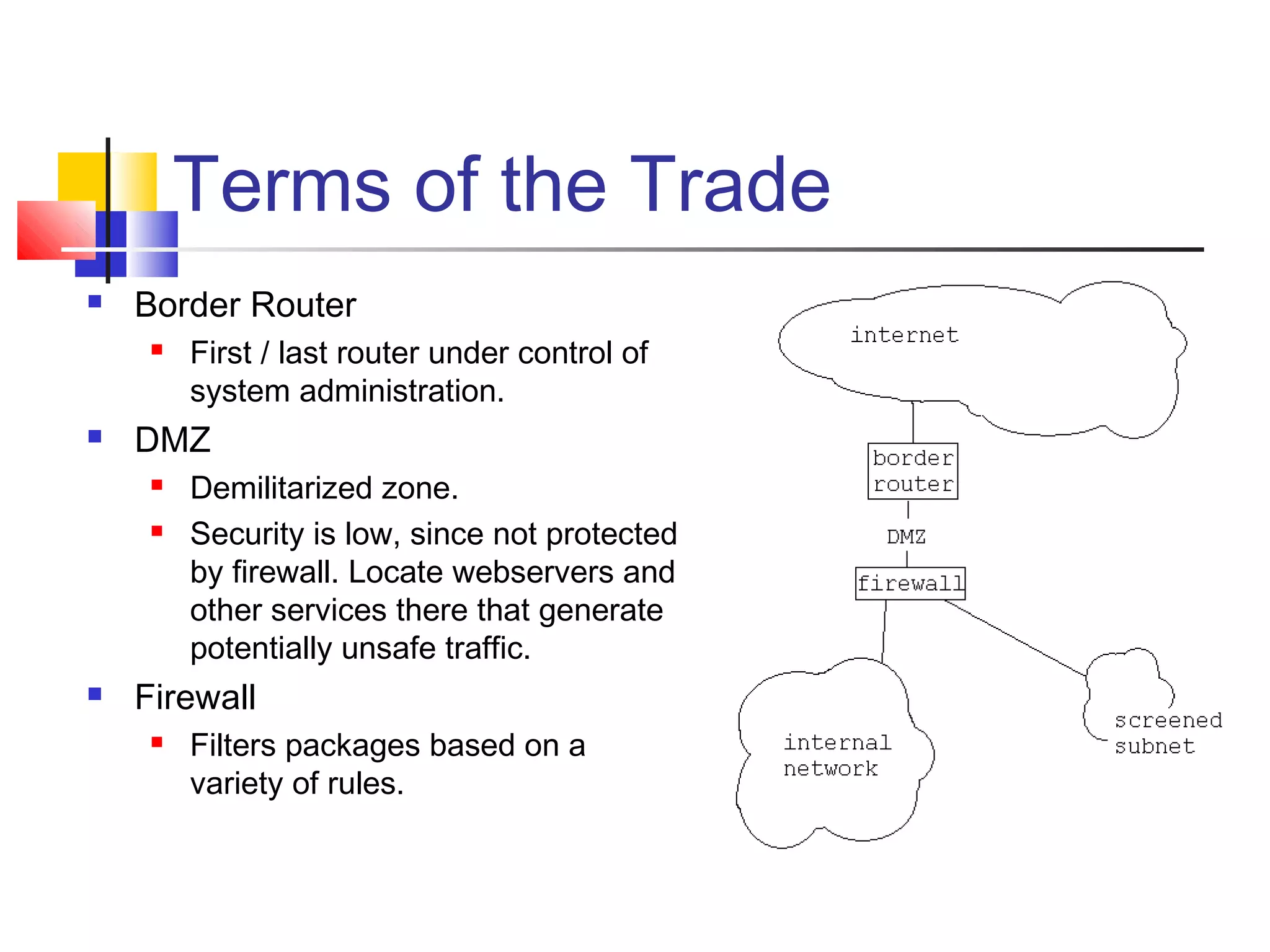
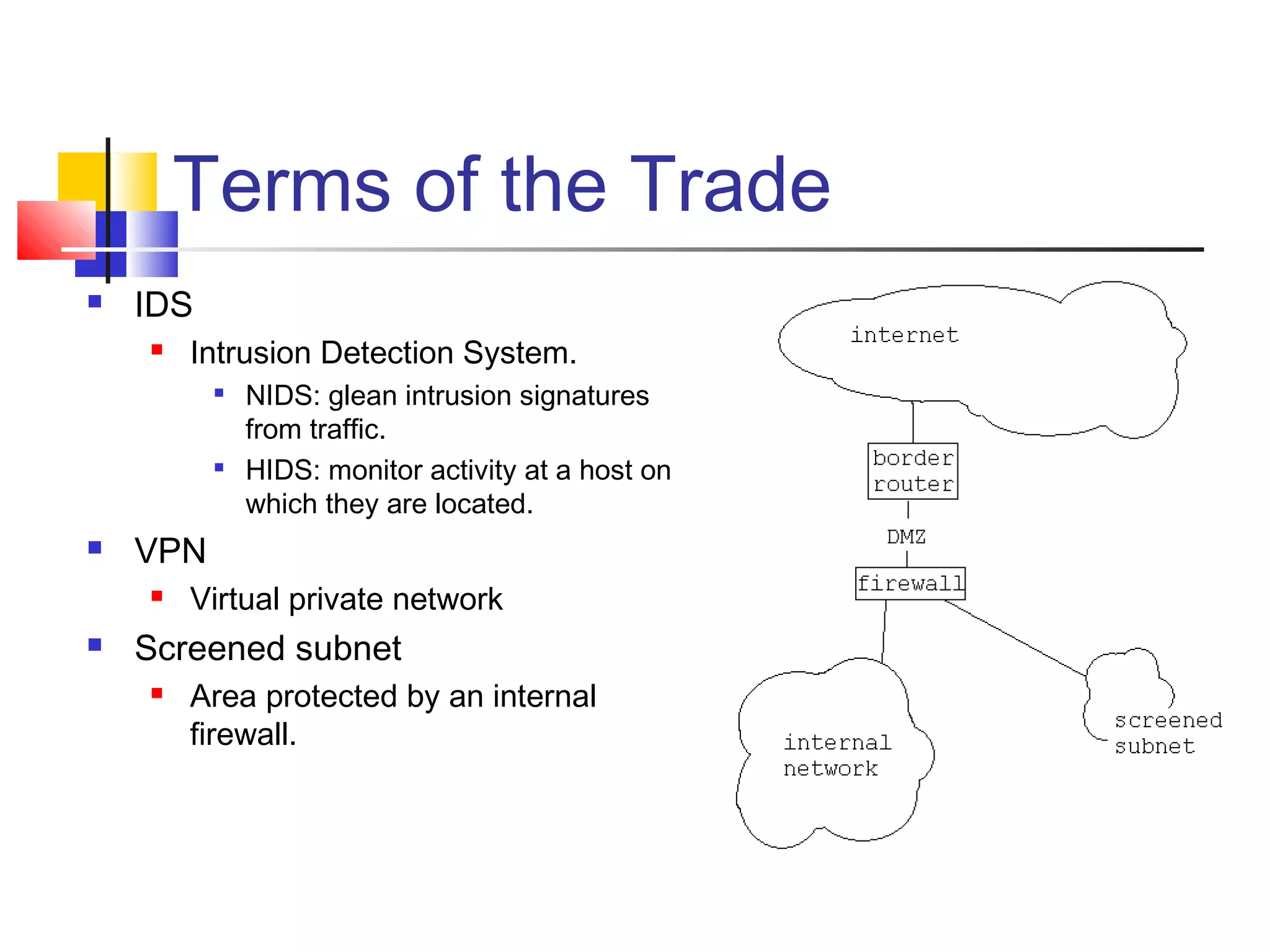
