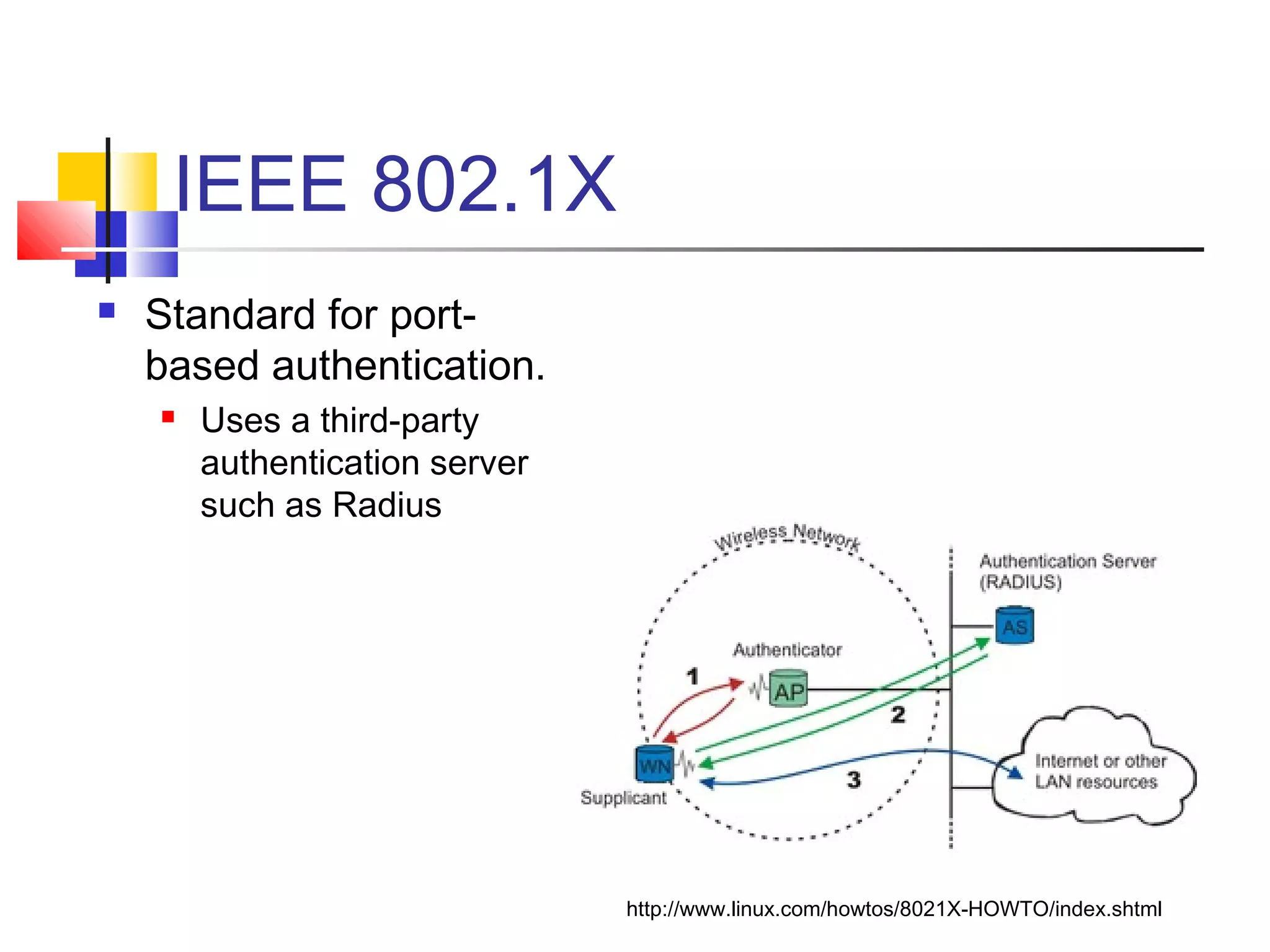
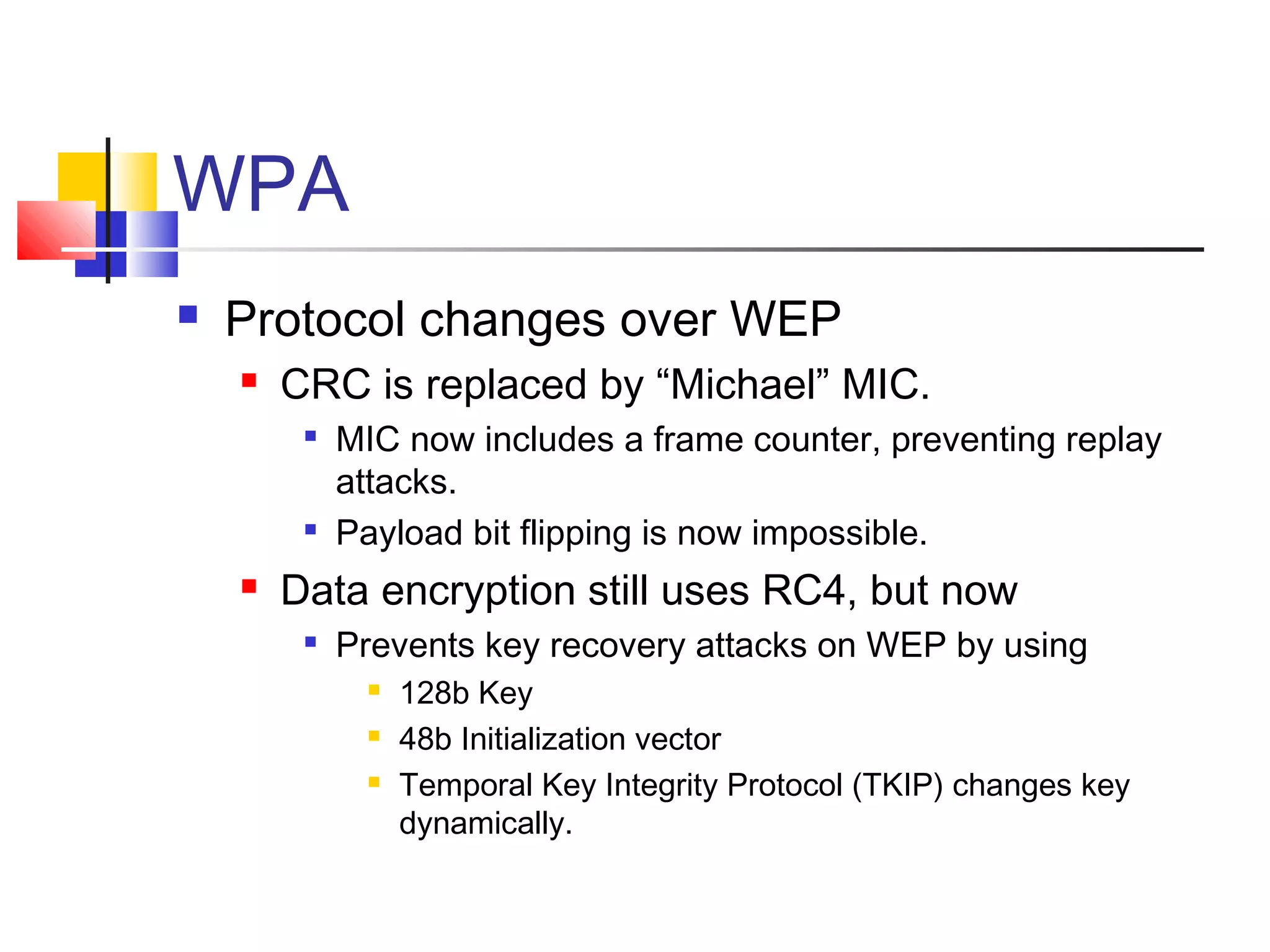
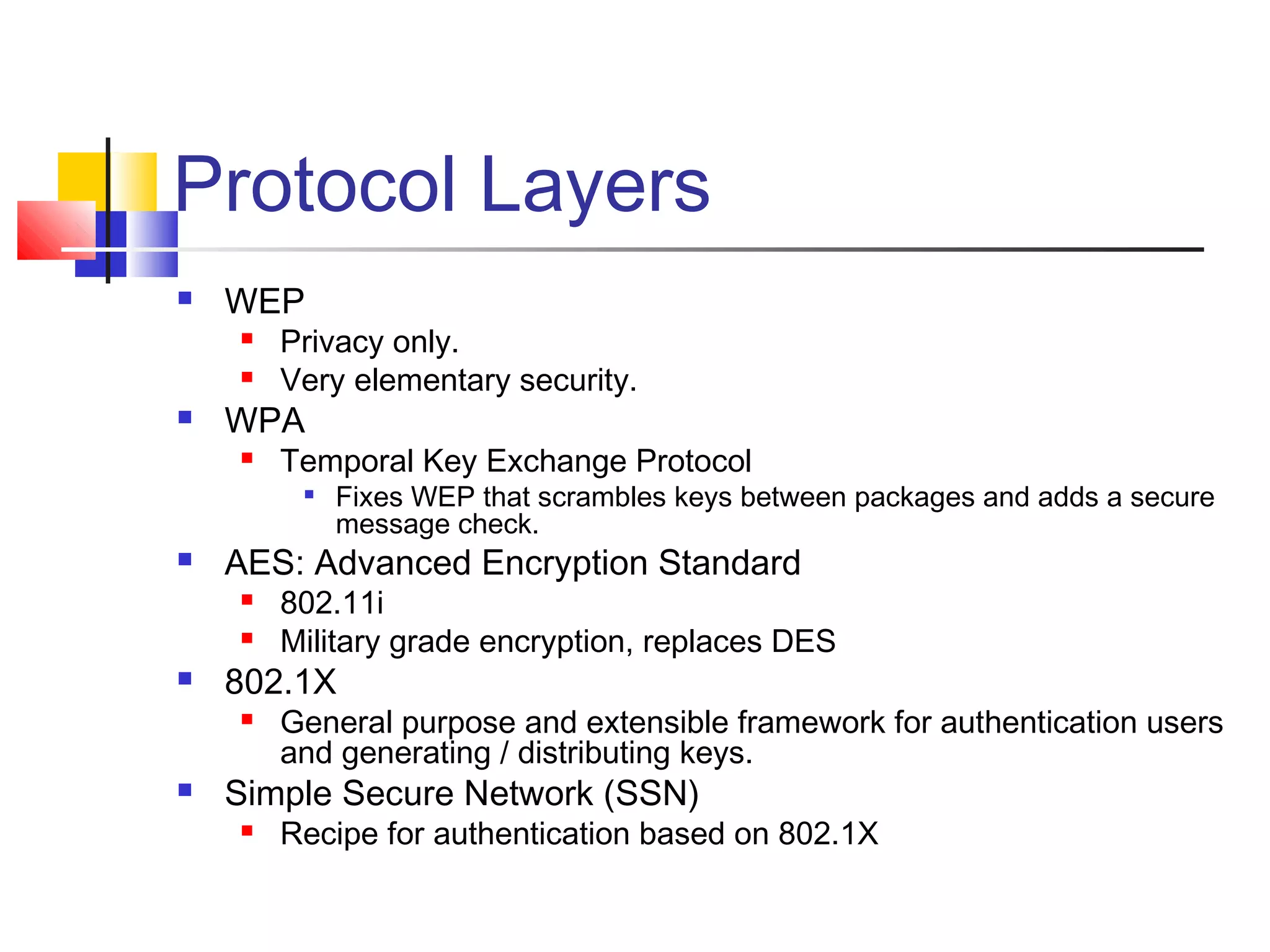
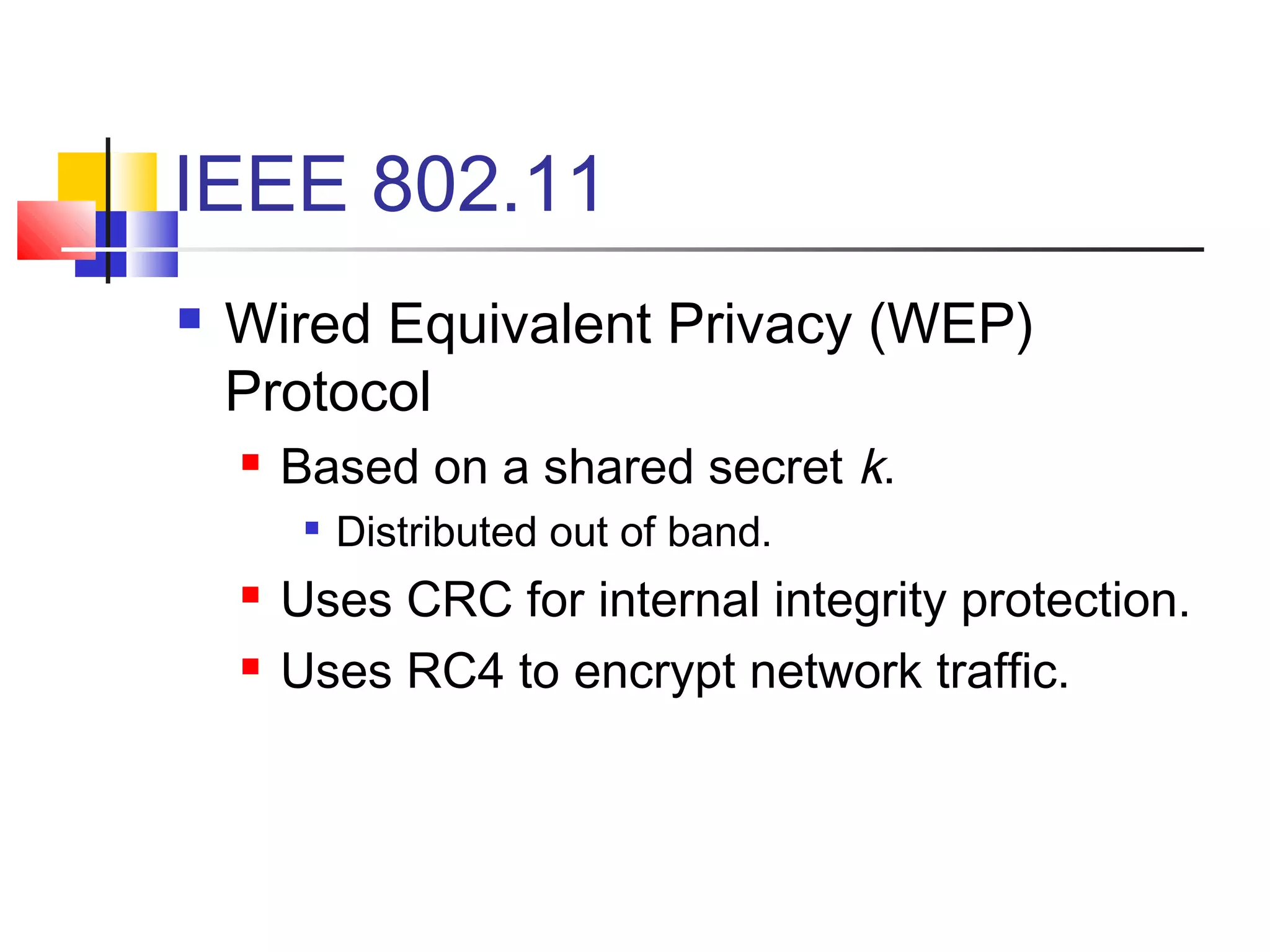
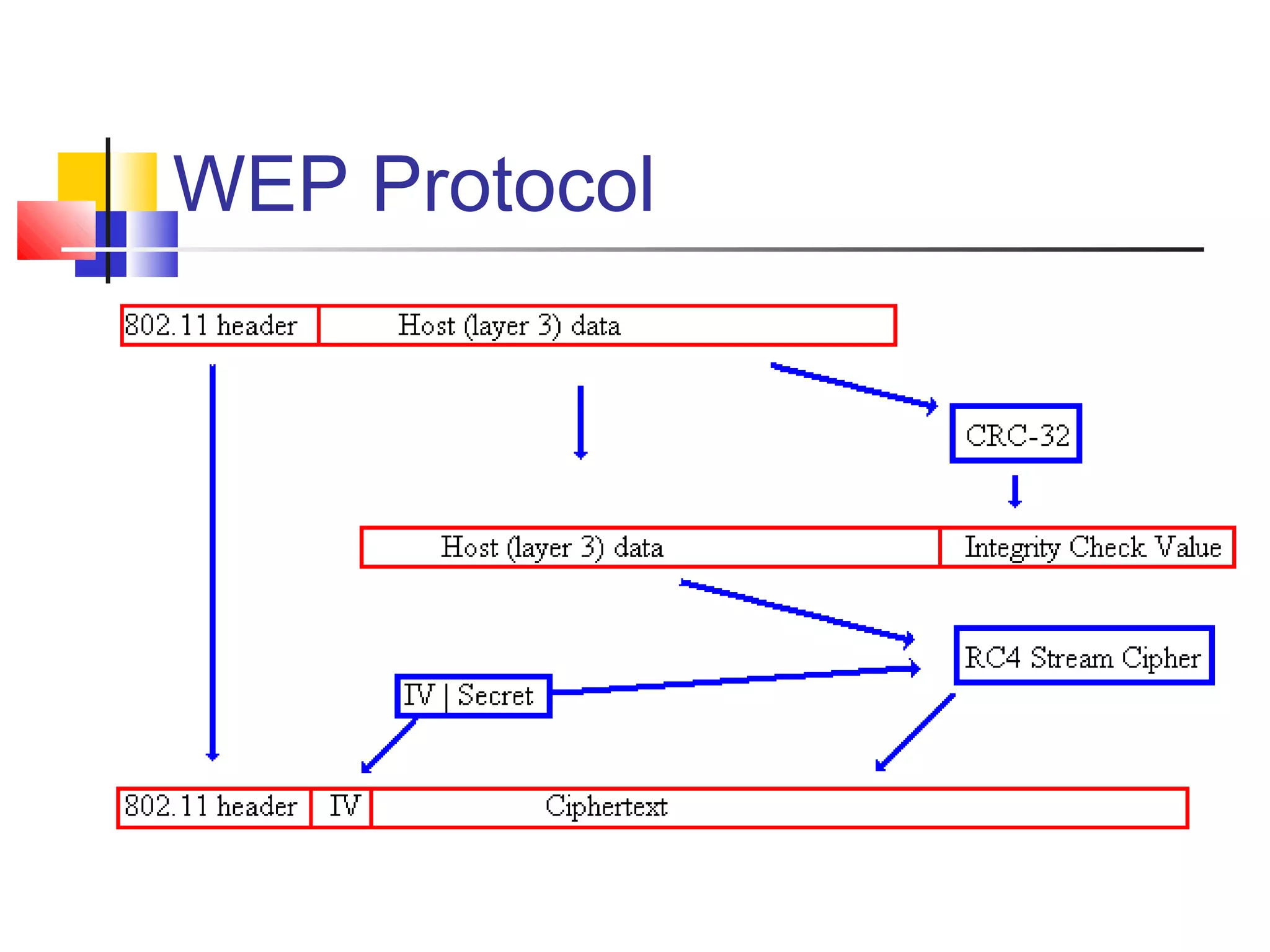
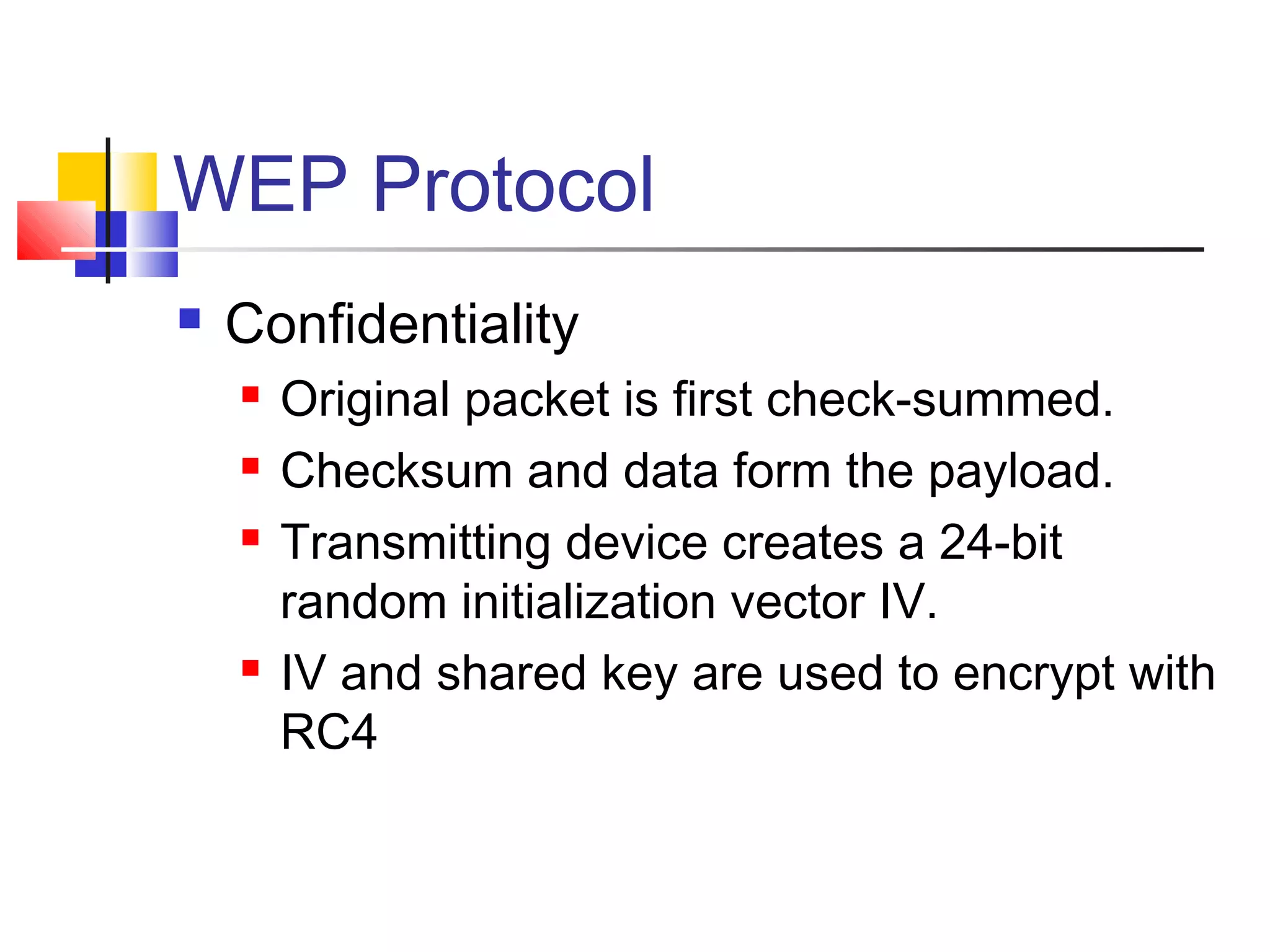
