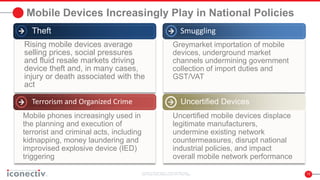
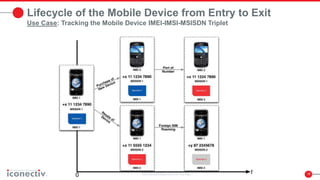
This document discusses issues with mobile device theft and strategies for addressing it. It notes that over 230,000 mobile phones were stolen in England, Wales and Scotland from 2010-2020, but only 1% were recovered. Existing solutions that blacklist stolen devices are ineffective at deterring theft as they are too slow. The document proposes a national mobile device registry that would automate data collection, analysis and enforcement across all mobile networks in a country. This would help deter theft, detect illicit devices and behaviors, and adapt to emerging threats over time through active management of device data. Consistent policies are needed across operators as well as data sharing to effectively address theft and other mobile security issues.