Distil Networks Protecting the Telephony Industry
•
0 likes•67 views
Telephony Fraud is a huge problem, Distil Networks is here to help. Please contact Paul Hobbs +44 (0) 20 3319 6543
Report
Share
Report
Share
Download to read offline
Recommended
Why Speech Recognition Technology is the New Watchword for Enterprise Cyber S...

This presentation intends to underline and correlate how Speech Recognition and Voice Biometrics can unearth and prevent online fraud while ensuring regulatory compliance during customer interactions.
Palo Alto Networks 2016 Cybersecurity Predictions

Palo Alto Networks experts make their predictions for cybersecurity trends in 2016.
45 key vendors and thier online fraud prevention solutions

Cyber security leaders focused on fraud prevention are concerned with fraud losses within organizational risk tolerances and thus want to detect fraud as it happens
Protecting Mobile

James F. Fox, information security practice lead at Booz Allen Hamilton MENA, discusses the critical issue of mobile security, and what it means for telcos.
The Cybercriminal Approach to Mobile Fraud: Now They’re Getting Serious

Mobile devices have been targeted by cybercriminals for over seven years now. However, in 2014 things got serious. Cybercriminals realized that a major portion of eCommerce and online banking is moving to the mobile space, and with that companies are giving clients more options for larger transactions, and actions that were previously only performed on PCs. New PC grade malware appeared on mobile devices, some old PC tricks were transformed for mobile, and new mobile specific threats emerged. In this session we will analyze these threats using multiple customer case studies and Trusteer’s security team research data. We also take a look at the latest mobile threats, threats in development and mitigation tactics.
Digital Transformation and the Role of IAM

We surveyed 200 IT decision makers across four countries
to learn where they are in their journey and the role that identity and access management (IAM) plays in the path to digital transformation.
Enabling a Zero Trust strategy for SMS

Zero Trust is the most effective and reliable way to kill SMS Phishing attacks that lead to online fraud, identity theft and malware attacks.
User authentication-info-graphic

TWO-FACTOR AUTHENTICATION & SMS - Learn how to protect your website and App users from bad guys!
Recommended
Why Speech Recognition Technology is the New Watchword for Enterprise Cyber S...

This presentation intends to underline and correlate how Speech Recognition and Voice Biometrics can unearth and prevent online fraud while ensuring regulatory compliance during customer interactions.
Palo Alto Networks 2016 Cybersecurity Predictions

Palo Alto Networks experts make their predictions for cybersecurity trends in 2016.
45 key vendors and thier online fraud prevention solutions

Cyber security leaders focused on fraud prevention are concerned with fraud losses within organizational risk tolerances and thus want to detect fraud as it happens
Protecting Mobile

James F. Fox, information security practice lead at Booz Allen Hamilton MENA, discusses the critical issue of mobile security, and what it means for telcos.
The Cybercriminal Approach to Mobile Fraud: Now They’re Getting Serious

Mobile devices have been targeted by cybercriminals for over seven years now. However, in 2014 things got serious. Cybercriminals realized that a major portion of eCommerce and online banking is moving to the mobile space, and with that companies are giving clients more options for larger transactions, and actions that were previously only performed on PCs. New PC grade malware appeared on mobile devices, some old PC tricks were transformed for mobile, and new mobile specific threats emerged. In this session we will analyze these threats using multiple customer case studies and Trusteer’s security team research data. We also take a look at the latest mobile threats, threats in development and mitigation tactics.
Digital Transformation and the Role of IAM

We surveyed 200 IT decision makers across four countries
to learn where they are in their journey and the role that identity and access management (IAM) plays in the path to digital transformation.
Enabling a Zero Trust strategy for SMS

Zero Trust is the most effective and reliable way to kill SMS Phishing attacks that lead to online fraud, identity theft and malware attacks.
User authentication-info-graphic

TWO-FACTOR AUTHENTICATION & SMS - Learn how to protect your website and App users from bad guys!
New trends in Payments Security: NFC & Mobile

SISA CEO, Mr. Dharshan Shanthamurthy spoke on new trends in Payments Security at ISACA Bangalore CPE Meet. Visit us at www.sisainfosec.com.
Digital workplace security for gen z

The digital workforce for GenZ must be able to work anytime, anywhere, and via any device. GenZ is mobile first and completely immersed. Hence digital workplace security program should seamlessly identify, detect, protect and respond to cyber threats and allowing employees to securely work anytime, from anywhere
Top 2016 Mobile Security Threats and your Employees

The proliferation of mobile technology brings a potential increase of security threats. As Businesses become more mobile we teardown physical servers and trade them in for virtual space on the cloud. we are opening ourselves up to risk.
Top 7 Mobile Banking Security Tips

Mobile banking has revolutionized the way we manage our bank accounts. Internet banking has made our lives easier by letting us bank from the comfort of our phones, desktops and laptops. But as convenient and easy this technology is, it has its own share of disadvantages. In this presentation, we help you understand:
a. The most common types of mobile banking threats
b. 7 mobile banking security tips to follow
c. How Quick Heal provides a safe and secure mobile banking experience
State of Application Security Vol. 4

Arxan Technologies inforgraphic on the current state of application security.
2015 Mobile Security Trends: Are You Ready?

