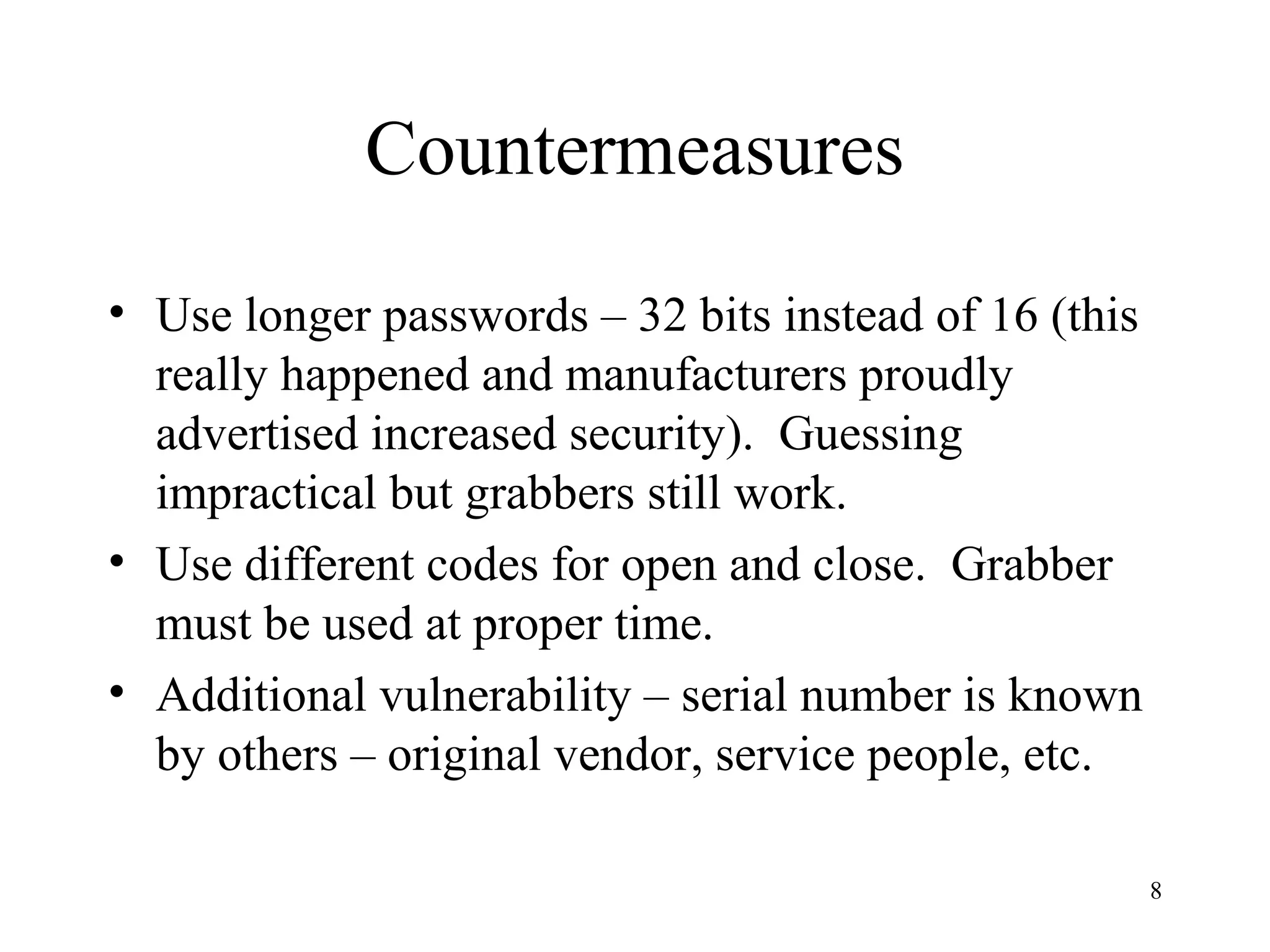
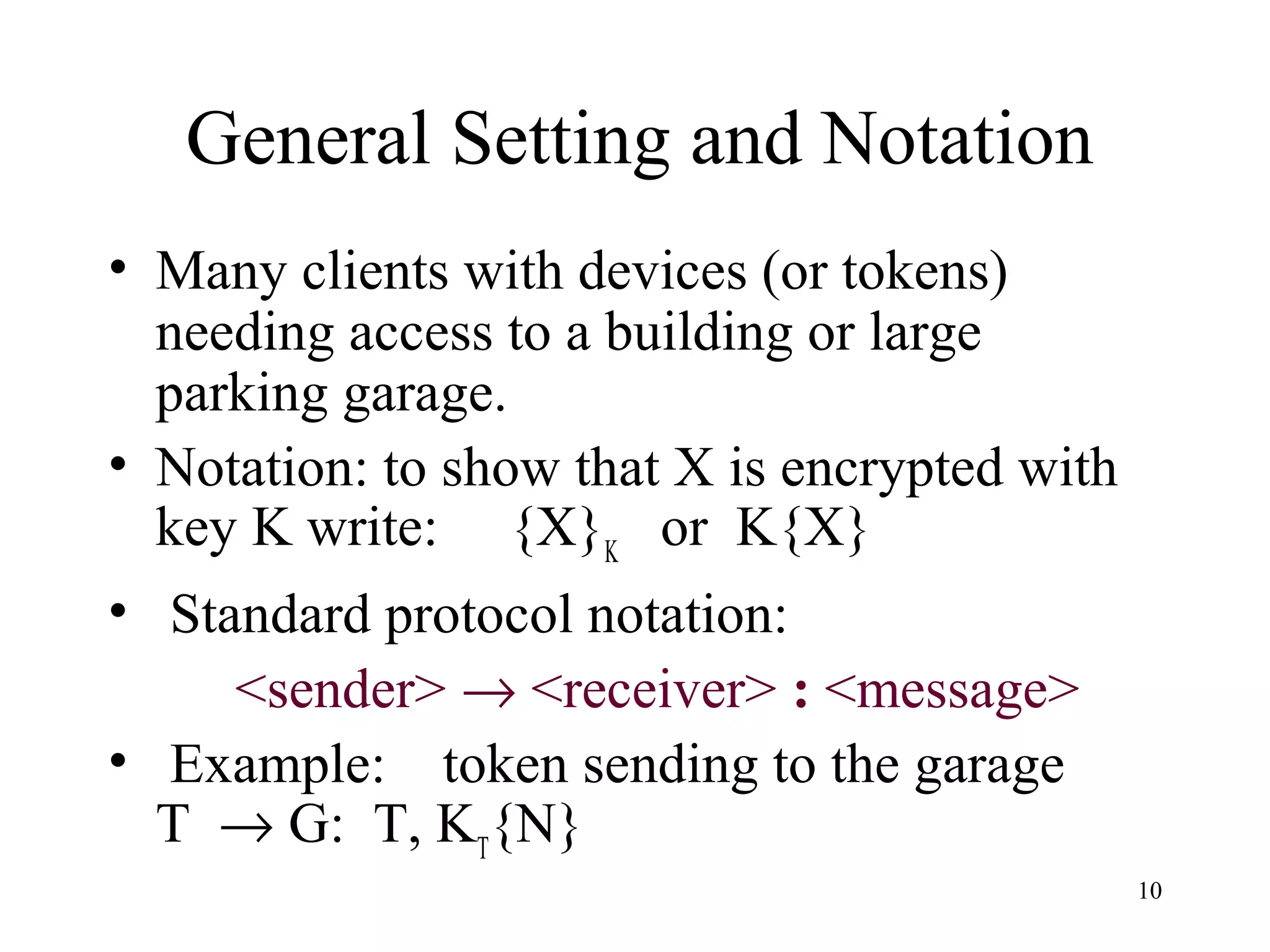
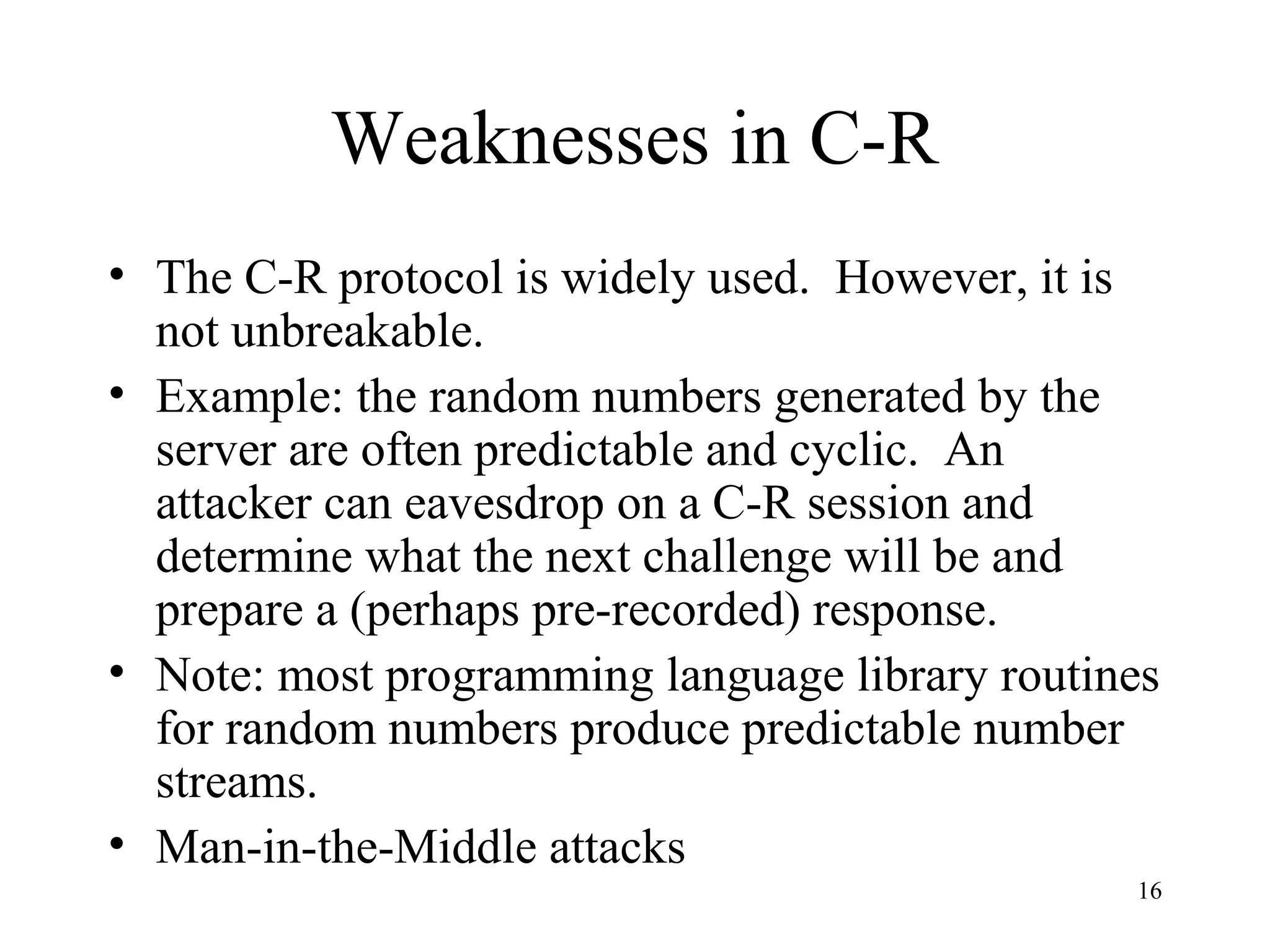
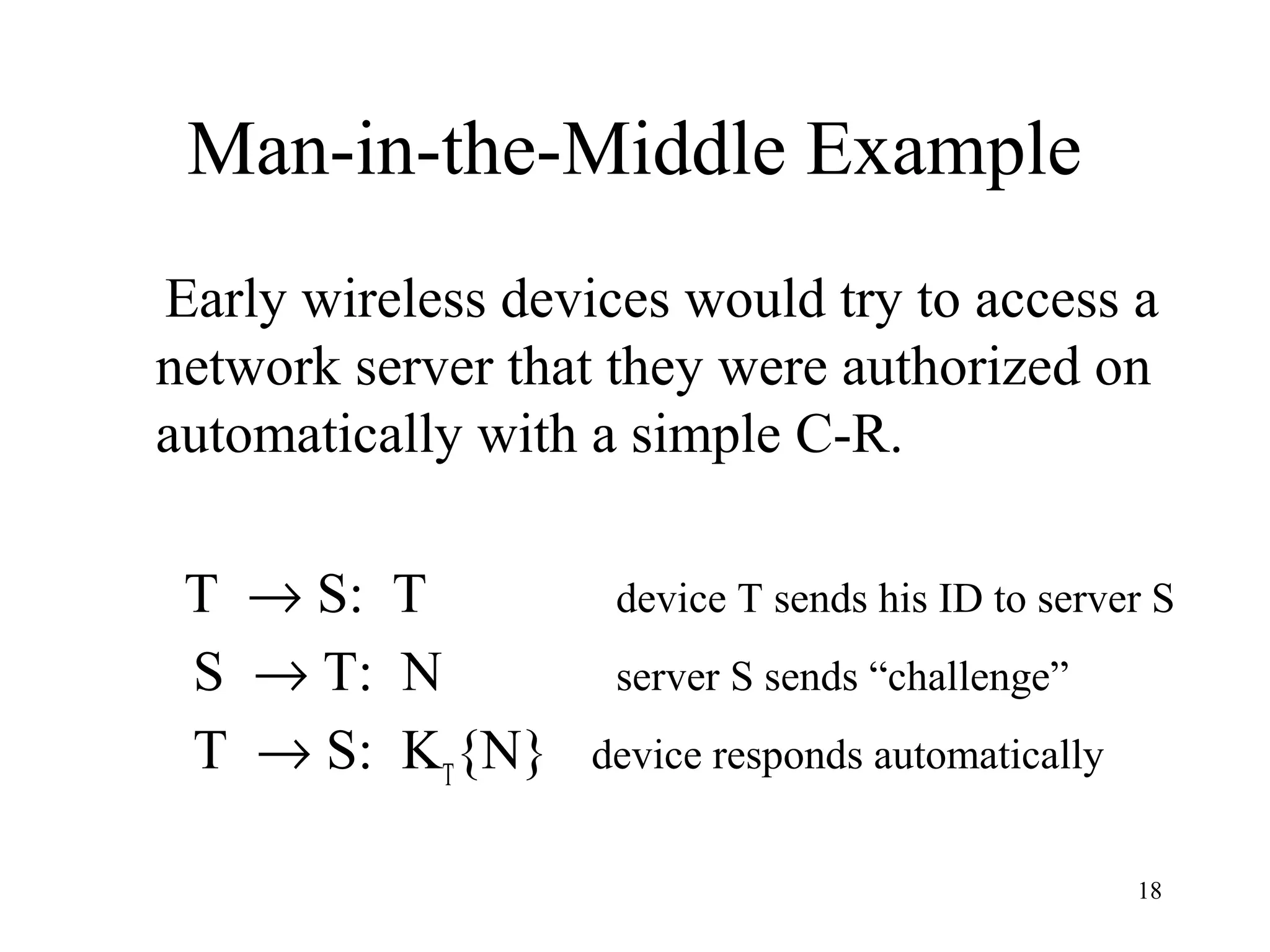
