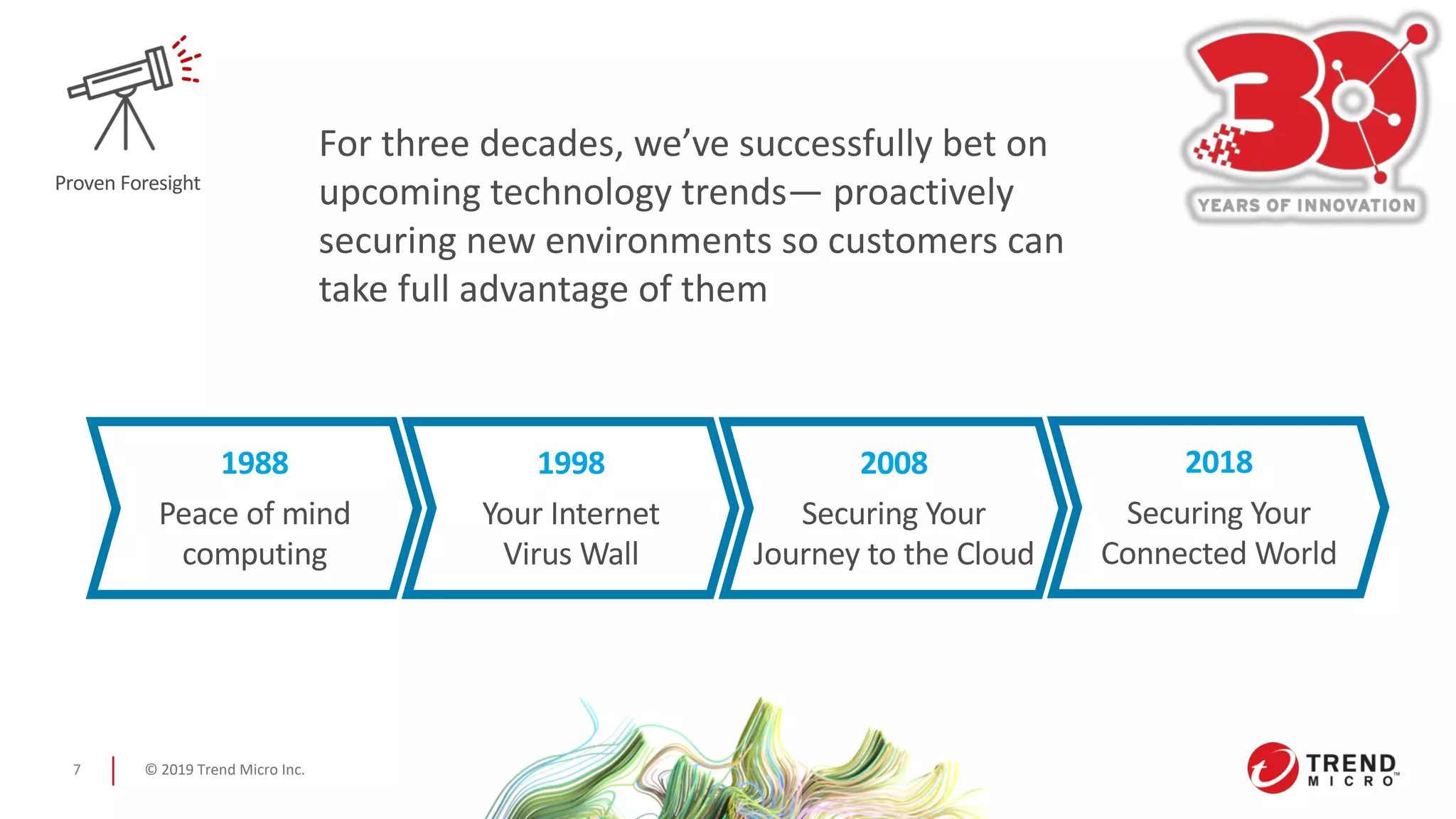
The document discusses the challenges and opportunities in cybersecurity, highlighting the increasing sophistication of cyber threats and the necessity for organizations to adapt. It emphasizes the importance of connected solutions, centralized visibility, and automated detection to combat these threats effectively, while showcasing Trend Micro's long-standing expertise in the field. The company, founded in 1988, boasts a significant market presence and a commitment to securing digital environments.