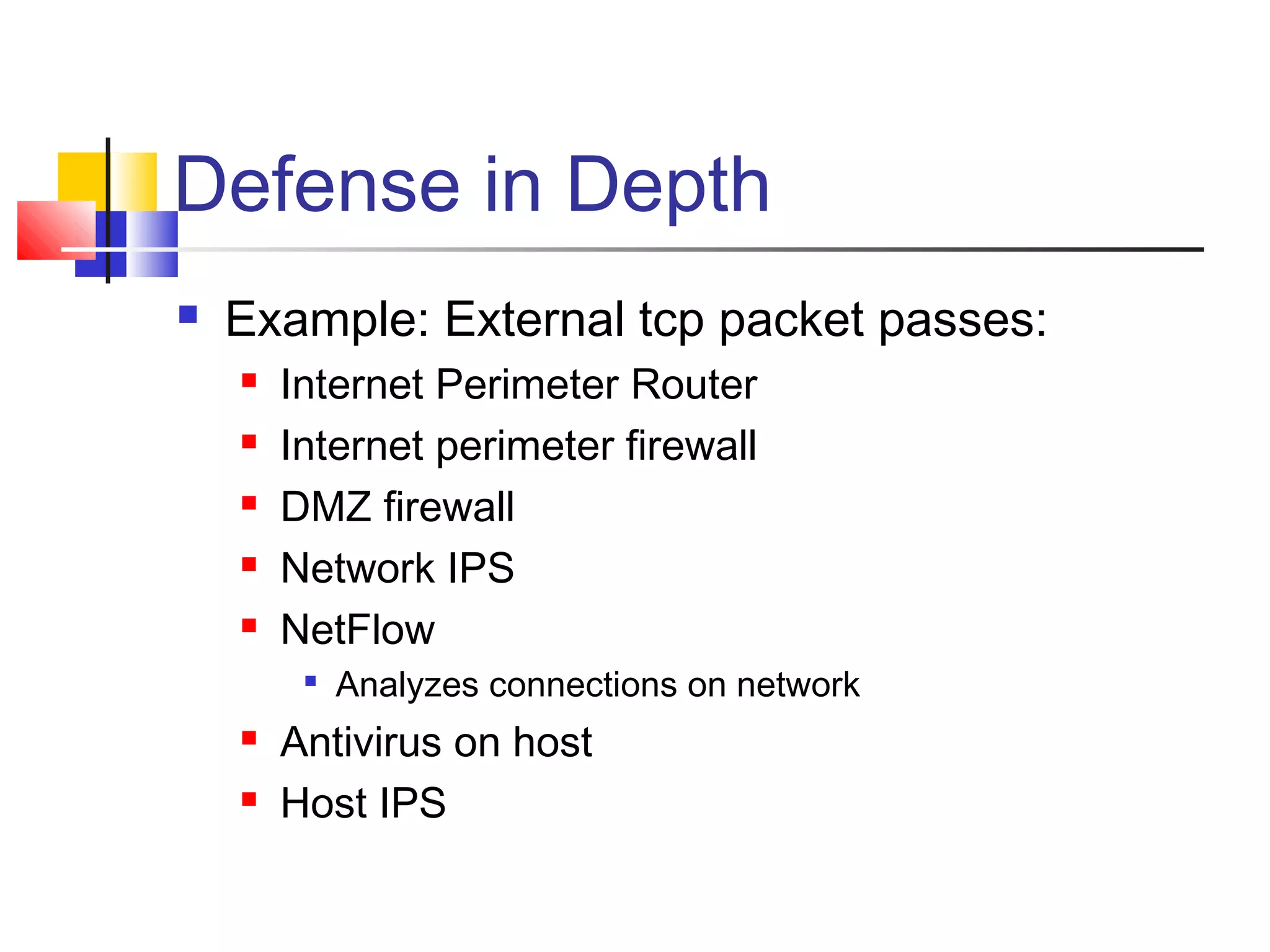
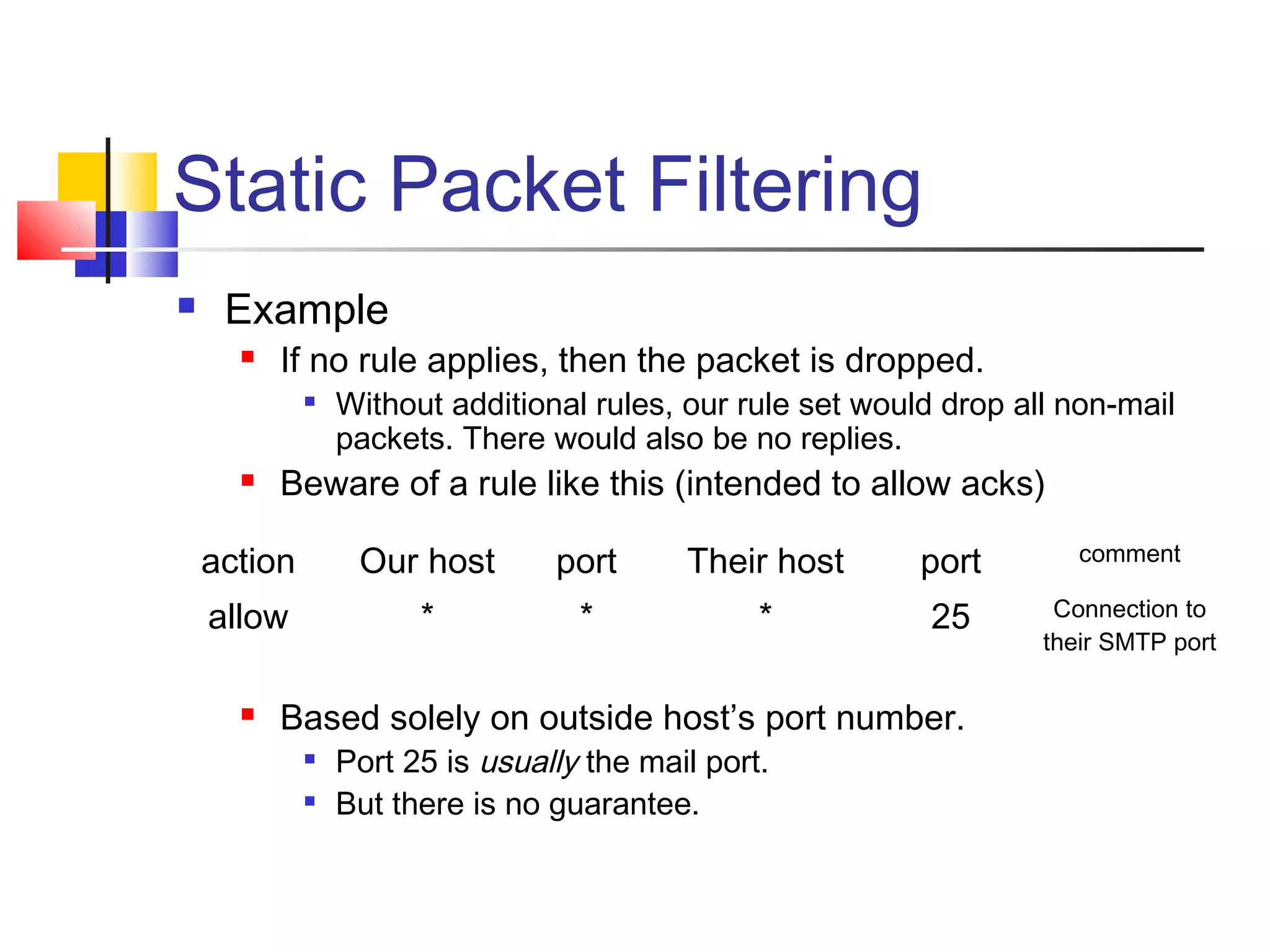
