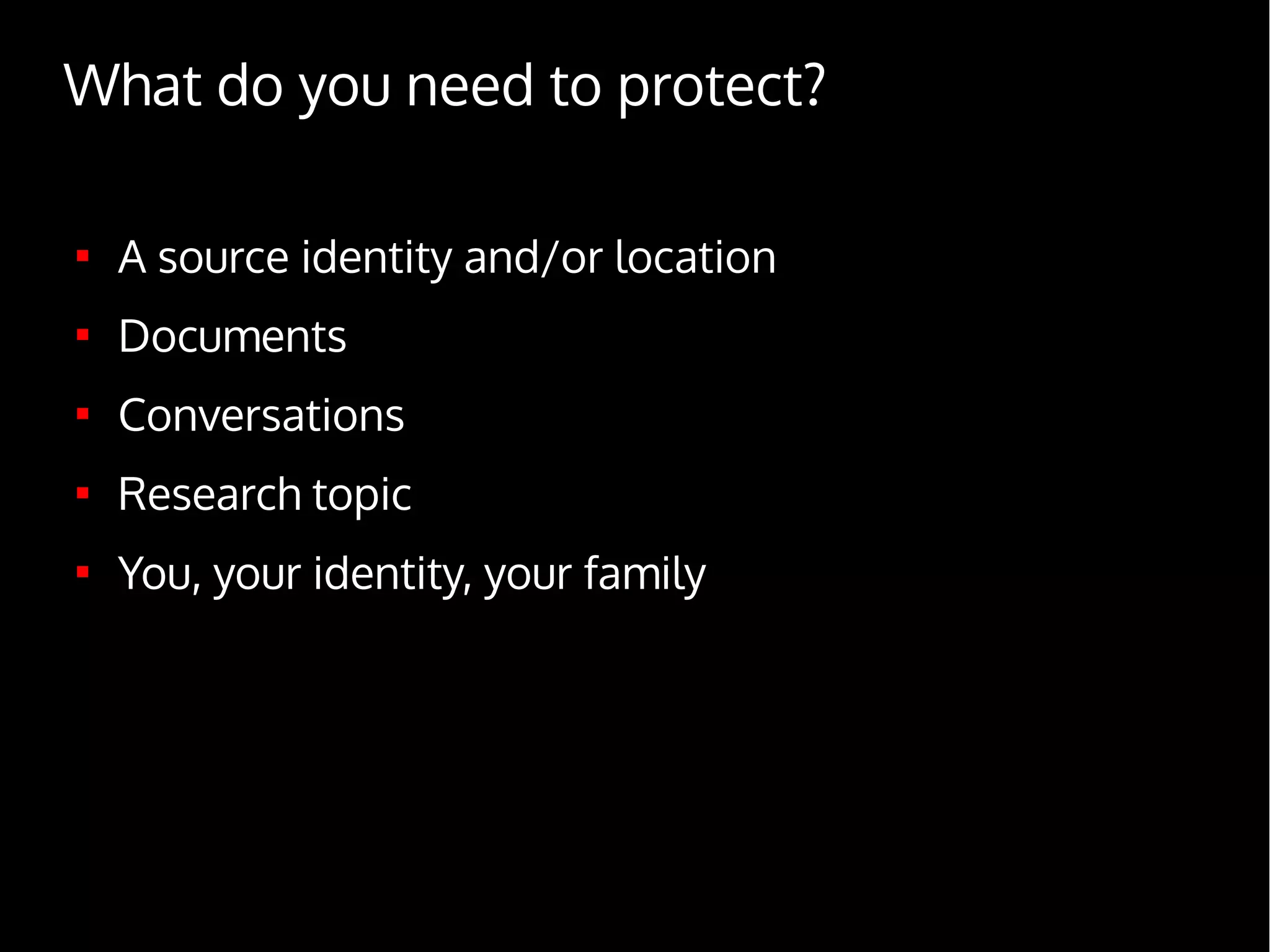
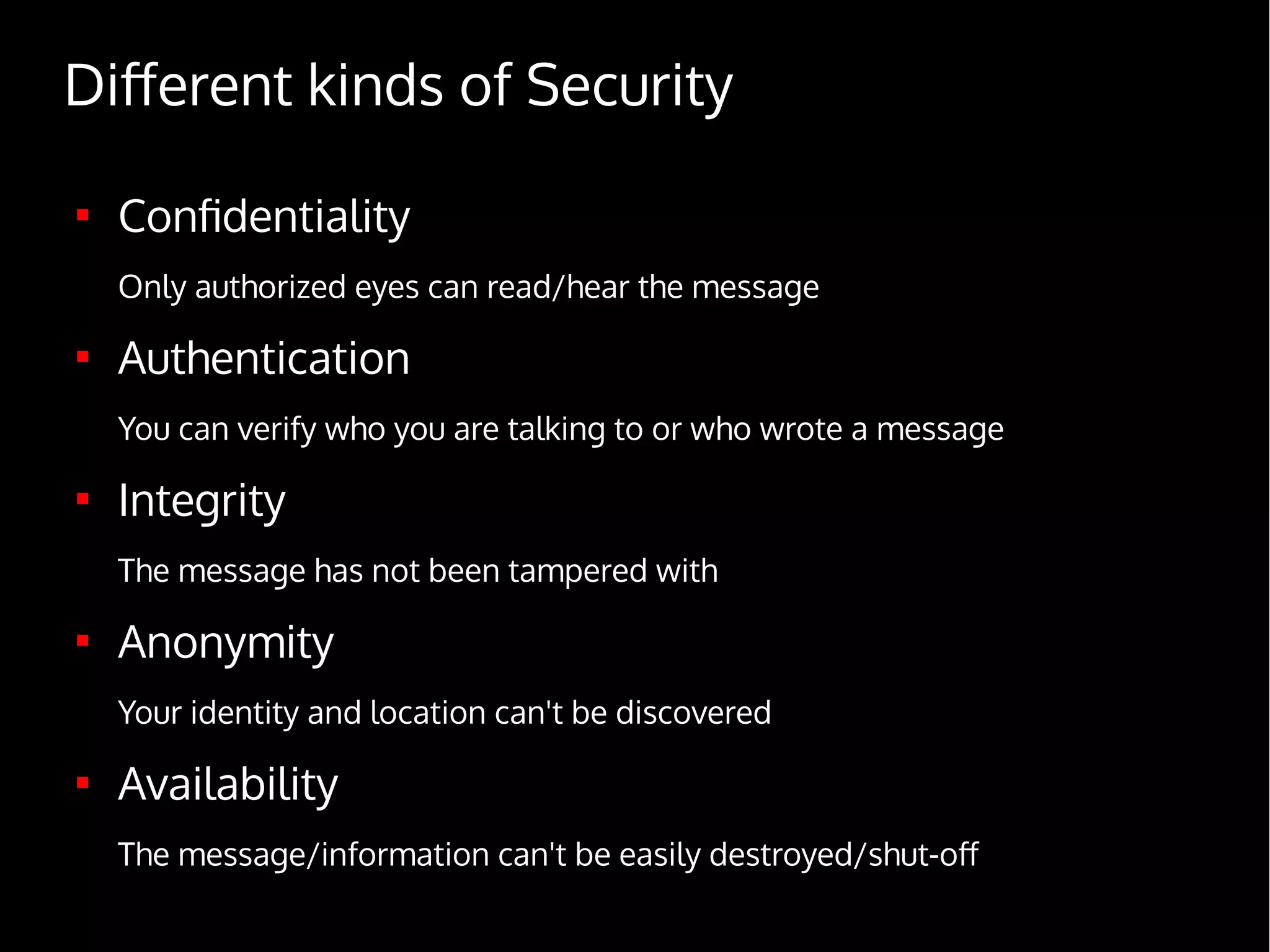
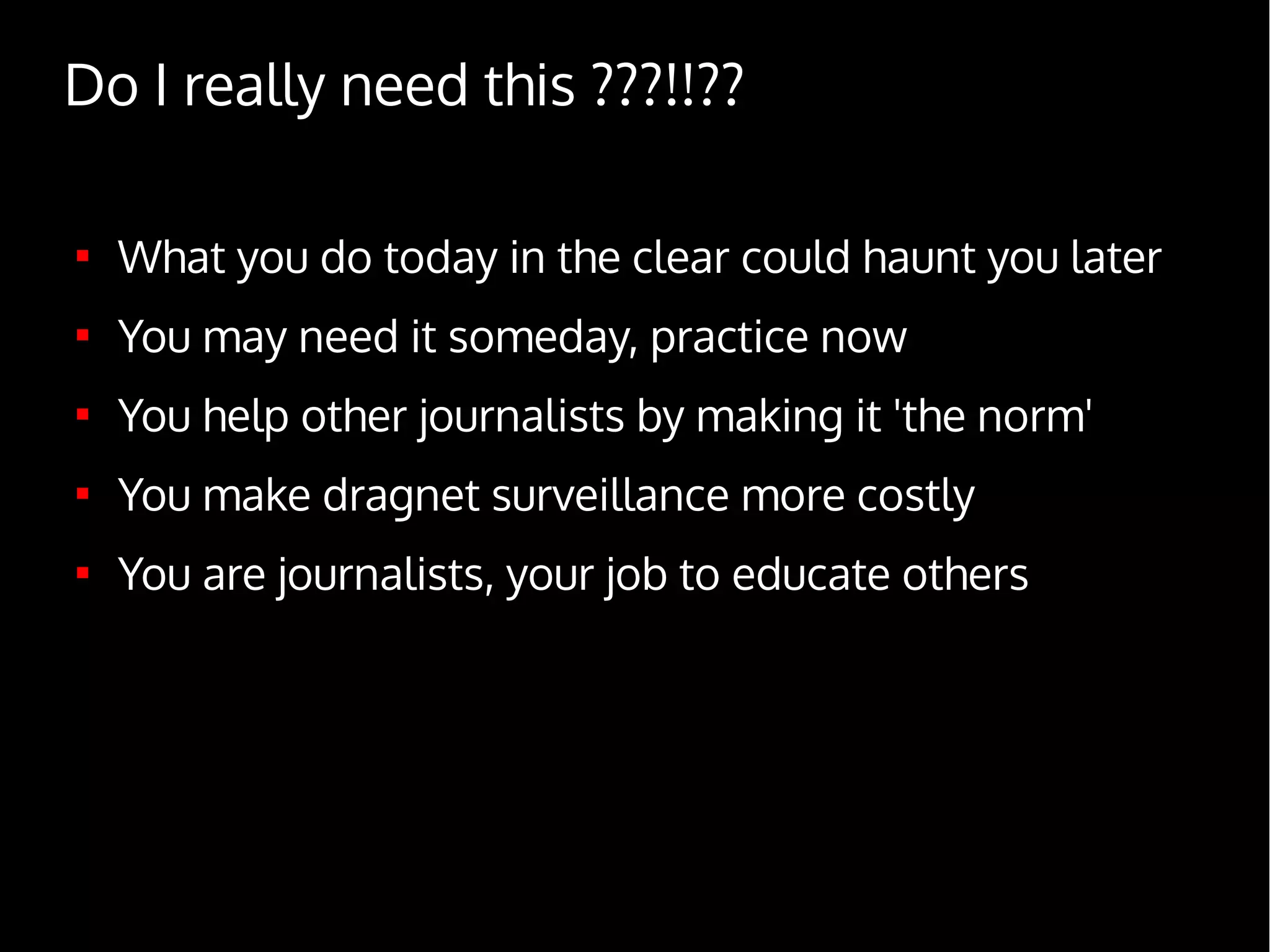
