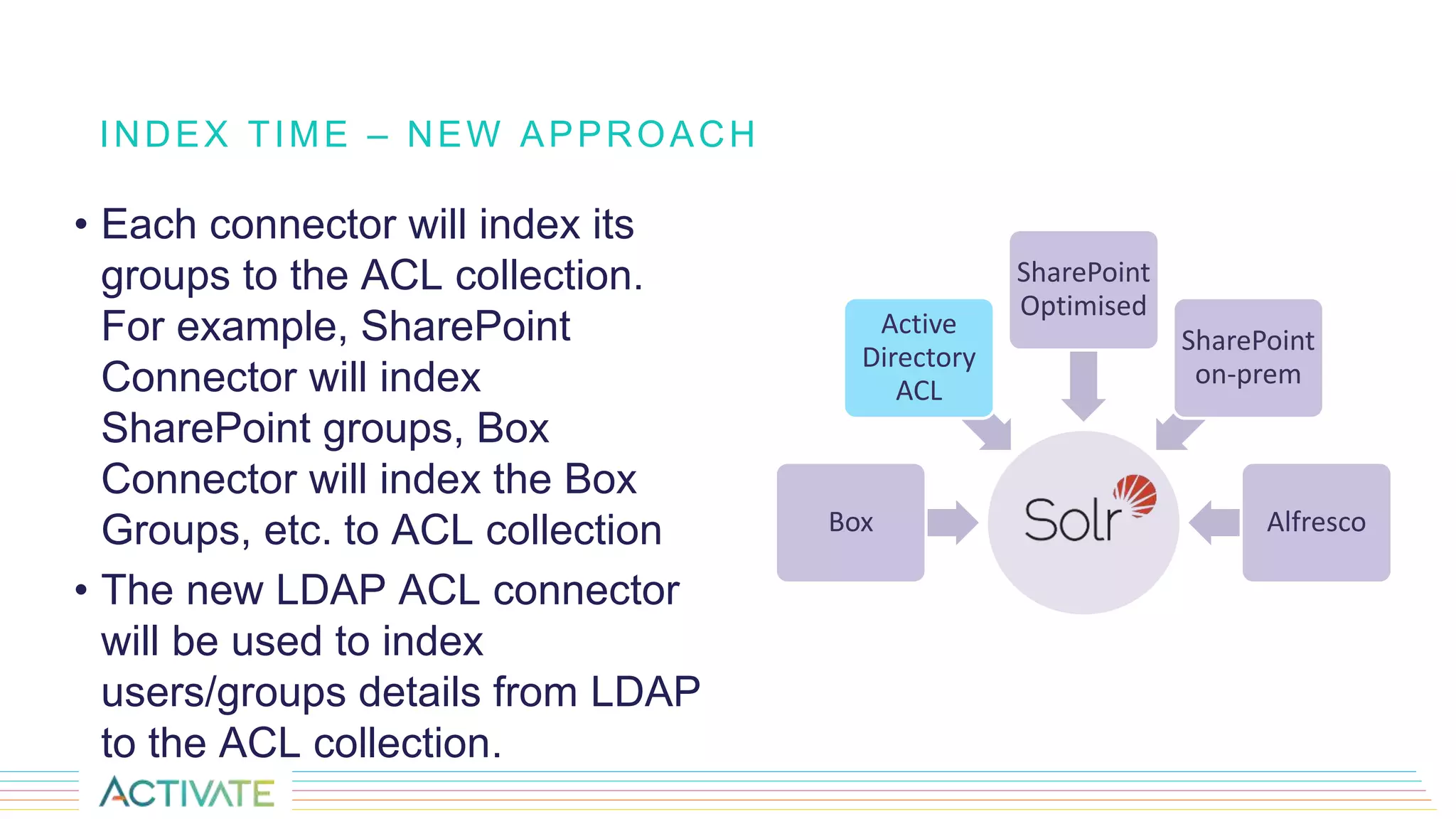
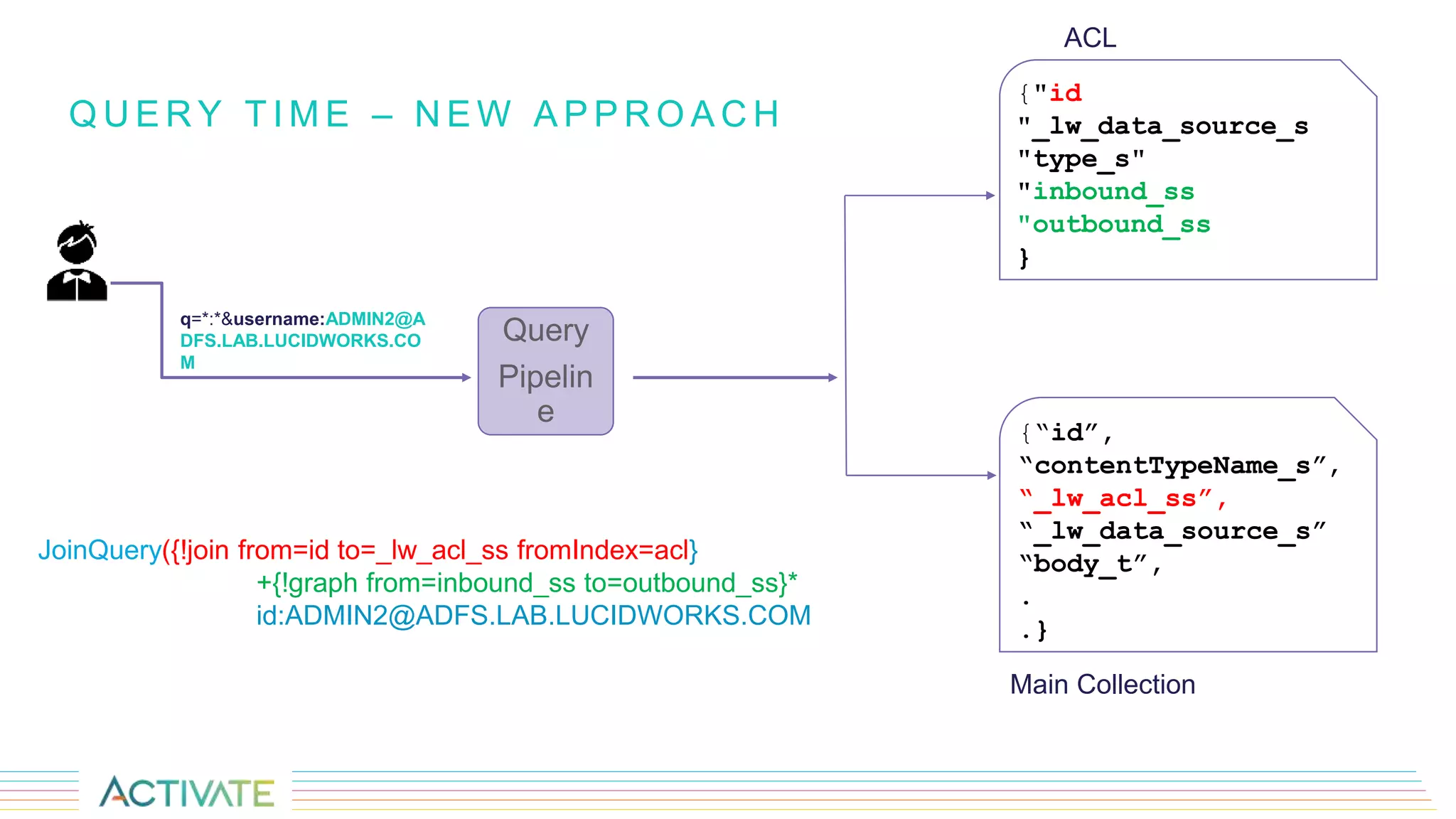
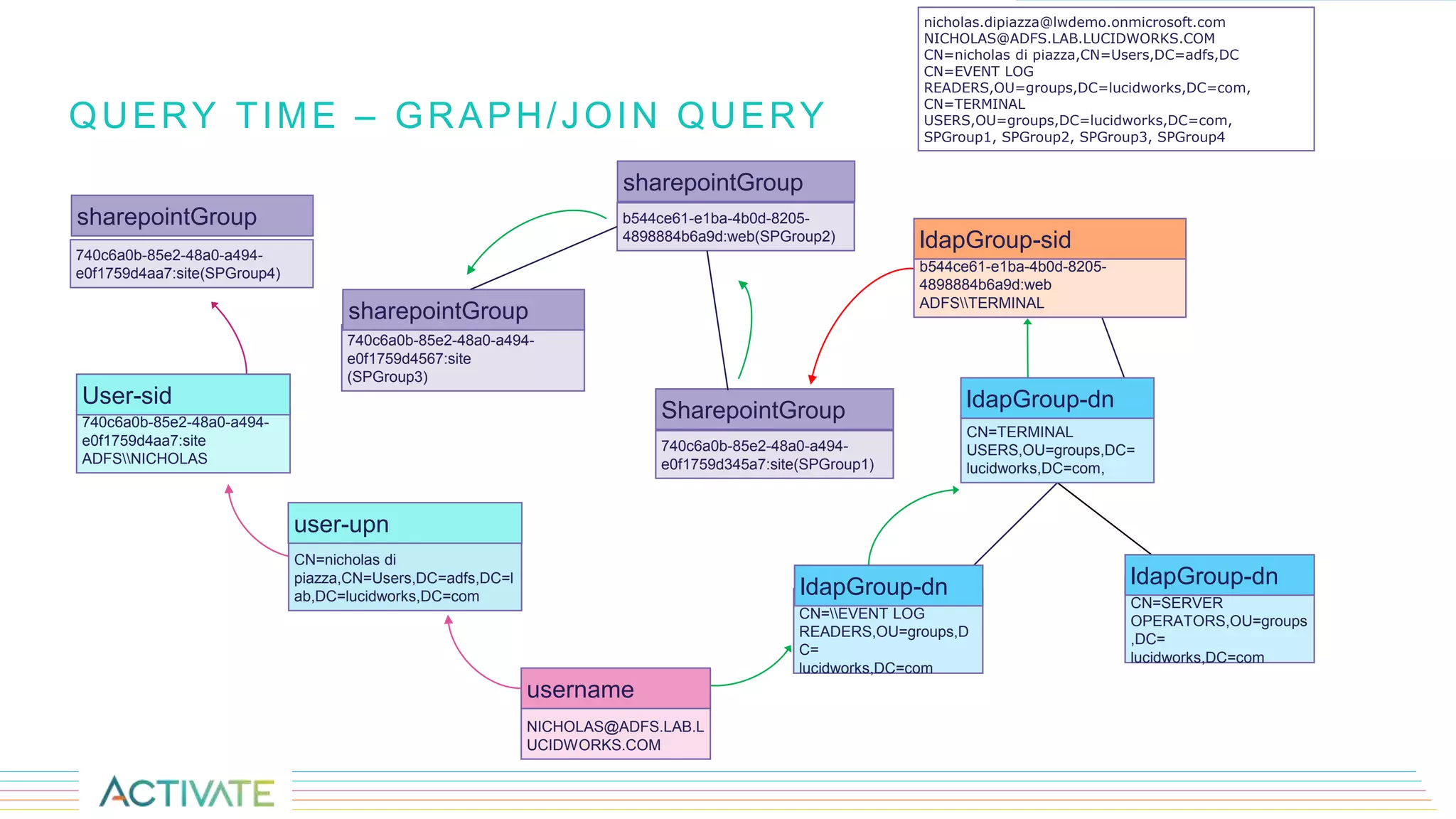
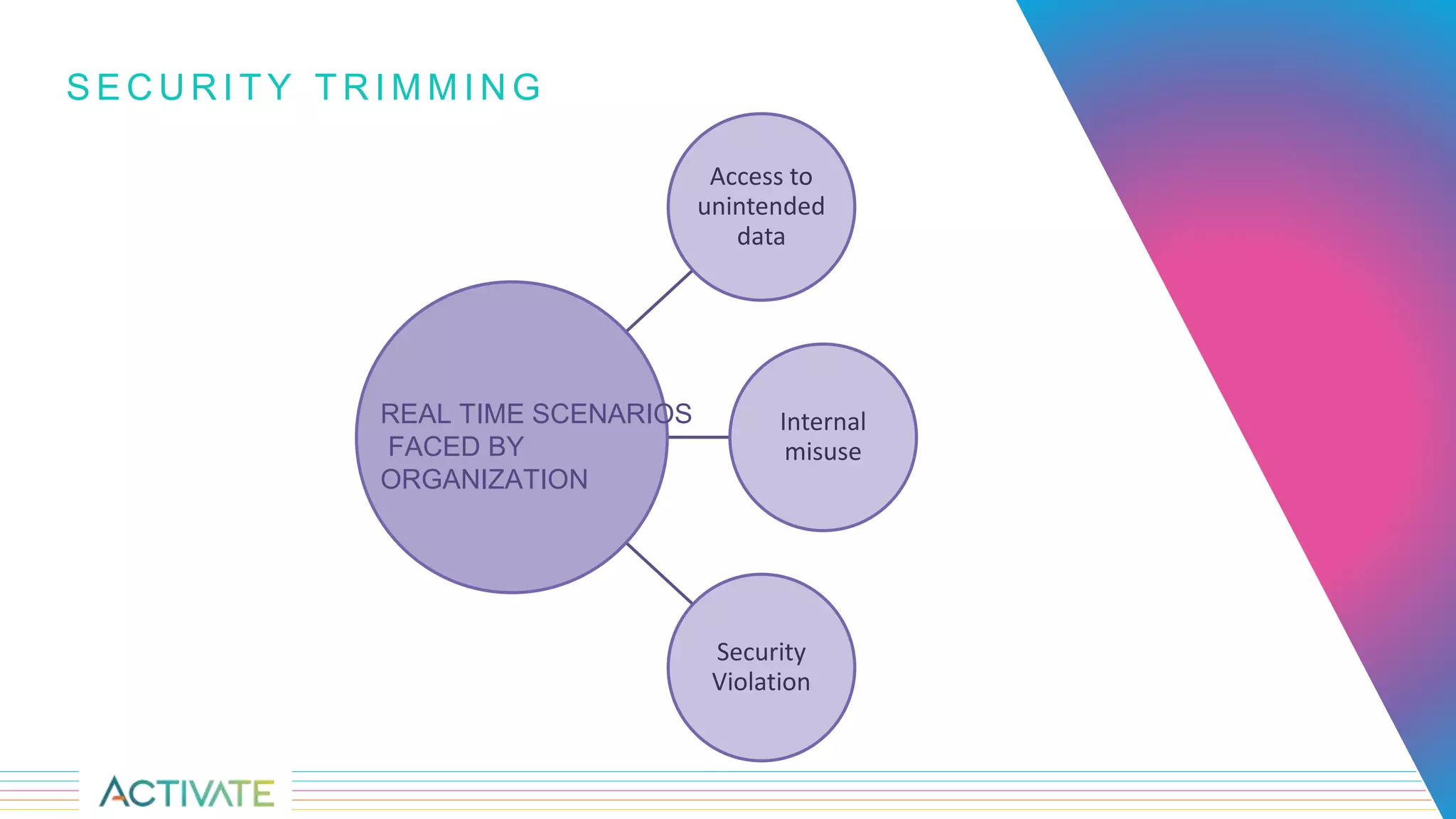
