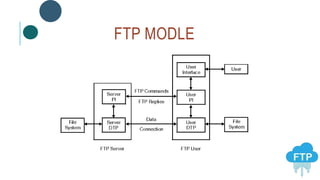
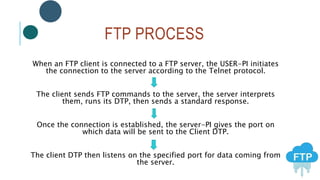
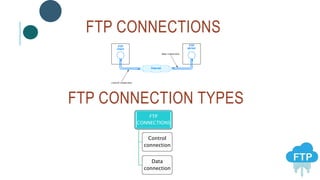
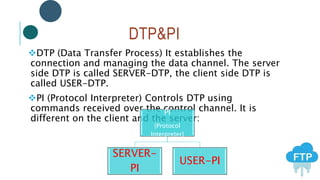
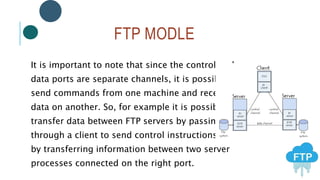
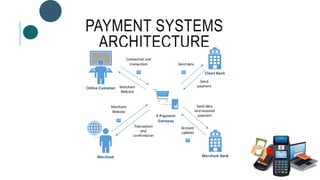
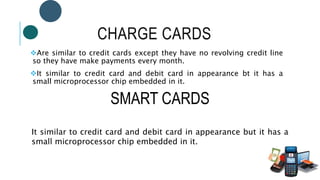
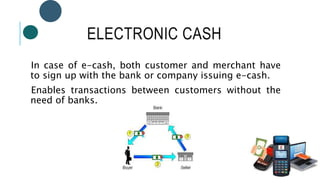
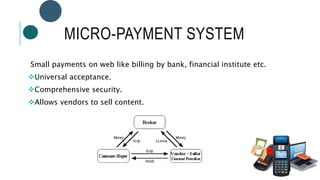
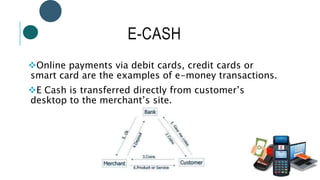
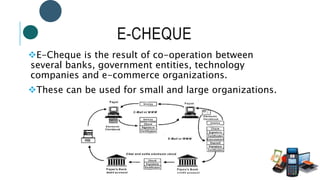
The document provides information about File Transfer Protocol (FTP). It discusses that FTP is a standard network protocol used to transfer files between clients and servers. FTP uses separate control and data connections, with the control connection managing commands and the data connection transferring files. The document outlines the FTP model, including the protocol interpreter and data transfer process on both the client and server sides. It also discusses FTP commands, connections types, clients, advantages and disadvantages.