Embed presentation
Downloaded 31 times
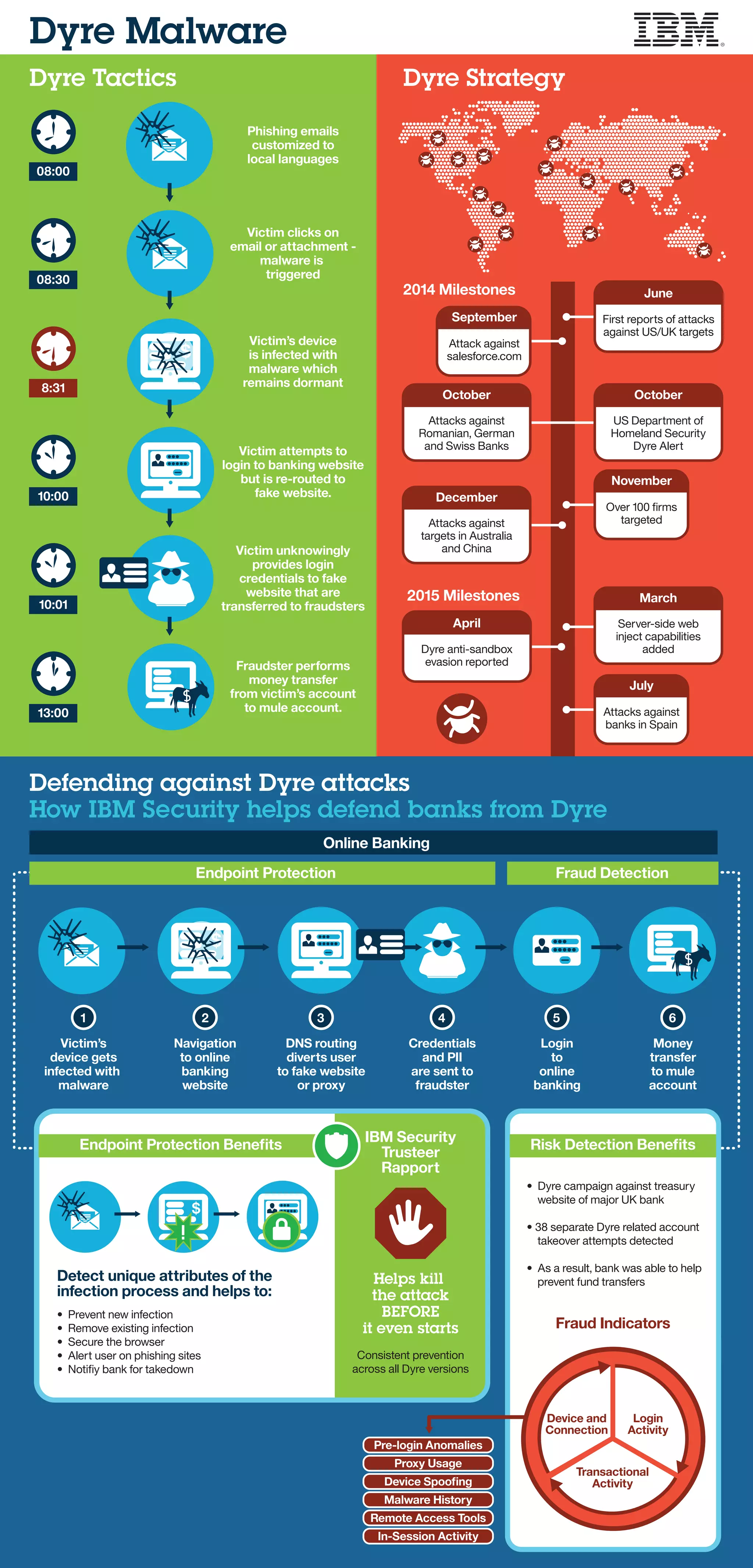

The document details the Dyre malware, outlining its infection process and tactics for targeting online banking users, including DNS routing to fake websites and money transfers to mule accounts. It describes how IBM Security's Trusteer Rapport provides endpoint protection by preventing infections, securing browsers, and alerting users to phishing attempts. The document also highlights the detection of numerous Dyre-related account takeover attempts against a major UK bank and ongoing attacks against financial institutions worldwide.
