The document provides best practices and recommendations for securing resources in AWS. It advises that users should:
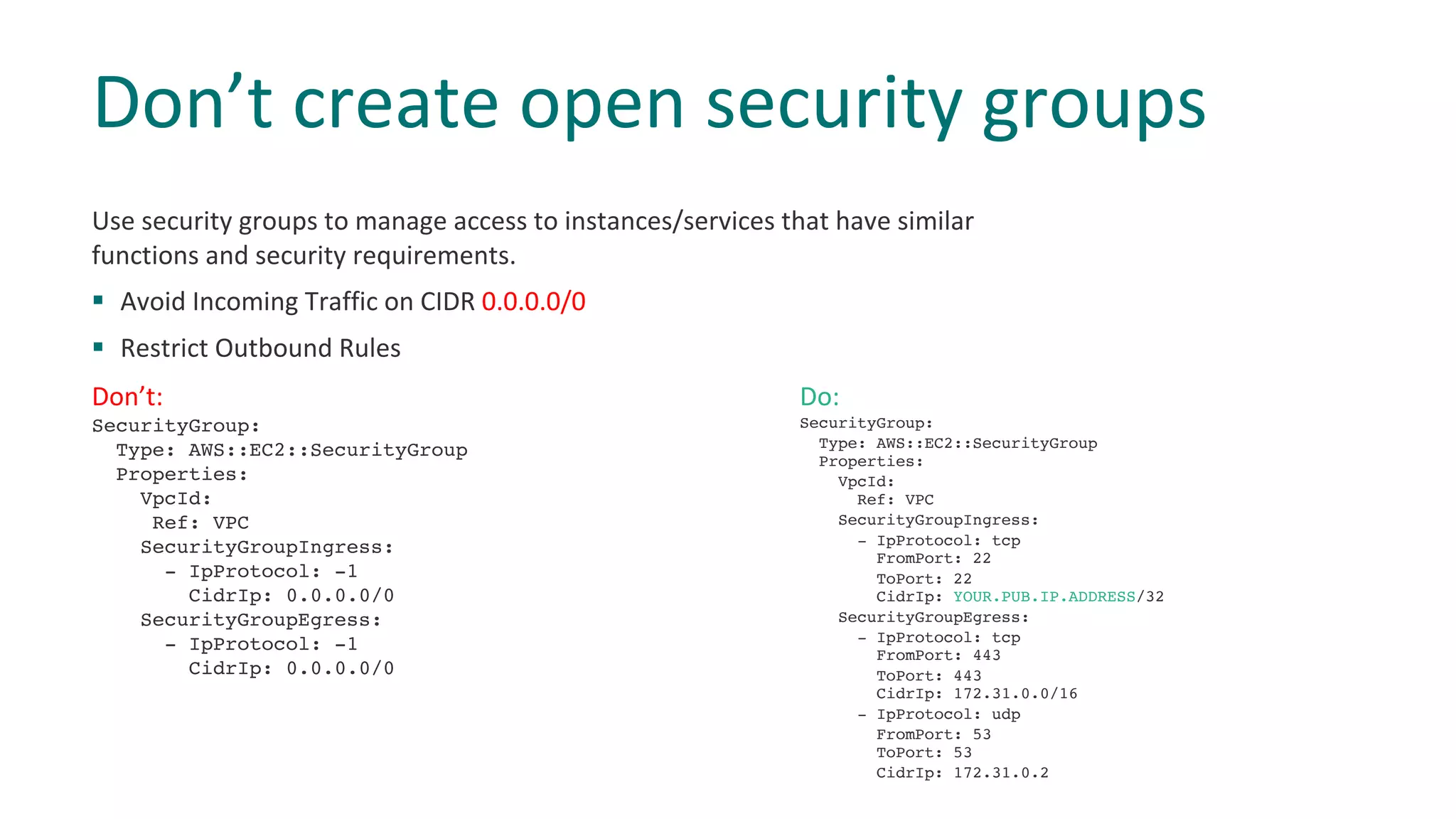
