When it comes to securing your cloud environment, choosing the right access control model is crucial. Here’s a quick look at the top options:
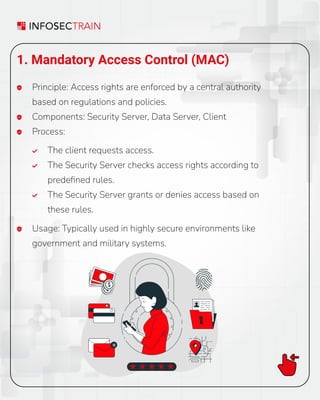
1️. Mandatory Access Control (MAC)
• Principle: Access enforced by a central authority based on policies.
• Best For: High-security environments like government and military.
2️. Discretionary Access Control (DAC)
• Principle: The resource owner controls access.
• Best For: Corporate environments where data owners need flexibility.
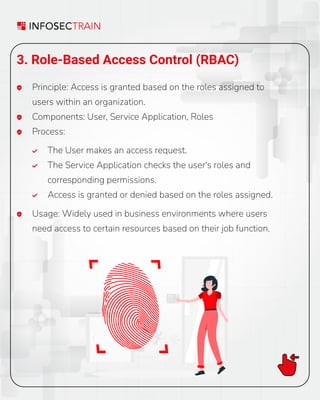
3️. Role-Based Access Control (RBAC)
• Principle: Access based on user roles within the organization.
• Best For: Business environments where access depends on job functions.
4️. Attribute-Based Access Control (ABAC)
• Principle: Access based on multiple attributes (user, resource, environment).
• Best For: Cloud environments where flexibility and dynamic access control are needed.