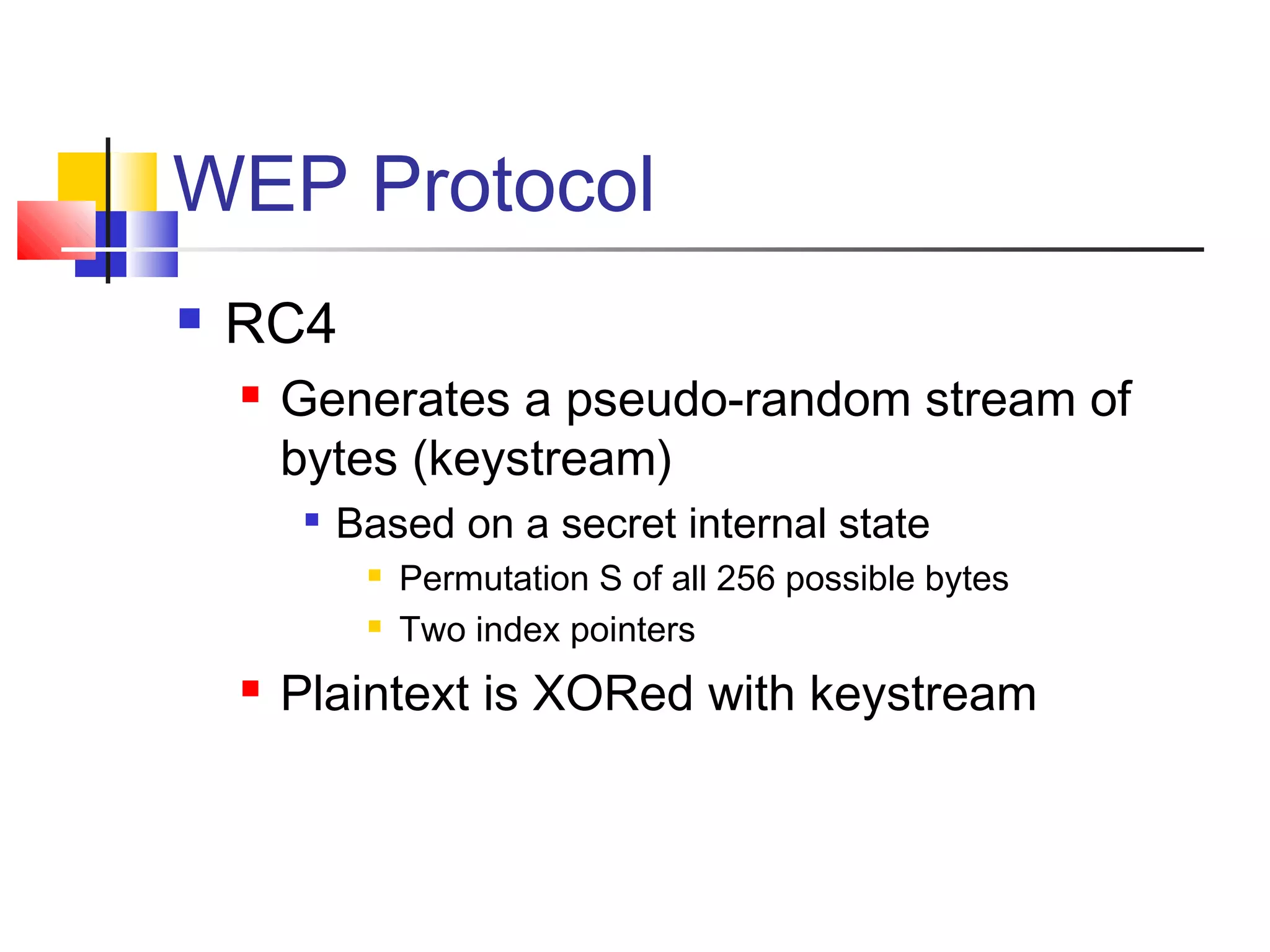
This document discusses wireless security and protocols such as WEP, WPA, and 802.11i. It describes weaknesses in WEP such as vulnerabilities in the RC4 encryption algorithm that allow attacks like dictionary attacks. It