We’ve been hearing for years now that mobile security threats are coming into their own, both in terms of volume and capacity to inflict harm. Is 2015 the year when organizations will move past their fundamental BYOD debates and start discussing more progressive mobile security topics? Securing the mobile enterprise requires a comprehensive approach that includes securing devices, protecting data, safeguarding applications, and managing access and fraud.
In this session, hear IBM Security experts discuss:
- The latest mobile security trends and challenges
- Real-life customer experiences
- Best practices on building your overall mobile security strategy
View on-demand recording: http://securityintelligence.com/events/2015-mobile-security-trends/
IDC - Security : From Pain To Empowerment

Cette infographie montre comment ont évolué à la fois les perceptions et les réalités de la sécurité en entreprise depuis le début des années 2000.
What are top 7 cyber security trends for 2020

Top 7 Cybersecurity Trends to Look Out For in 2020. Data Breaches as the Top Cyberthreat. The Cybersecurity Skills Gap. Cloud Security Issues. Automation and Integration in Cybersecurity. A Growing Awareness of the Importance of Cybersecurity. Mobile Devices as a Major Cybersecurity Risk.
The New NotCompatible

Over the past two years, Lookout has tracked the evolution of NotCompatible. NotCompatible.C has set a new bar for mobile malware sophistication and operational complexity.
Attack Autopsy: A Study of the Dynamic Attack Chain

View on-demand webinar: https://securityintelligence.com/events/study-of-the-dynamic-attack-chain/
The sophistication of today’s cybersecurity threats is astounding. Attackers have an advanced toolkit and the help of their peers, and the patience of a saint but the motivations of ruthless criminal. What drives them? The thrill of the chase, for some, but mostly it’s your organization’s data. Credit card numbers, healthcare records, and more. If they can find a way in and learn their way around, they’ll take it.
View this on-demand webinar to hear Diana Kelley, security expert and IBM Executive Security Advisor, talk about details of a dynamic attack and share how the investigation unfolds. Diana will also give you an “under the hood” look at the IBM Threat Protection System and you’ll learn how to improve the security health of your organization.
Mobile Banking Security Risks and Consequences iovation2015

View the recorded presentation: https://www.iovation.com/resources/webinars/mobile-banking-security-risks-consequences
Gain insight into the evolution of mobile banking and the risks that accompany this business channel.
The state of mobile app security 

This infographic talks about the latest in mobile app security, the challenges and the best practices to tackle them by building secure mobile apps.
The State of FIDO

Andrew Shikiar, Executive Director & CMO of the FIDO Alliance outlines what FIDO has achieved in the last 7 years, how the market is adopting FIDO, and new expanded work areas focusing on identity verification and binding and the Internet of Things.
The Next Stage of Fraud Protection: IBM Security Trusteer Fraud Protection Suite

View on-demand webinar:
http://event.on24.com/wcc/r/1155218/416359D28E2D43ACB417A8C7C097B3B8
Introducing the Next-Generation Fraud Protection Suite
The financial services industry continues to be plagued by advanced fraud attacks. Sometimes the attacks are successful, resulting in tremendous fraud losses. Virtually always, financial institutions invest significant time and resources to address this continued cyberfraud risk. The fraud protection solutions cobbled together over the past decade suffer from several shortcomings:
Accuracy – statistical risk models generate high false positive alerts, often missing actual fraud
Adaptability – inflexible solutions cannot (or are slow to) react to new threats and new attack methods
Affordability – disparate systems do not leverage pricing incentives and system updates/modifications can be very expensive
Approval – customers are needlessly disrupted by inaccurate risk assessments and the online channel is sub-optimized due to risk concerns
View this on-demand webinar to learn the more about how IBM has taken a fundamentally different approach to fraud protection and management. The IBM Security Trusteer Fraud Protection Suite provides
Evidence-based fraud detection – reduce false positives and missed fraud, leading to better customer experience
Threat-aware authentication – based on actual risk for rapid enforcement
Advanced case management and reporting capabilities – streamline investigations and threat analysis
A powerful remediation tool – quickly remove existing financial malware from infected endpoints
The Whys and Wherefores of Web Security – by United Security Providers

Since the advent of the Internet, cybersecurity has been handed new challenges due to the massively expanded accessibility and interconnectedness of the web. Where once security was considered to be dealt with in a multi-layered manner, now those layers are so fuzzy and expanded as to no longer exist.
By United Security Providers
Malware on Smartphones and Tablets: The Inconvenient Truth

View on-demand webinar: http://ibm.co/21C0aKO
Recent research shows that mobile has become the hackers’ new playground. However, most users and IT professionals do not think this is a real and substantial threat.
In this on-demand session, we will outline the broad scope of risk that mobile malware poses today on iOS and Android, and explain the potential business threats. The enterprise is at a critical juncture where advanced cyber-attacks targeting mobile users are now threatening both corporate and personal information.
Listen in to IBM Security product specialist, Shaked Vax to learn how to reduce risk of data leakage and protect against malicious activity with a comprehensive approach that combines enterprise mobility management (EMM) and mobile threat management.
Top Security Threats to Look Out for in 2023

