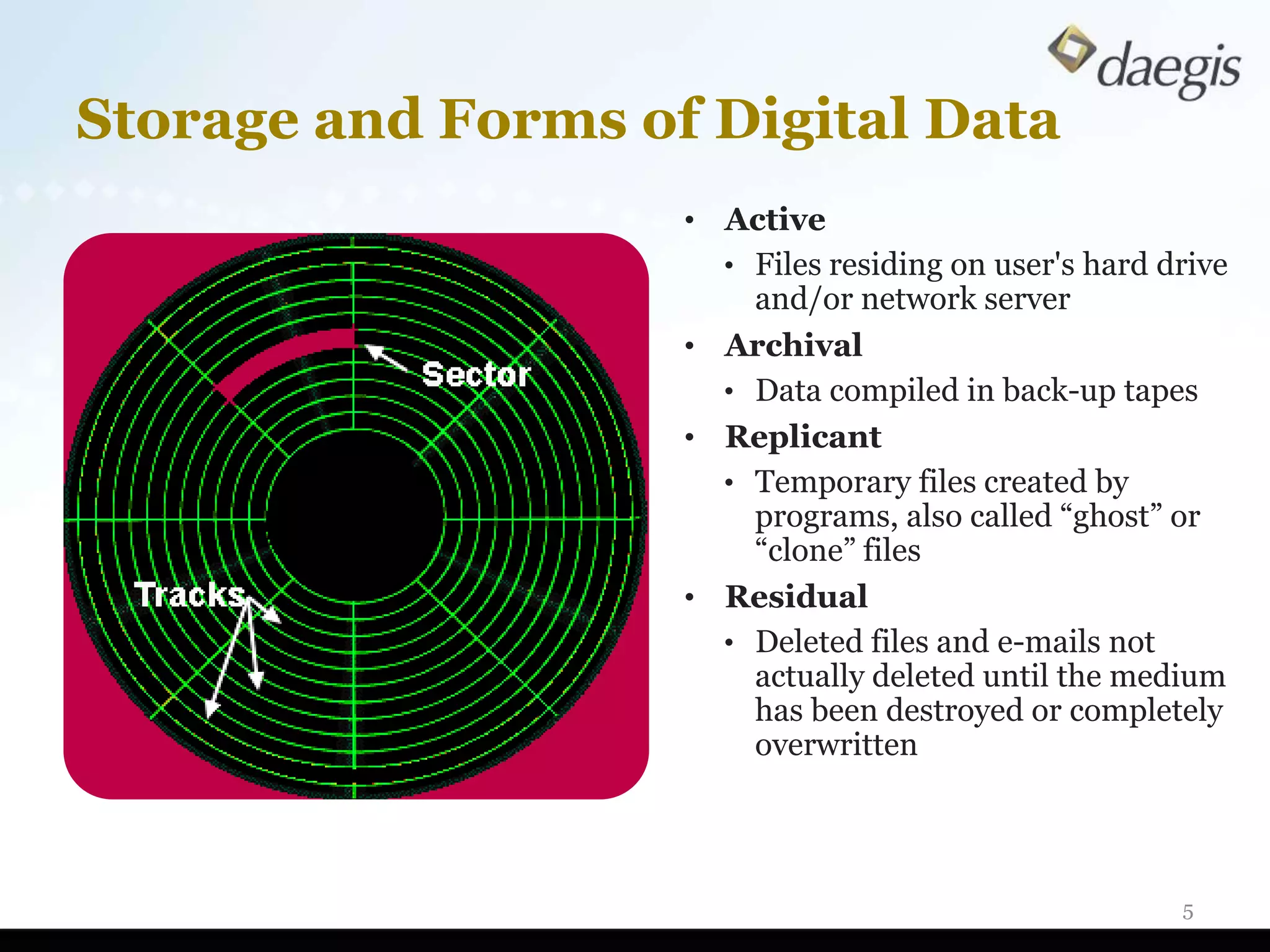
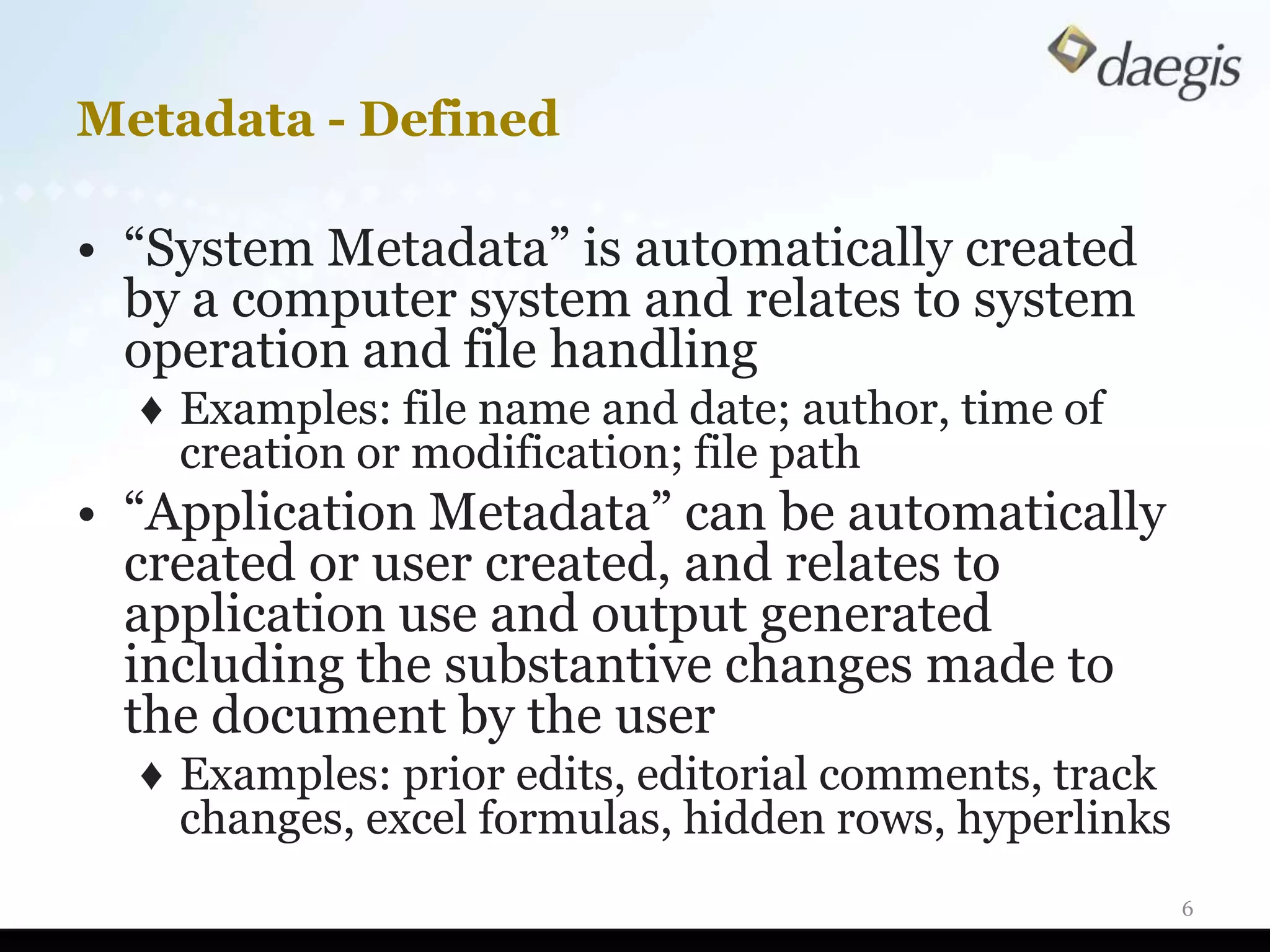
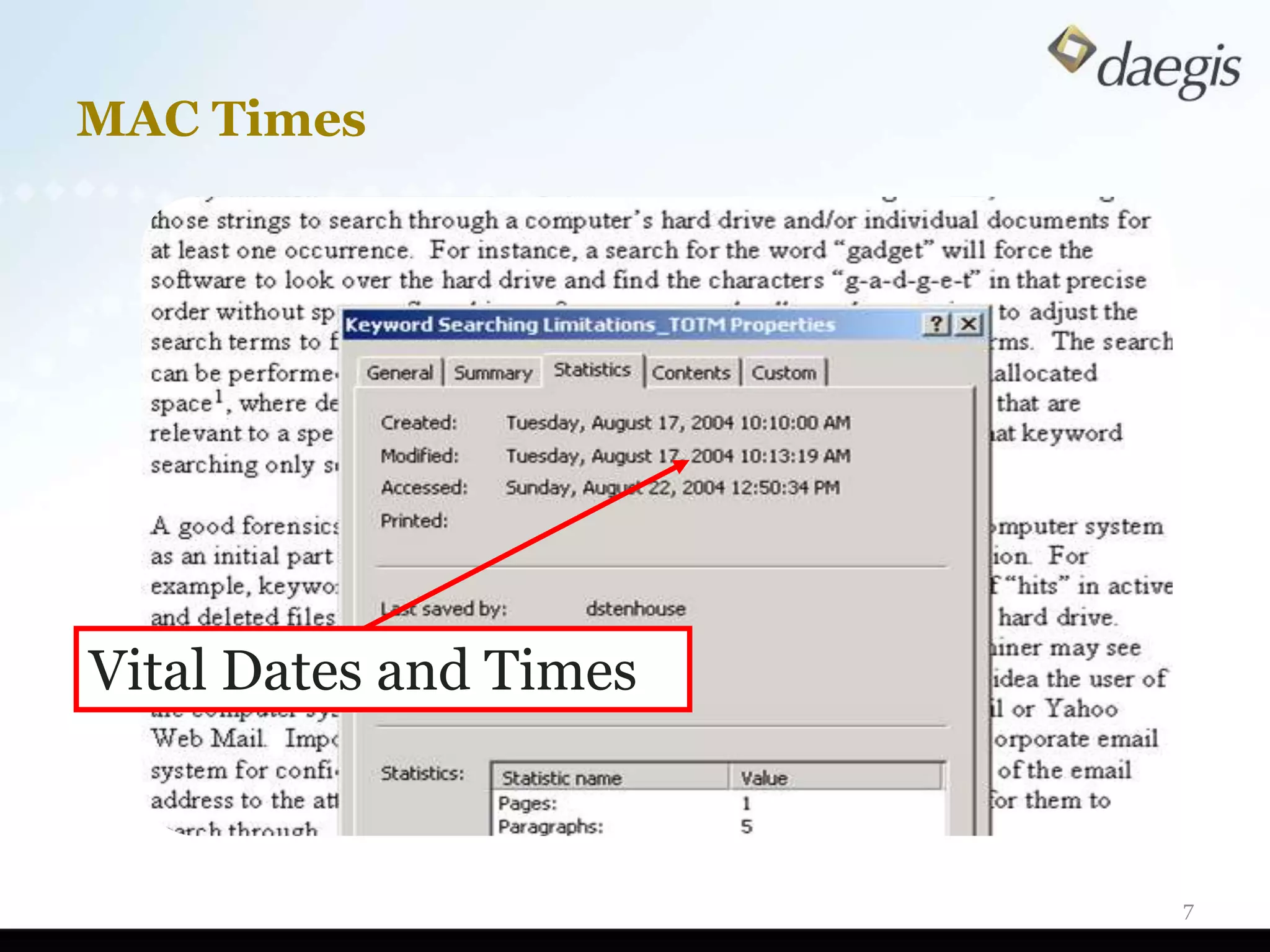
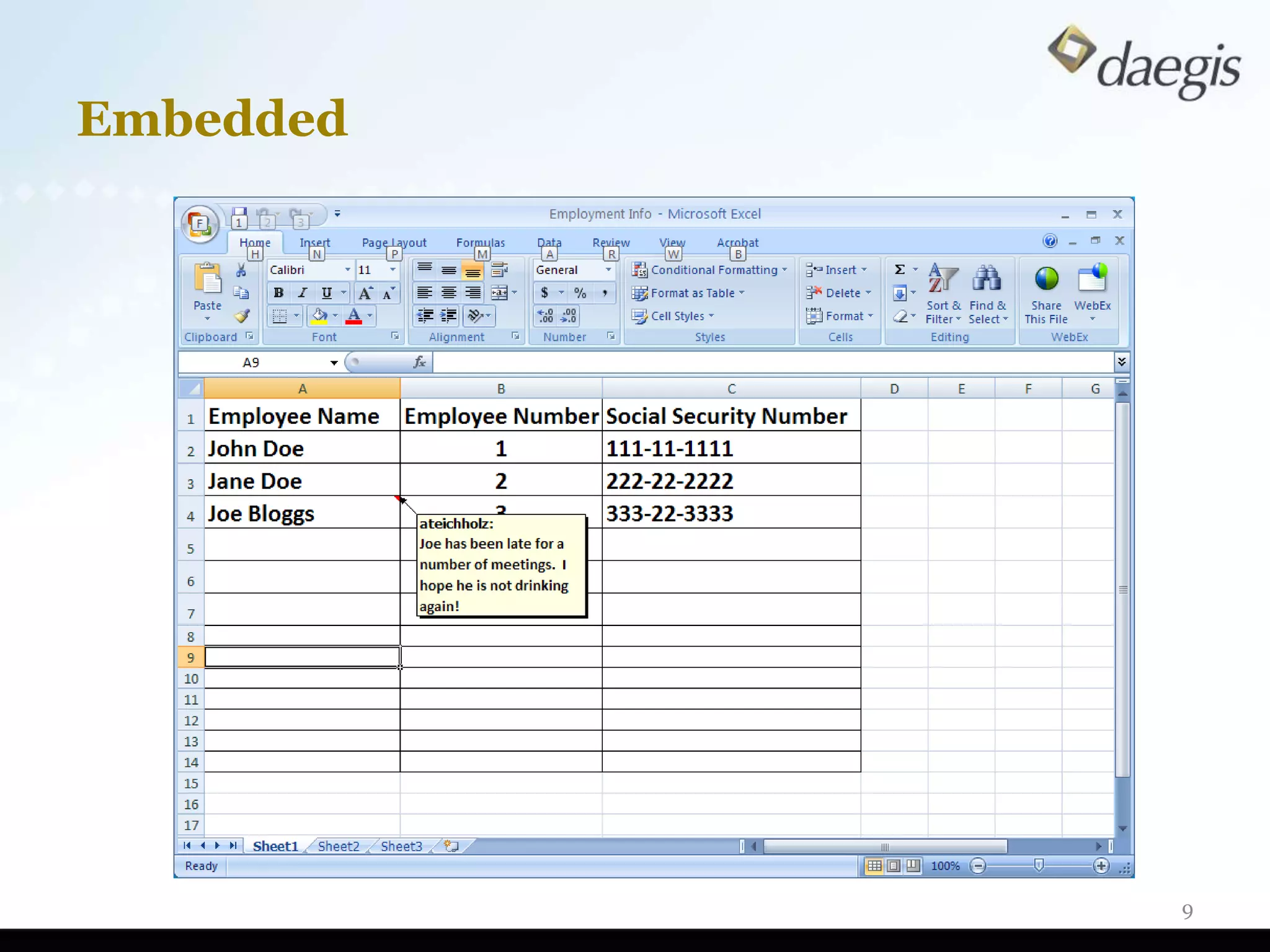