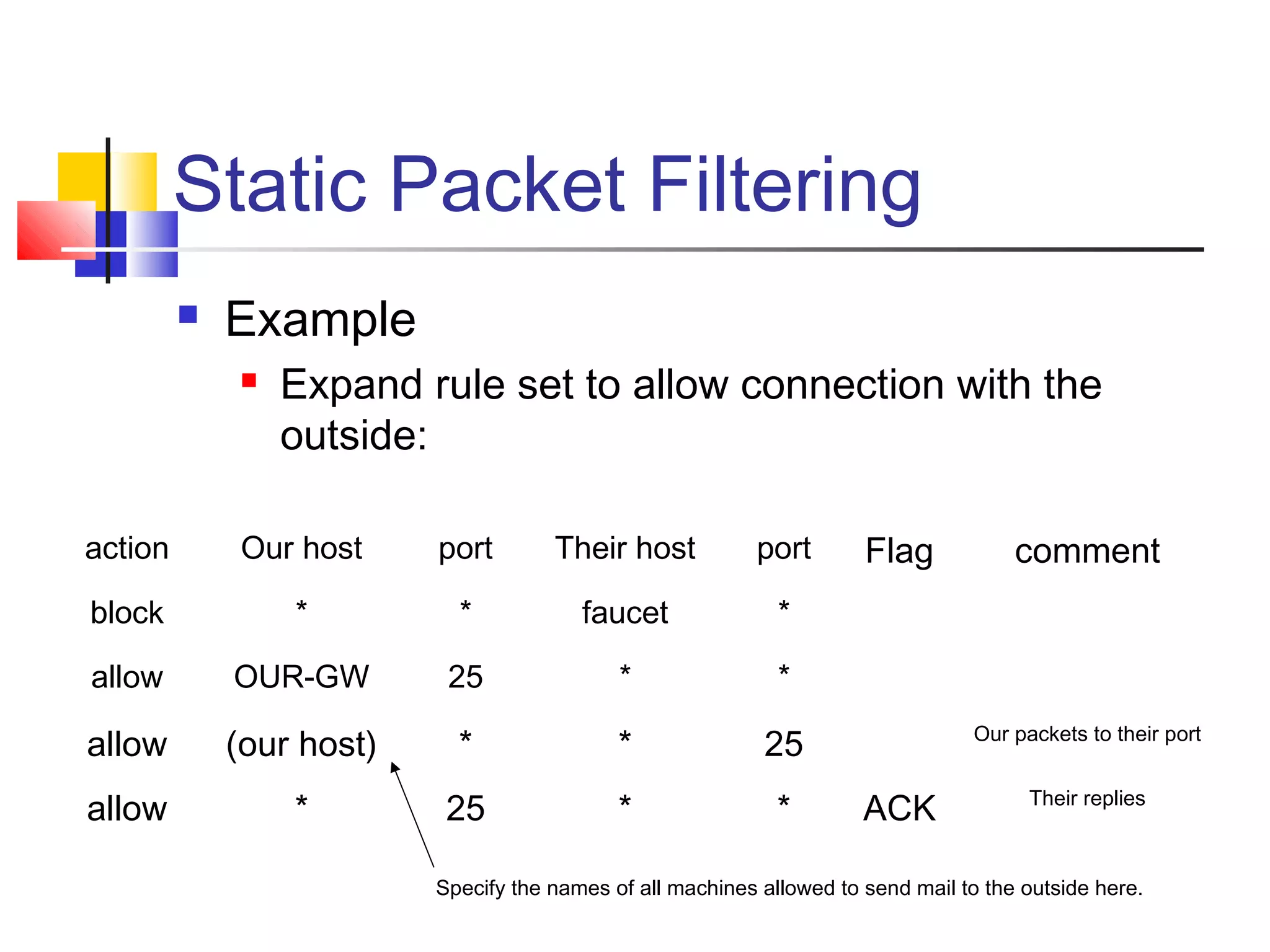
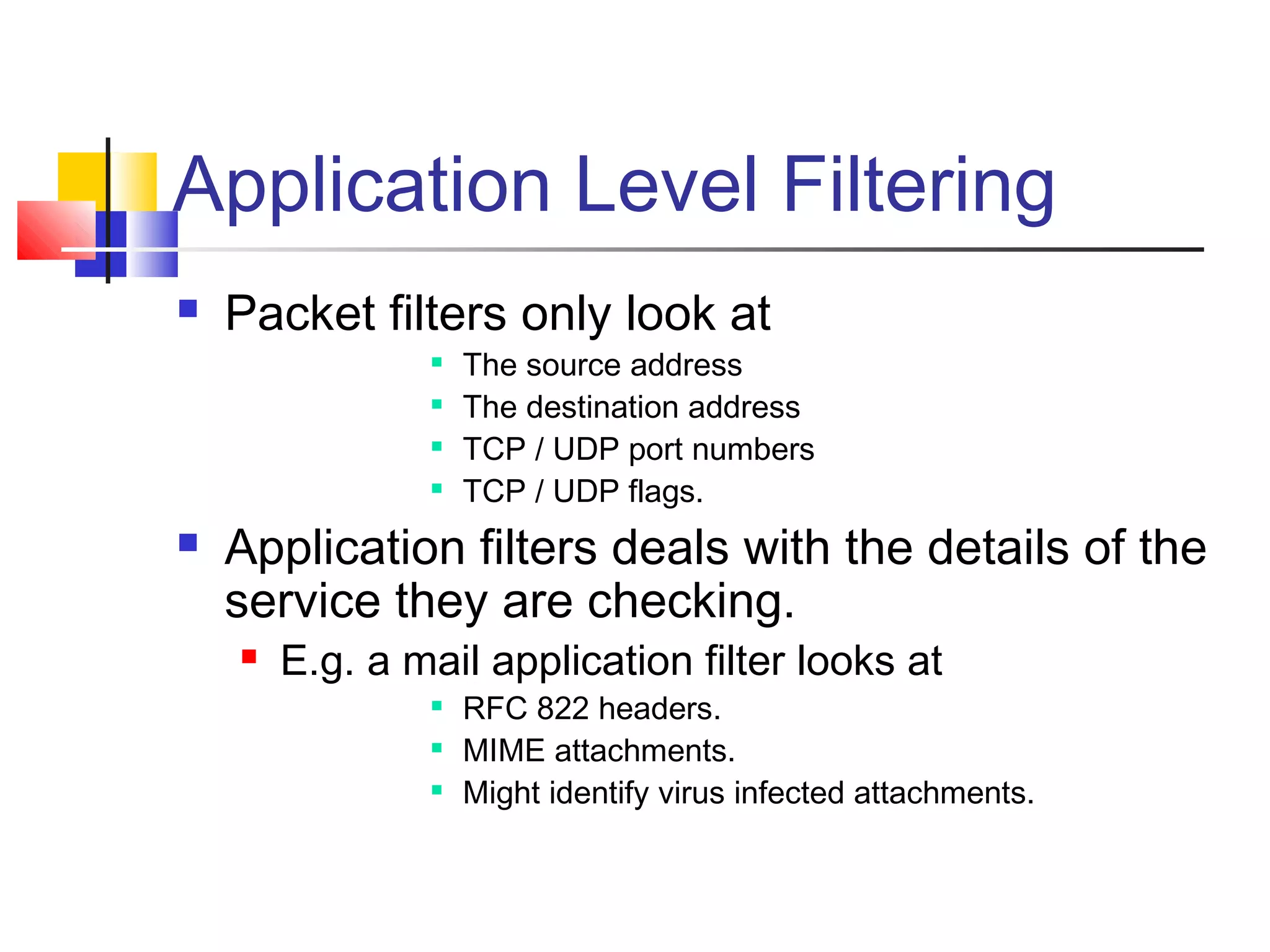
