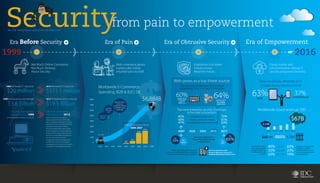
IDC - Security : From Pain To Empowerment
- 1. An IDC Infographic, sponsored by Blue Coat Identity and access management; Advanced authentication; Web single sign-on; Enterprise single sign-on; Legacy authorization; User provisioning; Personal portable security devices; Software licensing authentication token; Unified threat management; Intrusion detection and prevention; Virtual private network; Security and vulnerability management; Security information and event management; Proactive endpoint risk management; Forensics and incident investigation; Security device and systems management; Vulnerability assessment... $20 million 1999 Worldwide PC shipments 1999 Worldwide Security Software 2012 Worldwide Security Software $3.8 Billion $19.3 Billion 2012 Worldwide PC shipments $371.1 million 43 157 644 774 2000 2001 2002 2003 2004 2005 2006 2007 2008 $357.4B $6,884B DataLossDB.org incidents 2004-2007 Worldwide E-Commerce Spending (B2B & B2C) $B 8000 7000 6000 5000 4000 3000 2000 1000 0 Which if any of the following is your company currently using/likely to purchase or implement during the next 12 months? Any potential security risks cloud computing or SaaS introduce are far outweighed by the benefits. Employees using personal smartphones at work understand the risks, and are aware of security proper security practices. 45% 33% 22% AGREE DISAGREE NEUTRAL 63% 23% 14% from pain to empowerment Antiviral, Firewall, Encryption, Security AAA Security submarkets tracked by IDC 2013 Security submarkets tracked by IDC 1999 I LOVE YOU Emerges Code Red costs top $2B Slammer Worm infects an estimated 150,000 to 200,000 servers worldwide How would you describe your mobile device environment? 63%BYOD 37%IT-CONTROLLED Worldwide cloud revenue ($B) 2012 2013 2014 2015 2016 659 SMARTPHONE SHIPMENTS (M) 1,161 $29B $67B Employee Monitoring Solutions: 57% Network Admission Control: 57% Data loss prevention: 62% Complexity of security solutions Increasing sophistication of attacks Increasing volume of threats and/or attacks Web grows as a top threat source Top security challenges facing large enterprises over the next 12 months Top rated enterprise security challenges (a five year comparison) DIFFICULTY SECURING WEB APPS 64%EMPLOYEE USE OF WEB 2.0 60% 45% 45% 41% 53% 61% 63% 2007 2008 2009 2010 2011 Does your organization have a formal documented security policy? Yes 65%No 35% Yes 55% No 45% 1999 2016 Era Before Security Era of Pain Era of Obtrusive Security Era of Empowerment Cloud, mobile and consumerization disrupt IT. Security empowers business. Web commerce grows; hackers take notice, mischief turns to theft Enterprises lock-down infrastructures. Breaches mount. Not Much Online Commerce, Not Much thinking About Security
