The document outlines the end of life for Dell Data Protection (DDPE) and its various products, detailing their functionalities and reasons for discontinuation. It also provides instructions for uninstalling the software and suggests alternatives, including Dell Encryption and MiniTool ShadowMaker. Additionally, it highlights the importance of transitioning to other data protection solutions due to the obsolescence of DDPE.
![Title: [Warning] Dell Data Protection End of Life & Its Alternatives
Keywords: dell data protection, remove dell dataprotection,how touninstall dell dataprotection,
dell emcdata protection,whatisdell dataprotection
Description: Are you Dell Data Protection users? If so, you probably know that Dell Data Protection
gets its sunset and try to find a replacement like MiniTool ShadowMaker.
URL: https://www.minitool.com/backup-tips/dell-data-protection.html
Summary: This article written on MiniTool official webpage is mainly based on Dell Data Protection
| Encryption (DDPE). It covers the definition, function, uninstallation, reason for the end of the
lifecycle, and alternatives of DDPE. This post will give you almost everything you want to learn
about DDPE and it won’t let you down!
Do youknowwhat Dell Data Protection is? If you are a user of Dell devices, desktops or laptops, you
are probably familiar with this solution. And, some other computer users may also hear of it.
In the past few years,from 2017 to 2021, different variants of Dell Data Protection got their end of
life one by one. For example, Dell Data Protection | Endpoint Recovery came to end in October 2017;
Dell Data Protection | Protected Workspace withdrew itself in January 2018; Dell Data Protection |
Security Tools Mobile got ended in April 2018; Dell Data Protection | Cloud Encryption ended its life
in May 2018; Dell Data Protection | Secure Lifecycle dropped out in November 2018; and Dell Data
Protection | Encryption stopped in January 2021.
Besides the above completely ended products, Dell Data Protection | Security Tools has ended its
support and Dell Data Protection | Mobile Edition has ended its maintenance.
Tip:
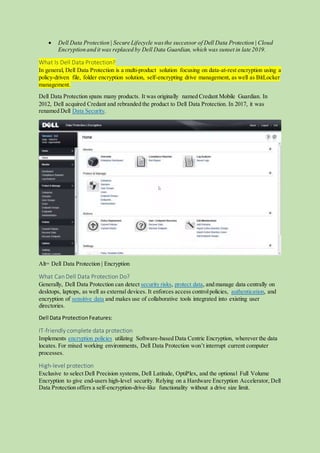
Dell Data Protection | Encryption was superseded by Dell Encryption in version 10.x and
later.](https://image.slidesharecdn.com/dell-data-protection-210323063920/85/Dell-data-protection-1-320.jpg)