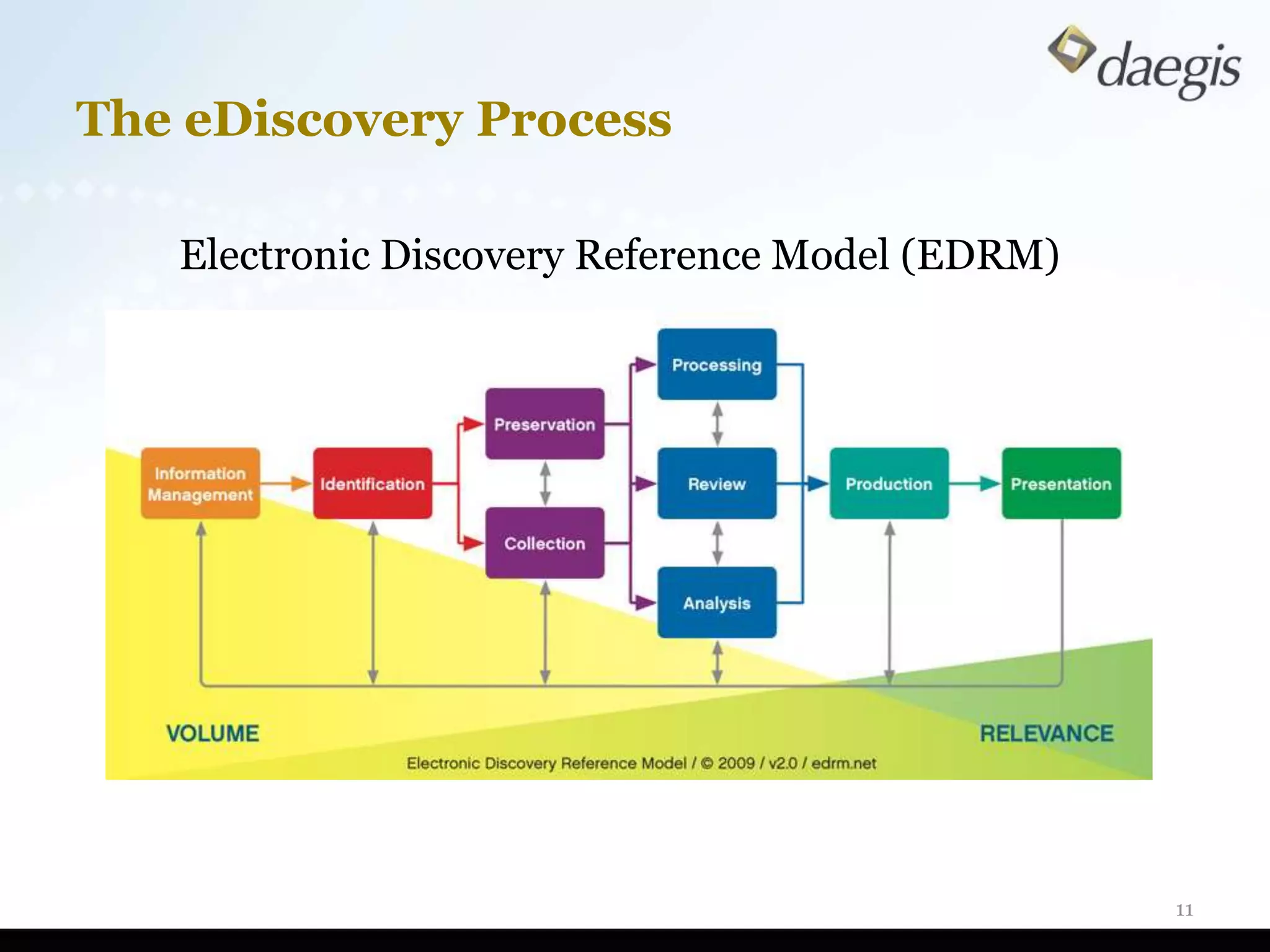
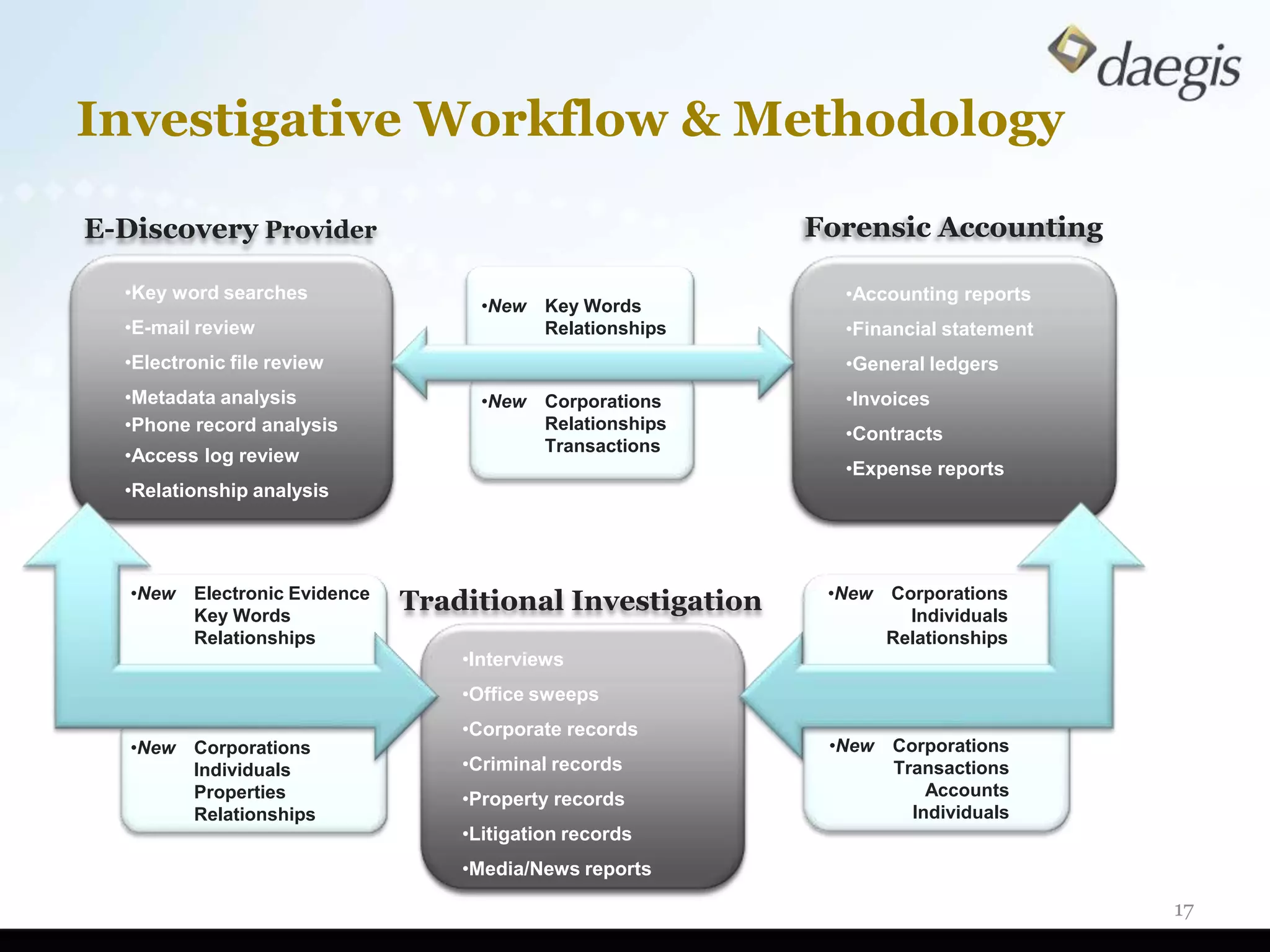
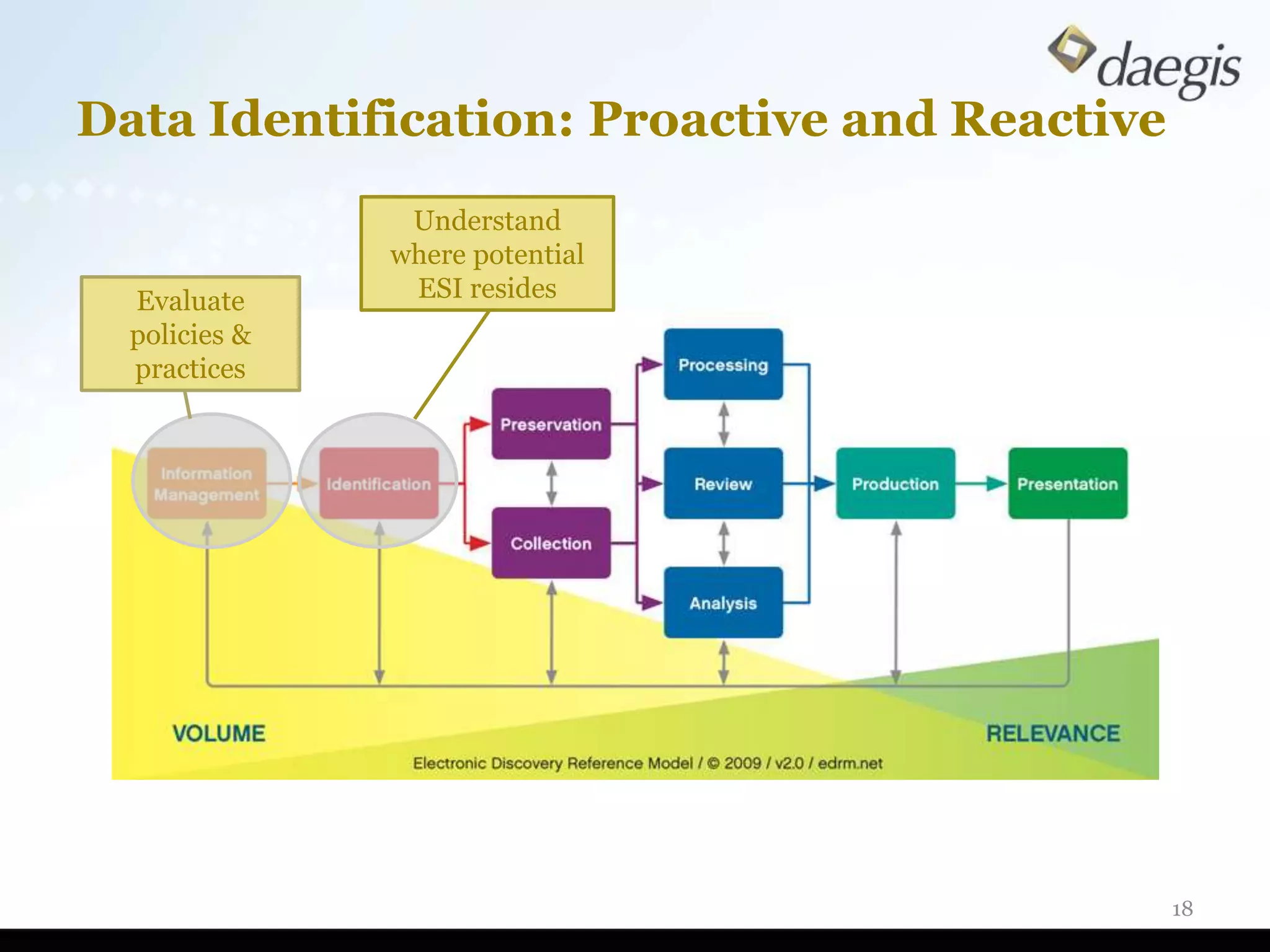
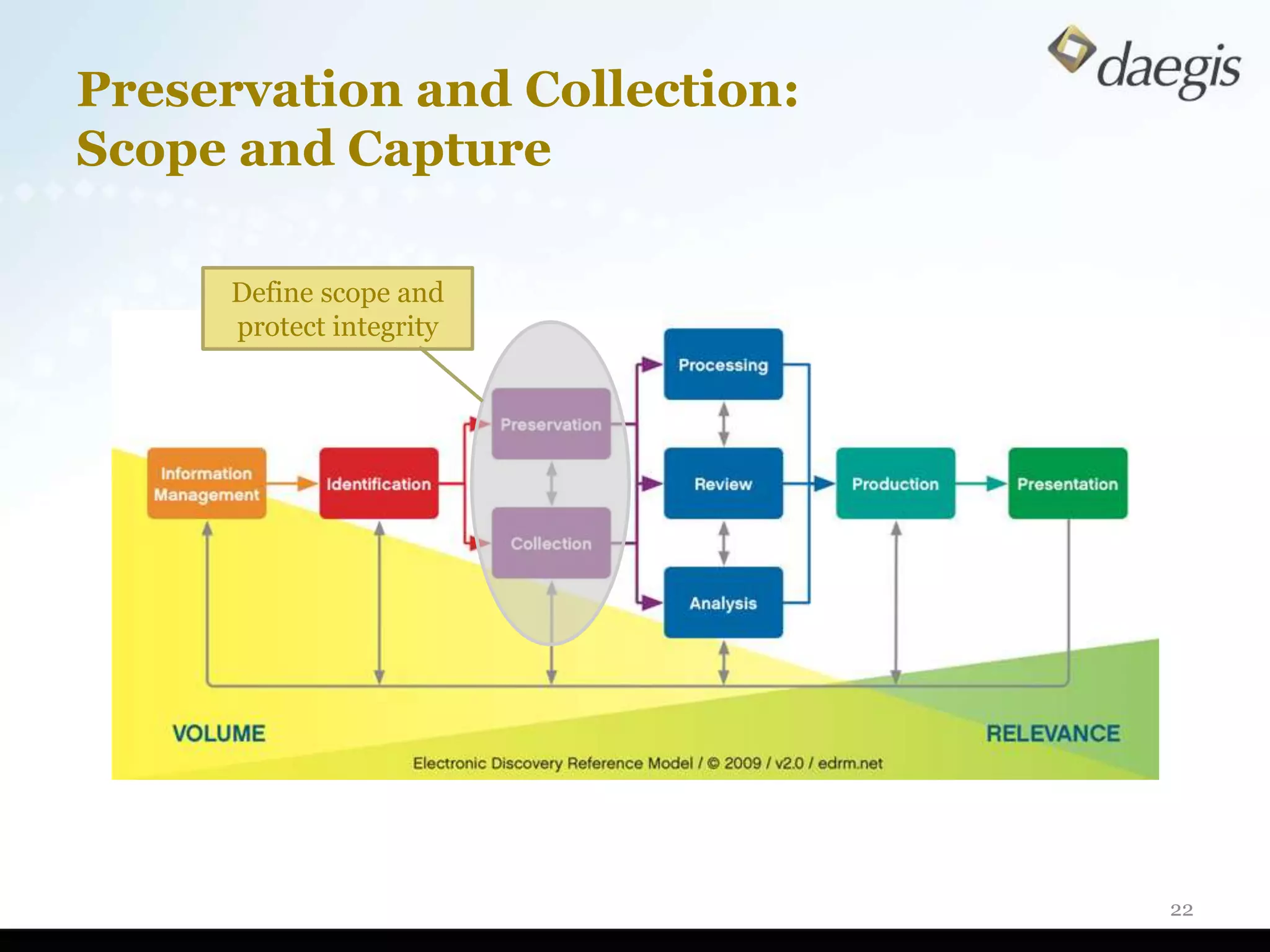
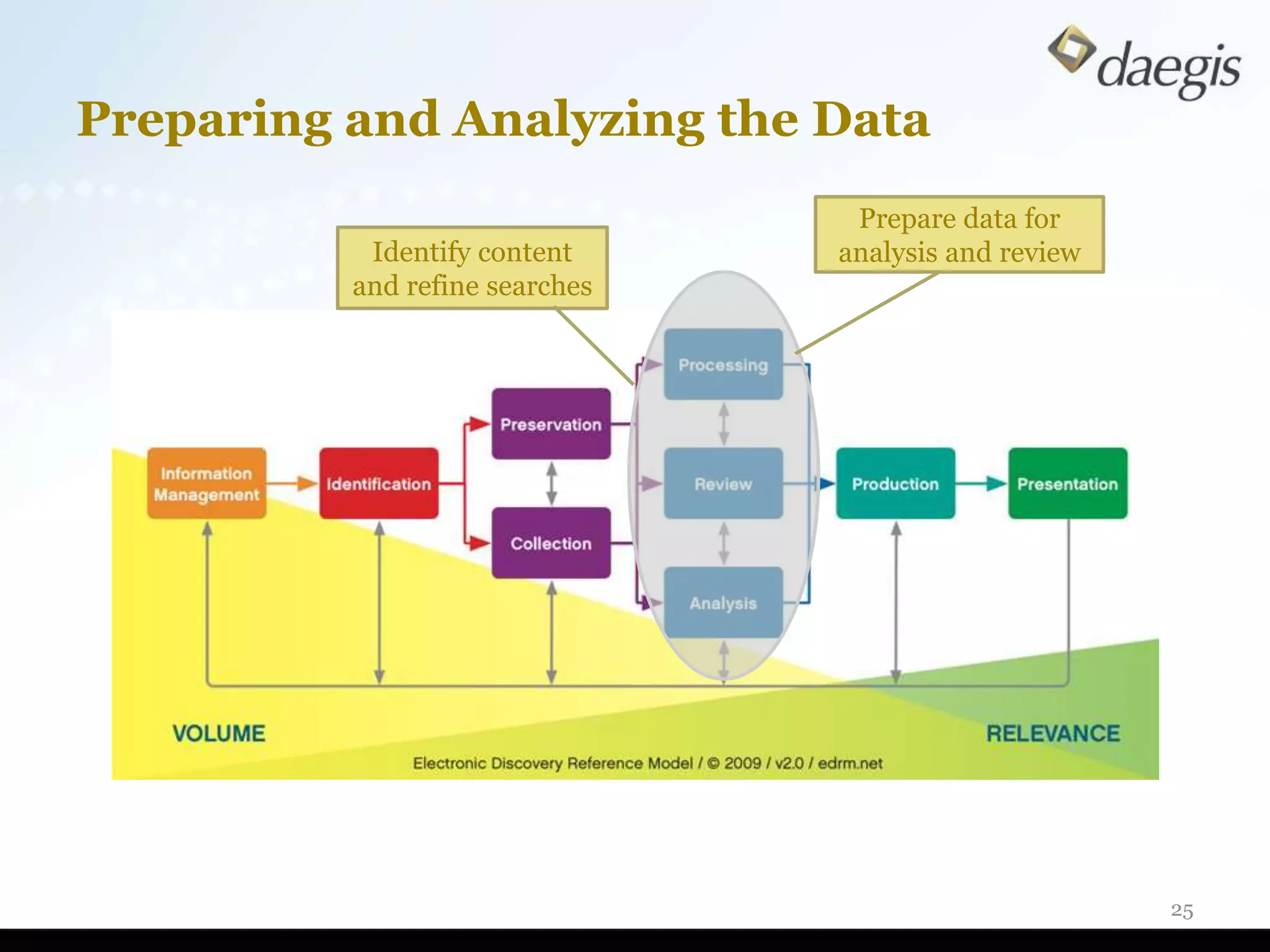
