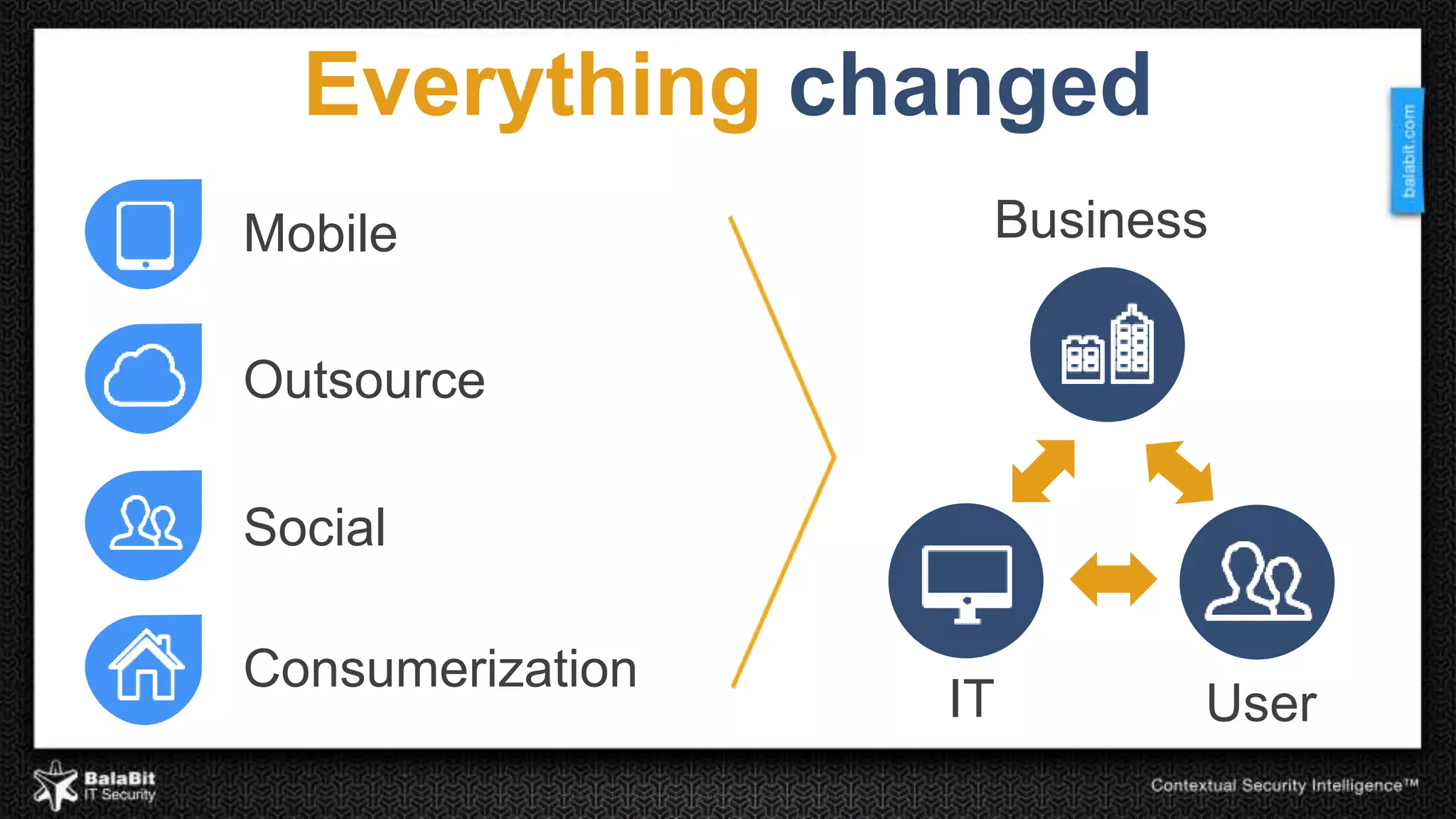
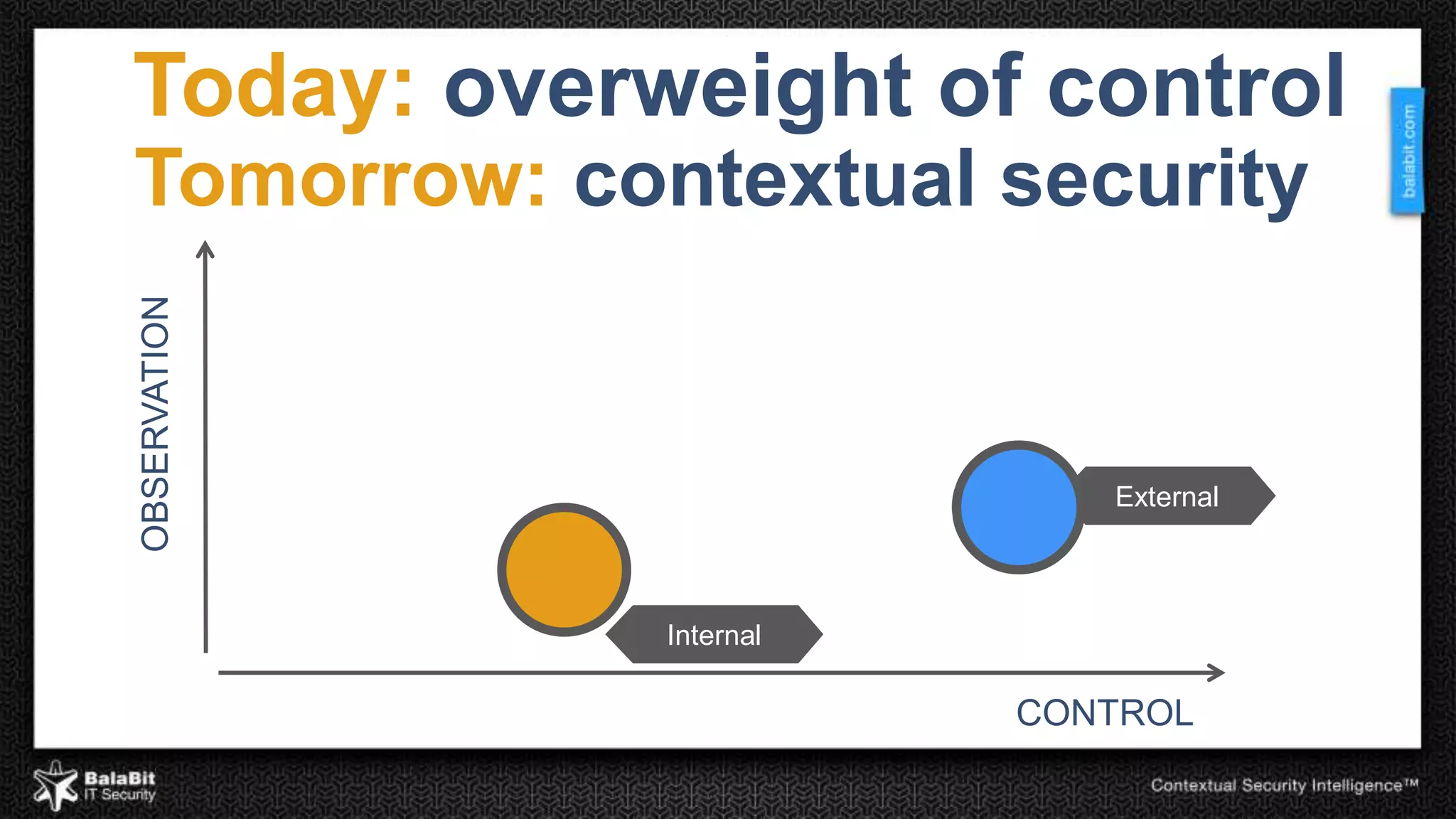
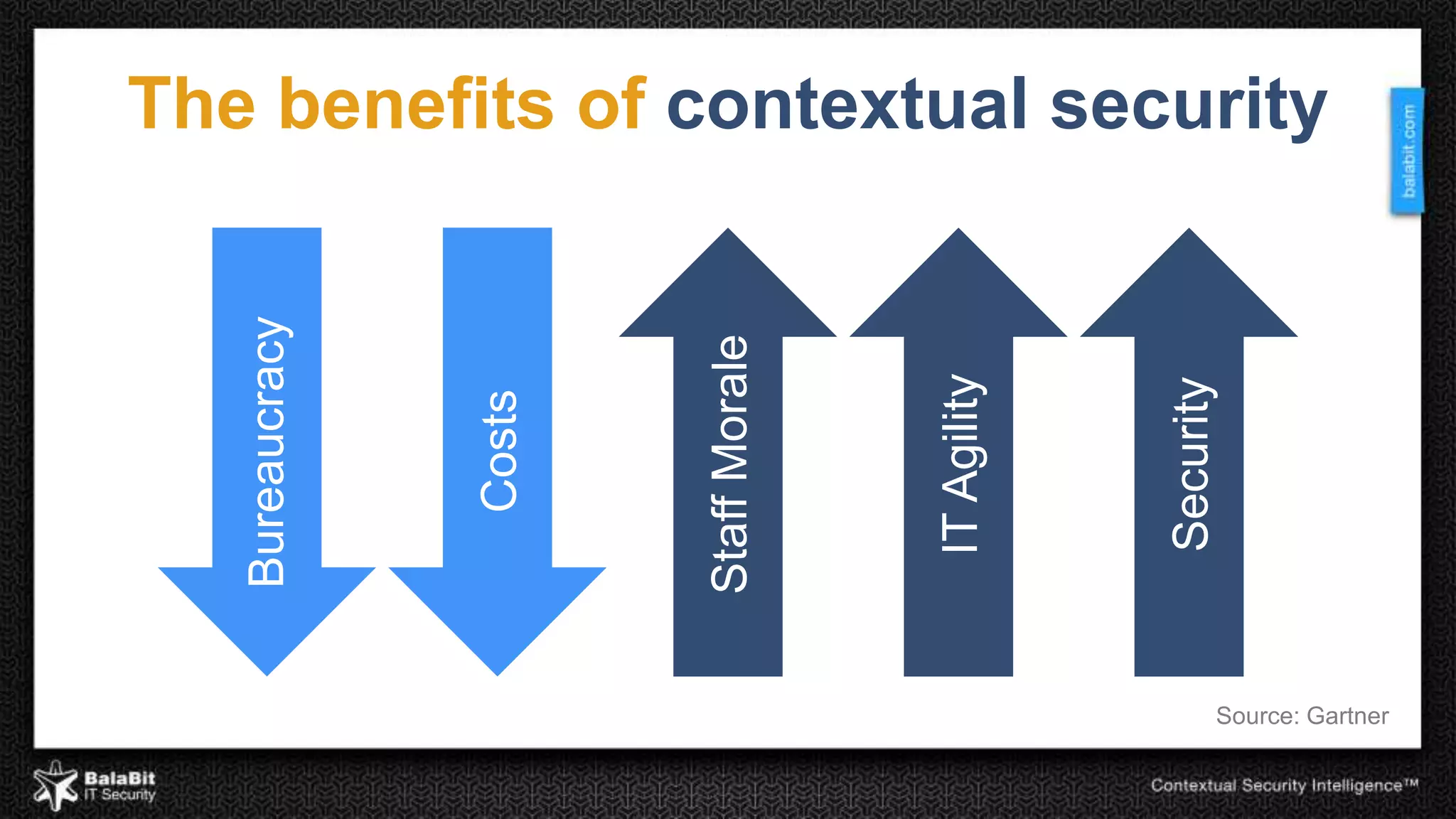