Top Security Threats to Look Out for in 2023
https://bit.ly/3GVoYfL | Visit: https://www.k7computing.com
More Related Content
What's hot
New trends in Payments Security: NFC & Mobile

SISA CEO, Mr. Dharshan Shanthamurthy spoke on new trends in Payments Security at ISACA Bangalore CPE Meet. Visit us at www.sisainfosec.com.
Digital workplace security for gen z

The digital workforce for GenZ must be able to work anytime, anywhere, and via any device. GenZ is mobile first and completely immersed. Hence digital workplace security program should seamlessly identify, detect, protect and respond to cyber threats and allowing employees to securely work anytime, from anywhere
Top 2016 Mobile Security Threats and your Employees

The proliferation of mobile technology brings a potential increase of security threats. As Businesses become more mobile we teardown physical servers and trade them in for virtual space on the cloud. we are opening ourselves up to risk.
Top 7 Mobile Banking Security Tips

Mobile banking has revolutionized the way we manage our bank accounts. Internet banking has made our lives easier by letting us bank from the comfort of our phones, desktops and laptops. But as convenient and easy this technology is, it has its own share of disadvantages. In this presentation, we help you understand:
a. The most common types of mobile banking threats
b. 7 mobile banking security tips to follow
c. How Quick Heal provides a safe and secure mobile banking experience
State of Application Security Vol. 4

Arxan Technologies inforgraphic on the current state of application security.
2015 Mobile Security Trends: Are You Ready?

We’ve been hearing for years now that mobile security threats are coming into their own, both in terms of volume and capacity to inflict harm. Is 2015 the year when organizations will move past their fundamental BYOD debates and start discussing more progressive mobile security topics? Securing the mobile enterprise requires a comprehensive approach that includes securing devices, protecting data, safeguarding applications, and managing access and fraud.
In this session, hear IBM Security experts discuss:
- The latest mobile security trends and challenges
- Real-life customer experiences
- Best practices on building your overall mobile security strategy
View on-demand recording: http://securityintelligence.com/events/2015-mobile-security-trends/
IDC - Security : From Pain To Empowerment

Cette infographie montre comment ont évolué à la fois les perceptions et les réalités de la sécurité en entreprise depuis le début des années 2000.
What are top 7 cyber security trends for 2020

Top 7 Cybersecurity Trends to Look Out For in 2020. Data Breaches as the Top Cyberthreat. The Cybersecurity Skills Gap. Cloud Security Issues. Automation and Integration in Cybersecurity. A Growing Awareness of the Importance of Cybersecurity. Mobile Devices as a Major Cybersecurity Risk.
The New NotCompatible

Over the past two years, Lookout has tracked the evolution of NotCompatible. NotCompatible.C has set a new bar for mobile malware sophistication and operational complexity.
Attack Autopsy: A Study of the Dynamic Attack Chain

View on-demand webinar: https://securityintelligence.com/events/study-of-the-dynamic-attack-chain/
The sophistication of today’s cybersecurity threats is astounding. Attackers have an advanced toolkit and the help of their peers, and the patience of a saint but the motivations of ruthless criminal. What drives them? The thrill of the chase, for some, but mostly it’s your organization’s data. Credit card numbers, healthcare records, and more. If they can find a way in and learn their way around, they’ll take it.
View this on-demand webinar to hear Diana Kelley, security expert and IBM Executive Security Advisor, talk about details of a dynamic attack and share how the investigation unfolds. Diana will also give you an “under the hood” look at the IBM Threat Protection System and you’ll learn how to improve the security health of your organization.
Mobile Banking Security Risks and Consequences iovation2015

View the recorded presentation: https://www.iovation.com/resources/webinars/mobile-banking-security-risks-consequences
Gain insight into the evolution of mobile banking and the risks that accompany this business channel.
The state of mobile app security 

This infographic talks about the latest in mobile app security, the challenges and the best practices to tackle them by building secure mobile apps.
The State of FIDO

Andrew Shikiar, Executive Director & CMO of the FIDO Alliance outlines what FIDO has achieved in the last 7 years, how the market is adopting FIDO, and new expanded work areas focusing on identity verification and binding and the Internet of Things.
The Next Stage of Fraud Protection: IBM Security Trusteer Fraud Protection Suite

View on-demand webinar:
http://event.on24.com/wcc/r/1155218/416359D28E2D43ACB417A8C7C097B3B8
Introducing the Next-Generation Fraud Protection Suite
The financial services industry continues to be plagued by advanced fraud attacks. Sometimes the attacks are successful, resulting in tremendous fraud losses. Virtually always, financial institutions invest significant time and resources to address this continued cyberfraud risk. The fraud protection solutions cobbled together over the past decade suffer from several shortcomings:
Accuracy – statistical risk models generate high false positive alerts, often missing actual fraud
Adaptability – inflexible solutions cannot (or are slow to) react to new threats and new attack methods
Affordability – disparate systems do not leverage pricing incentives and system updates/modifications can be very expensive
Approval – customers are needlessly disrupted by inaccurate risk assessments and the online channel is sub-optimized due to risk concerns
View this on-demand webinar to learn the more about how IBM has taken a fundamentally different approach to fraud protection and management. The IBM Security Trusteer Fraud Protection Suite provides
Evidence-based fraud detection – reduce false positives and missed fraud, leading to better customer experience
Threat-aware authentication – based on actual risk for rapid enforcement
Advanced case management and reporting capabilities – streamline investigations and threat analysis
A powerful remediation tool – quickly remove existing financial malware from infected endpoints
The Whys and Wherefores of Web Security – by United Security Providers