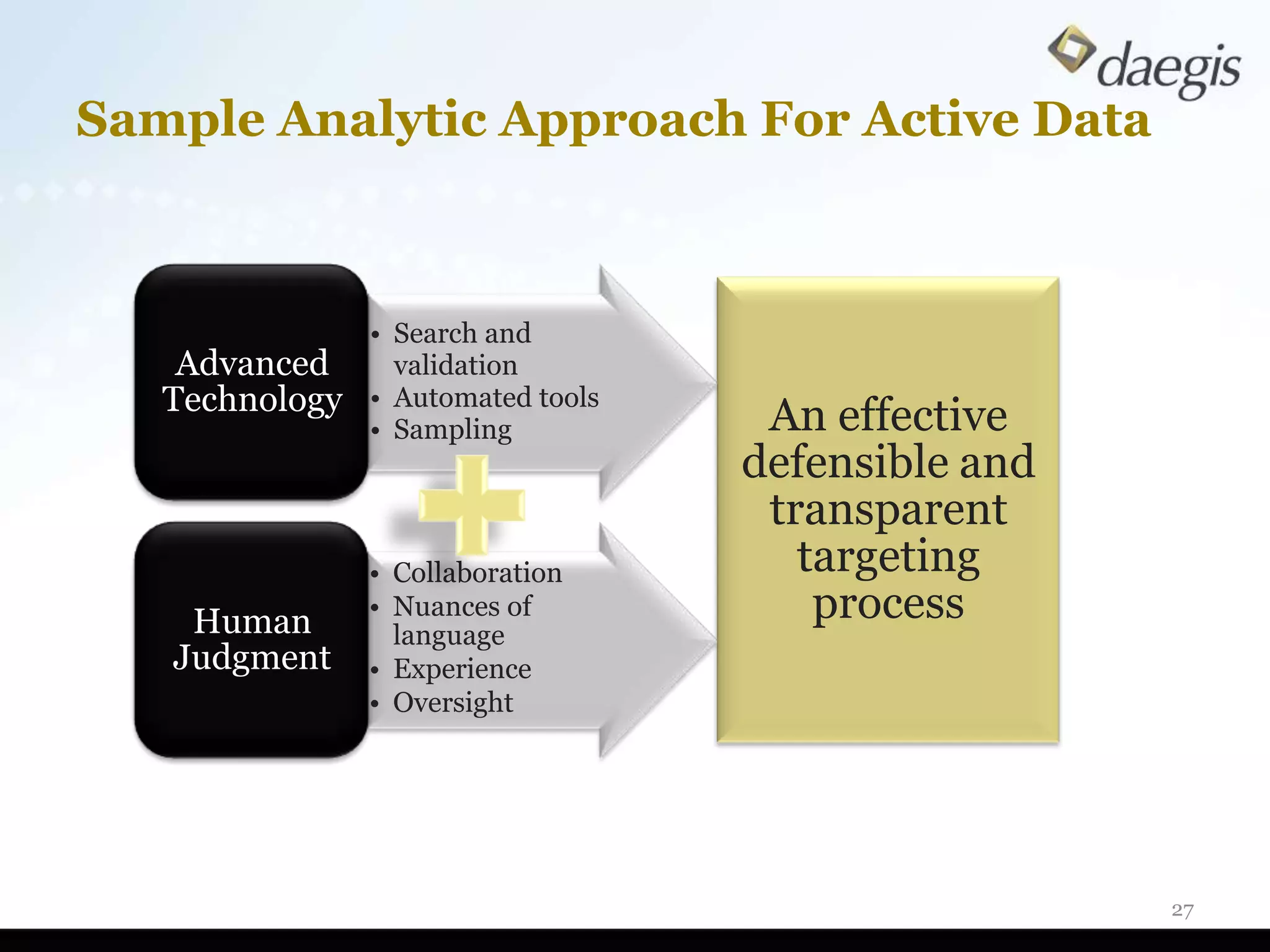
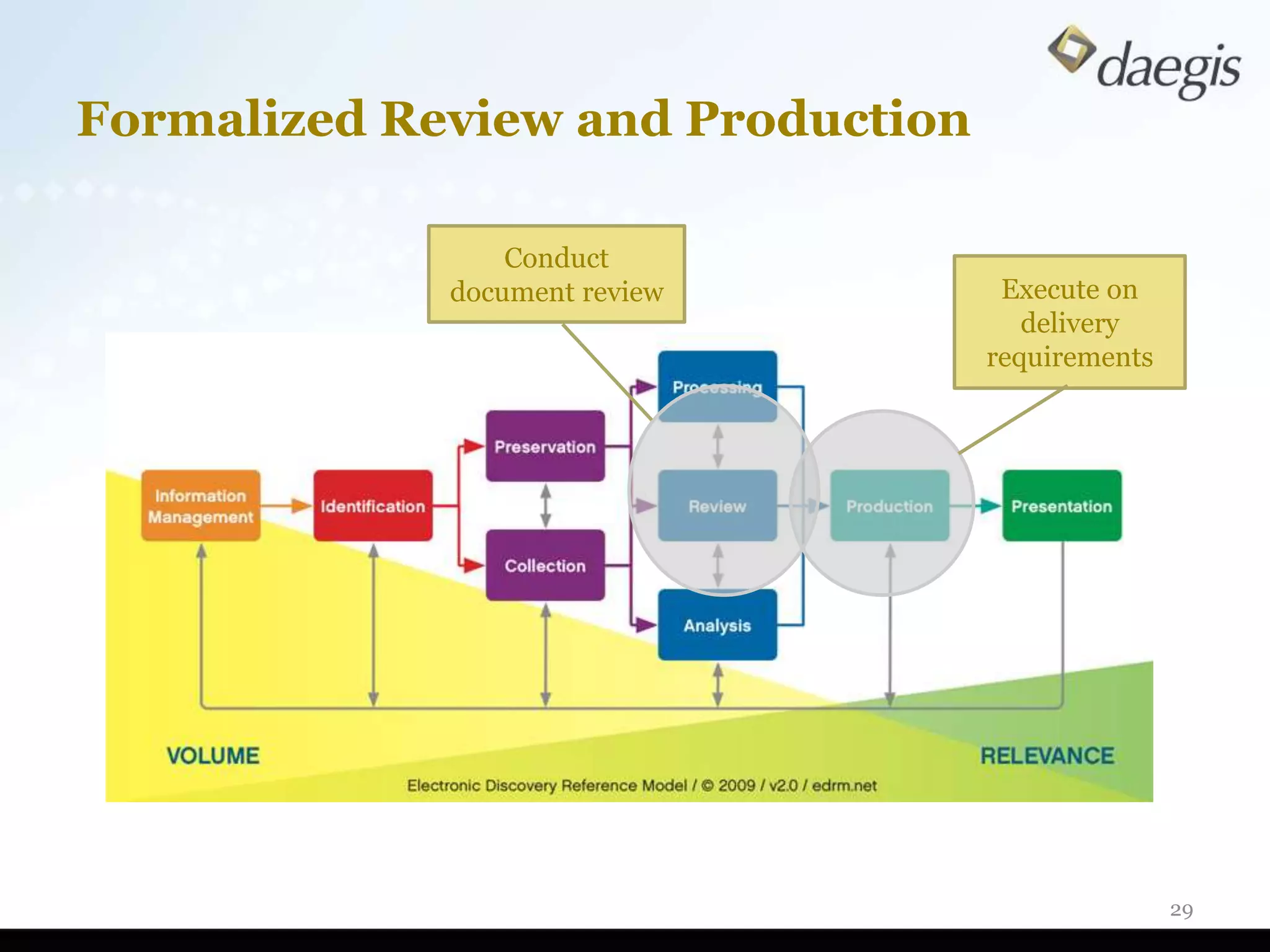
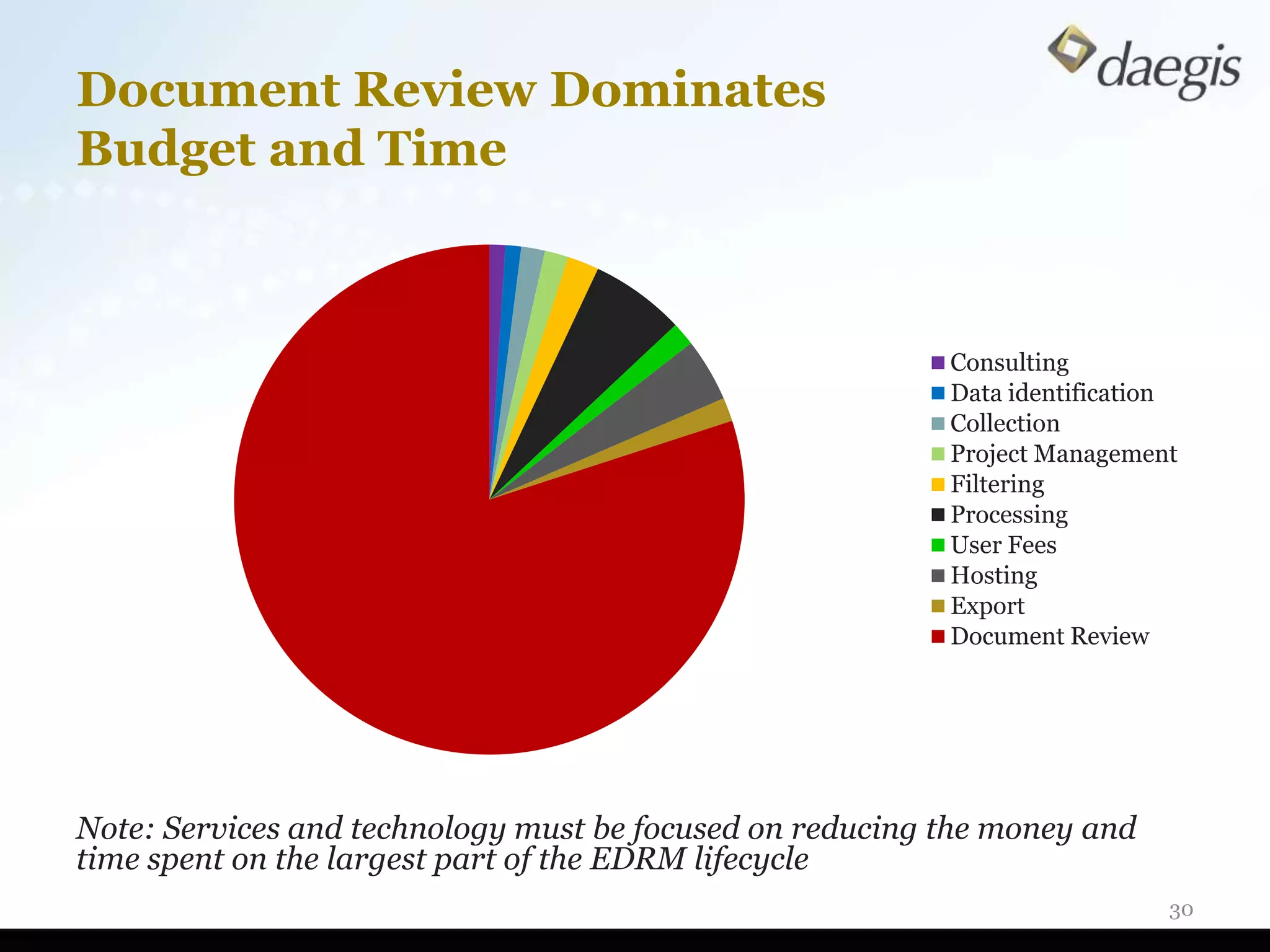
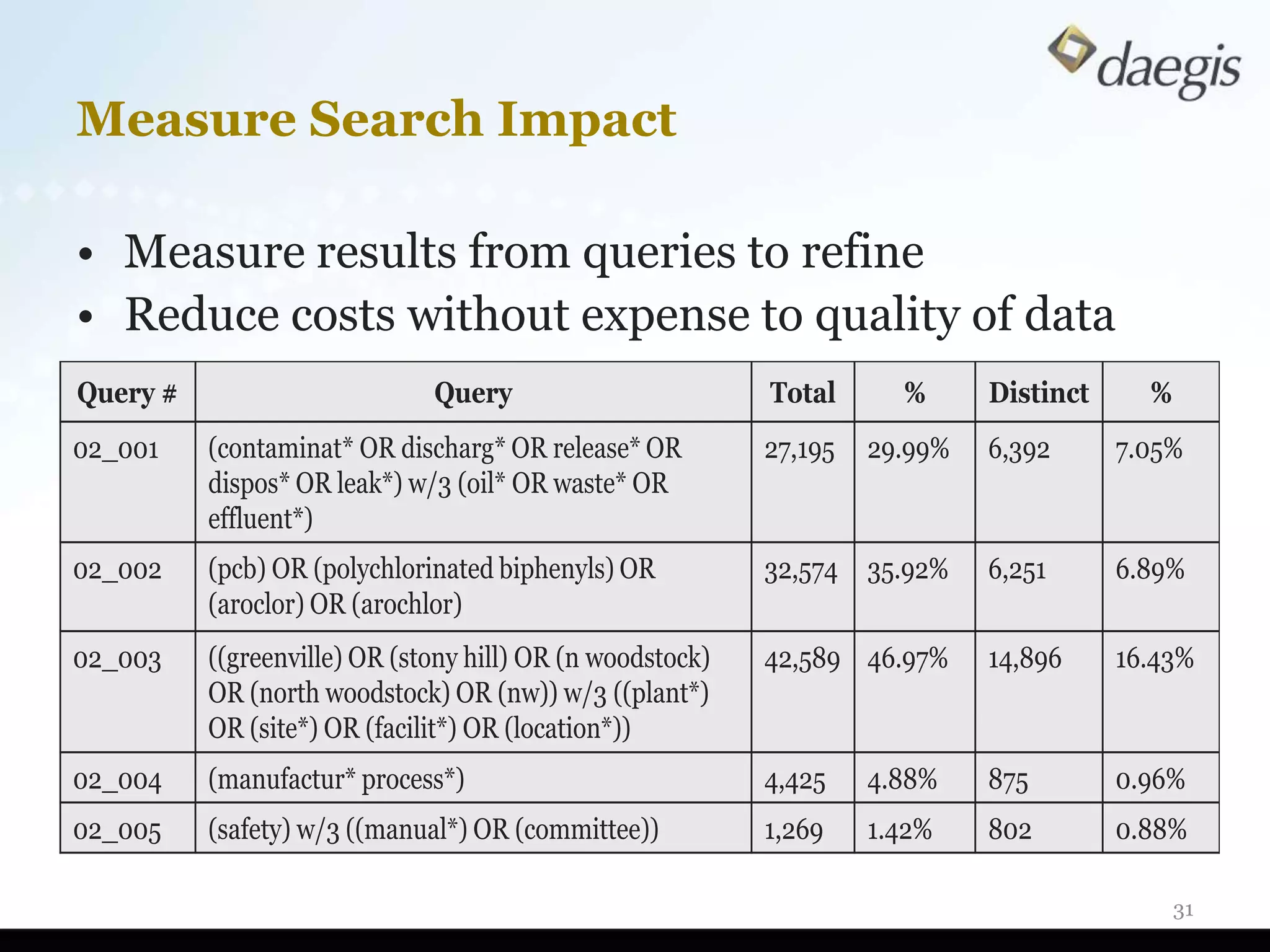
