Decomposition of network part 2 bk
•
0 likes•313 views
Barkley & Motard Algorithm and Basic Tearing Algorithm
Report
Share
Report
Share
Download to read offline
Recommended
https://arxiv.org/abs/2011.04370
A concept of quantum computing is proposed which naturally incorporates an additional kind of uncertainty, i.e. vagueness (fuzziness), by introducing obscure qudits (qubits), which are simultaneously characterized by a quantum probability and a membership function. Along with the quantum amplitude, a membership amplitude for states is introduced. The Born rule is used for the quantum probability only, while the membership function can be computed through the membership amplitudes according to a chosen model. Two different versions are given here: the "product" obscure qubit in which the resulting amplitude is a product of the quantum amplitude and the membership amplitude, and the "Kronecker" obscure qubit, where quantum and vagueness computations can be performed independently (i.e. quantum computation alongside truth). The measurement and entanglement of obscure qubits are briefly described.S.Duplij, R.Vogl, "Membership amplitudes and obscure qudits", arXiv:2011.04370 

S.Duplij, R.Vogl, "Membership amplitudes and obscure qudits", arXiv:2011.04370 Steven Duplij (Stepan Douplii)
Recommended
https://arxiv.org/abs/2011.04370
A concept of quantum computing is proposed which naturally incorporates an additional kind of uncertainty, i.e. vagueness (fuzziness), by introducing obscure qudits (qubits), which are simultaneously characterized by a quantum probability and a membership function. Along with the quantum amplitude, a membership amplitude for states is introduced. The Born rule is used for the quantum probability only, while the membership function can be computed through the membership amplitudes according to a chosen model. Two different versions are given here: the "product" obscure qubit in which the resulting amplitude is a product of the quantum amplitude and the membership amplitude, and the "Kronecker" obscure qubit, where quantum and vagueness computations can be performed independently (i.e. quantum computation alongside truth). The measurement and entanglement of obscure qubits are briefly described.S.Duplij, R.Vogl, "Membership amplitudes and obscure qudits", arXiv:2011.04370 

S.Duplij, R.Vogl, "Membership amplitudes and obscure qudits", arXiv:2011.04370 Steven Duplij (Stepan Douplii)
7th Semester Electronic and Communication Engineering (2013-June) Question Pa...

7th Semester Electronic and Communication Engineering (2013-June) Question Pa...BGS Institute of Technology, Adichunchanagiri University (ACU)
More Related Content
What's hot
7th Semester Electronic and Communication Engineering (2013-June) Question Pa...

7th Semester Electronic and Communication Engineering (2013-June) Question Pa...BGS Institute of Technology, Adichunchanagiri University (ACU)
What's hot (18)
A novel method for mounting gunn diode in active slot ring

A novel method for mounting gunn diode in active slot ring
Jarrod Hurley: Interactions Between White Dwarfs, Neutron Stars and Black Hol...

Jarrod Hurley: Interactions Between White Dwarfs, Neutron Stars and Black Hol...
7th Semester Electronic and Communication Engineering (2013-June) Question Pa...

7th Semester Electronic and Communication Engineering (2013-June) Question Pa...
RADIAL BASIS FUNCTION PROCESS NEURAL NETWORK TRAINING BASED ON GENERALIZED FR...

RADIAL BASIS FUNCTION PROCESS NEURAL NETWORK TRAINING BASED ON GENERALIZED FR...
Multiple Resonant Multiconductor Transmission line Resonator Design using Cir...

Multiple Resonant Multiconductor Transmission line Resonator Design using Cir...
Similar to Decomposition of network part 2 bk
Similar to Decomposition of network part 2 bk (20)
International Journal of Computational Engineering Research(IJCER)

International Journal of Computational Engineering Research(IJCER)
IRJET- Design of Phased Array Antenna for Beam Forming Applications using...

IRJET- Design of Phased Array Antenna for Beam Forming Applications using...
Adiabatic Logic Based Low Power Carry Select Adder for future Technologies

Adiabatic Logic Based Low Power Carry Select Adder for future Technologies
Toward coordinated transmission and distribution operations

Toward coordinated transmission and distribution operations
Modelling And Miniaturization of A 2-Bits Phase Shifter Using Koch Fractal Sh...

Modelling And Miniaturization of A 2-Bits Phase Shifter Using Koch Fractal Sh...
Integration of Irreversible Gates in Reversible Circuits Using NCT Library

Integration of Irreversible Gates in Reversible Circuits Using NCT Library
Optimum Network Reconfiguration using Grey Wolf Optimizer

Optimum Network Reconfiguration using Grey Wolf Optimizer
A Novel Approach for Allocation of Optimal Capacitor and Distributed Generati...