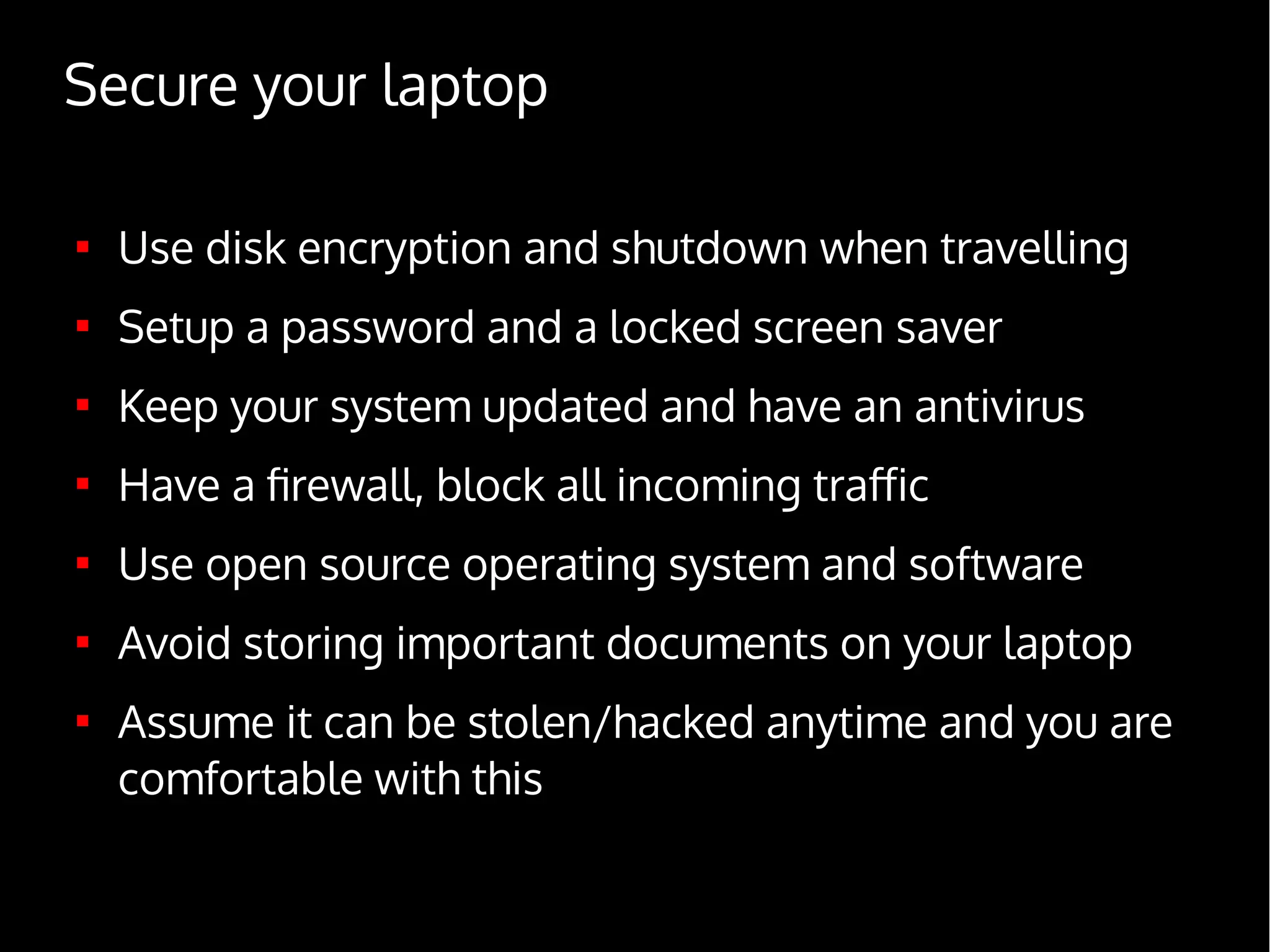
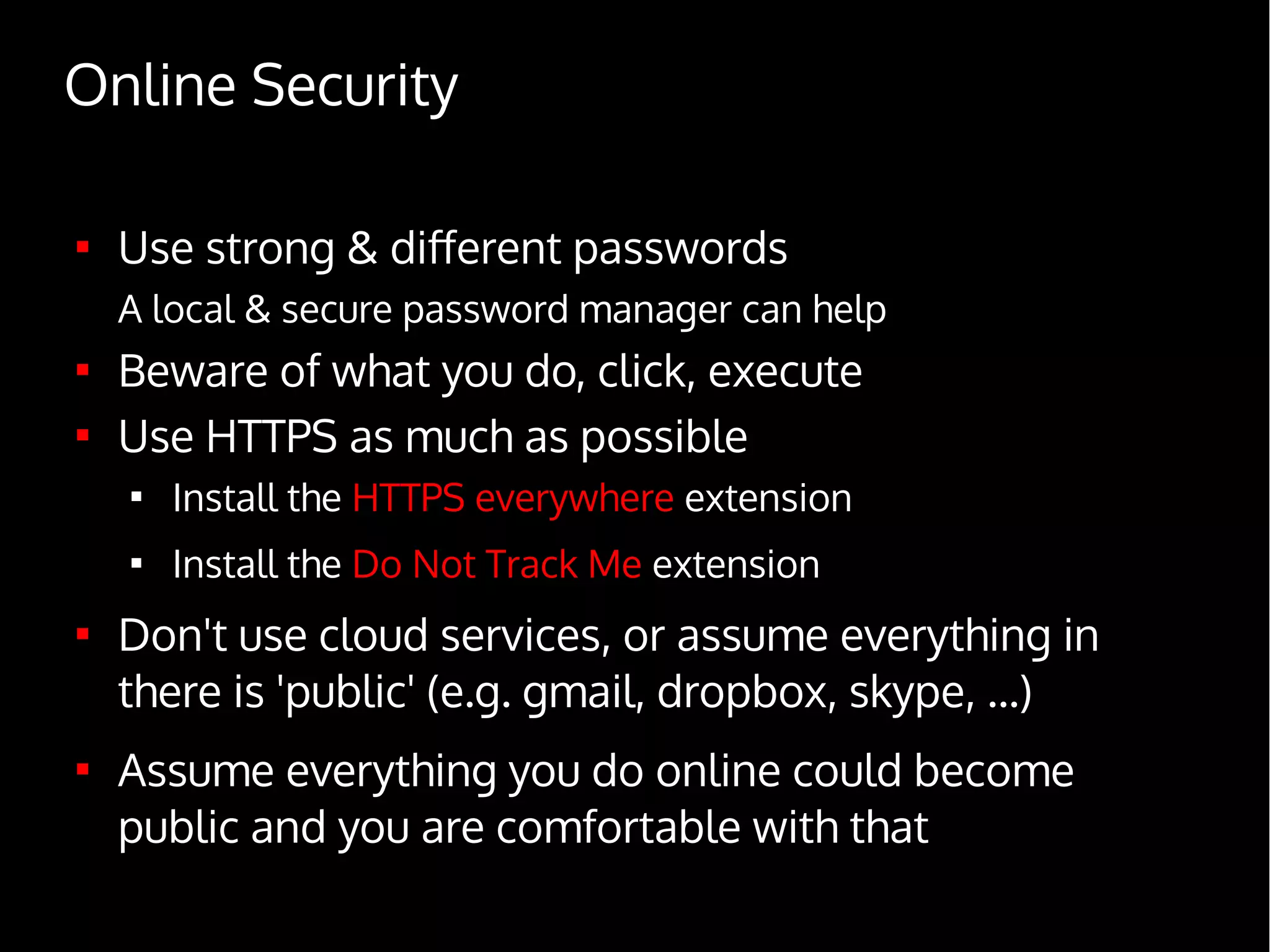
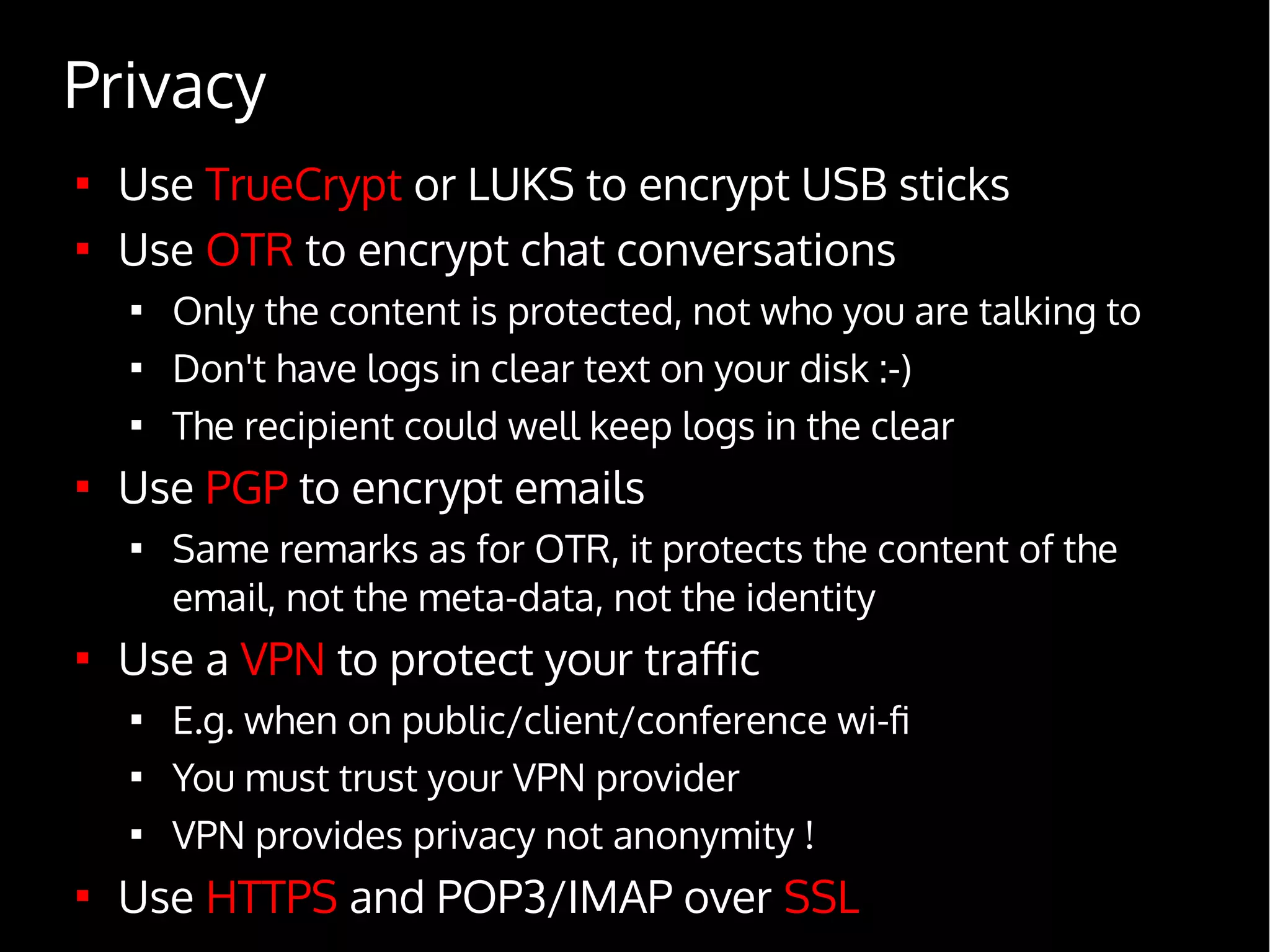