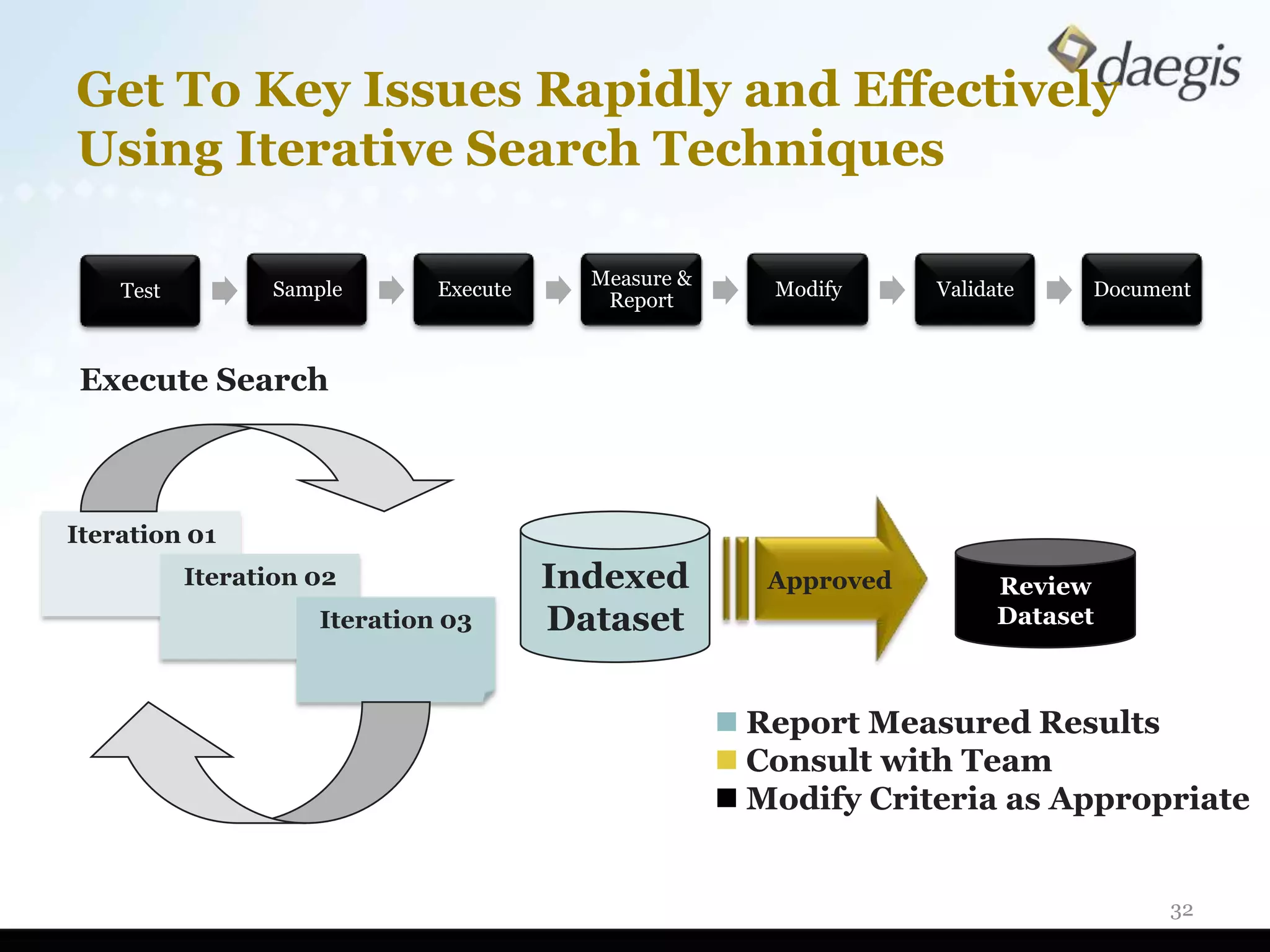
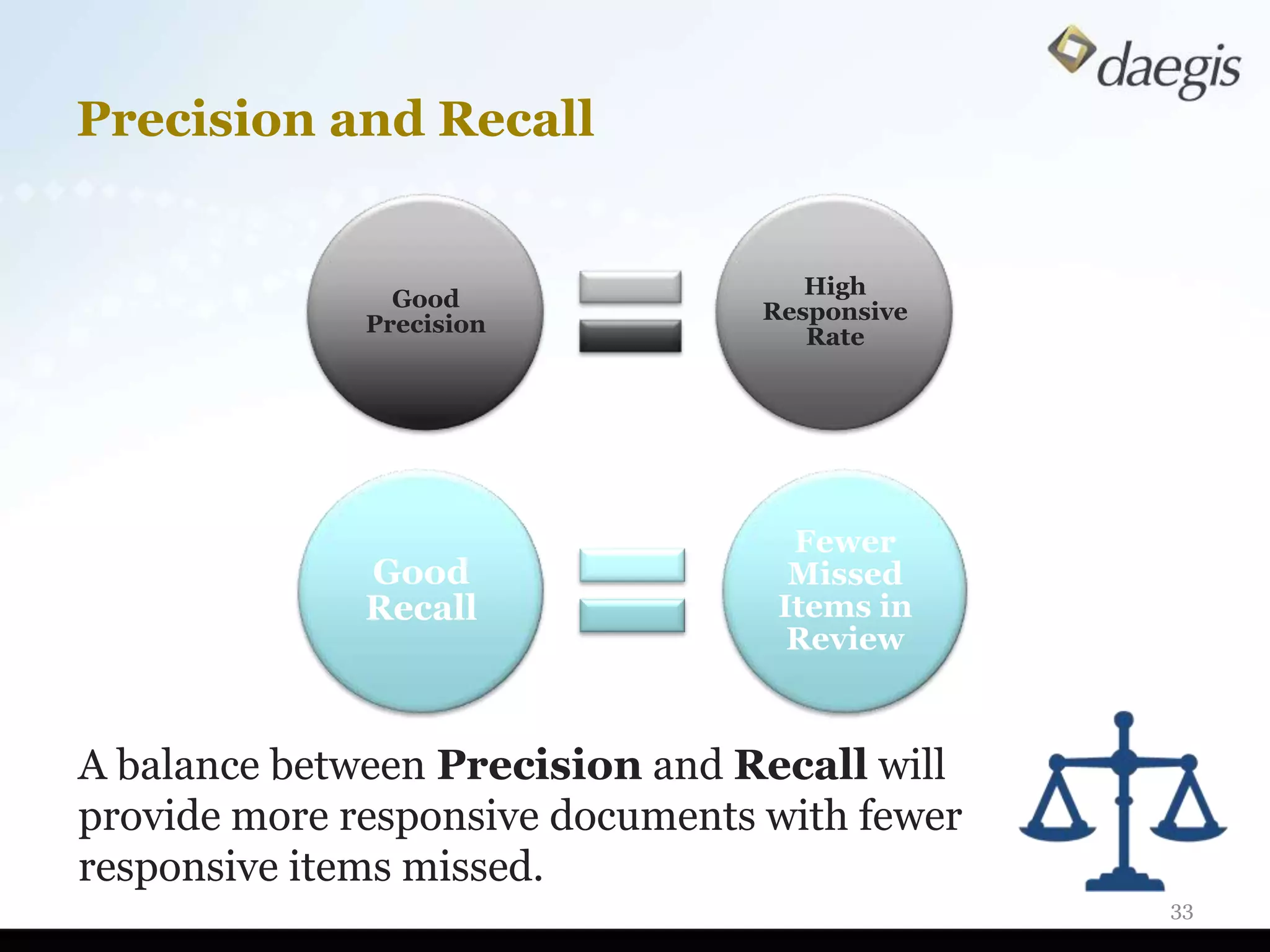
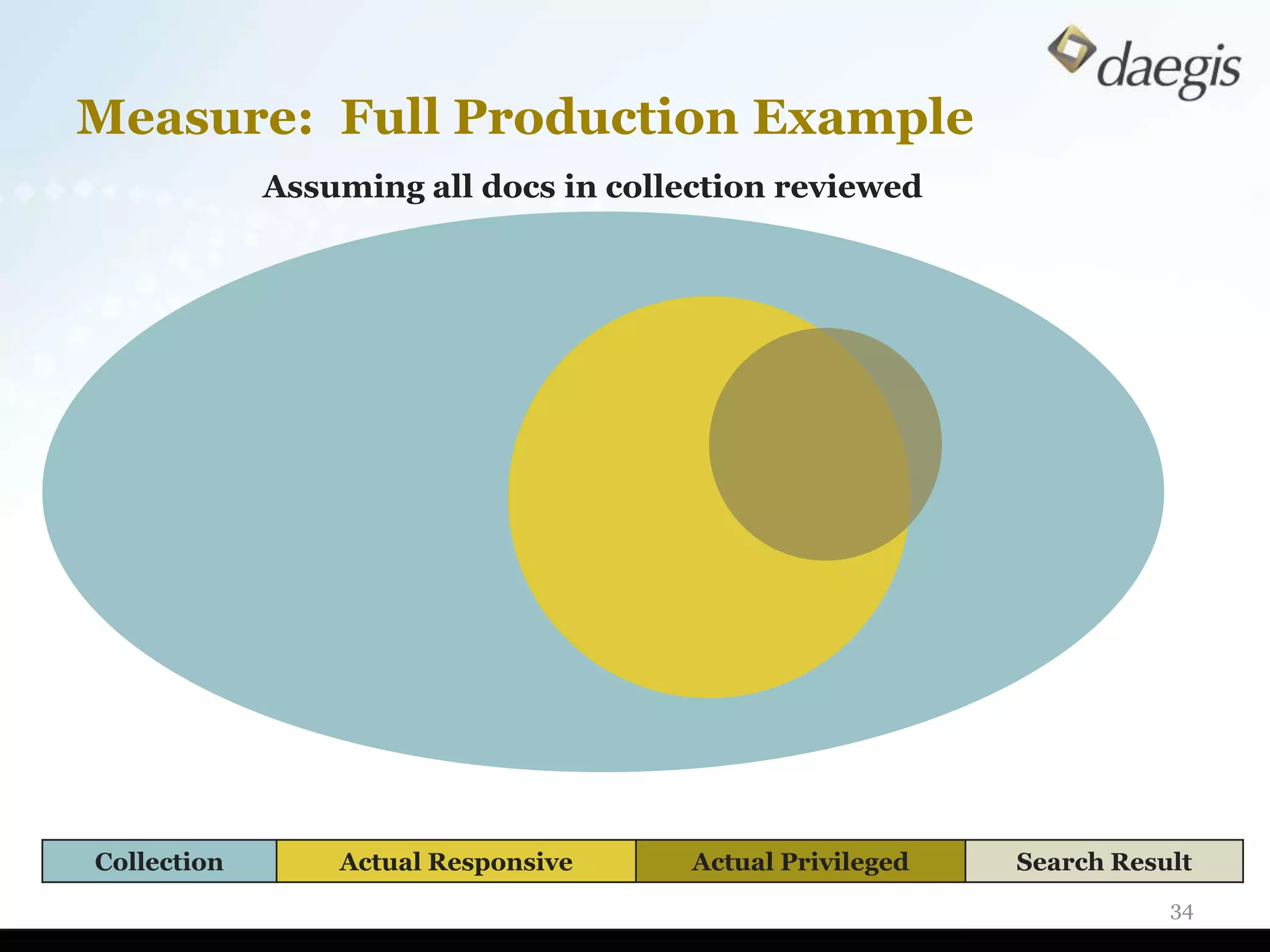
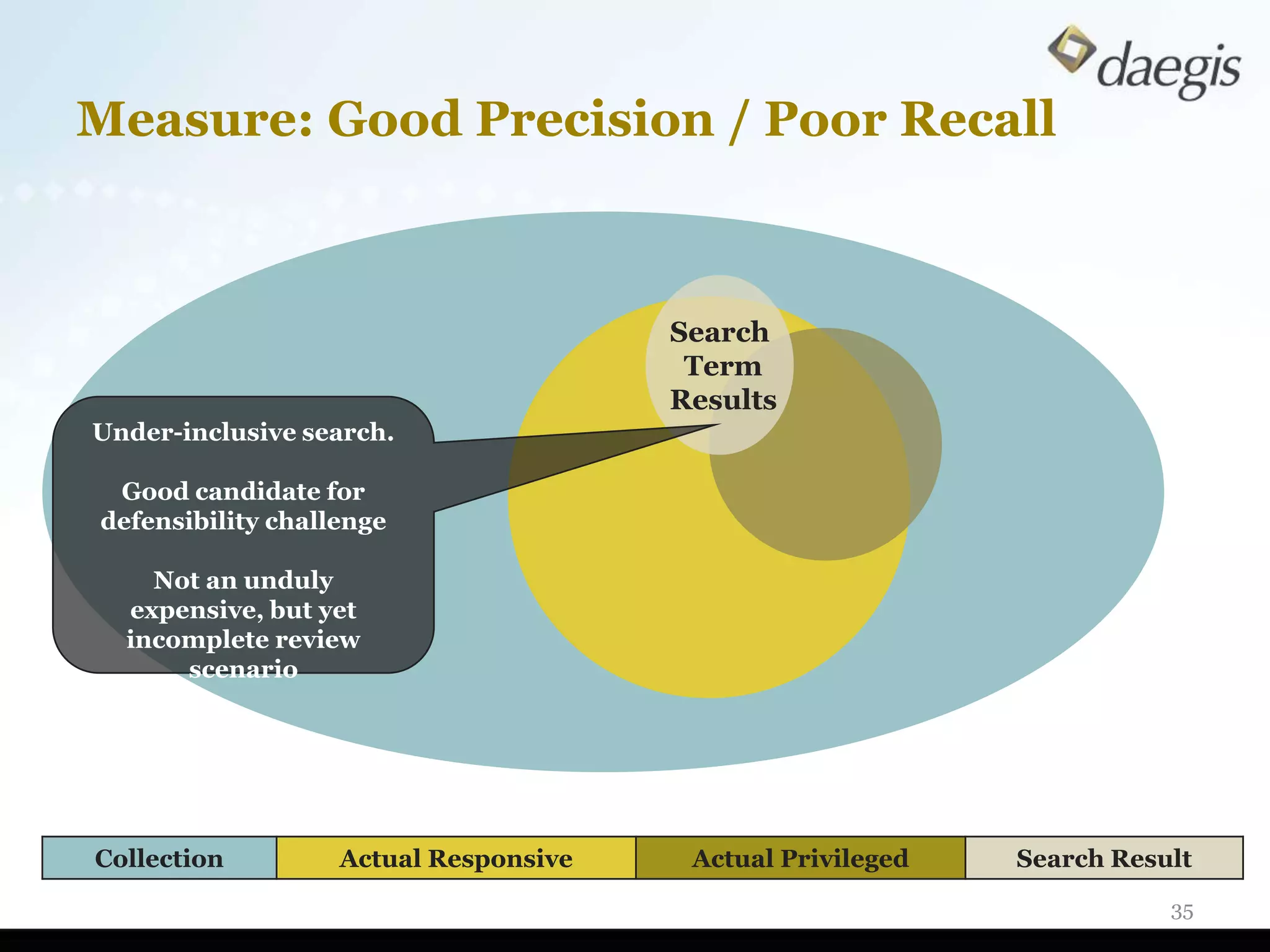
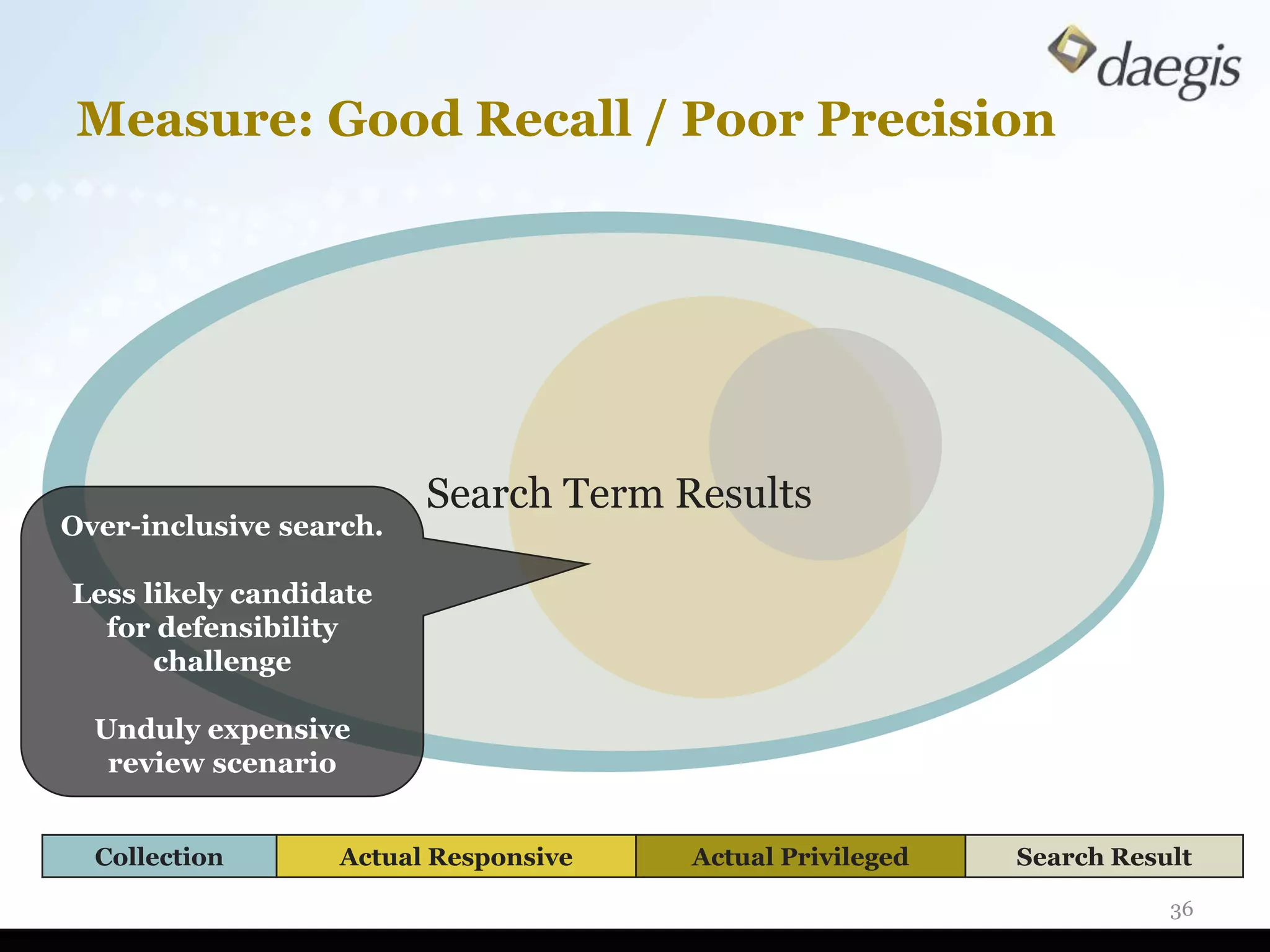
