization techniques for electrical drives.pptx
Influence of Marketing Strategy and Market Competition on Business Plan

Influence of Marketing Strategy and Market Competition on Business Plan
Algorithmic optimizations for Dynamic Levelwise PageRank (from STICD) : SHORT...

Algorithmic optimizations for Dynamic Levelwise PageRank (from STICD) : SHORT...
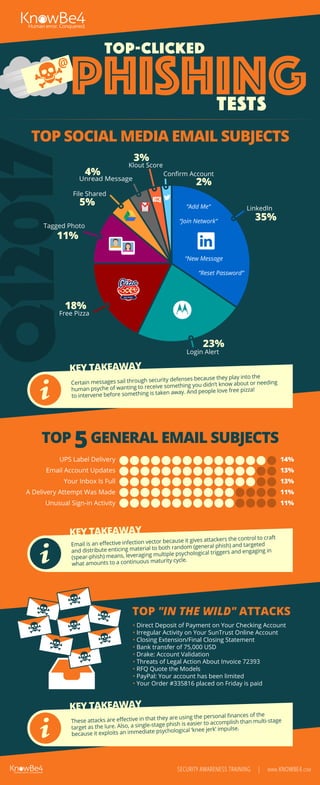
First Quarter 2017 Top-Clicked Phishing Tests [INFOGRAPHIC]
- 1. Q12017 TOP SOCIAL MEDIA EMAIL SUBJECTS TOP "IN THE WILD" ATTACKS • Direct Deposit of Payment on Your Checking Account • Irregular Activity on Your SunTrust Online Account • Closing Extension/Final Closing Statement • Bank transfer of 75,000 USD • Drake: Account Validation • Threats of Legal Action About Invoice 72393 • RFQ Quote the Models • PayPal: Your account has been limited • Your Order #335816 placed on Friday is paid SECURITY AWARENESS TRAINING | WWW.KNOWBE4.COM TOP 5GENERAL EMAIL SUBJECTS UPS Label Delivery Email Account Updates Your Inbox Is Full A Delivery Attempt Was Made Unusual Sign-in Activity 14% 13% 13% 11% 11% KEY TAKEAWAY These attacks are effective in that they are using the personal finances of the target as the lure. Also, a single-stage phish is easier to accomplish than multi-stage because it exploits an immediate psychological ‘knee jerk’ impulse. KEY TAKEAWAY Email is an effective infection vector because it gives attackers the control to craft and distribute enticing material to both random (general phish) and targeted (spear-phish) means, leveraging multiple psychological triggers and engaging in what amounts to a continuous maturity cycle. KEY TAKEAWAY Certain messages sail through security defenses because they play into the human psyche of wanting to receive something you didn’t know about or needing to intervene before something is taken away. And people love free pizza! LinkedIn 35% 23% 18% 11% 5% 4% 3% 2% “Add Me“ “Join Network“ “New Message “Reset Password“ Login Alert Free Pizza Tagged Photo File Shared Unread Message Klout Score Confirm Account Phishing Top-Clicked TESTS