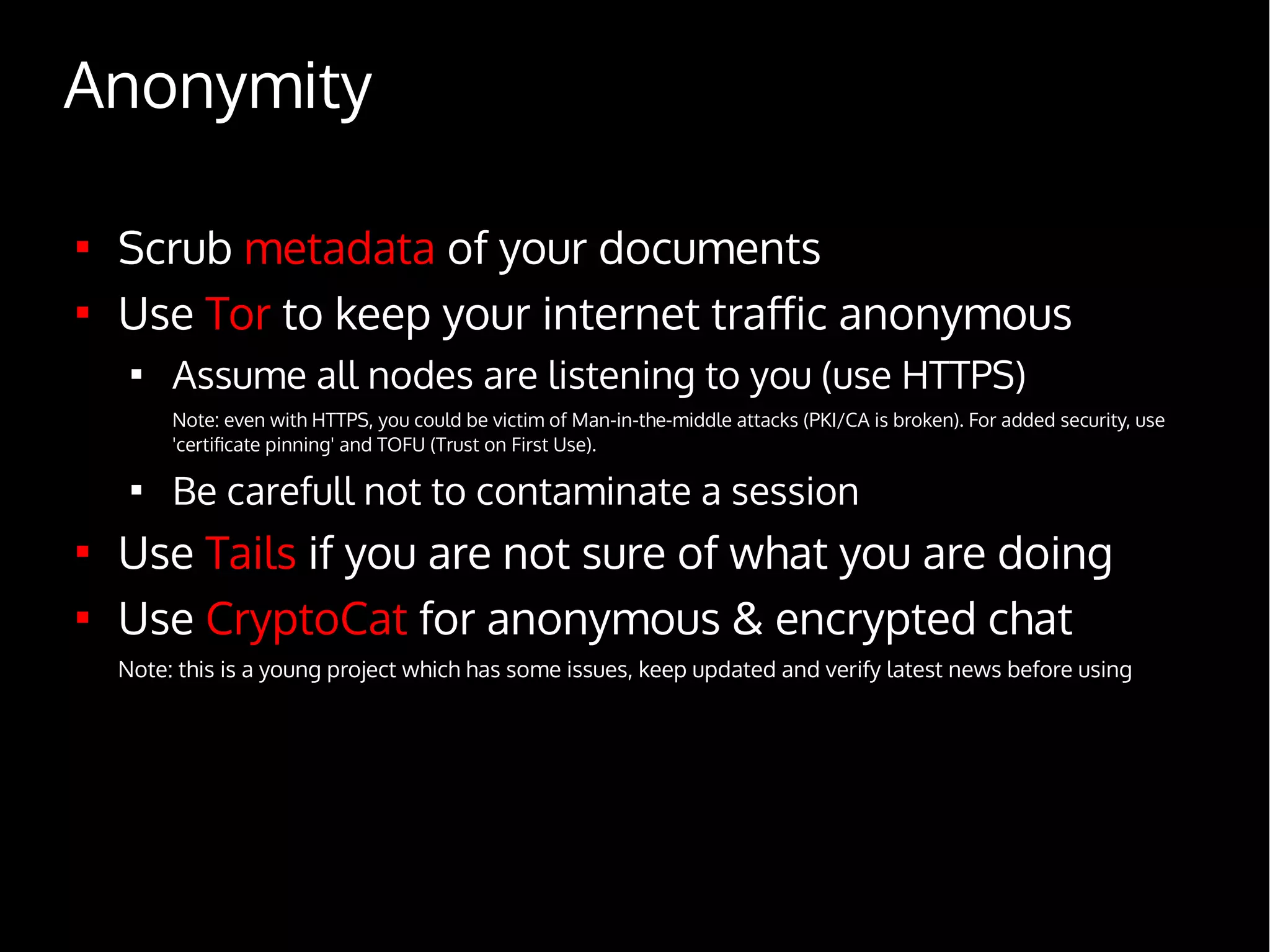
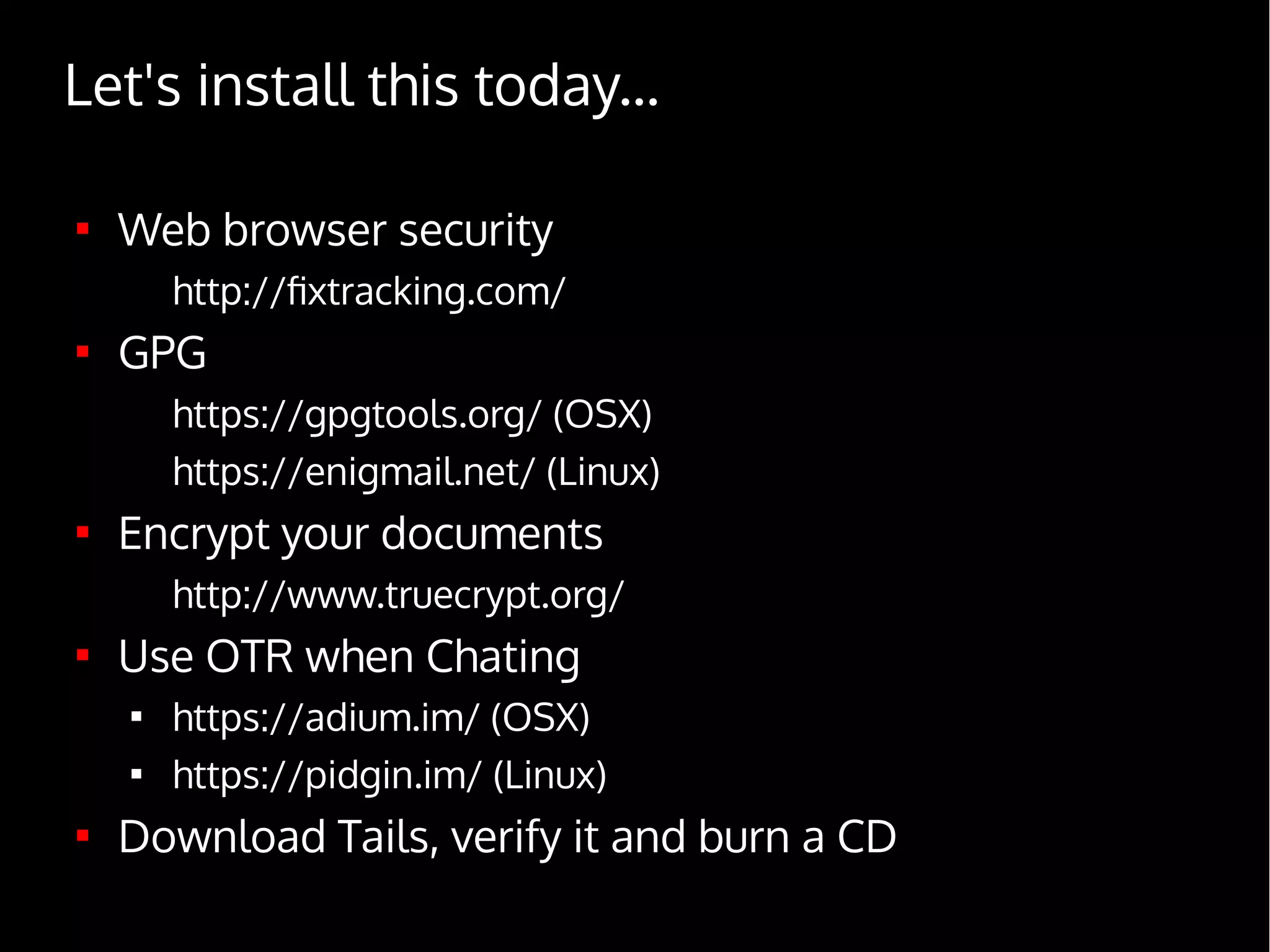
Digital Security for Journalists provides an overview of digital security best practices for journalists. It discusses how governments collect vast amounts of digital data on citizens through phone and internet surveillance programs. It emphasizes the importance of security for journalists to protect sources and sensitive work. The document recommends using encrypted email, chat, phones and laptops. It also suggests practicing "operational security" through techniques like using burner phones and not storing sensitive files digitally. The document is intended to educate journalists on basic security practices as well as more advanced tools and techniques like Tor, Tails and disk encryption.