The July 2024 Patch Tuesday webinar highlights the resolution of 142 unique CVEs, including two zero-day vulnerabilities affecting Windows OS and various browser updates required for Mozilla Firefox, Google Chrome, and Edge. Key vulnerabilities include important issues in Windows MSHTML and Hyper-V platforms, as well as remote code execution vulnerabilities in .NET and Visual Studio. Additionally, new Linux vulnerabilities were reported, with updates required for affected systems and critical updates announced for Microsoft products and SharePoint Server.














![Copyright © 2024 Ivanti. All rights reserved. 19
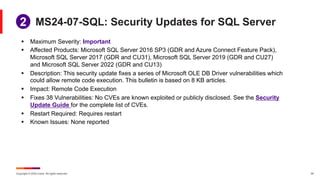
July Known Issues for Windows 11
§ KB 5040431 – Windows 11 version 21H2, all editions
§ [Prof_Pic] After installing this update, you might be unable to change your user account
profile picture. When attempting to change a profile picture by selecting the button Start>
Settings> Accounts > Your info, and then selecting Choose a file, you might receive an error
message with error code 0x80070520. Workaround: Microsoft is working on a resolution
§ KB 5040442 – Windows 11 version 22H2 and 23H2, all editions
§ [Ent_Up] After installing this update or later updates, you might face issues while upgrading
from Windows Pro to a valid Windows Enterprise subscription.
Resulting from this operation, you might observe the following symptoms: - OS upgrade
operations may fail, and this might be shown in the LicenseAcquisition scheduled task in
Task Scheduler -> Task Scheduler Library -> Microsoft -> Windows -> Subscription as
‘Access denied error (error code 0x80070005)’ under ‘Last Run Result’
• Workaround: Microsoft is working on a resolution.](https://image.slidesharecdn.com/itjuly2024patchtuesday-240711151454-e3d3291e/85/Patch-Tuesday-Italia-Luglio-19-320.jpg)

![Copyright © 2024 Ivanti. All rights reserved. 21
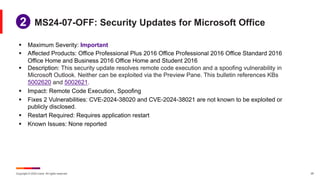
July Known Issues for Windows 10
§ KB 5040430 – Win 10 Enterprise LTSC 2019, Win 10 IoT Enterprise LTSC 2019, Windows 10
IoT Core 2019 LTSC, Windows Server 2019
§ [Language Change] After installing KB5039217, released June 11, 2024, you might
observe a change in language for context menus and dialog buttons in Windows
applications. Parts of the UI might display in English when English is not set as the
Windows display language. In addition, font size might change for the names of tabs and
buttons
§ Workaround: Microsoft is working on a resolution.](https://image.slidesharecdn.com/itjuly2024patchtuesday-240711151454-e3d3291e/85/Patch-Tuesday-Italia-Luglio-21-320.jpg)
![Copyright © 2024 Ivanti. All rights reserved. 22
July Known Issues for Windows 10 (cont)
§ KB 5040427 – Windows 10 Enterprise LTSC 2021, Windows 10 IoT Enterprise LTSC 2021,
Windows 10, version 22H2, all editions
§ [Cache] After you install KB5034203 (dated 01/23/2024) or later updates, some Windows
devices that use the DHCP Option 235 to discover Microsoft Connected Cache (MCC)
nodes in their network might be unable to use those nodes. Instead, these Windows
devices will download updates and apps from the public internet. Workaround: See KB for
configuration options.
§ [Prof_Pic]
§ Microsoft is working on a resolution for both issues.
§ KB 5040437 – Windows Server 2022
§ [Prof_Pic]](https://image.slidesharecdn.com/itjuly2024patchtuesday-240711151454-e3d3291e/85/Patch-Tuesday-Italia-Luglio-22-320.jpg)