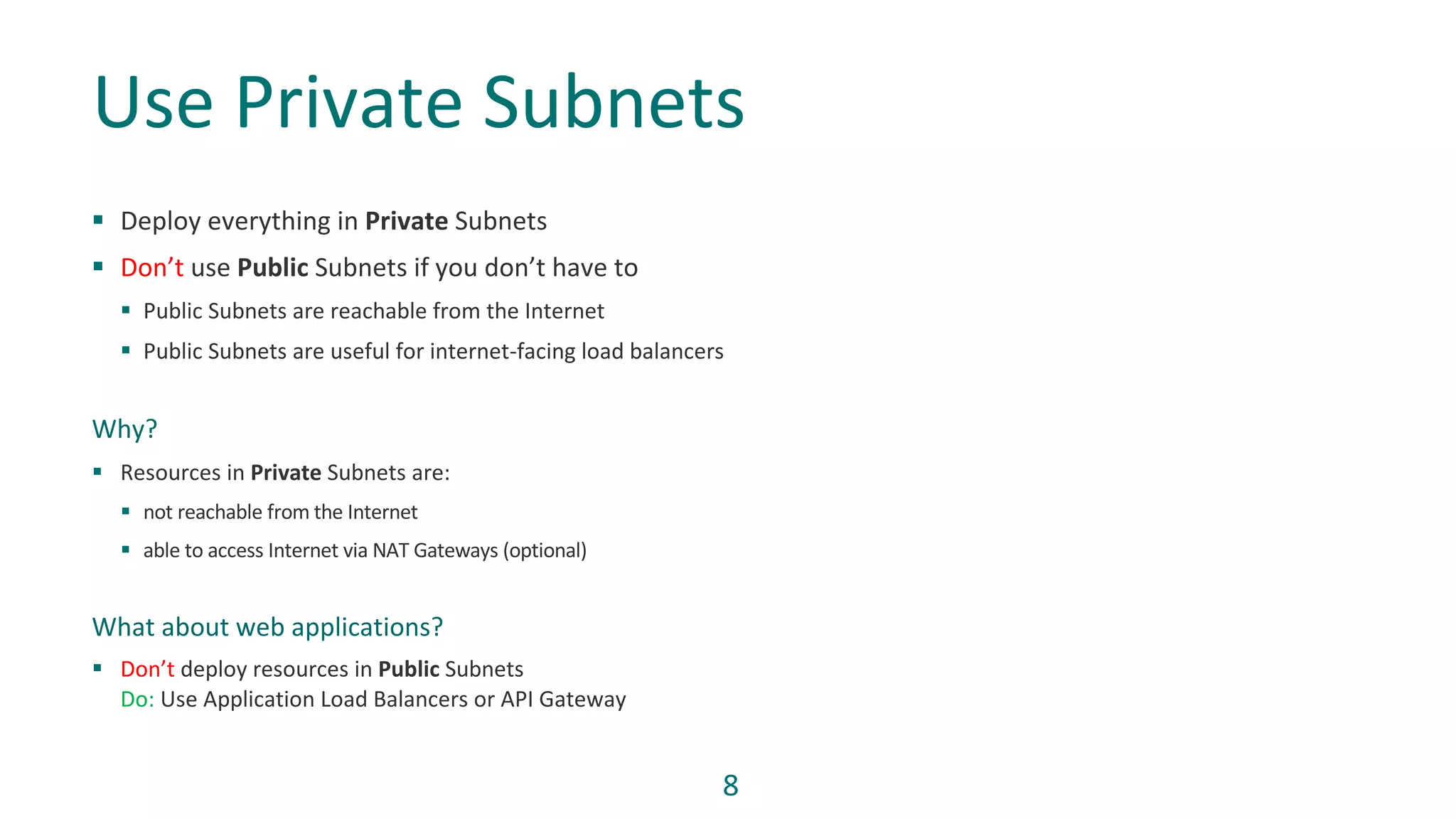
1) Grant least privilege to IAM roles and policies, use private subnets, and avoid public buckets or open security groups.