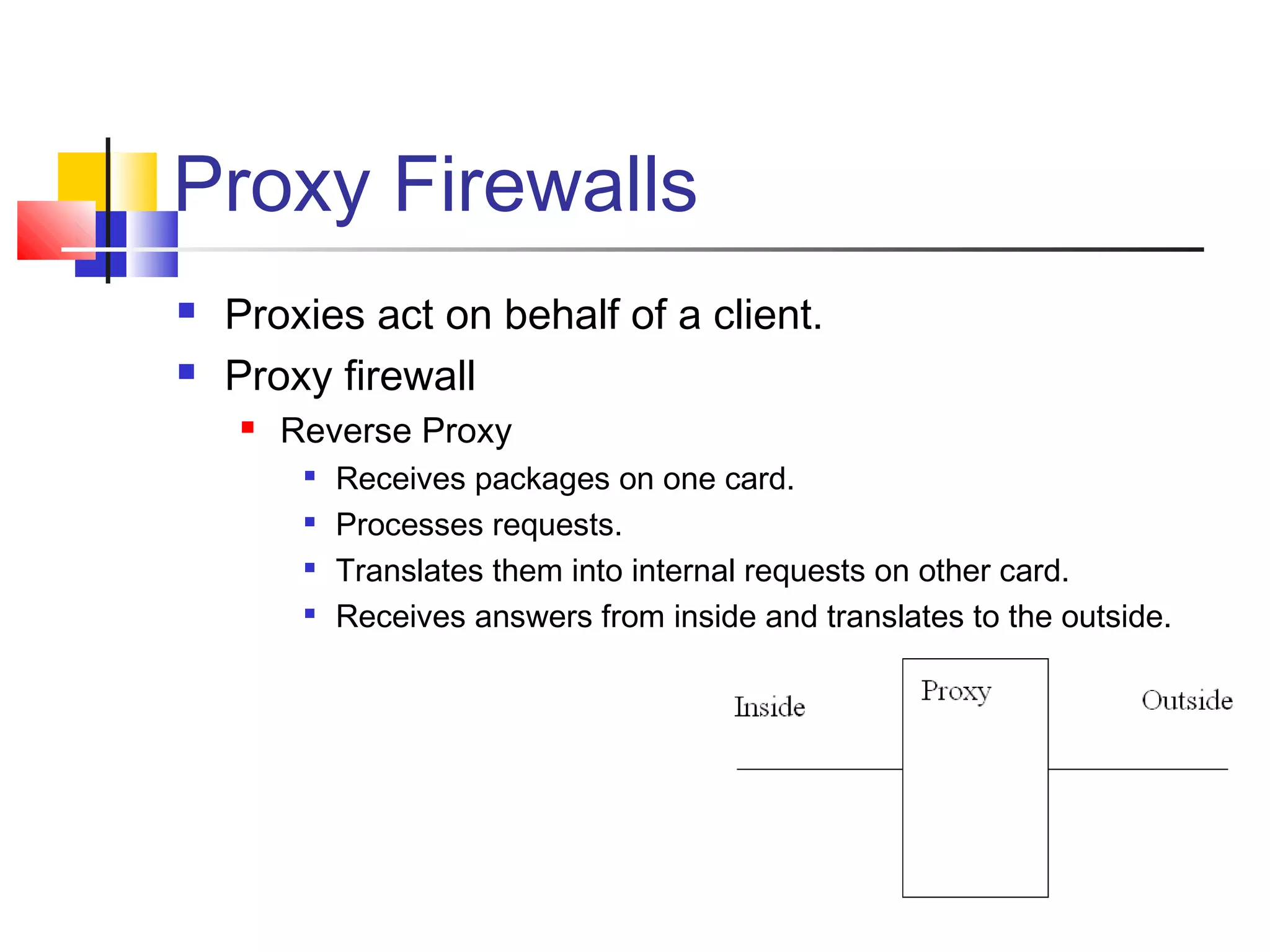
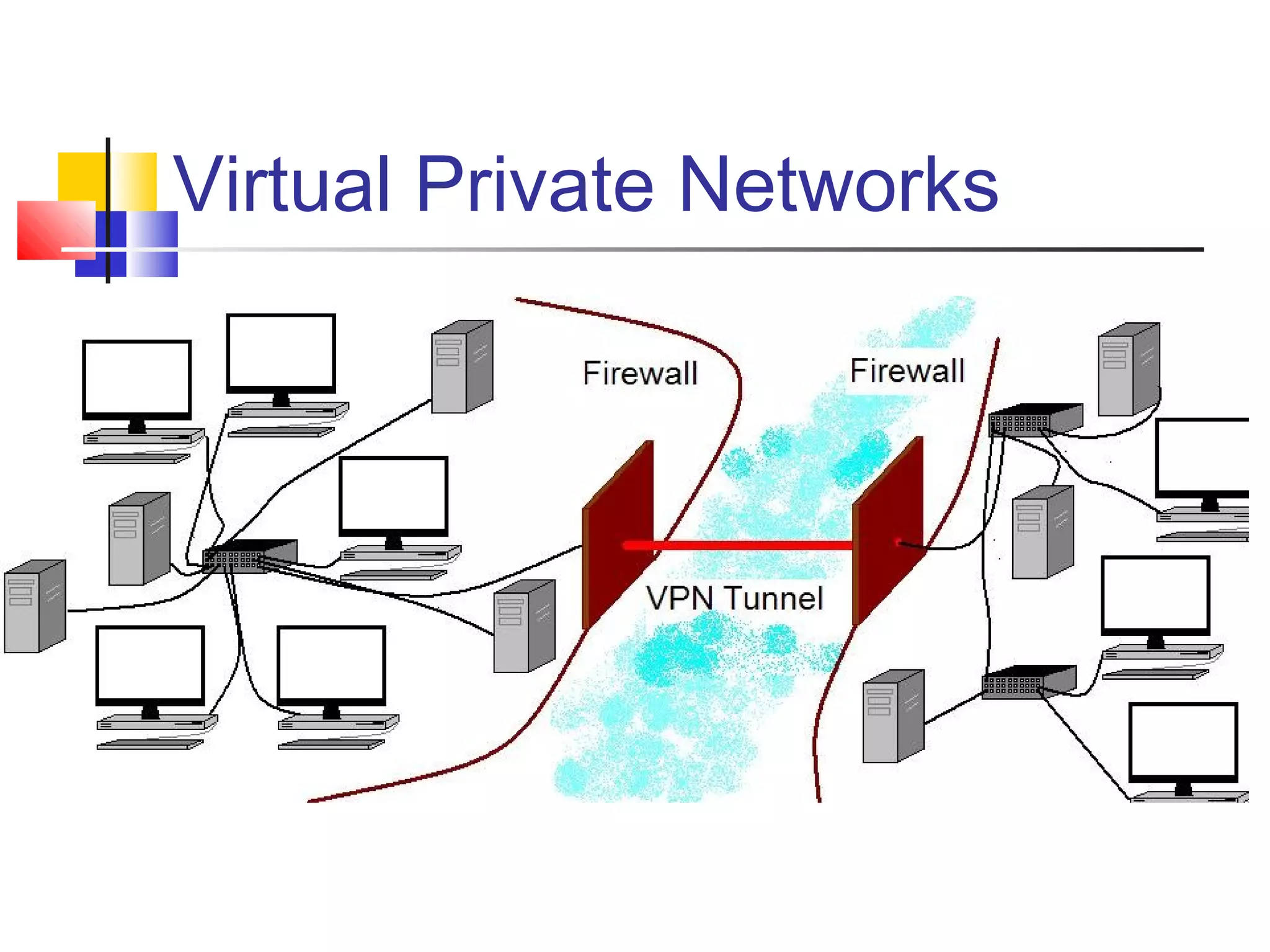
This document discusses key concepts related to network defense in depth. It defines common terms like firewalls, DMZs, IDS, and VPNs. It also covers techniques for packet filtering, application inspection, network address translation, and virtual private networks. The goal of defense in depth is to implement multiple layers of security and not rely on any single mechanism.