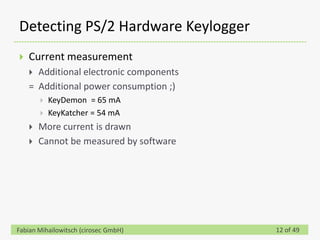
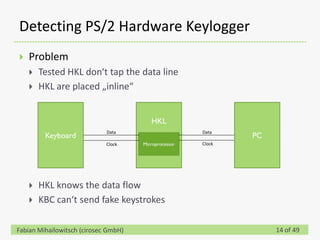
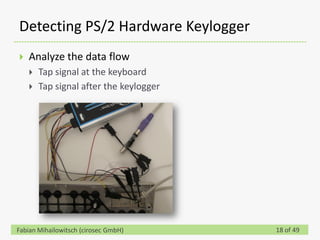
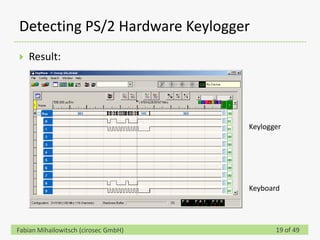
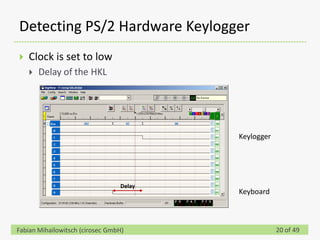
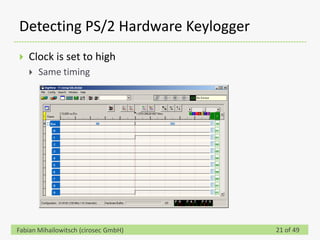
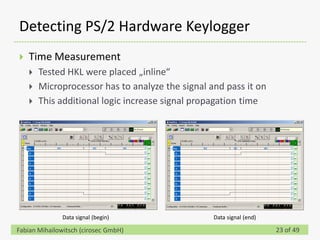
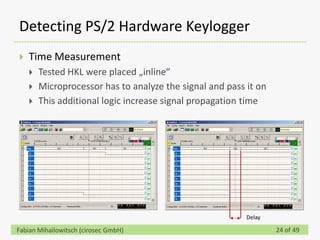
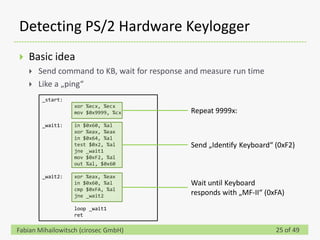
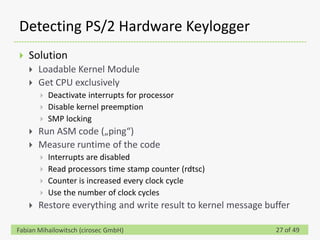
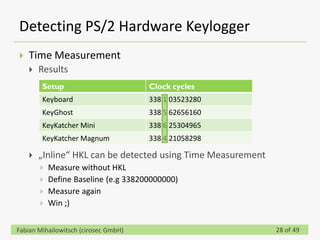
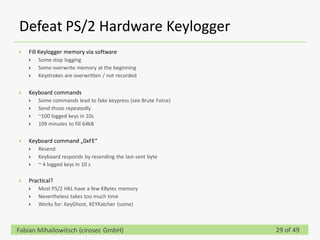
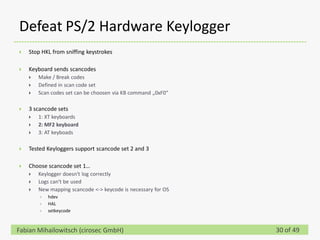
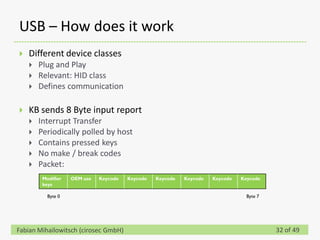
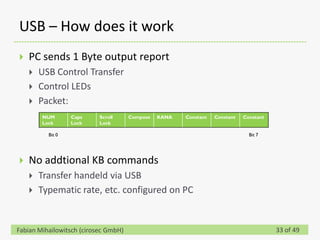
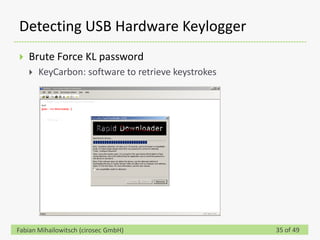
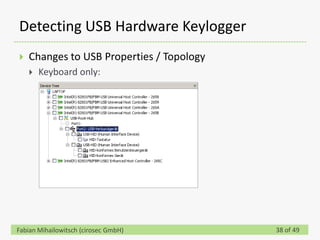
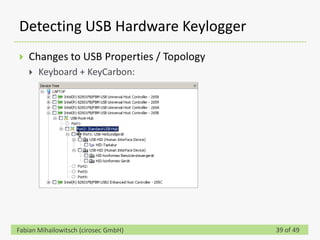
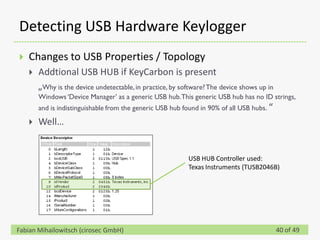
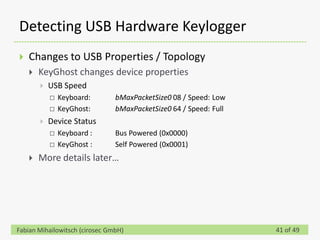
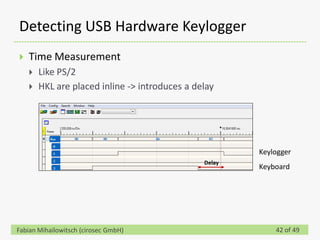
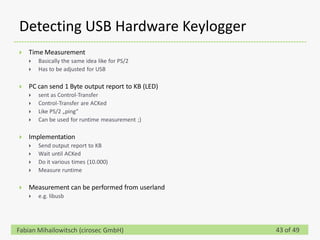
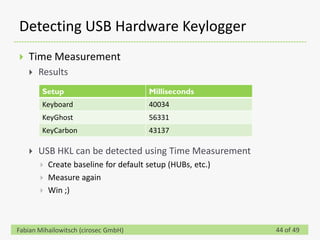
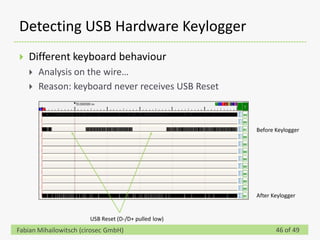
