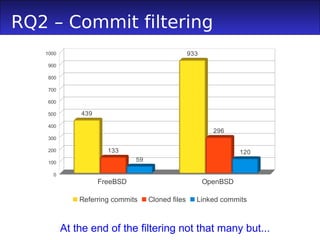
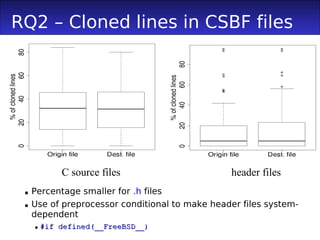
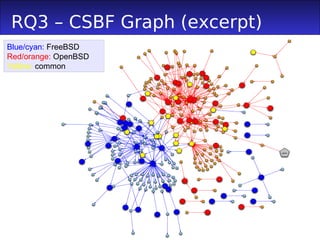
1) The document proposes a method to track cross-system bug fixings (CSBFs) between systems like FreeBSD and OpenBSD.
2) An empirical study found that while the development teams were largely separate, a small but significant number of CSBFs were identified between FreeBSD and OpenBSD.
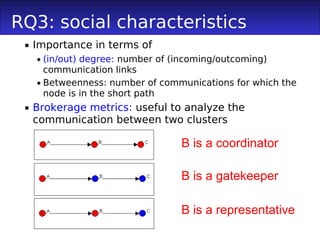
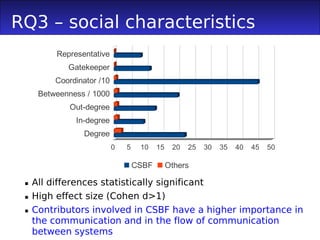
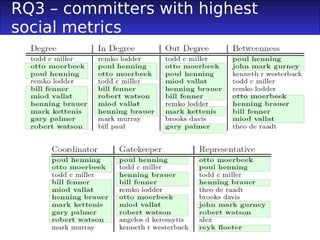
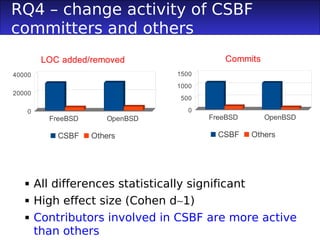
3) Committers involved in CSBFs had higher social metrics like degree and betweenness centrality, acted as more brokers between the teams, and were more active committers than others.



![Building Committers' Network
We extract communication from mailing
lists
Bug fixing mailing lists
Heuristic similar to the one of Bird et al.
[2006] to map inconsistent namings /
emails
Also, to map committer Ids to mailing list
names/emails
Nodes of the network labeled as:
Committer / other mailing list contributors
CSBFs committer](https://image.slidesharecdn.com/dipenta-msr2011-csbf-110522123624-phpapp01/85/Dipenta-msr2011-csbf-6-320.jpg)