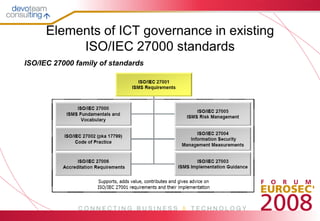
ISO/IEC 38500 provides a framework of principles for corporate governance of information technology, while ISO/IEC 27000 standards address information security management. ISO/IEC 38500 covers responsibilities, planning, acquisition, performance, conformity, and human factors of IT use. ISO/IEC 27000 overlaps with areas like risk management, legal compliance, performance, and management responsibility. A new IT governance standard should account for similarities to prevent inconsistencies, especially for combined auditing against governance and information security standards.