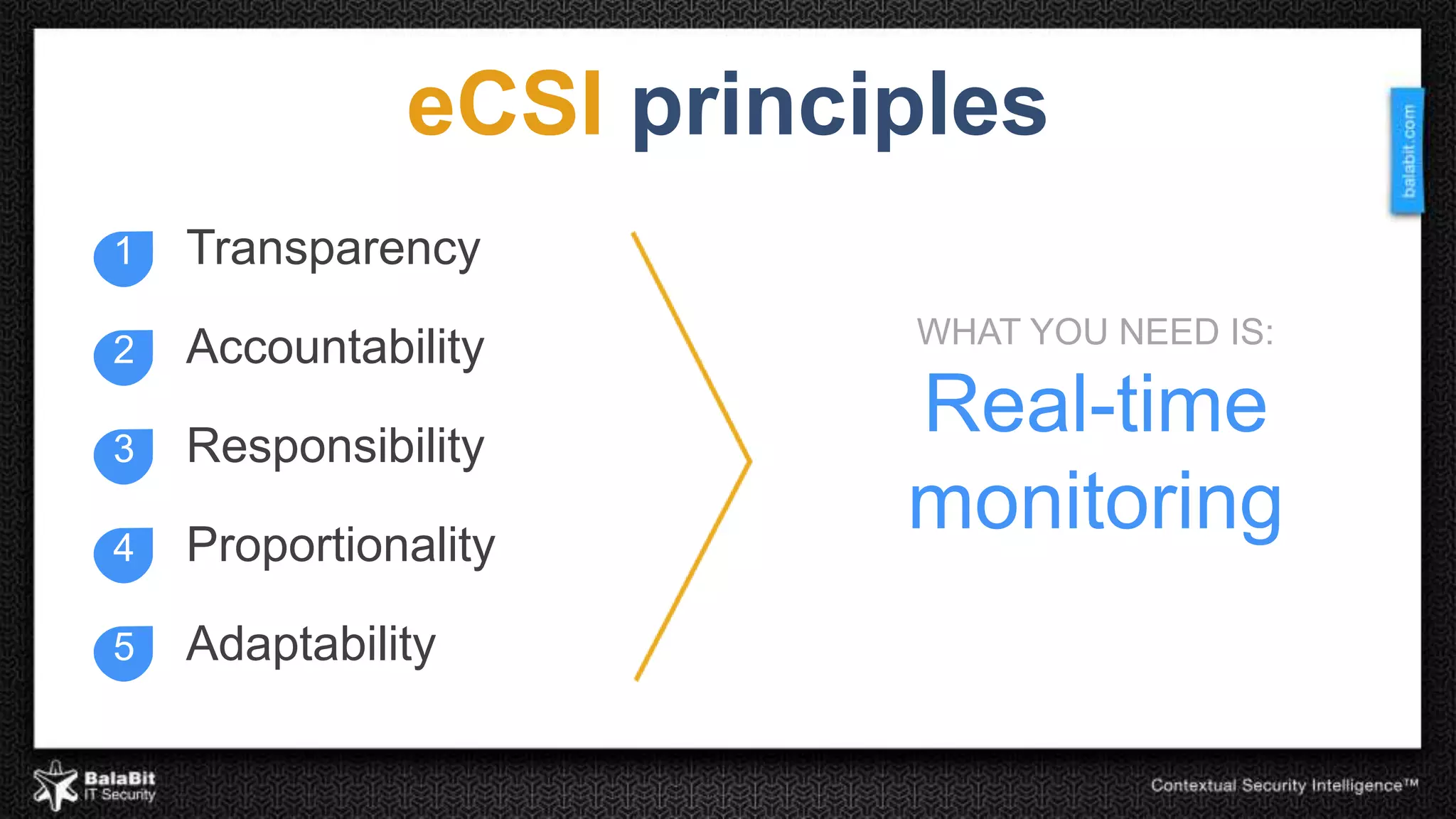
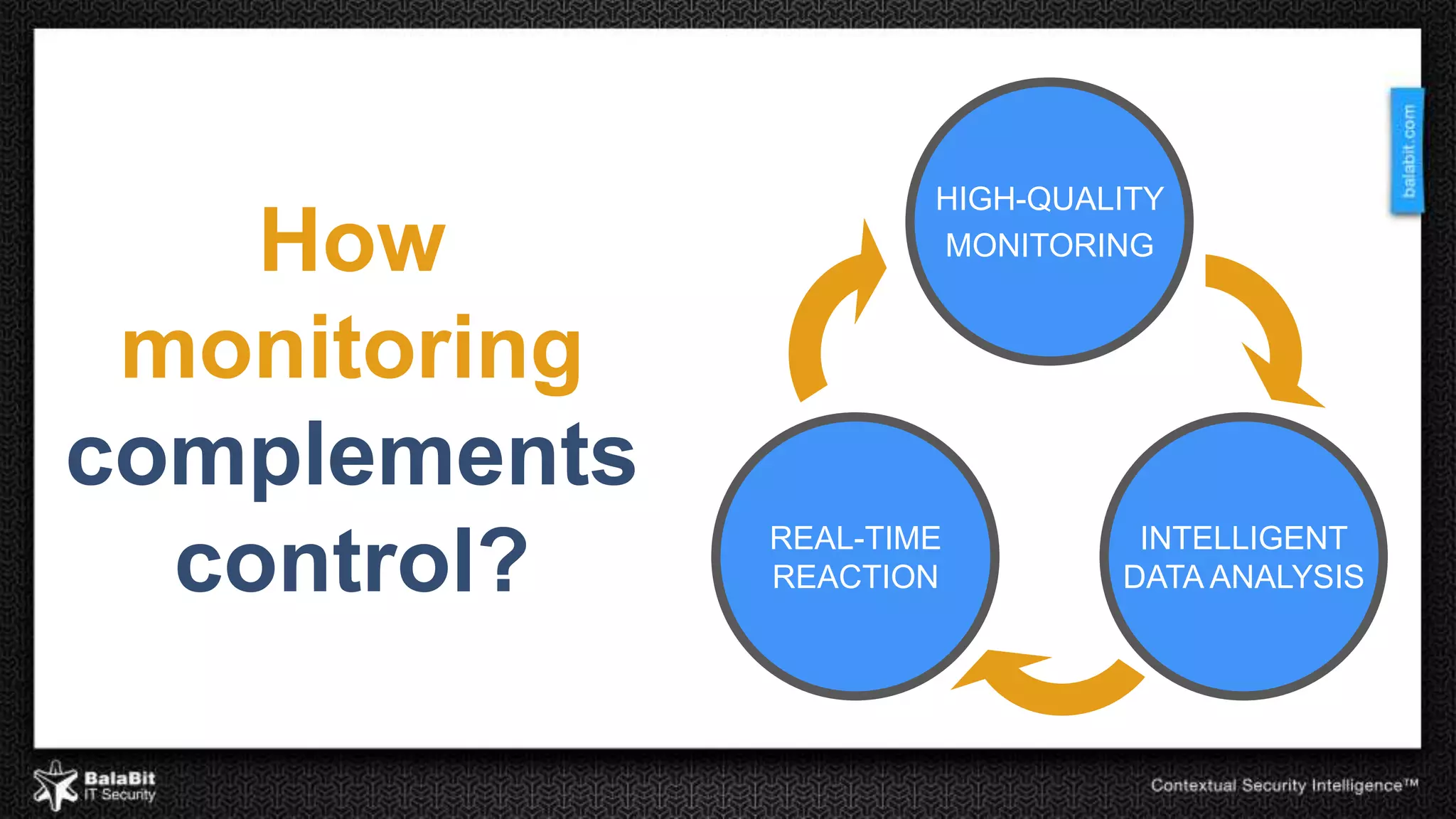
