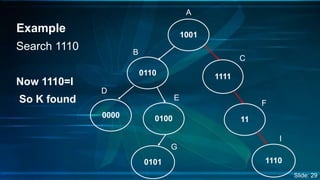
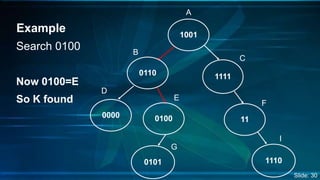
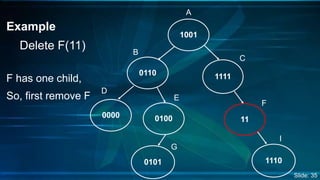
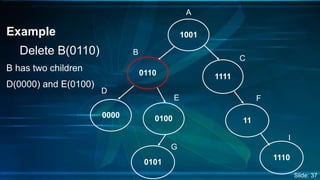
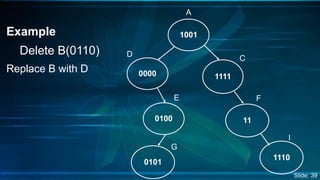
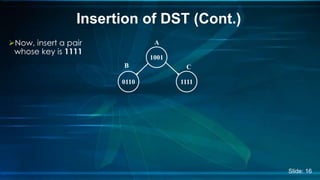
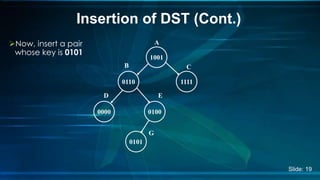
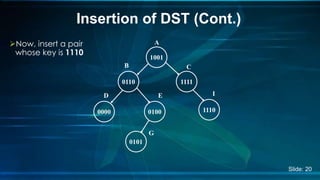
The document presents an overview of Digital Search Trees (DST), which are binary trees designed for efficient storage and retrieval of binary data based on bit representation. It discusses the structure, insertion, search, and deletion operations of DST, highlighting applications in IP routing (IPv4 and IPv6) and firewall systems. The document also addresses the benefits and drawbacks of DST compared to traditional binary search trees and AVL trees.





















![loop
{
if p->key == k then a matching item has been found
return p->item;
i = i - 1; /*Traverse left or right branch, depending on the current bit.*/
let j be the value of the (i)th bit of k;
if p->a[j] is null then
{
p->a[j] = new node for the item with key k;
return null;
}
p = p->a[j];
}
Insertion Pseudo Code of DST
Slide: 24](https://image.slidesharecdn.com/digitalsearchtree-141208102856-conversion-gate01/85/Digital-Search-Tree-25-320.jpg)
![Insertion Pseudo Code of DST
In the above pseudo-code, insertion fails if there is already an item with key
k in the tree, and a pointer to the matching item will be returned.
Otherwise, when insertion is successful, a null pointer is returned. When the
new node, x, is created, its fields are initialized as follows.
x->key = k;
x->item = item;
x->a[0] = x->a[1] = NULL;
Slide: 25](https://image.slidesharecdn.com/digitalsearchtree-141208102856-conversion-gate01/85/Digital-Search-Tree-26-320.jpg)