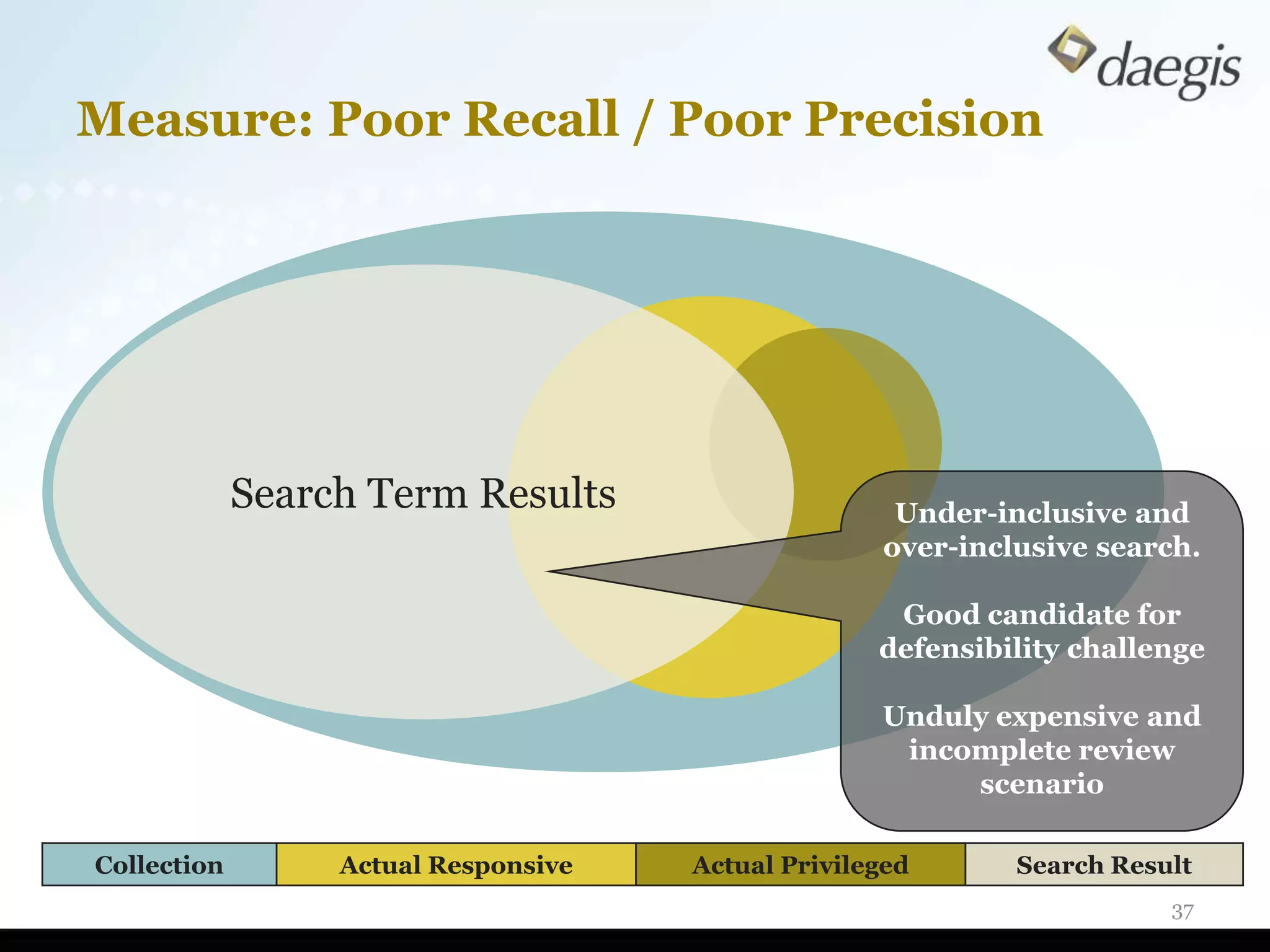
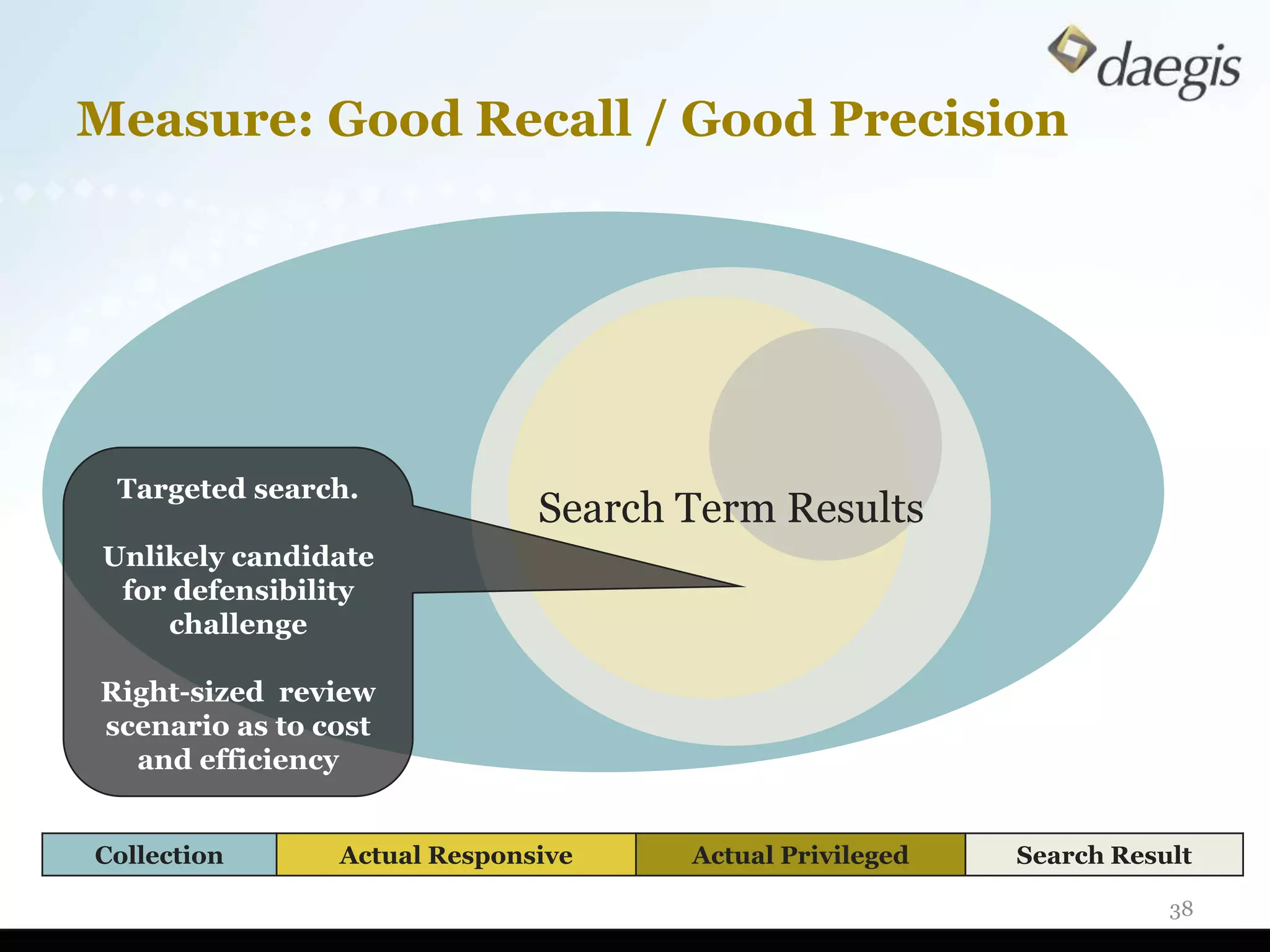
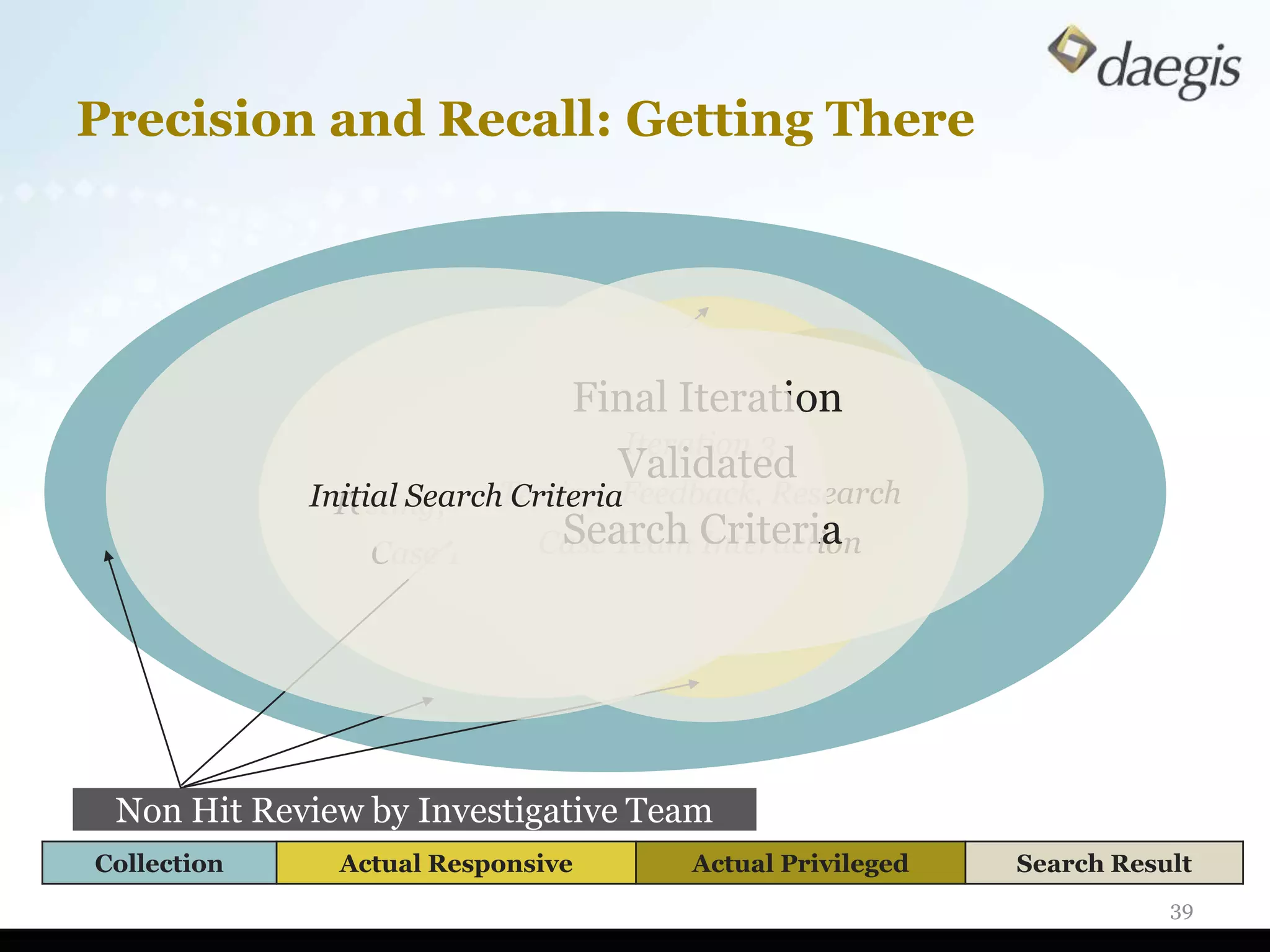
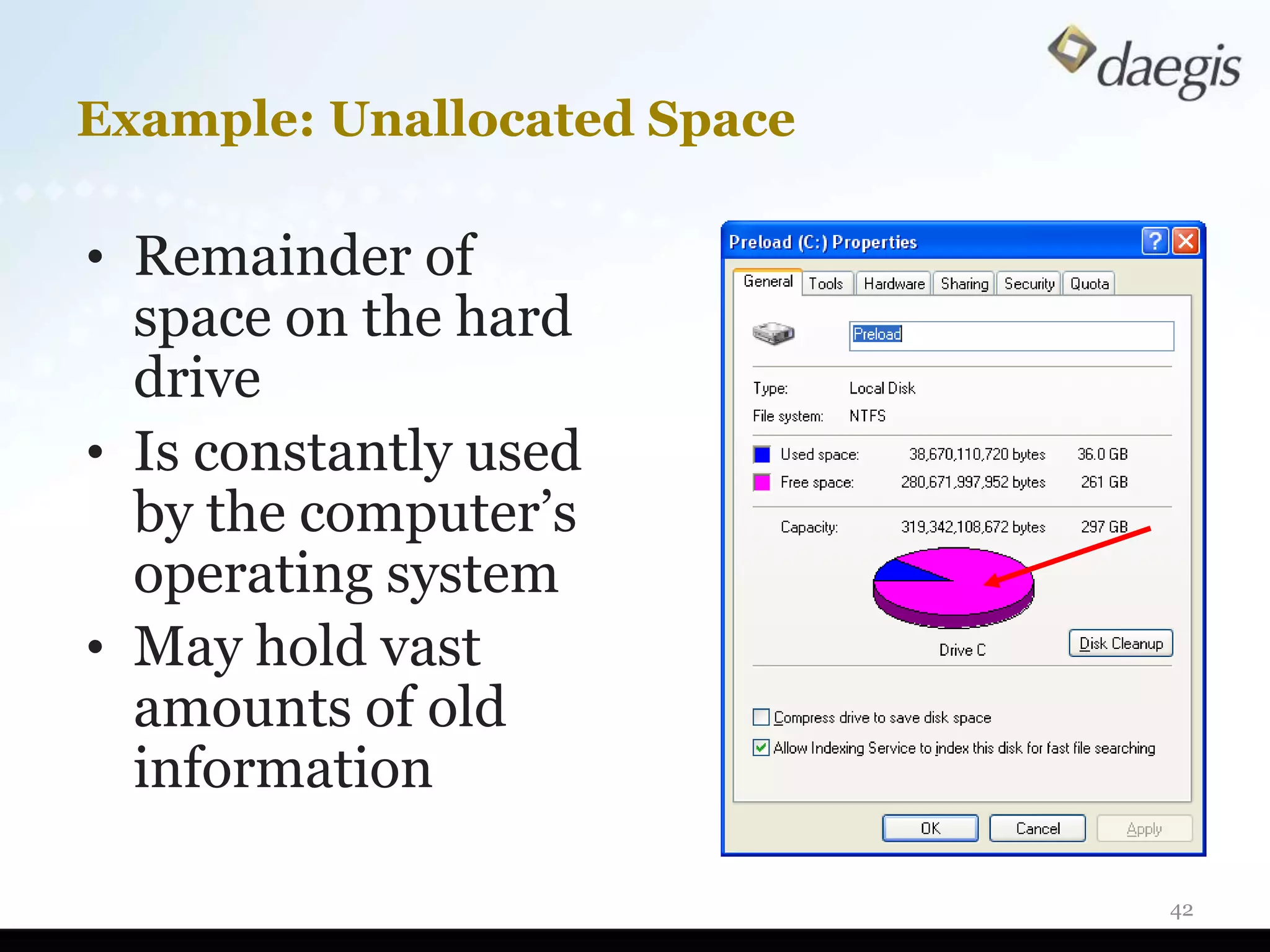