Since the advent of the Internet, cybersecurity has been handed new challenges due to the massively expanded accessibility and interconnectedness of the web. Where once security was considered to be dealt with in a multi-layered manner, now those layers are so fuzzy and expanded as to no longer exist.
By United Security Providers
Malware on Smartphones and Tablets: The Inconvenient Truth

View on-demand webinar: http://ibm.co/21C0aKO
Recent research shows that mobile has become the hackers’ new playground. However, most users and IT professionals do not think this is a real and substantial threat.
In this on-demand session, we will outline the broad scope of risk that mobile malware poses today on iOS and Android, and explain the potential business threats. The enterprise is at a critical juncture where advanced cyber-attacks targeting mobile users are now threatening both corporate and personal information.
Listen in to IBM Security product specialist, Shaked Vax to learn how to reduce risk of data leakage and protect against malicious activity with a comprehensive approach that combines enterprise mobility management (EMM) and mobile threat management.
What's hot (20)
Top 2016 Mobile Security Threats and your Employees

Top 2016 Mobile Security Threats and your Employees
Cataleya-Security-Feature_SAWC_April2016page-20-23

Cataleya-Security-Feature_SAWC_April2016page-20-23
Attack Autopsy: A Study of the Dynamic Attack Chain

Attack Autopsy: A Study of the Dynamic Attack Chain
Mobile Banking Security Risks and Consequences iovation2015

Mobile Banking Security Risks and Consequences iovation2015
Updated Cyber Security and Fraud Prevention Tools Tactics

Updated Cyber Security and Fraud Prevention Tools Tactics
The Next Stage of Fraud Protection: IBM Security Trusteer Fraud Protection Suite

The Next Stage of Fraud Protection: IBM Security Trusteer Fraud Protection Suite
The Whys and Wherefores of Web Security – by United Security Providers

The Whys and Wherefores of Web Security – by United Security Providers
Malware on Smartphones and Tablets: The Inconvenient Truth

Malware on Smartphones and Tablets: The Inconvenient Truth
Similar to Distil Networks Protecting the Telephony Industry
Top Security Threats to Look Out for in 2023

Top Security Threats to Look Out for in 2023
https://bit.ly/3GVoYfL | Visit: https://www.k7computing.com
Mobile Payments: Protecting Apps and Data from Emerging Risks

Arxan Technologies, FS-ISAC, and IBM joined forces to deliver a presentation on how to protect your applications and data from emerging risks. This session will cover:
- The threat landscape regarding mobile payments
- How cybercriminals can hack your applications
- Comprehensive prevention and protection techniques
Borderless Breaches and Migrating Malware: How Cybercrime is Breaking Down Ba...

View On-Demand Webinar: https://event.on24.com/eventRegistration/EventLobbyServlet?target=reg20.jsp&referrer=&eventid=1139921&sessionid=1&key=993ECF370F9F3C594E6E3F44A0FA6BA2®Tag=13522&sourcepage=register
2015 was peppered with mega-breaches of highly sensitive data like personal health information and private bedroom behaviors. and companies of all sizes need to pay attention to security basics to stop the infiltration of attackers and protect their data.
Cybercriminals’ targets are now bigger and their rewards greater as they fine-tune efforts to obtain and leverage higher value data than years’ past.
New attack techniques like mobile overlay malware are gaining, while “classic” attacks like DDoS and POS malware continue to be effective due to lackluster practice in security fundamentals.
Malware leaps across target countries are indicative of increasing sophistication and organization in cybercrime rings.
In the 2016 edition of the IBM X-Force Threat Intelligence Report, IBM security research experts examine the macro trends that affected the industry, what to expect in 2016, and recommendations on how you can protect your digital assets.
How to build a highly secure fin tech application

Indeed, The FinTech industry is a specific sector where developing a successful mobile solution necessitates some extraordinary measures to capture clients’ loyalty. The takeaway is that a good FinTech app is more than simply an excellent companion.
Why is cyber security a disruption in the digital economy