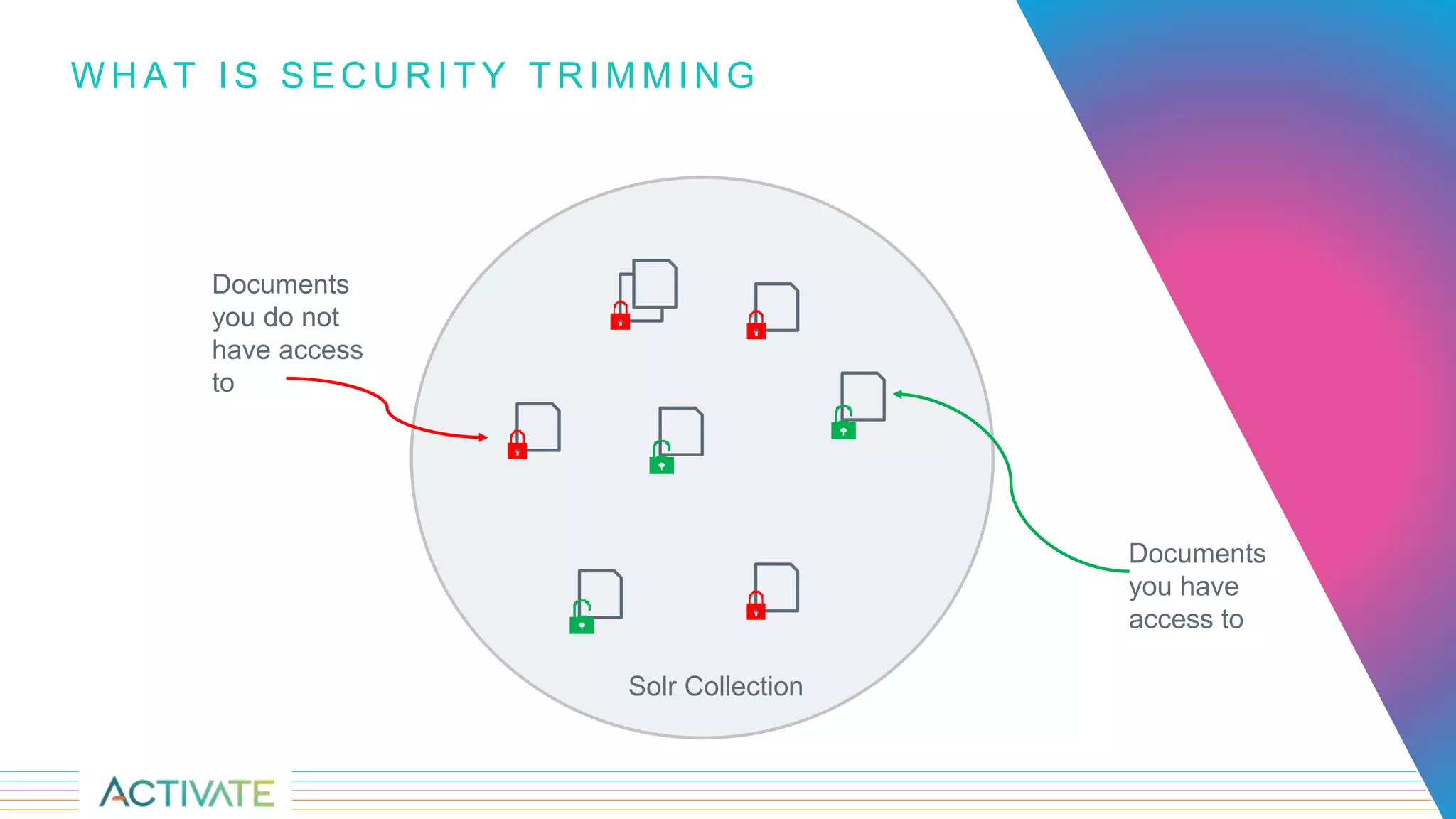
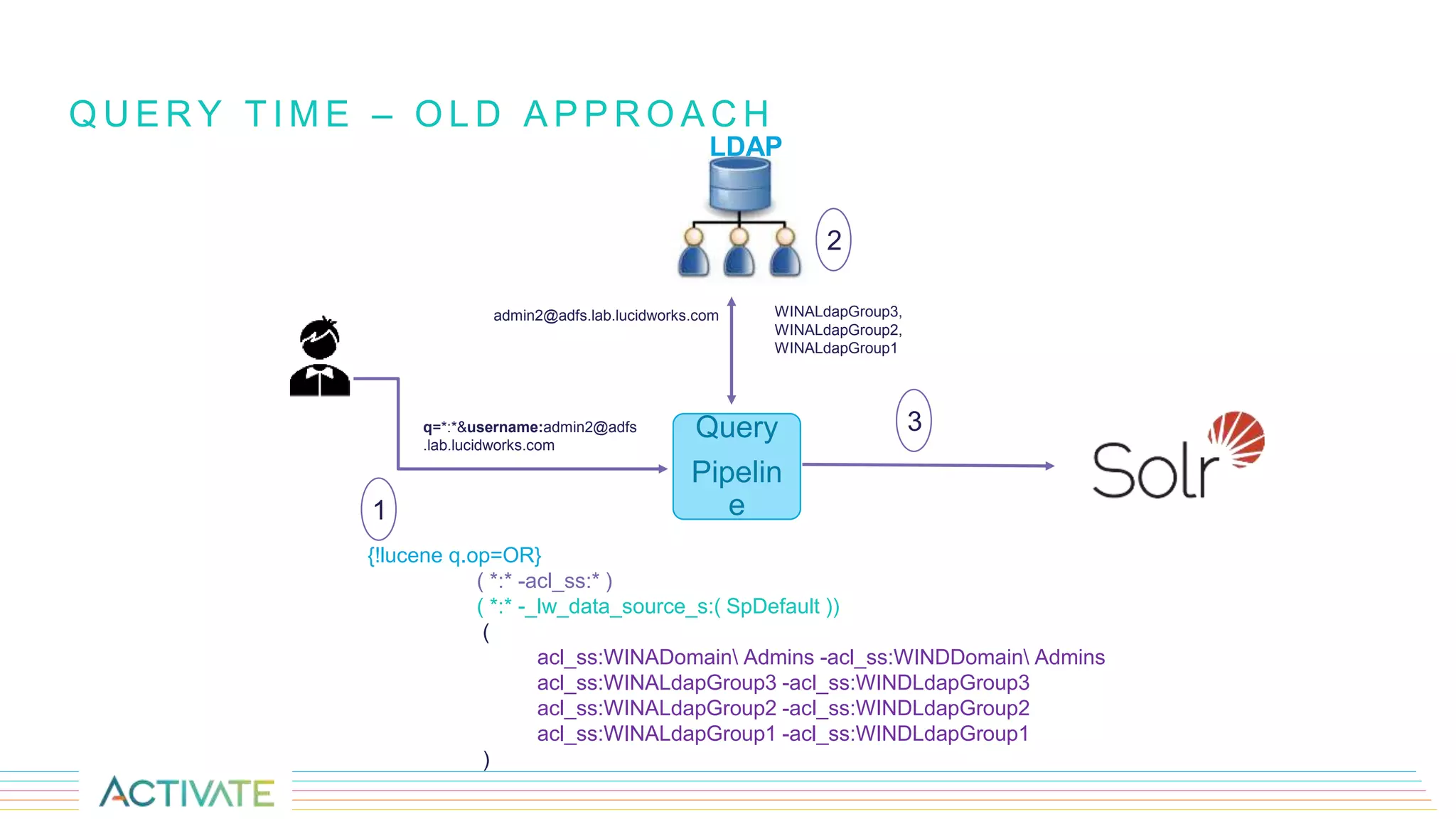
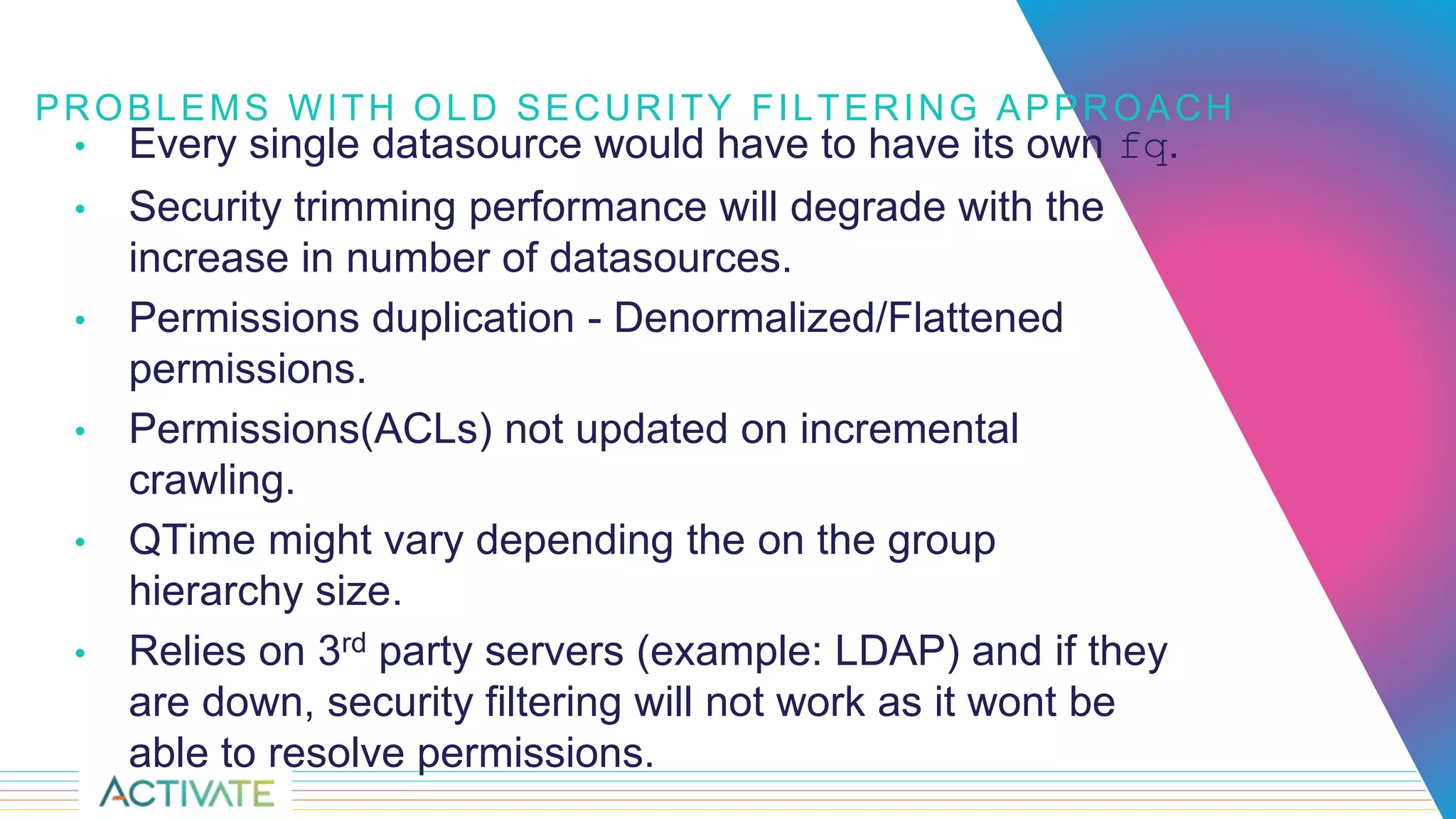
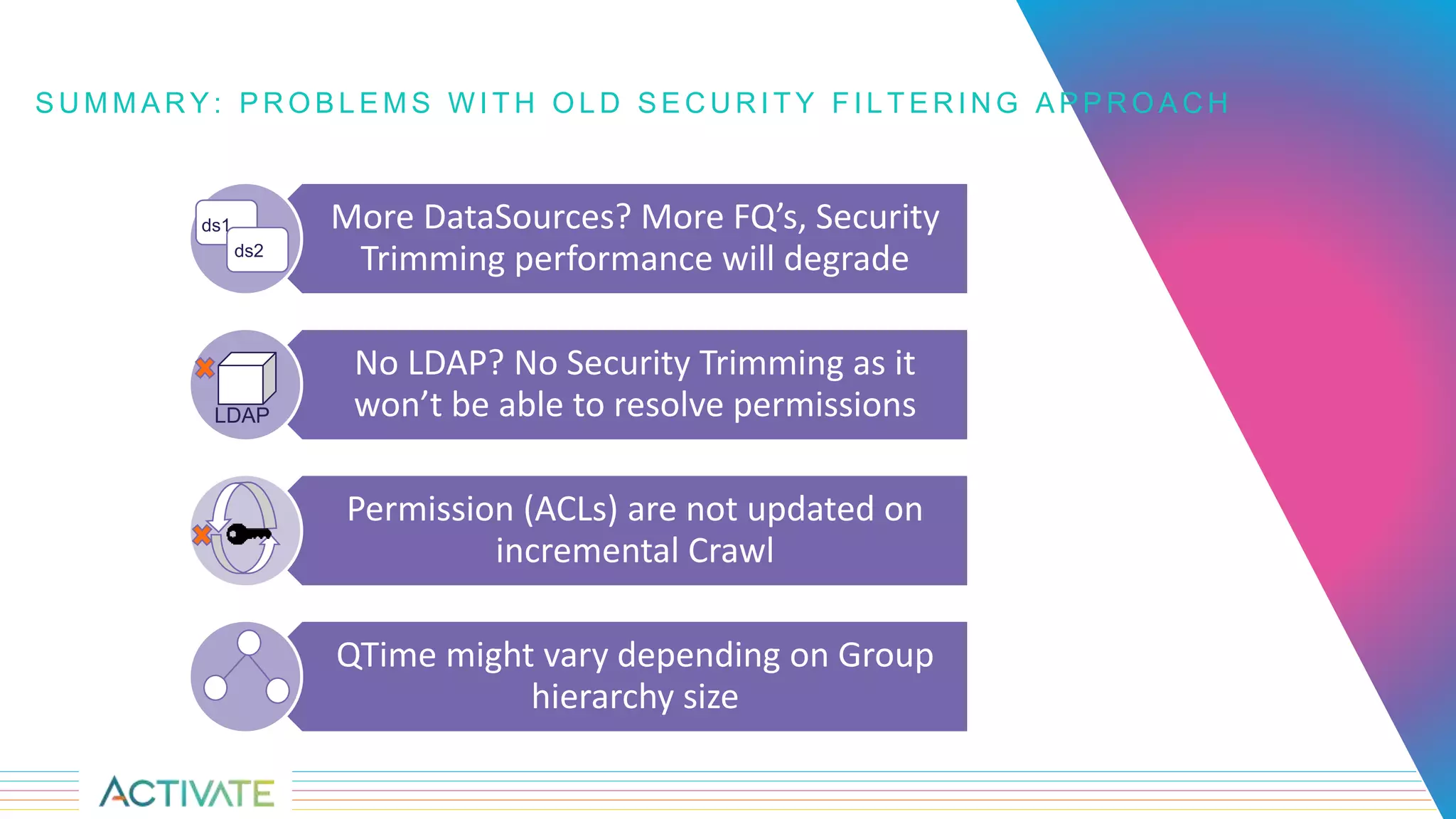
The document discusses security trimming in Fusion, comparing old and new security filtering approaches. The old method involved storing access control lists (ACLs) with content documents, leading to performance issues and dependency on third-party systems. The new approach, which separates user and group access control entities into a distinct collection and utilizes a solr graph+join query for security filters, offers better performance and flexibility in managing permissions.





![• While crawling documents
through a data source,
Fusion stores Access
Control List(ACL) metadata
as SOLR fields in the
content document.
• The Security Trimming
query stage matches this
information against the ID of
the user running the search
query.