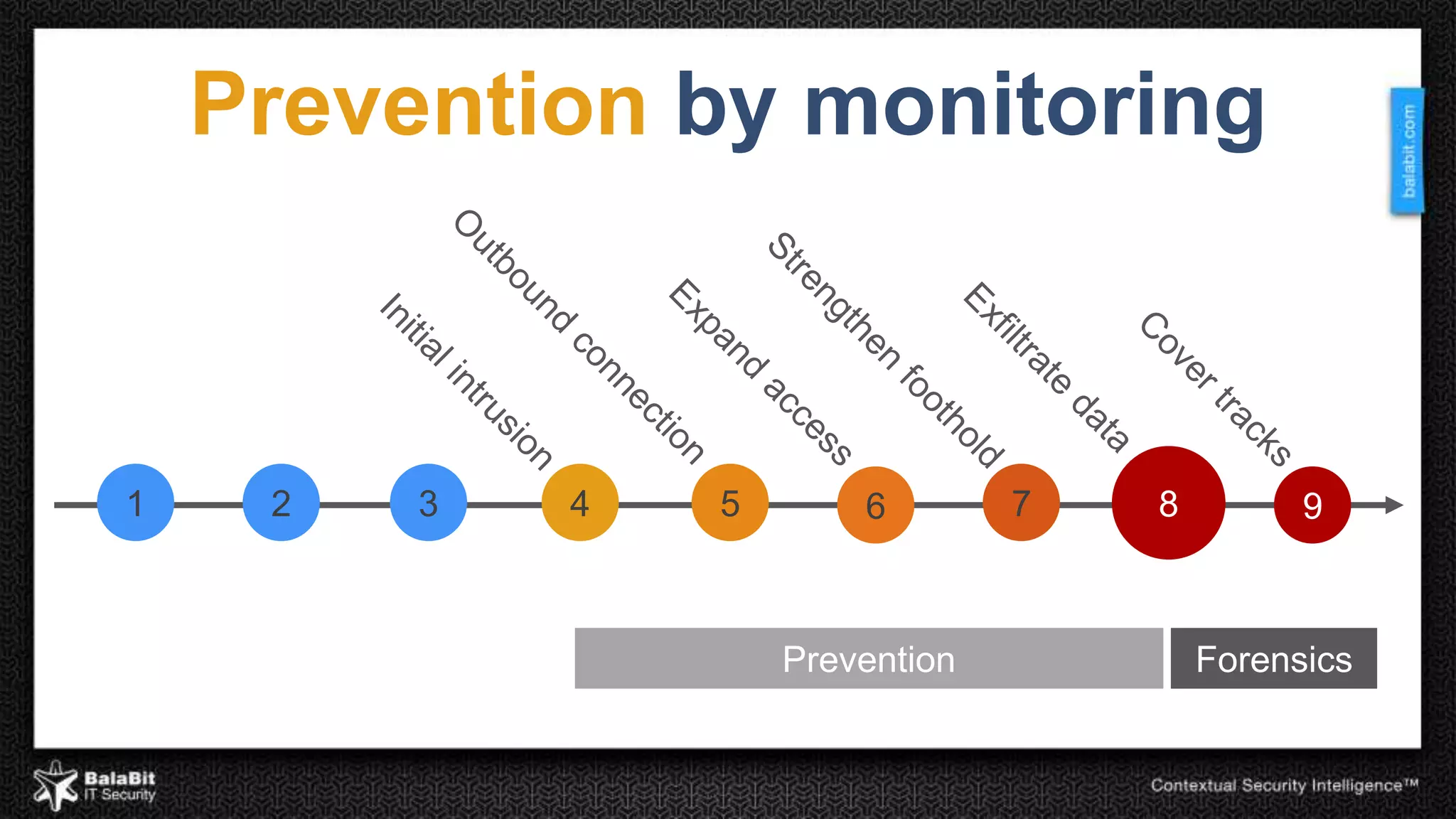
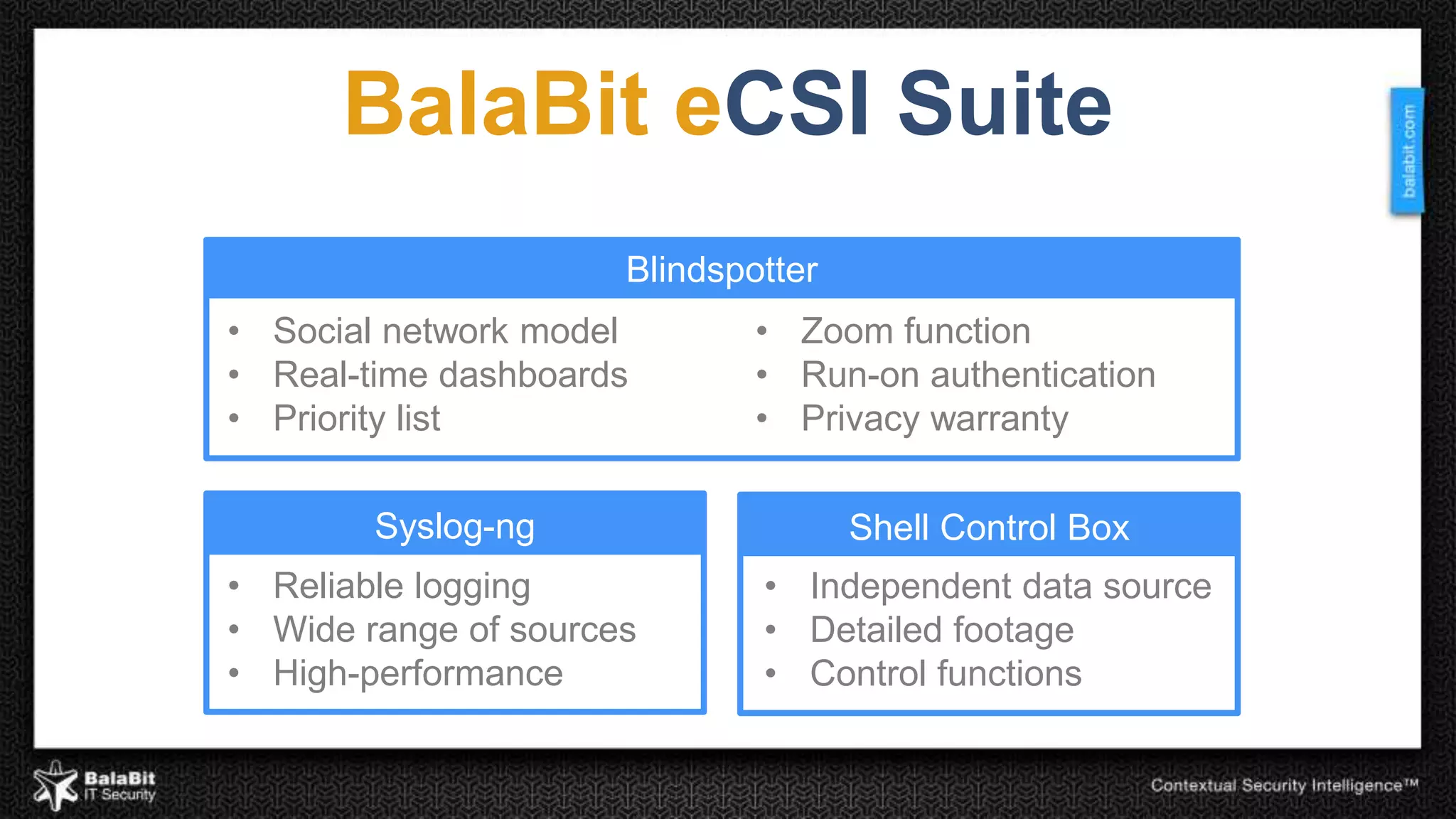
The document discusses the shift from traditional IT security control models to contextual security through real-time monitoring. It advocates a prevention approach using monitoring to complement control. The BalaBit eCSI Suite is presented as a solution that provides reliable logging from multiple sources, high-performance monitoring, and real-time dashboards to enable prevention through intelligent data analysis and monitoring.