As we enter the digital economy, companies will quickly realize that the differentiator in the digital economy is information and information being a valuable resource is subject to theft, hacking, phishing and a host of other issues which compromise a company’s ability to participate in the digital economy. Cybersecurity misfires compromise the trust of buyers and partners necessary to participate in the digital economy. It is up to every company to ensure that the information shared with them is protected to the best of their ability and proactively notify persons and organizations who entrust their information necessary to transact business (any personal identity information including but not limited to addresses, credit card information, social security numbers, account information, credit information, medical records, etc.) with any potential compromises which can yield harm to them by that information either being used maliciously or shared with others.
The digital economy is different than other versions of commerce because in the digital economy, information is the lifeblood of digital commerce that passes through the hands of many platforms involved in a digital event. Each of these platforms are an opportunity to wreak havoc on your well-intended but incomplete intents to protect the information contained within the network you control. In the digital economy, it is not only the network you control, but the platforms that touch the personal data entrusted to you as a means of enabling digital commerce, and several techniques have begun to emerge to protect personal information contained within your information domain and the domain of platforms participating in digital commerce.
Because the life blood of the digital economy is information, information hacked in the digital economy is akin to shrinkage in the legacy economy. Both are means to directly attack your bottom line, whether it is redirecting customers elsewhere because they don’t trust your privacy program, ransomware which makes your site or one of your partner platform sites dangerous to use or some other reason which challenges your ability to participate in the digital economy. Shrinking the potential market share because of information safety and security challenges is a disruption, making cyber-security a disruptive activity, particularly if it is not dealt with swiftly.
If your cyber-security program is focused entirely on protecting the information housed in your four walls, you have exposed yourself to problems you will have difficulty in identifying both the source and the entry point of these issues.
Cyber security fundamentals (Cantonese)

Are you aware of the current security threats to your business? Are you prepared to handle the next big DDoS attack? What can you do to be prepared?
Join this webinar to learn about:
- Growing threat landscape
- Challenges to a successful security strategy
- Business impact of attacks
- Securing web applications from attacks
Commercial Real Estate - Cyber Risk 2020

Commercial real estate has always been an attractive cyber target offering sophisticated hackers a wealth of personal information store in banking, lease, and employment records and multiple transaction points. Enter COVID-19. Almost overnight, nearly all routine activities are tied to remote capabilities. Now, it’s cyber threat and cyber risk on steroids. Here's a cyber professional’s view of the situation and links to several additional resources.
Countering Cyber Threats By Monitoring “Normal” Website Behavior

Have you considered using big data to protect against cyber threats? Savvy CSOs are doing just that-leveraging hoards of web traffic data to model normal online behavior and then use that insight to counter attempts at business-logic abuse. Check out this informative technology dossier to explore the ins and outs of using big data analysis and web-user profiling to protect your company against cyber threats.
Centrify rethink security brochure

Think differently about security. Perimeter defenses are failing to protect customers. Hackers are getting smarter, more persistent and better organized. So must you.
Verizon DMS' Bot Mitigation from Paul Hobbs

Bot Mitigation, help protect log in pages, API's and applications from Automation, Account takeover and fraud.
Securing Mobile Banking Apps - You Are Only as Strong as Your Weakest Link

The mobile banking and payments opportunity for financial institutions is tremendous, and those who offer the most secure apps will prevail over the competition. But this opportunity is not without hazards, and the effect on revenue and brand caused by hackers can be devastating.
In this webinar, IBM Security Trusteer and Arxan focuson the mobile threat landscape and leading protection techniques to safeguard mobile payments and apps.
Industry experts from IBM Security Trusteer and Arxan review:
The changes in technology that have made mobile applications so vulnerable
Emerging mobile threat vectors and what you can do to mitigate the risks
Musts for the future of your security model
View the on-demand recording: http://arxan.wistia.com/medias/036z0iw7y1
Secure your Voice over IP (VoIP)

Tough most people are often unaware of such hacking, ‘phreaking’ (e.g. phone hacking) is a real curse. Find out how to protect yourself.
Top cybersecurity trends to adapt in 2022

As a result of the pandemic's transition to remote work, companies have become more exposed to malicious assaults. To combat such attacks, you must keep a close eye on developing cybersecurity trends. The main cybersecurity trends for 2022 will be discussed in this article.
Read more: https://www.cigniti.com/blog/cybersecurity-trends-2022/
How AI is impacting digital identity security.pdf

AI is revolutionizing digital identity security by enhancing authentication methods, detecting anomalies, and preventing fraud with its ability to analyze vast data sets and recognize patterns accurately.
Website : https://vlinkinc-my.sharepoint.com/:w:/g/personal/vipul_bhardwaj_vlinkinfo_com/EaQPA2UFPuxKomhOXisVC40Bmj4Jvbu6Zx5XRvmCfNJMSQ?e=cjJXCt
Accounting for Cyber Risks - How much does Cyber actually cost the Industry?

A presentation made to 2018 Asian Insurers’ CFO Summit
Protecting Autonomous Vehicles and Connected Services with Software Defined P...

Cybersecurity is one of the biggest challenges for autonomous vehicles due to a large number of Internet-enabled software systems. The high dependence on Internet connectivity for navigation, telematics and information services makes autonomous vehicles highly vulnerable to network-based cyber attacks. For example, Denial of Service (DoS) attacks can block autonomous vehicles from receiving critical over-the-air (OTA) updates while connection hacking can be used to tamper software or re-task OTA instructions. Additionally, the automotive industry’s global supply chain is vulnerable to malware that propagates to critical vehicle systems from cloud environments. In response to the potential loss of life due to cyber attacks, the US government is introducing new legislation that mandates strict cybersecurity requirements for all networked software. This webinar will introduce participants to a new cybersecurity architecture called Software Defined Perimeter (SDP) that provides OEMs and application developers a framework to meet emerging government requirements to ensure safe autonomous vehicle operations. SDP utilizes a control channel to verify the identity and integrity of hardware and software systems before allowing automotive OTA transactions. Additionally, SDP’s application-aware connectivity ensures that malware cannot propagate through network connections.
Key Take-Aways:
Why are the existing cybersecurity solutions not suitable for the current auto industry?
How can SDP meet the new US government auto cybersecurity requirements?
Why the automotive industry should embrace SDP as a key technology for the next-generation cybersecurity solution?
21 Cybersecurity Companies You Need to Know.pptx

