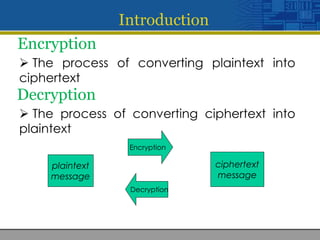
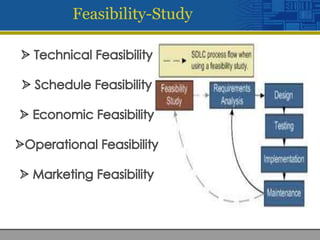
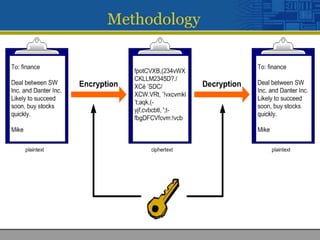
This document discusses encryption and decryption processes. Encryption converts plaintext into ciphertext using a key, while decryption reverses this process to convert ciphertext back to plaintext using the same key. The document was developed by four students and submitted to their professor for a class project on providing security through file, communication, and network encryption using encryption/decryption techniques. It outlines the feasibility study, methodology, and system requirements for the project.