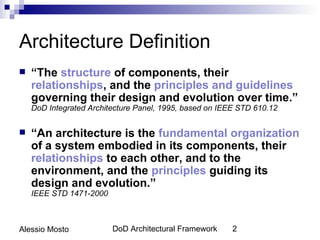
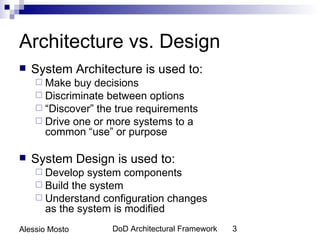
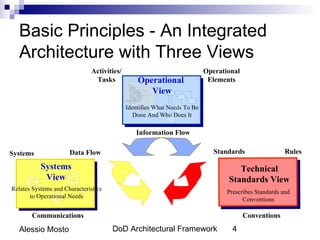
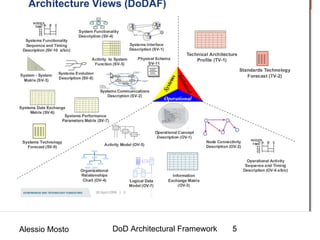
This document discusses software architecture and design testing. It explains that software architecture and design defects can lead to bugs and issues later in development. Some common types of early-stage defects include requirements defects, architectural defects, and design defects. Thorough testing of architecture and design can help reduce later defects by discovering problems early. The document recommends techniques like architecture reviews, modeling, and inspections to test software architecture and design quality before implementation.