S E C U R I T Y T R I M M I N G I N F U S I O N – O L D A P P R O A C H
"acls_ss":["SP_ALLOW_GROUP_ADFSCOMMUNICATION SITE MEMBERS",
"SP_ALLOW_GROUP_ADFSCOMMUNICATION SITE OWNERS",
"SP_ALLOW_GROUP_ADFSCOMMUNICATION SITE VISITORS",
"SP_ALLOW_GROUP_ADFSEVERYONE EXCEPT EXTERNAL USERS",
"SP_ALLOW_GROUP_ADFSSHAREPOINT SERVICE ADMINISTRATOR",
"SP_ALLOW_USER_ADMIN2@ADFS.LAB.LUCIDWORKS.COM",
"SP_ALLOW_USER_DBENSON@AZURE.LAB.LUCIDWORKS.COM"]](https://image.slidesharecdn.com/rd0glmjztv61ansejrz0-signature-c75a7d7fcd776973c606549683b9baf42b3c774325d0028542e1af0048998ba4-poli-190925162241/75/Deep-Dive-Security-Trimming-in-Fusion-8-2048.jpg)

![V 1 C O N N E C T O R I N D E X W O R K F L O W – O L D A P P R O A C H
LDAP
Data
Source
Parser
Index
Pipeline
"id":"https://lucidworksfusiondev.sharepoint.com/LoadTest
"acls_ss":["SP_ALLOW_GROUP_ADFSCOMMUNICATION SITE MEMBERS",
"SP_ALLOW_GROUP_ADFSCOMMUNICATION SITE OWNERS",
"SP_ALLOW_GROUP_ADFSCOMMUNICATION SITE VISITORS",
"SP_ALLOW_GROUP_ADFSCOMPANY ADMINISTRATOR",
"SP_ALLOW_GROUP_ADFSCOMPANY ADMINISTRATOR",
"SP_ALLOW_GROUP_ADFSEVERYONE EXCEPT EXTERNAL USERS",
"SP_ALLOW_GROUP_ADFSSHAREPOINT SERVICE
ADMINISTRATOR",
"SP_ALLOW_USER_ADMIN2@ADFS.LAB.LUCIDWORKS.COM",
"SP_ALLOW_USER_DBENSON@AZURE.LAB.LUCIDWORKS.COM"],
"_lw_data_source_s":"SpDefault",
"body_t":"# ESP Forecast Informationn#n# …](https://image.slidesharecdn.com/rd0glmjztv61ansejrz0-signature-c75a7d7fcd776973c606549683b9baf42b3c774325d0028542e1af0048998ba4-poli-190925162241/75/Deep-Dive-Security-Trimming-in-Fusion-10-2048.jpg)


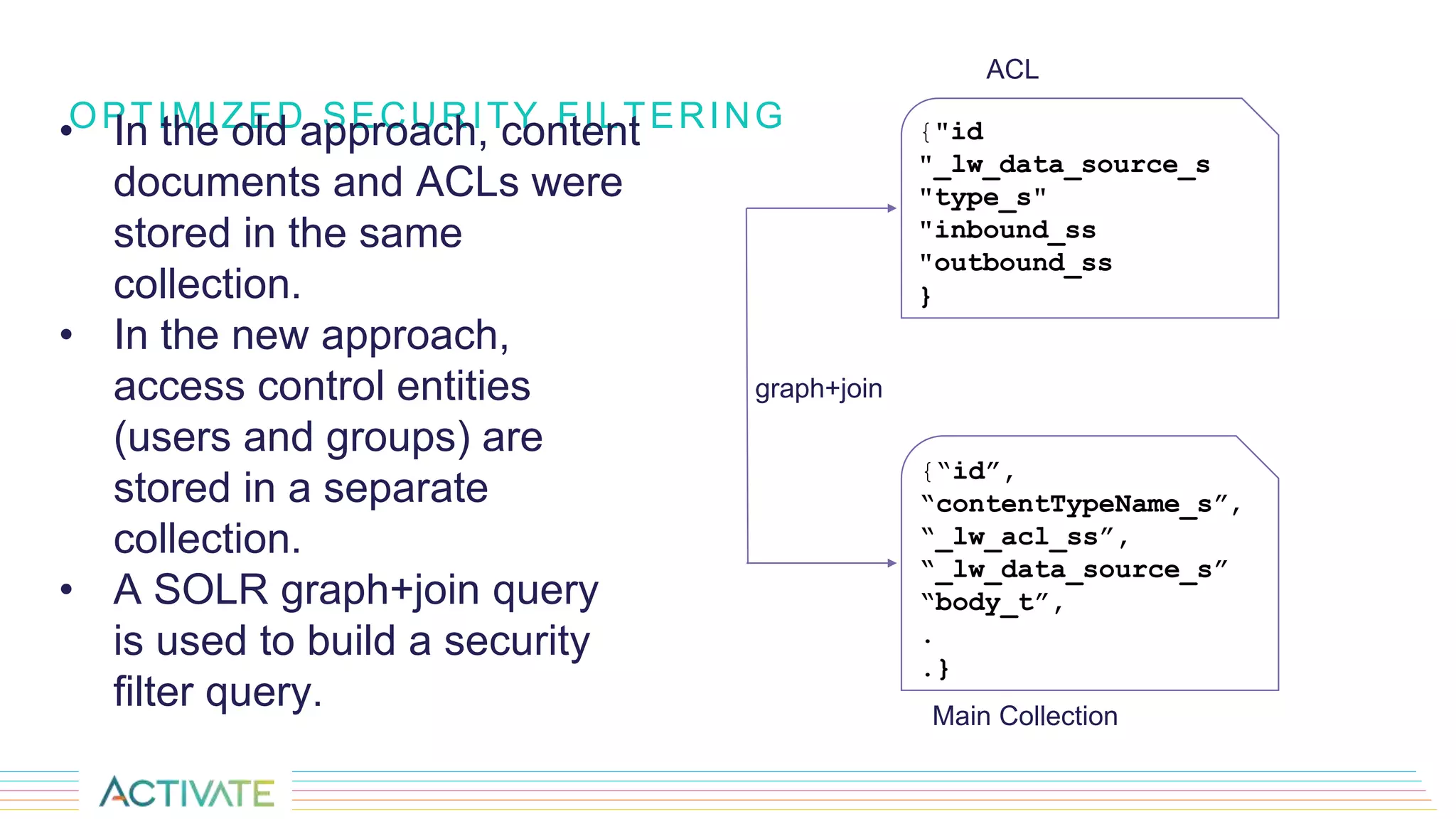
![SOLR COLLECTIONS- MAIN COLLECTION
The _lw_acl_ss field contains the direct users and/or groups that can access the document.