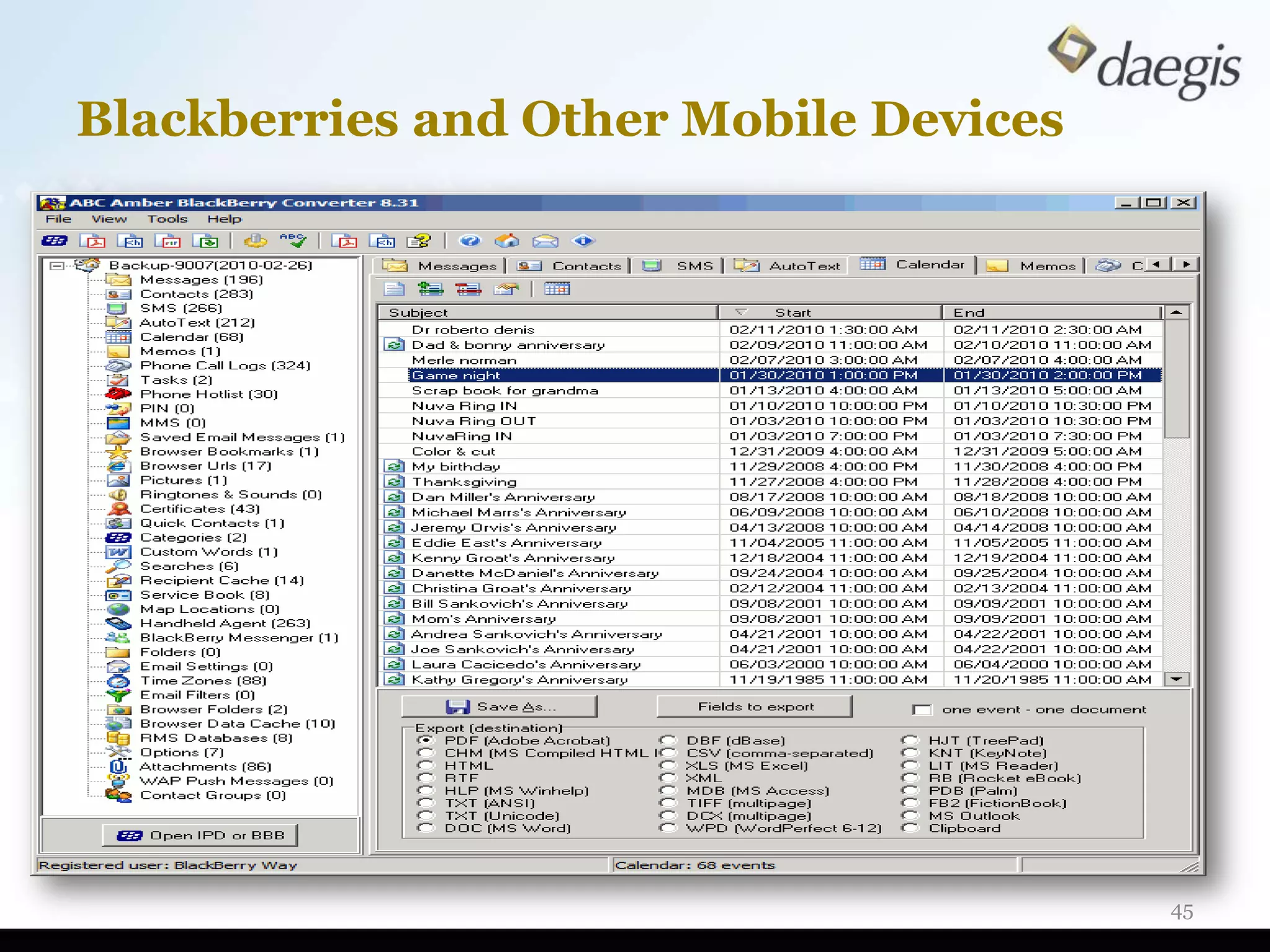
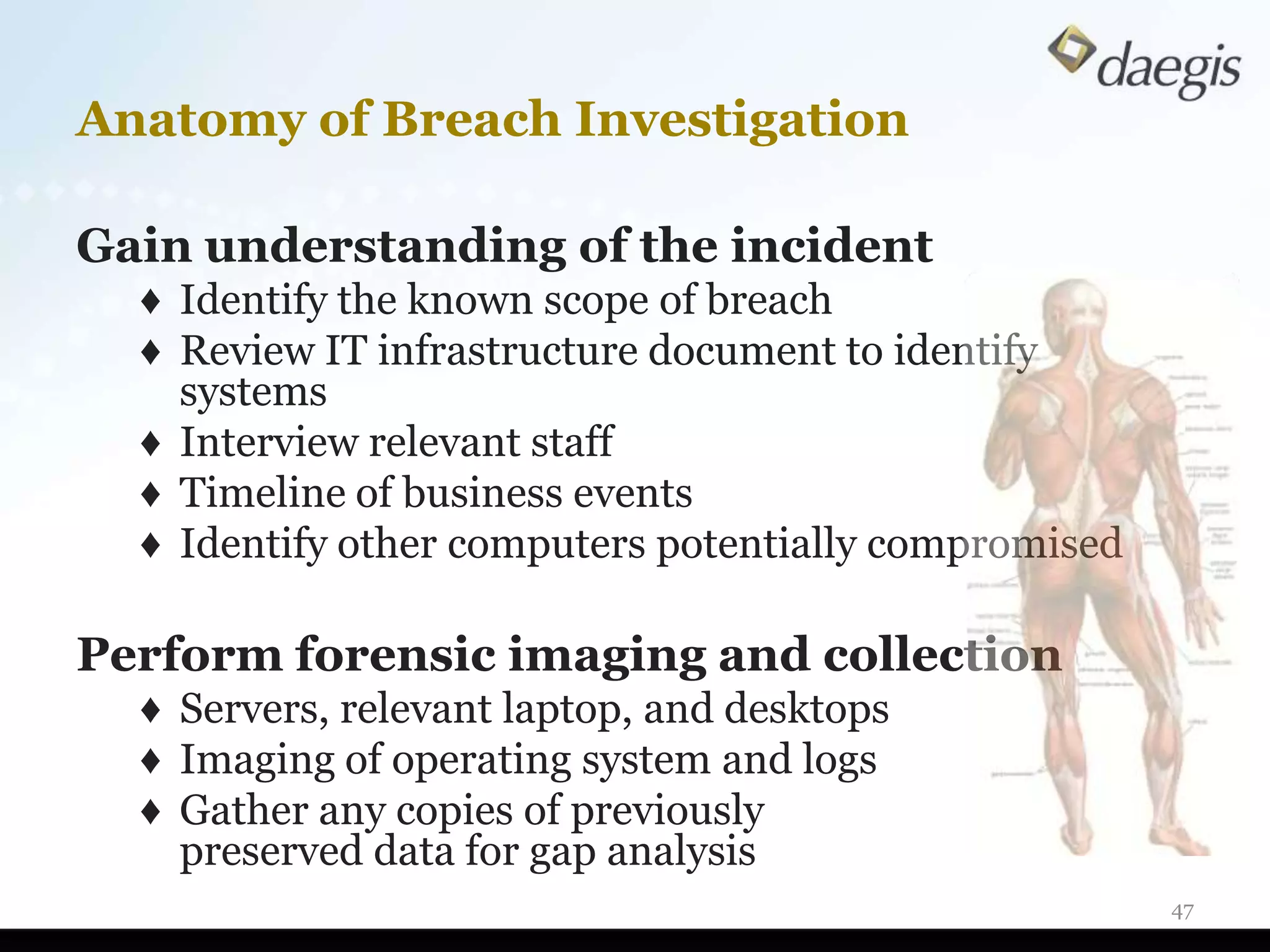
The document outlines critical activities and considerations for conducting effective internal investigations involving electronically stored information (ESI). It covers various stages of the e-discovery process, including data identification, collection, analysis, and the importance of proper planning and team collaboration. Key topics include the nature of investigations, data forensics, metadata, and best practices for data protection and compliance.