A Novel Approach for Allocation of Optimal Capacitor and Distributed Generati...
Implementation of BDDs by Various Techniques in Low Power VLSI Design

Implementation of BDDs by Various Techniques in Low Power VLSI Design
CONCURRENT TERNARY GALOIS-BASED COMPUTATION USING NANO-APEX MULTIPLEXING NIBS...

CONCURRENT TERNARY GALOIS-BASED COMPUTATION USING NANO-APEX MULTIPLEXING NIBS...
CONCURRENT TERNARY GALOIS-BASED COMPUTATION USING NANO-APEX MULTIPLEXING NIBS...

CONCURRENT TERNARY GALOIS-BASED COMPUTATION USING NANO-APEX MULTIPLEXING NIBS...
Recently uploaded
Call girls in delhi ✔️✔️🔝 9953056974 🔝✔️✔️Welcome To Vip Escort Services In Delhi [ ]Noida Gurgaon 24/7 Open Sex Escort Services With Happy Ending ServiCe Done By Most Attractive Charming Soft Spoken Bold Beautiful Full Cooperative Independent Escort Girls ServiCe In All-Star Hotel And Home Service In All Over Delhi, Noida, Gurgaon, Faridabad, Ghaziabad, Greater Noida,
• IN CALL AND OUT CALL SERVICE IN DELHI NCR
• 3* 5* 7* HOTELS SERVICE IN DELHI NCR
• 24 HOURS AVAILABLE IN DELHI NCR
• INDIAN, RUSSIAN, PUNJABI, KASHMIRI ESCORTS
• REAL MODELS, COLLEGE GIRLS, HOUSE WIFE, ALSO AVAILABLE
• SHORT TIME AND FULL TIME SERVICE AVAILABLE
• HYGIENIC FULL AC NEAT AND CLEAN ROOMS AVAIL. IN HOTEL 24 HOURS
• DAILY NEW ESCORTS STAFF AVAILABLE
• MINIMUM TO MAXIMUM RANGE AVAILABLE.
Call Girls in Delhi & Independent Escort Service –
CALL GIRLS SERVICE DELHI NCR
Vip call girls in Delhi
Call Girls in Delhi, Call Girl Service 24×7 open
Call Girls in Delhi Best Delhi Escorts in Delhi
Low Rate Call Girls In Saket Delhi
X~CALL GIRLS IN Ramesh Nagar Metro
best Delhi call girls and Delhi escort service.
CALL GIRLS SERVICE IN ALL DELHI …
(Delhi) Call Girls in (Chanakyapuri)
Hot And Sexy Independent Model Escort Service In Delhi Unlimited Enjoy Genuine 100% Profiles And Trusted Door Step Call Girls Feel Free To Call Us Female Service Hot Busty & Sexy Party Girls Available For Complete Enjoyment. We Guarantee Full Satisfaction & In Case Of Any Unhappy Experience, We Would Refund Your Fees, Without Any Questions Asked. Feel Free To Call Us Female Service Provider Hours Opens Thanks.
Delhi Escorts Services 100% secure Services.Incall_OutCall Available and outcall Services provide.
We are available 24*7 for Full Night and short Time Escort Services all over Delhi NCR.
Delhi All Hotel Services available 3* 4* 5* Call Call
Delhi Escorts Services And Delhi Call Girl Agency 100% secure Services in my agency. Incall and outcall Services provide.
We are available 24*7 for Full Night and short Time Escort Services my agency in all over New Delhi
Delhi All Hotel Services available my agency
SERVICES [✓✓✓]
Housewife
College Girl
VIP Escort
Independent Girl
Aunty
Without a Condom sucking )?
Sexy Aunty.DSL (Dick Sucking Lips)?
DT (Dining at the Toes English Spanking)
Doggie (Sex style from no behind)??
OutCall- All Over Delhi Noida Gurgaon 24/7
FOR APPOINTMENT Call/Whatsop / 9953056974Call Girls in Ramesh Nagar Delhi 💯 Call Us 🔝9953056974 🔝 Escort Service