introduces WPA as an improvement over WEP that uses stronger encryption keys, protocols like TKIP that change keys dynamically, and AES encryption in 802.11i as stronger alternatives. It also discusses authentication methods like 802.1X that distribute unique keys to each user to address issues with shared keys in WEP.





![WEP Protocol
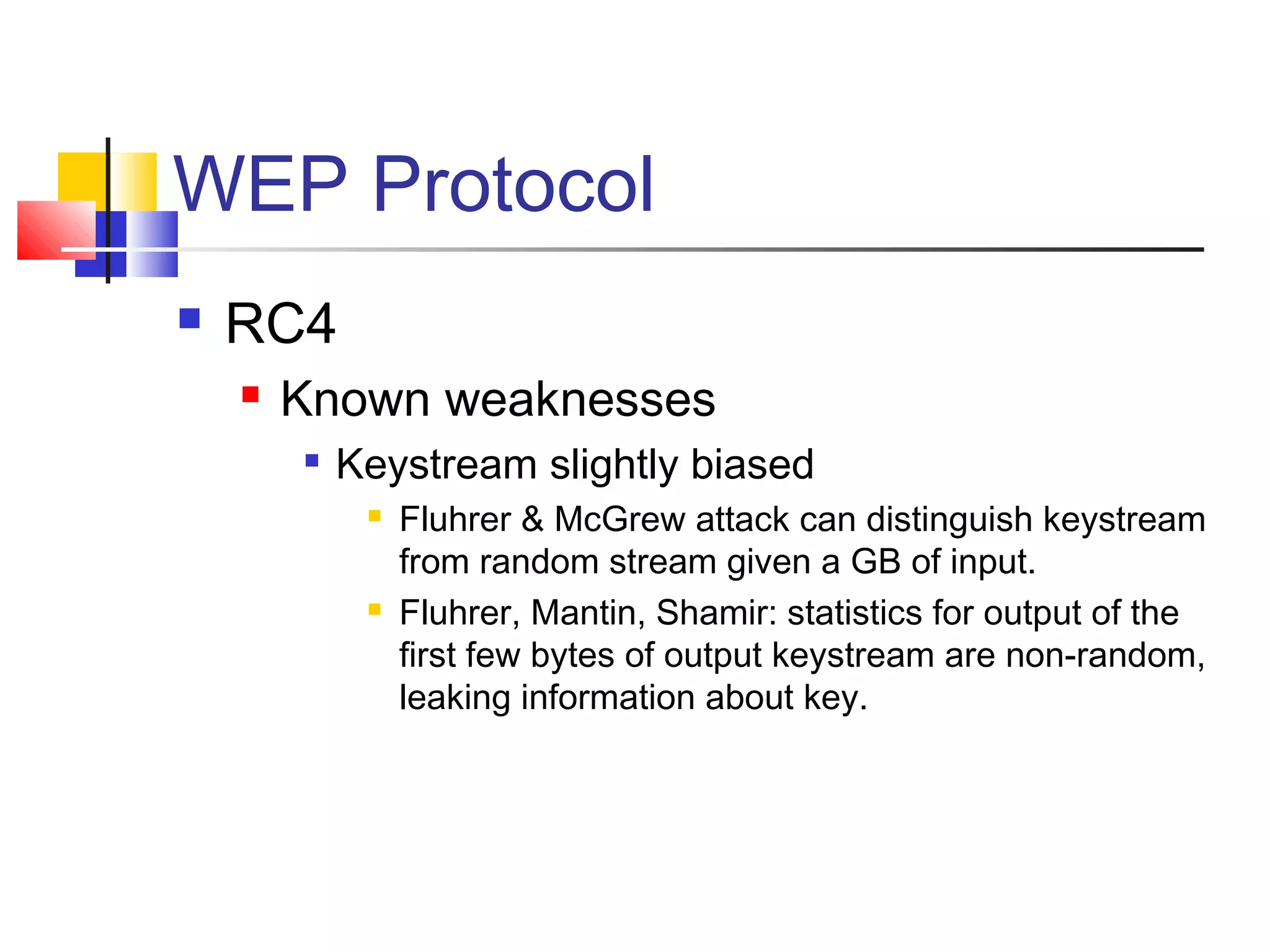
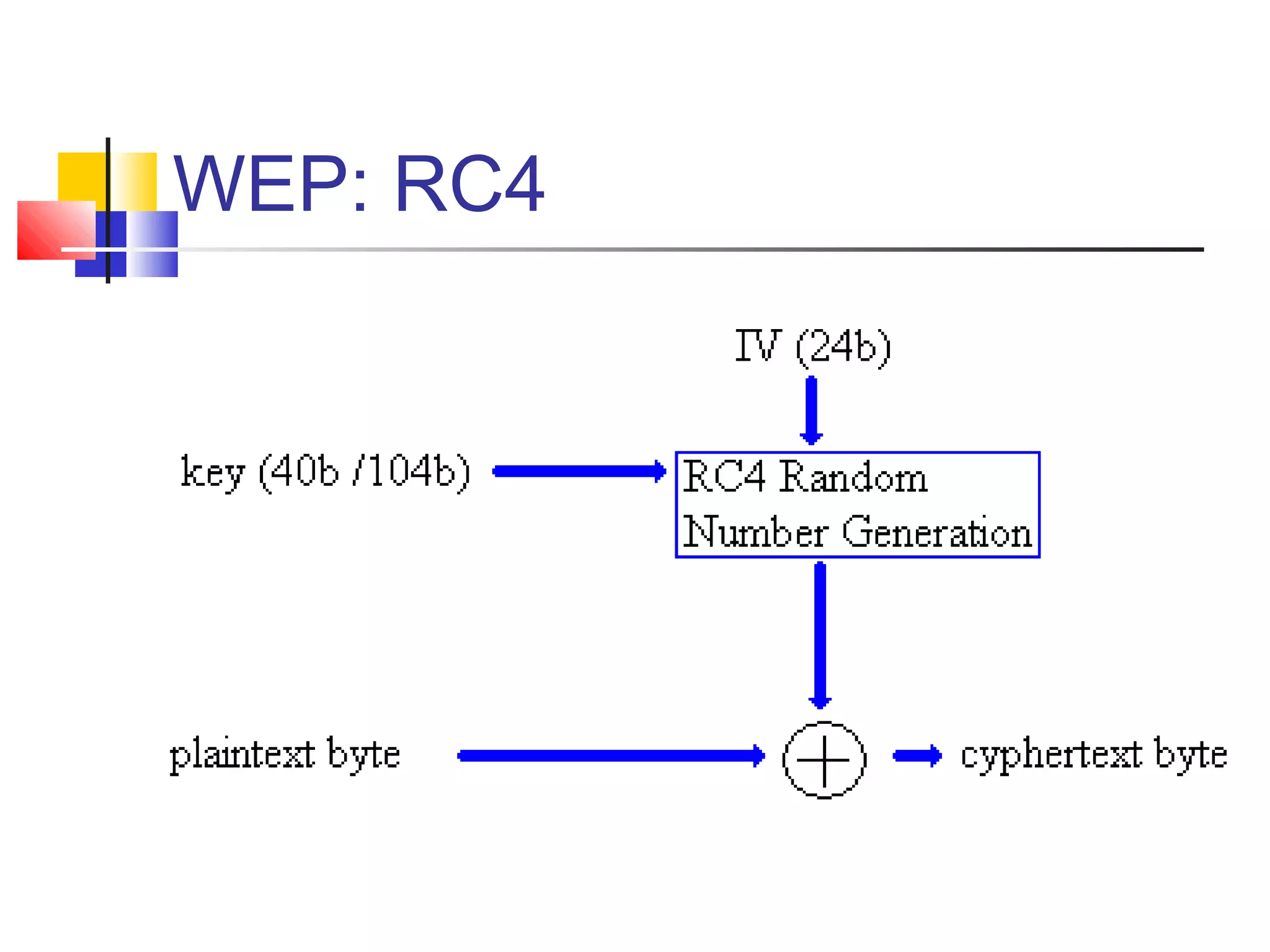
RC4
Key Scheduling Algorithm (KSA)
Initializes S based on a key
for i from 0 to 255