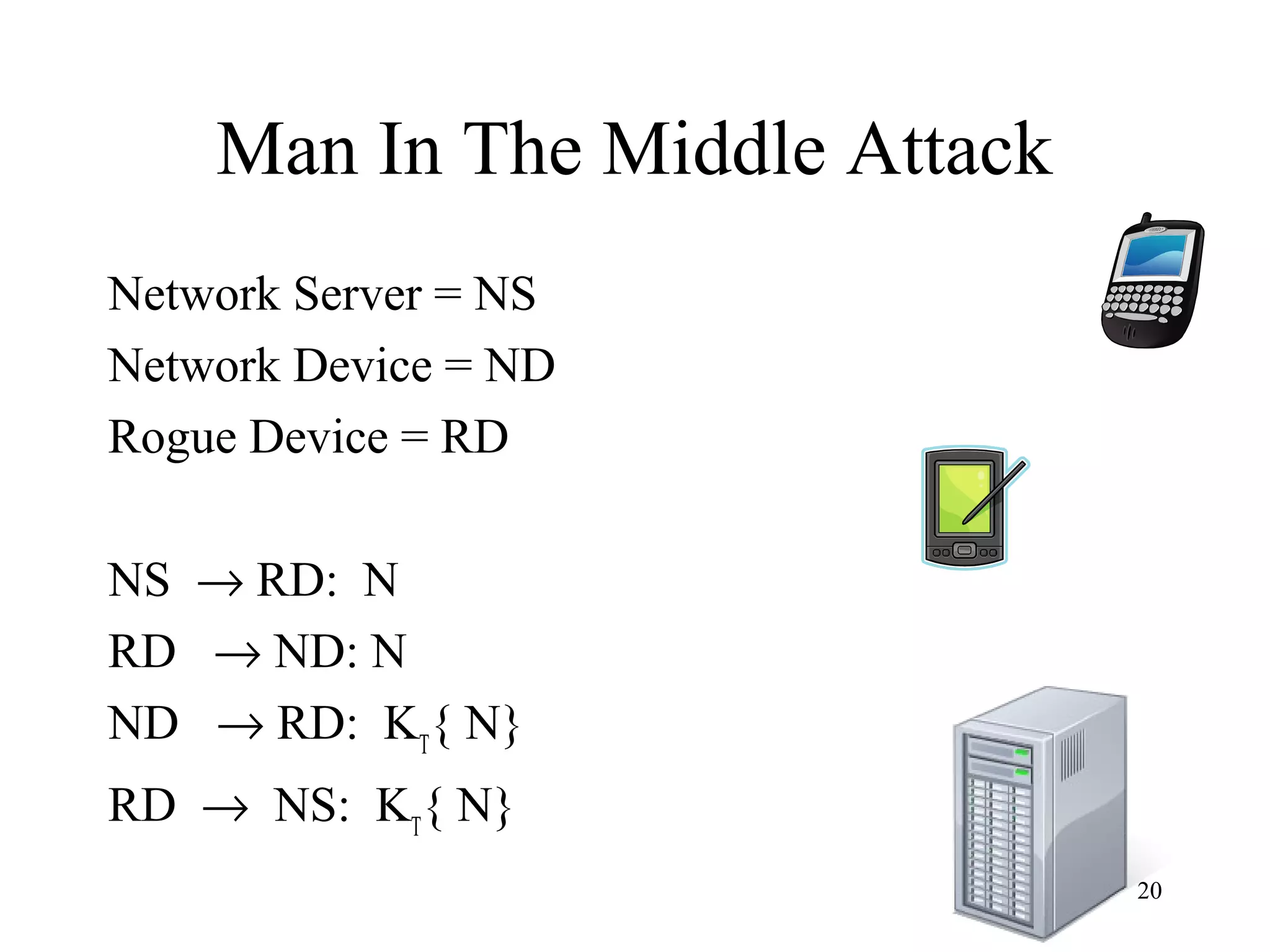
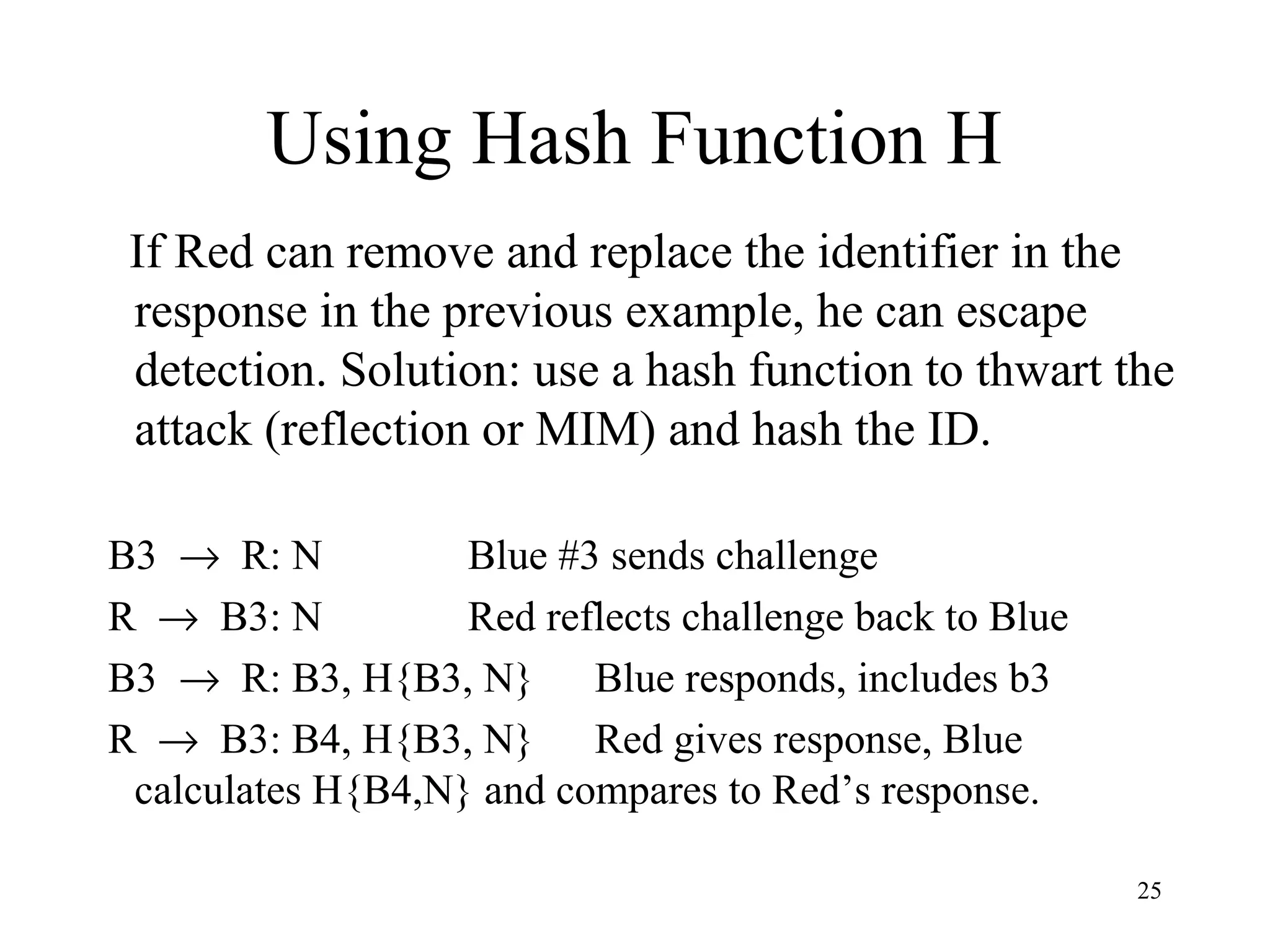
The document discusses authentication protocols for wireless devices. It begins by describing the authentication problem and some basic client-server protocols. It then introduces the challenge-response protocol which aims to prevent replay attacks by including a random number in the response. However, this protocol is still vulnerable to man-in-the-middle and reflection attacks. The document proposes improvements like including an identifier in the hashed response to prevent message manipulation attacks. Overall, the document provides an overview of authentication challenges for wireless devices and the development of challenge-response protocols to address these issues.