This document discusses detecting hardware keyloggers installed on PS/2 keyboards through software. While hardware keyloggers are generally undetectable via software, the author proposes that subtle timing delays may be introduced in the PS/2 communication from additional logic in hardware keyloggers. The document suggests methods to precisely measure the signal propagation time when sending commands to the keyboard to see if a delay would indicate the presence of a hardware keylogger installed inline. A demonstration is shown of potential timing differences that could be detected and used to identify keyloggers.







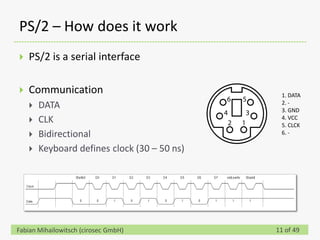
![PS/2 – How does it work
PS/2 is a serial interface
Communication 1. DATA
2. -
DATA 3. GND
CLK 4. VCC
5. CLCK
Bidirectional 6. -
Keyboard defines clock (30 – 50 ns)
Data frames
KB (11 bit): startbit, D0-D7 [data], odd parity, stopbit
KBC (12 bit): startbit, D0-D7 [data], odd parity, stopbit, ACK (KB)
Fabian Mihailowitsch (cirosec GmbH) 10 of 49](https://image.slidesharecdn.com/hardwarekeylogger-110903182926-phpapp01/85/Detectando-Hardware-keylogger-10-320.jpg)