S[i] := i
j := 0
for i from 0 to 255
j := (j + S[i] + key[i mod keylength]) mod 256
swap(S[i],S[j])](https://image.slidesharecdn.com/mobile-150924020604-lva1-app6891/75/Mobile-Security-Wireless-hacking-10-2048.jpg)
![WEP Protocol
RC4
Pseudo-Random Generation Algorithm
(PRGA)
Generates pseudo-random byte stream
i := 0
j := 0
while GeneratingOutput:
i := (i + 1) mod 256
j := (j + S[i]) mod 256
swap(S[i],S[j])
output S[(S[i] + S[j]) mod 256]](https://image.slidesharecdn.com/mobile-150924020604-lva1-app6891/75/Mobile-Security-Wireless-hacking-11-2048.jpg)




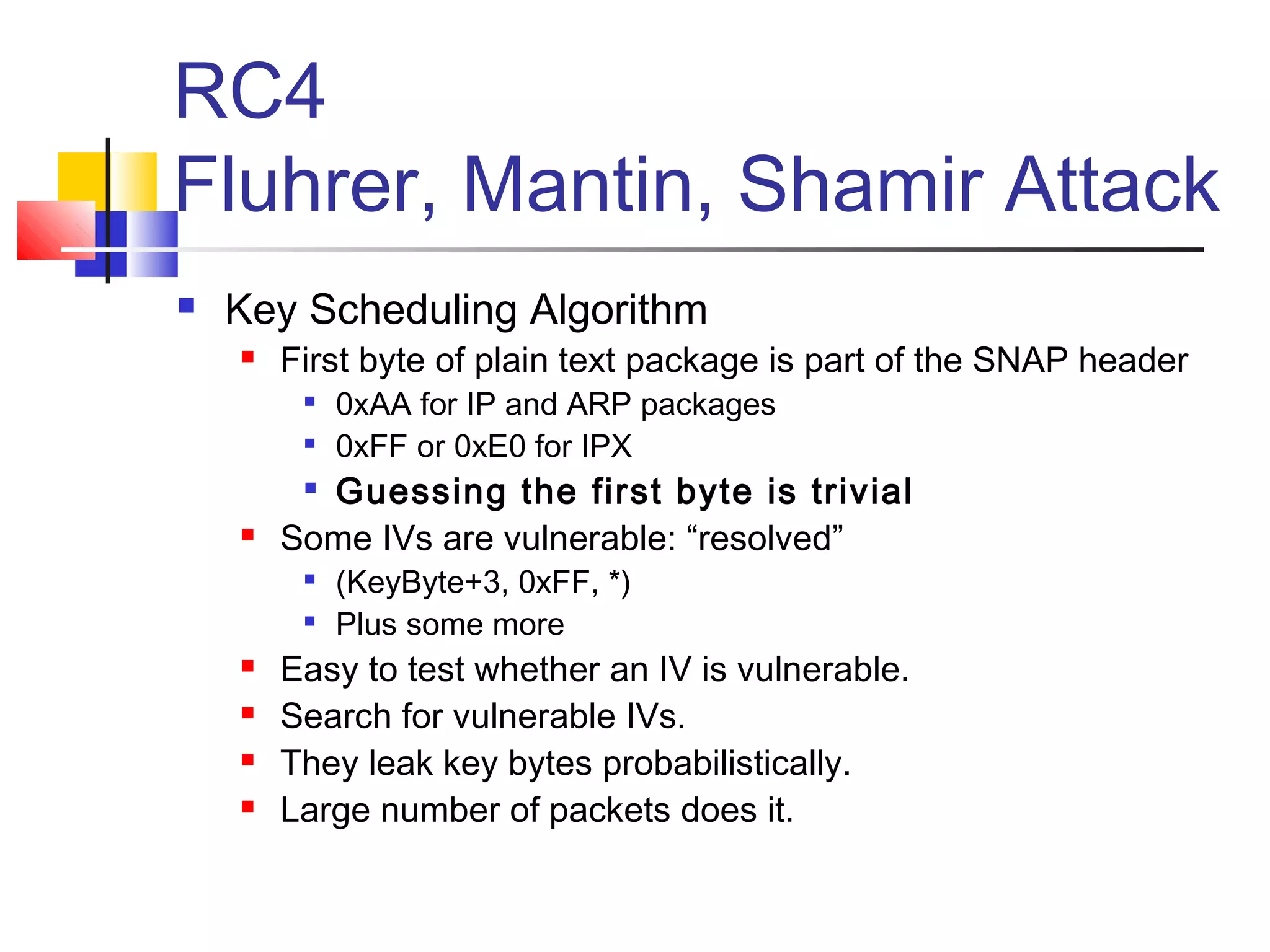
![RC4
Fluhrer, Mantin, Shamir Attack
Key Scheduling Algorithm
Sets up RC4 state array S
S is a permutation of 0, 1, … 255
Output generator uses S to create a
pseudo-random sequence.
First byte of output is given by
S[S[1]+S[S[1]]].
First byte depends on
{S[1], S[S[1], S[S[1]+S[S[1]]}](https://image.slidesharecdn.com/mobile-150924020604-lva1-app6891/75/Mobile-Security-Wireless-hacking-21-2048.jpg)