Cybersecurity guards against cyber-attacks on Internet-connected systems, including hardware, software, and data.
Similar to Distil Networks Protecting the Telephony Industry (20)
Five Network Security Threats And How To Protect Your Business Wp101112

Five Network Security Threats And How To Protect Your Business Wp101112
Mobile Payments: Protecting Apps and Data from Emerging Risks

Mobile Payments: Protecting Apps and Data from Emerging Risks
Borderless Breaches and Migrating Malware: How Cybercrime is Breaking Down Ba...

Borderless Breaches and Migrating Malware: How Cybercrime is Breaking Down Ba...
Why is cyber security a disruption in the digital economy

Why is cyber security a disruption in the digital economy
Countering Cyber Threats By Monitoring “Normal” Website Behavior

Countering Cyber Threats By Monitoring “Normal” Website Behavior
Securing Mobile Banking Apps - You Are Only as Strong as Your Weakest Link

Securing Mobile Banking Apps - You Are Only as Strong as Your Weakest Link
Accounting for Cyber Risks - How much does Cyber actually cost the Industry?

Accounting for Cyber Risks - How much does Cyber actually cost the Industry?
Protecting Autonomous Vehicles and Connected Services with Software Defined P...

Protecting Autonomous Vehicles and Connected Services with Software Defined P...
Recently uploaded
Securing your Kubernetes cluster_ a step-by-step guide to success !

Today, after several years of existence, an extremely active community and an ultra-dynamic ecosystem, Kubernetes has established itself as the de facto standard in container orchestration. Thanks to a wide range of managed services, it has never been so easy to set up a ready-to-use Kubernetes cluster.
However, this ease of use means that the subject of security in Kubernetes is often left for later, or even neglected. This exposes companies to significant risks.
In this talk, I'll show you step-by-step how to secure your Kubernetes cluster for greater peace of mind and reliability.
PHP Frameworks: I want to break free (IPC Berlin 2024)

In this presentation, we examine the challenges and limitations of relying too heavily on PHP frameworks in web development. We discuss the history of PHP and its frameworks to understand how this dependence has evolved. The focus will be on providing concrete tips and strategies to reduce reliance on these frameworks, based on real-world examples and practical considerations. The goal is to equip developers with the skills and knowledge to create more flexible and future-proof web applications. We'll explore the importance of maintaining autonomy in a rapidly changing tech landscape and how to make informed decisions in PHP development.
This talk is aimed at encouraging a more independent approach to using PHP frameworks, moving towards a more flexible and future-proof approach to PHP development.
Video Streaming: Then, Now, and in the Future

In his public lecture, Christian Timmerer provides insights into the fascinating history of video streaming, starting from its humble beginnings before YouTube to the groundbreaking technologies that now dominate platforms like Netflix and ORF ON. Timmerer also presents provocative contributions of his own that have significantly influenced the industry. He concludes by looking at future challenges and invites the audience to join in a discussion.
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

The publishing industry has been selling digital audiobooks and ebooks for over a decade and has found its groove. What’s changed? What has stayed the same? Where do we go from here? Join a group of leading sales peers from across the industry for a conversation about the lessons learned since the popularization of digital books, best practices, digital book supply chain management, and more.
Link to video recording: https://bnctechforum.ca/sessions/selling-digital-books-in-2024-insights-from-industry-leaders/
Presented by BookNet Canada on May 28, 2024, with support from the Department of Canadian Heritage.
Communications Mining Series - Zero to Hero - Session 1

This session provides introduction to UiPath Communication Mining, importance and platform overview. You will acquire a good understand of the phases in Communication Mining as we go over the platform with you. Topics covered:
• Communication Mining Overview
• Why is it important?
• How can it help today’s business and the benefits
• Phases in Communication Mining
• Demo on Platform overview
• Q/A
Elevating Tactical DDD Patterns Through Object Calisthenics

After immersing yourself in the blue book and its red counterpart, attending DDD-focused conferences, and applying tactical patterns, you're left with a crucial question: How do I ensure my design is effective? Tactical patterns within Domain-Driven Design (DDD) serve as guiding principles for creating clear and manageable domain models. However, achieving success with these patterns requires additional guidance. Interestingly, we've observed that a set of constraints initially designed for training purposes remarkably aligns with effective pattern implementation, offering a more ‘mechanical’ approach. Let's explore together how Object Calisthenics can elevate the design of your tactical DDD patterns, offering concrete help for those venturing into DDD for the first time!
Microsoft - Power Platform_G.Aspiotis.pdf

Revolutionizing Application Development
with AI-powered low-code, presentation by George Aspiotis, Sr. Partner Development Manager, Microsoft
20240605 QFM017 Machine Intelligence Reading List May 2024

