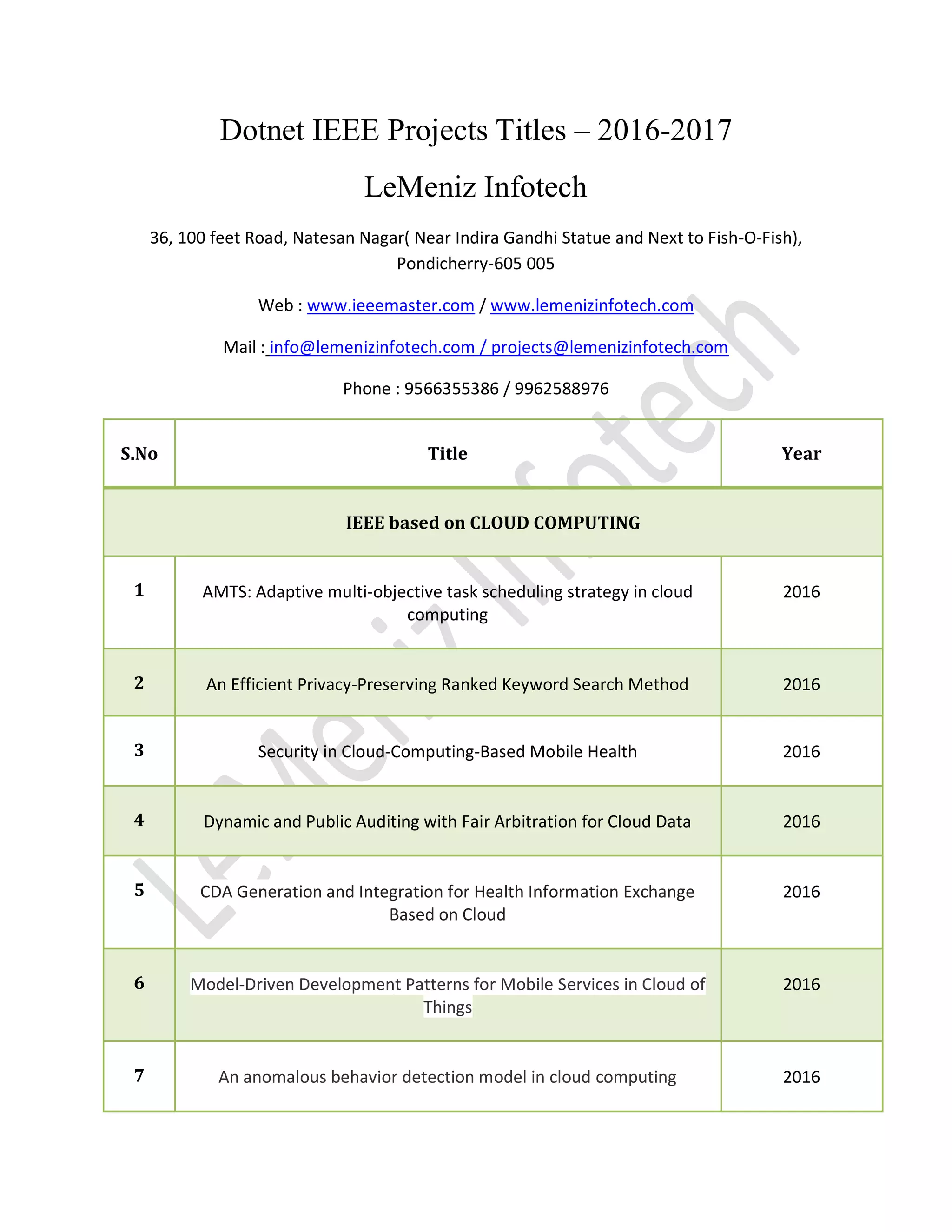
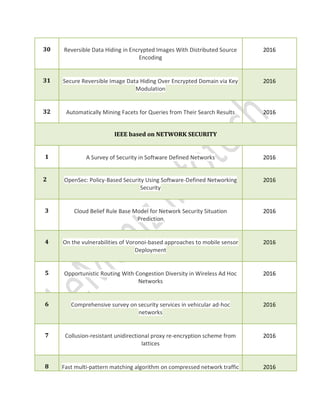
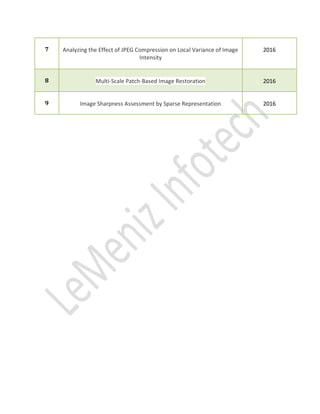
This document lists various IEEE project titles from 2016-2017 related to different fields such as cloud computing, data mining, network security, web mining, secure computing, and image processing. Each project title includes a brief description, highlighting areas like task scheduling, security, data sharing, and machine learning applications. Contact details for the organization, Leminiz Infotech, are provided at the beginning.