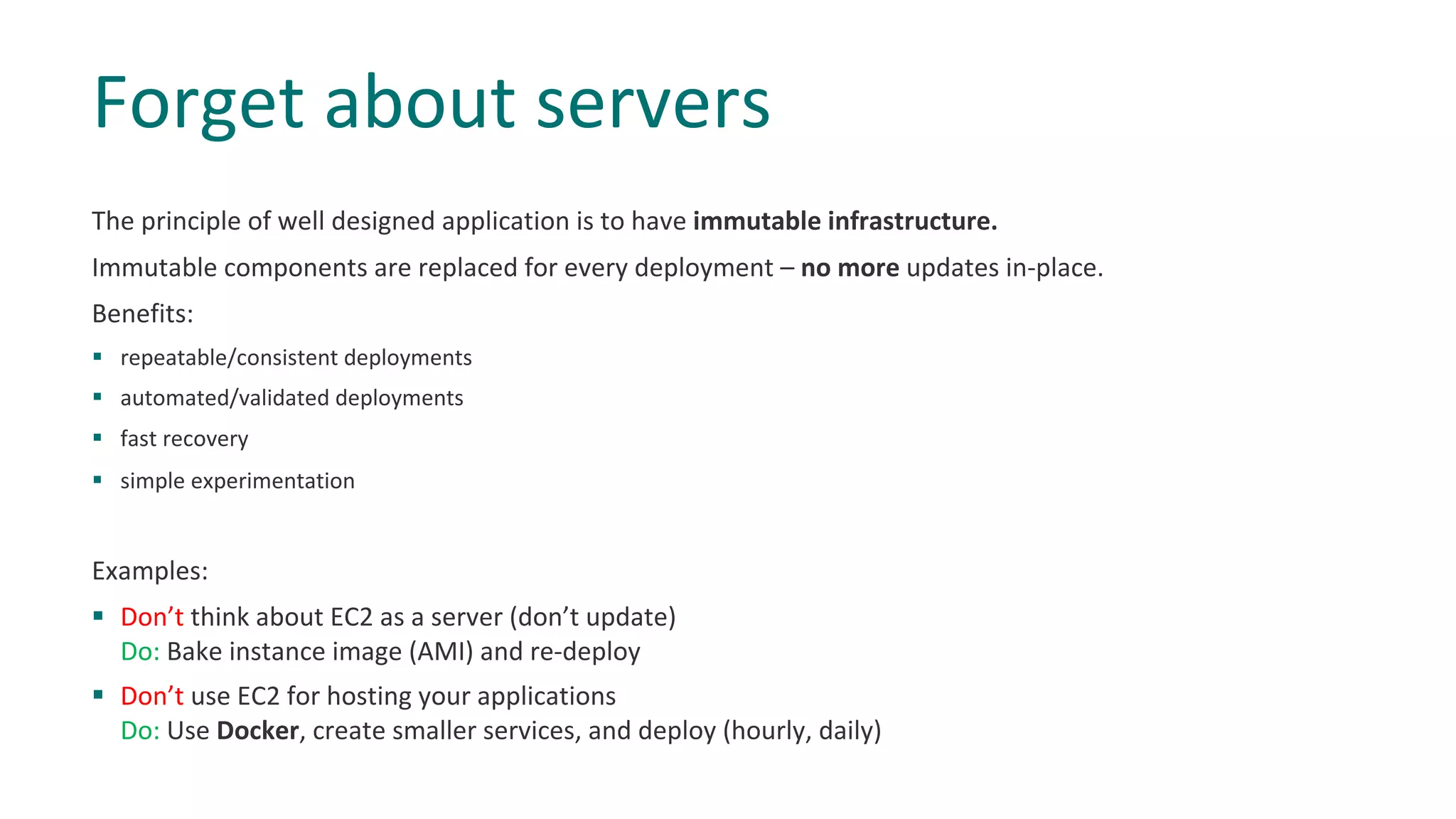
2) Rely on managed AWS services instead of maintaining resources like databases on EC2 instances directly.
3) Implement infrastructure as code and immutable infrastructure to ensure consistency and reliability of deployments.