Everything I found interesting about machines behaving intelligently during May 2024
GraphRAG is All You need? LLM & Knowledge Graph

Guy Korland, CEO and Co-founder of FalkorDB, will review two articles on the integration of language models with knowledge graphs.
1. Unifying Large Language Models and Knowledge Graphs: A Roadmap.
https://arxiv.org/abs/2306.08302
2. Microsoft Research's GraphRAG paper and a review paper on various uses of knowledge graphs:
https://www.microsoft.com/en-us/research/blog/graphrag-unlocking-llm-discovery-on-narrative-private-data/
National Security Agency - NSA mobile device best practices

Threats to mobile devices are more prevalent and increasing in scope and complexity. Users of mobile devices desire to take full advantage of the features
available on those devices, but many of the features provide convenience and capability but sacrifice security. This best practices guide outlines steps the users can take to better protect personal devices and information.
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

Sudheer Mechineni, Head of Application Frameworks, Standard Chartered Bank
Discover how Standard Chartered Bank harnessed the power of Neo4j to transform complex data access challenges into a dynamic, scalable graph database solution. This keynote will cover their journey from initial adoption to deploying a fully automated, enterprise-grade causal cluster, highlighting key strategies for modelling organisational changes and ensuring robust disaster recovery. Learn how these innovations have not only enhanced Standard Chartered Bank’s data infrastructure but also positioned them as pioneers in the banking sector’s adoption of graph technology.
By Design, not by Accident - Agile Venture Bolzano 2024

As presented at the Agile Venture Bolzano, 4.06.2024
Epistemic Interaction - tuning interfaces to provide information for AI support

Paper presented at SYNERGY workshop at AVI 2024, Genoa, Italy. 3rd June 2024
https://alandix.com/academic/papers/synergy2024-epistemic/
As machine learning integrates deeper into human-computer interactions, the concept of epistemic interaction emerges, aiming to refine these interactions to enhance system adaptability. This approach encourages minor, intentional adjustments in user behaviour to enrich the data available for system learning. This paper introduces epistemic interaction within the context of human-system communication, illustrating how deliberate interaction design can improve system understanding and adaptation. Through concrete examples, we demonstrate the potential of epistemic interaction to significantly advance human-computer interaction by leveraging intuitive human communication strategies to inform system design and functionality, offering a novel pathway for enriching user-system engagements.
GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...

Dr. Sean Tan, Head of Data Science, Changi Airport Group
Discover how Changi Airport Group (CAG) leverages graph technologies and generative AI to revolutionize their search capabilities. This session delves into the unique search needs of CAG’s diverse passengers and customers, showcasing how graph data structures enhance the accuracy and relevance of AI-generated search results, mitigating the risk of “hallucinations” and improving the overall customer journey.
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
DevOps and Testing slides at DASA Connect

My and Rik Marselis slides at 30.5.2024 DASA Connect conference. We discuss about what is testing, then what is agile testing and finally what is Testing in DevOps. Finally we had lovely workshop with the participants trying to find out different ways to think about quality and testing in different parts of the DevOps infinity loop.
Recently uploaded (20)
Securing your Kubernetes cluster_ a step-by-step guide to success !

Securing your Kubernetes cluster_ a step-by-step guide to success !
Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx

Secstrike : Reverse Engineering & Pwnable tools for CTF.pptx
PHP Frameworks: I want to break free (IPC Berlin 2024)

PHP Frameworks: I want to break free (IPC Berlin 2024)
Transcript: Selling digital books in 2024: Insights from industry leaders - T...

Transcript: Selling digital books in 2024: Insights from industry leaders - T...
Communications Mining Series - Zero to Hero - Session 1

Communications Mining Series - Zero to Hero - Session 1
Elevating Tactical DDD Patterns Through Object Calisthenics

Elevating Tactical DDD Patterns Through Object Calisthenics
FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf

FIDO Alliance Osaka Seminar: Passkeys at Amazon.pdf
FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf

FIDO Alliance Osaka Seminar: FIDO Security Aspects.pdf
20240605 QFM017 Machine Intelligence Reading List May 2024

20240605 QFM017 Machine Intelligence Reading List May 2024
National Security Agency - NSA mobile device best practices

National Security Agency - NSA mobile device best practices
GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...

GraphSummit Singapore | Graphing Success: Revolutionising Organisational Stru...
By Design, not by Accident - Agile Venture Bolzano 2024

By Design, not by Accident - Agile Venture Bolzano 2024
Epistemic Interaction - tuning interfaces to provide information for AI support

Epistemic Interaction - tuning interfaces to provide information for AI support
GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...

GraphSummit Singapore | Enhancing Changi Airport Group's Passenger Experience...
Elizabeth Buie - Older adults: Are we really designing for our future selves?

