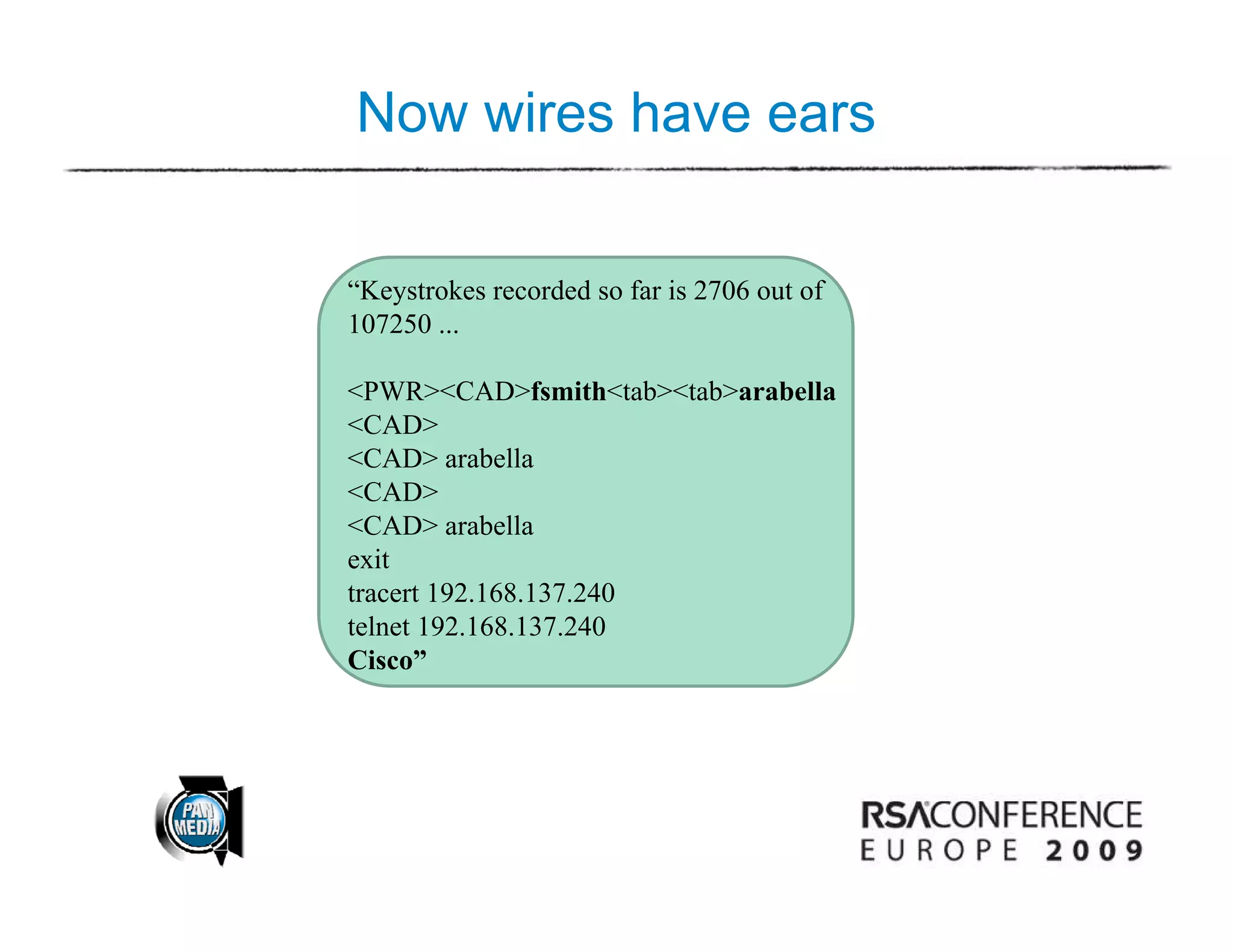
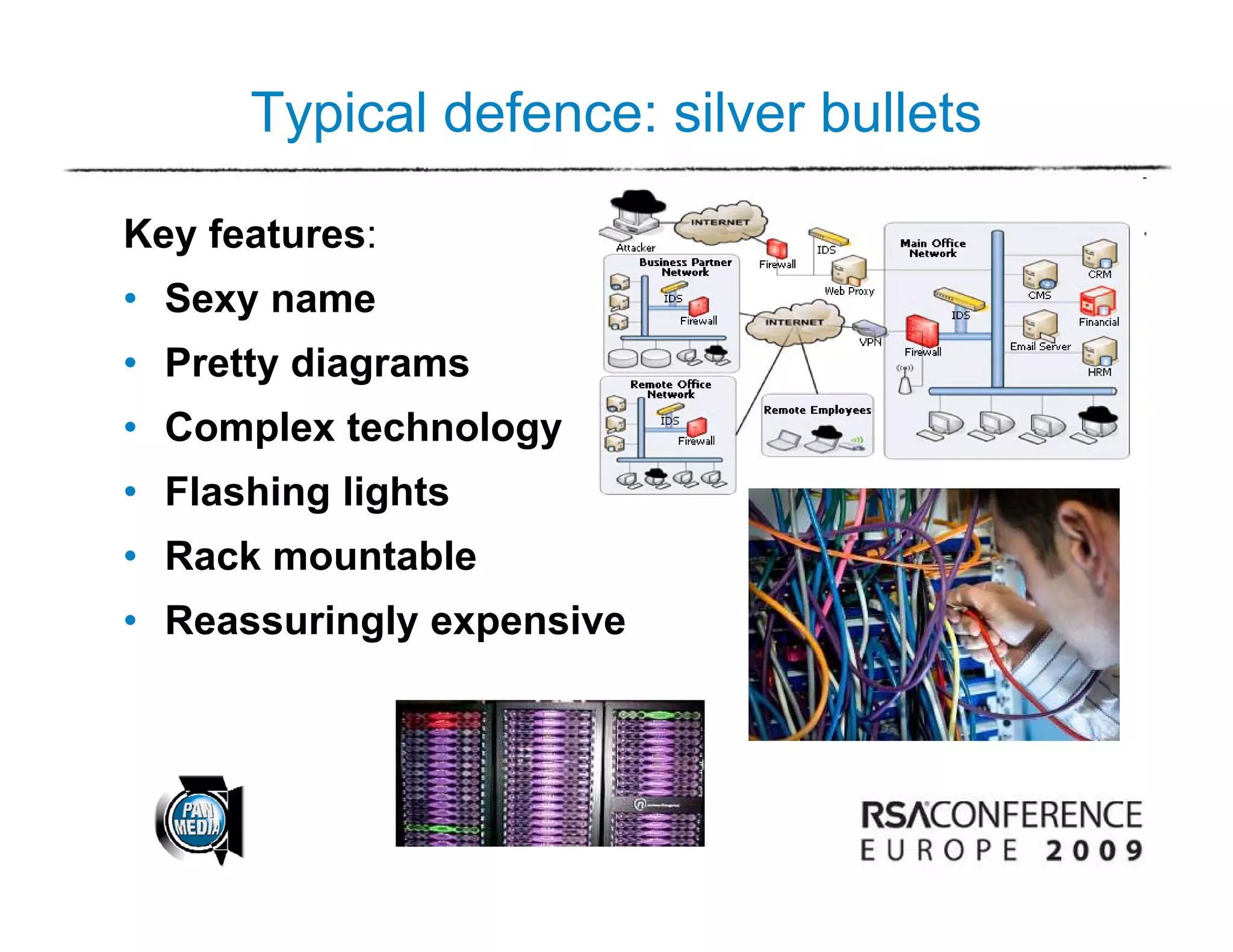
This document discusses the need to use stories and games to educate corporate executives about cybersecurity threats, as technical explanations often fail to convey the severity of the issues. It suggests designing games and animations that bring cyber attacks to life in a vivid way. One expert argues that executives should play special computer games and watch animations to help them understand the scale of the threat from cyber-crime and support improvements in security. The document also discusses using social engineering techniques like persuasion and impersonation to gain access to systems, and the need for physical and psychological countermeasures as well as technical controls to address these kinds of attacks.