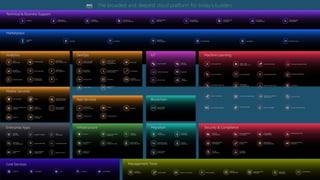
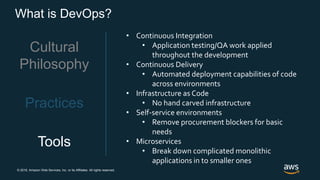
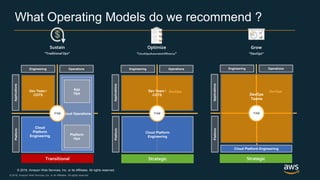
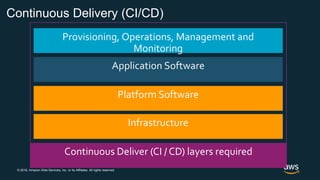
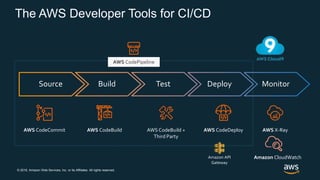
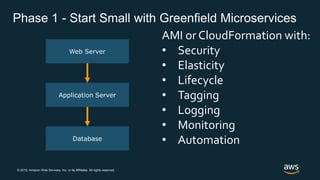
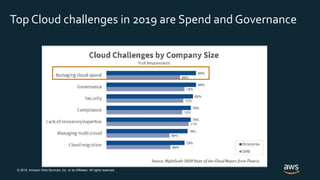
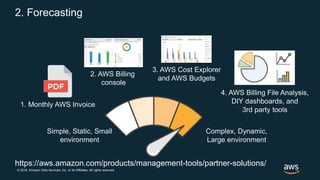
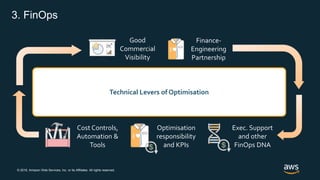
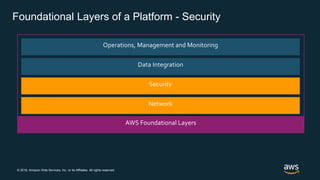
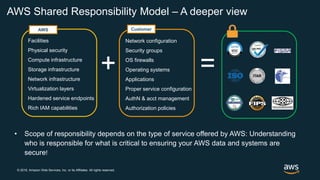
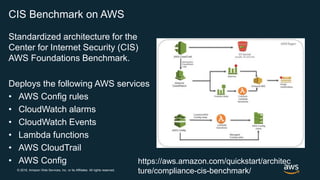
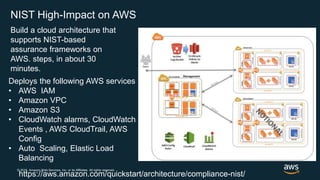
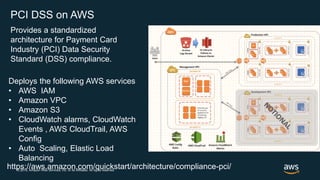
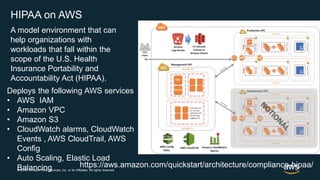
The document outlines AWS best practices for implementing DevOps, CI/CD, cost management, and security, emphasizing the importance of cultural philosophy and automated processes. It discusses tools and techniques for continuous integration and delivery, infrastructure as code, and governance frameworks to optimize cloud operations. Additionally, it highlights lessons learned from Amazon's transition to DevOps, including cost management strategies and security compliance frameworks.