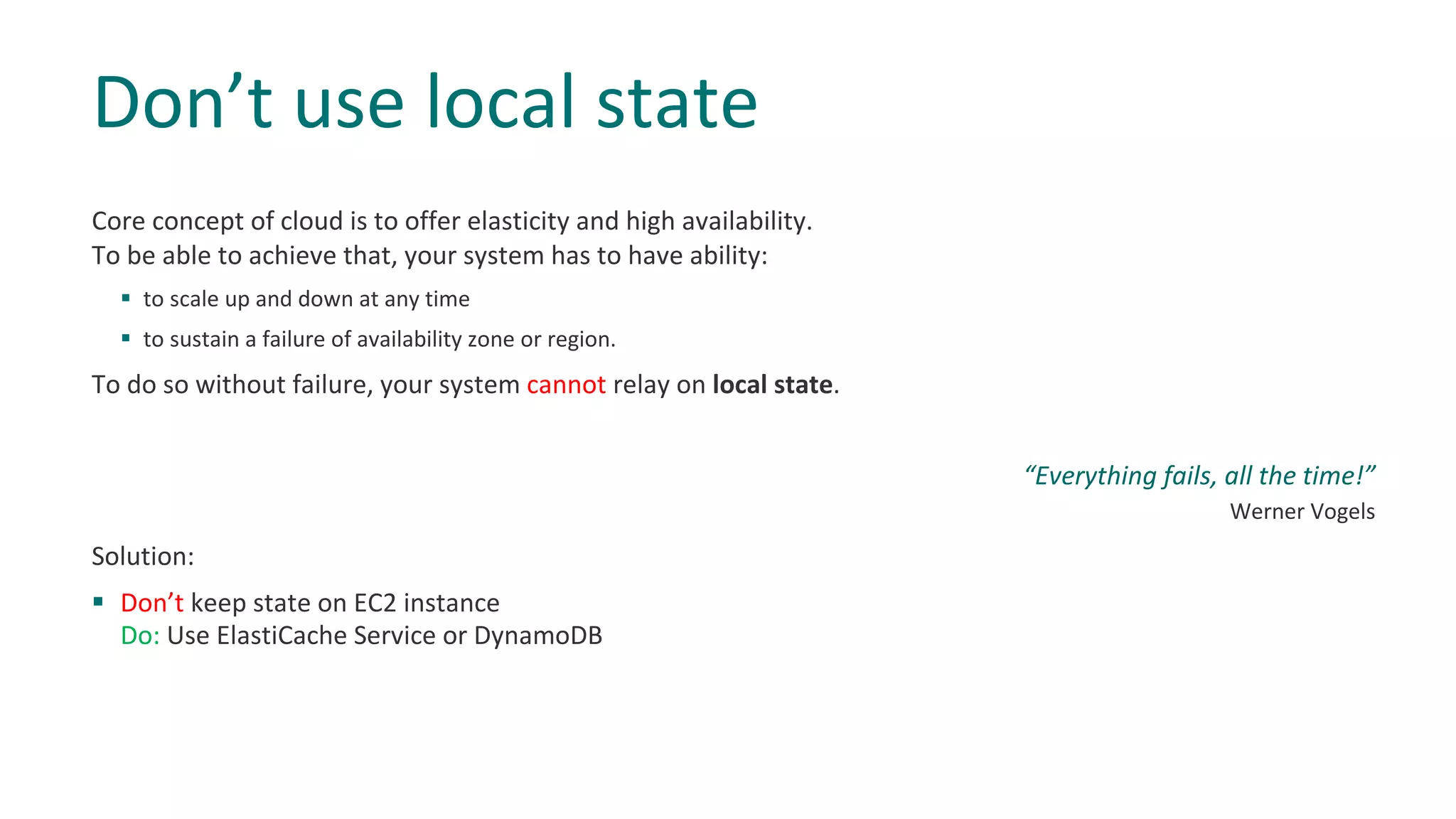
4) Keep application state in services like ElastiCache instead of on individual instances to ensure high availability.
5) Leverage AWS services, documentation, and community resources to continuously improve security practices.


![IAM policies should follow standard security advice:
§ Grant least privilege
§ Start with a minimum set of permissions
§ Add additional permissions when necessary
Grant Least Privileges
Don’t:
{
"Statement": [
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": "*"
}
]
}
Do:
"Statement": [
{
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::<BUCKET-NAME>"
},
{
"Effect": "Allow",
"Action": [
"s3:PutObject",
"s3:GetObject"
],
"Resource": "arn:aws:s3:::<BUCKET-NAME>/*"
}
]](https://image.slidesharecdn.com/dosanddontsaws09102018-181009150604/75/Dos-and-don-ts-in-AWS-5-2048.jpg)