Note: It does not contain the nested groups, just the direct groups and users.
{"id":"https://lwdemo.sharepoint.com/sites/corpa/Shared
Documents/001/001912.ppt",
"parent_s":"https://lwdemo.sharepoint.com/sites/corpa/Shared
Documents/001/001912.ppt",
"contentTypeName_s":"Document",
"_lw_acl_ss":["740c6a0b-85e2-48a0-a494-
e0f1759d4aa7:site:2386a403-8d76-4737-b774-
dabad52201e3:web:7a2f544f-e3ed-444e-8de3-178c2c9b5848:3”. . .
"],
"_lw_data_source_s":"SPv1Optimised",
"editorValue_s":"Nicholas DiPiazza",
"body_t":”Enterprise Resource Management ProgramnnCPIC,
"_version_":1643660287496159232}]](https://image.slidesharecdn.com/rd0glmjztv61ansejrz0-signature-c75a7d7fcd776973c606549683b9baf42b3c774325d0028542e1af0048998ba4-poli-190925162241/75/Deep-Dive-Security-Trimming-in-Fusion-17-2048.jpg)
![SIDECAR COLLECTION- ACL
Field Description
Id ID of the access control
type_s Type of access control (group, user, role assignment, role definition , etc)
outbound_ss Outbound edges, i.e. parent objects can be represented with this field
inbound_ss Inbound edges i.e. list of access controls which are owned by the current
access control
{ "id":"ADFSADMINISTRATORS",
"dn_s":"CN=Administrators,CN=Builtin,DC=adfs,DC=lab,DC=lucidworks,DC=com",
"base_s":"dc=adfs,dc=lab,dc=lucidworks,dc=com",
"_lw_data_source_s":"AclAD",
"type_s":"ldapGroup",
"when_changed_s":"20190611155947.0Z",
"outbound_ss":["ADFSADMINISTRATORS"],
"inbound_ss":["CN=Administrator,CN=Users,DC=adfs,DC=lab,DC=lucidworks,DC=com",
"CN=Domain Admins,CN=Users,DC=adfs,DC=lab,DC=lucidworks,DC=com",
"CN=Enterprise Admins,CN=Users,DC=adfs,DC=lab,DC=lucidworks,DC=com",
"CN=admin2,CN=Users,DC=adfs,DC=lab,DC=lucidworks,DC=com",
"ADFSADMINISTRATORS"],
"_version_":1643736564827684871},
Domain Admins
ldapGroup-dn
admin2
ldapUser-dn
ADFSADMINISTRATORS
ldapGroup-dn
Enterprise Admins
ldapGroup-dn](https://image.slidesharecdn.com/rd0glmjztv61ansejrz0-signature-c75a7d7fcd776973c606549683b9baf42b3c774325d0028542e1af0048998ba4-poli-190925162241/75/Deep-Dive-Security-Trimming-in-Fusion-18-2048.jpg)
![INDEX WORK FLOW – NEW APPROACH
LDAP
Data
Source
Parser
Index
Pipeline
ACL Collection
Content Collection
Schedule
LDAP
Connector
{"id":"ADFSNICHOLAS",
"_lw_data_source_s":"AD-ACLs",
"type_s":"user",
"inbound_ss":["ADFSNICHOLAS"],
"outbound_ss":["ADFSNICHOLAS", "all-users"],
"_version_":1643660598409428998},
{ "id":"740c6a0b-85e2-48a0-a494-e0f1759d4aa7:…
"_lw_data_source_s":"SPv1Optimised",
"type_s":"sharepointGroup",
"inbound_ss":["740c… "all-users"],
"outbound_ss":["740c6a0b-… :4"],
"_version_":1643659978005807105},
{"id":"https://lwdemo.share point.com/sites/corpa/Shared
Documents/001/001912.ppt",
"contentTypeName_s":"Document",
"_lw_acl_ss":["740c6a0b-85e2-48a0-a494-
e0f1759d4aa7:site:2386a403-8d76-4737-b774-
dabad52201e3:web:7a2f544f-e3ed-444e-8de3-
178c2c9b5848:3", …."],
"_lw_data_source_s":"SPv1Optimised",
"body_t":"Enterprise Resource Management Program”}
1
2
a
b
c](https://image.slidesharecdn.com/rd0glmjztv61ansejrz0-signature-c75a7d7fcd776973c606549683b9baf42b3c774325d0028542e1af0048998ba4-poli-190925162241/75/Deep-Dive-Security-Trimming-in-Fusion-19-2048.jpg)