Elizabeth Buie - Older adults: Are we really designing for our future selves?
Distil Networks Protecting the Telephony Industry
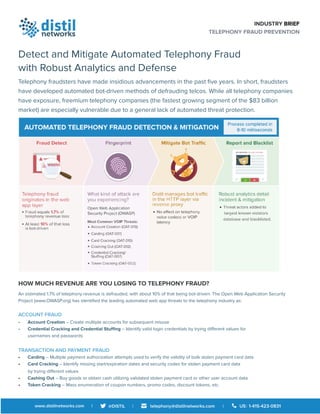
- 1. INDUSTRY BRIEF TELEPHONY FRAUD PREVENTION Detect and Mitigate Automated Telephony Fraud with Robust Analytics and Defense Telephony fraudsters have made insidious advancements in the past five years. In short, fraudsters have developed automated bot-driven methods of defrauding telcos. While all telephony companies have exposure, freemium telephony companies (the fastest growing segment of the $83 billion market) are especially vulnerable due to a general lack of automated threat protection. HOW MUCH REVENUE ARE YOU LOSING TO TELEPHONY FRAUD? An estimated 1.7% of telephony revenue is defrauded, with about 10% of that being bot-driven. The Open Web Application Security Project (www.OWASP.org) has identified the leading automated web app threats to the telephony industry as: ACCOUNT FRAUD • Account Creation – Create multiple accounts for subsequent misuse • Credential Cracking and Credential Stuffing – Identify valid login credentials by trying different values for usernames and passwords TRANSACTION AND PAYMENT FRAUD • Carding – Multiple payment authorization attempts used to verify the validity of bulk stolen payment card data • Card Cracking – Identify missing start/expiration dates and security codes for stolen payment card data by trying different values • Cashing Out – Buy goods or obtain cash utilizing validated stolen payment card or other user account data • Token Cracking – Mass enumeration of coupon numbers, promo codes, discount tokens, etc.
- 2. “Botnets and automated attacks are increasing in both volume and capability. These are revenue generating cybercrime tools, and the motivation for organized criminal factions to steal and monetize anything of value (including data, phone service, and more) isn't going to go away. IoT and the increasing connectedness of everyday devices is already increasing the staging ground for botnets and this will get worse before it gets better. Companies need to obtain visibility into the degree to which they're impacted by this, and then employ strategies and tools to defend themselves, reducing the impact to an acceptable level for their organization.” Michael Machado Chief Security Officer “Any company that does not ensure its software is designed to be securable leaves itself open to attack. According to Veracode, “with more than 20 percent of all web vulnerabilities being attributed to SQL injection” this is a major target for hackers. There are of course multiple other Web application exploits, however at least addressing Injection, Broken Authentication and Session Management, and Cross-Scripting can make a major difference. Hackers have tools that can help them find vulnerabilities and they are looking for the easiest sites to exploit.” Bryan Martin Chief Technology Officer “As an internet telephony service provider for ten years, our company has encountered and learned from occurrences of fraud, some quite costly. This caused us to need to invest significant time and money developing sophisticated proprietary methods to thwart fraud as there were no available solutions on the market.” Koi Lim Chief Executive Officer
- 3. ABOUT DISTIL NETWORKS Distil Networks, the global leader in bot detection and mitigation, is the only easy and accurate way to protect web applications from bad bots, API abuse, and fraud. With Distil, you automatically block 99.9% of malicious traffic without impacting legitimate users. Distil Web Security defends websites against web scraping, brute force attacks, competitive data mining, account takeovers, online fraud, unauthorized vulnerability scans, spam, man-in-the-middle attacks, digital ad fraud, and downtime. Distil API Security protects all types of APIs including those serving web browsers, mobile applications, and Internet of Things (IoT) connected devices. Distil API Security defends APIs against developer errors, integration bugs, automated scraping, and web and mobile hijacking. For more information on Distil Networks, visit us at http://www.distilnetworks.com or follow @DISTIL on Twitter. SOPHISTICATED ATTACKS DEMAND A SOPHISTICATED RESPONSE Relentless automated bot-driven attacks require a powerful security solution that is itself “always-on” and can respond with speed equal to the attackers and provide for instantaneous defense. Distil Networks can be deployed as a physical or virtual appliance to protect VOIP, without interfering with voice traffic or causing latency. The Distil solution integrates with diverse technology stacks including Amazon Web Services AMI, Microsoft Azure, VMWare, Google Cloud Platform, and Akamai. FLEXIBLE DEPLOYMENT OPTIONS Cloud CDN: If VOIP traffic is streamed separately from web traffic on a separate domain, bot mitigation can be deployed using the Distil Public Cloud. Appliance: Customers can configure their load balancer to not route VOIP traffic to Distil but to a separate domain for private deployments. Telephony APIs: Distil’s API Protection is optimal for telephony APIs since they are usually private and Distil API is designed specifically to protect against overload endpoint requests and stolen tokens. CONTACT DISTIL FOR A FREE CONSULTATION AND TRIAL Distil can provide a free in-depth Automated Threat VOIP Revenue Loss Audit to provide you with a holistic view of your telephony fraud landscape. We also offer a 30-day no-cost, no-obligation trial of Bot Mitigation solution for VOIP. “Telephony providers have significantly bigger challenges to overcome in order to support free trials and other freemium models because of their cost structure. The industry is a magnet for fraudsters and freeloaders. Distil is the first tool that evens the odds back in favor of the providers.” Sam Aparicio Chief Executive Officer