Call Girls in Ramesh Nagar Delhi 💯 Call Us 🔝9953056974 🔝 Escort Service9953056974 Low Rate Call Girls In Saket, Delhi NCR
Model Call Girl Services in Delhi reach out to us at 🔝 9953056974 🔝✔️✔️
Our agency presents a selection of young, charming call girls available for bookings at Oyo Hotels. Experience high-class escort services at pocket-friendly rates, with our female escorts exuding both beauty and a delightful personality, ready to meet your desires. Whether it's Housewives, College girls, Russian girls, Muslim girls, or any other preference, we offer a diverse range of options to cater to your tastes.
We provide both in-call and out-call services for your convenience. Our in-call location in Delhi ensures cleanliness, hygiene, and 100% safety, while our out-call services offer doorstep delivery for added ease.
We value your time and money, hence we kindly request pic collectors, time-passers, and bargain hunters to refrain from contacting us.
Our services feature various packages at competitive rates:
One shot: ₹2000/in-call, ₹5000/out-call
Two shots with one girl: ₹3500/in-call, ₹6000/out-call
Body to body massage with sex: ₹3000/in-call
Full night for one person: ₹7000/in-call, ₹10000/out-call
Full night for more than 1 person: Contact us at 🔝 9953056974 🔝. for details
Operating 24/7, we serve various locations in Delhi, including Green Park, Lajpat Nagar, Saket, and Hauz Khas near metro stations.
For premium call girl services in Delhi 🔝 9953056974 🔝. Thank you for considering us!Call Now ≽ 9953056974 ≼🔝 Call Girls In New Ashok Nagar ≼🔝 Delhi door step de...

Call Now ≽ 9953056974 ≼🔝 Call Girls In New Ashok Nagar ≼🔝 Delhi door step de...9953056974 Low Rate Call Girls In Saket, Delhi NCR
Booking open Available Pune Call Girls Koregaon Park 6297143586 Call Hot Indian Girls Waiting For You To Fuck
Booking Contact Details
WhatsApp Chat: +91-6297143586
pune Escort Service includes providing maximum physical satisfaction to their clients as well as engaging conversation that keeps your time enjoyable and entertaining. Plus they look fabulously elegant; making an impressionable.
Independent Escorts pune understands the value of confidentiality and discretion - they will go the extra mile to meet your needs. Simply contact them via text messaging or through their online profiles; they'd be more than delighted to accommodate any request or arrange a romantic date or fun-filled night together.
We provide -
01-may-2024(v.n)
Booking open Available Pune Call Girls Koregaon Park 6297143586 Call Hot Ind...

Booking open Available Pune Call Girls Koregaon Park 6297143586 Call Hot Ind...Call Girls in Nagpur High Profile
Recently uploaded (20)
CCS335 _ Neural Networks and Deep Learning Laboratory_Lab Complete Record

CCS335 _ Neural Networks and Deep Learning Laboratory_Lab Complete Record
Call for Papers - Educational Administration: Theory and Practice, E-ISSN: 21...

Call for Papers - Educational Administration: Theory and Practice, E-ISSN: 21...
Call Girls in Ramesh Nagar Delhi 💯 Call Us 🔝9953056974 🔝 Escort Service

Call Girls in Ramesh Nagar Delhi 💯 Call Us 🔝9953056974 🔝 Escort Service
Call Now ≽ 9953056974 ≼🔝 Call Girls In New Ashok Nagar ≼🔝 Delhi door step de...

Call Now ≽ 9953056974 ≼🔝 Call Girls In New Ashok Nagar ≼🔝 Delhi door step de...
Call Girls Wakad Call Me 7737669865 Budget Friendly No Advance Booking

Call Girls Wakad Call Me 7737669865 Budget Friendly No Advance Booking
Booking open Available Pune Call Girls Koregaon Park 6297143586 Call Hot Ind...

Booking open Available Pune Call Girls Koregaon Park 6297143586 Call Hot Ind...
Call Girls In Bangalore ☎ 7737669865 🥵 Book Your One night Stand

Call Girls In Bangalore ☎ 7737669865 🥵 Book Your One night Stand
VIP Call Girls Ankleshwar 7001035870 Whatsapp Number, 24/07 Booking

VIP Call Girls Ankleshwar 7001035870 Whatsapp Number, 24/07 Booking
VIP Model Call Girls Kothrud ( Pune ) Call ON 8005736733 Starting From 5K to ...

VIP Model Call Girls Kothrud ( Pune ) Call ON 8005736733 Starting From 5K to ...
chapter 5.pptx: drainage and irrigation engineering

chapter 5.pptx: drainage and irrigation engineering
Roadmap to Membership of RICS - Pathways and Routes

Roadmap to Membership of RICS - Pathways and Routes
Decomposition of network part 2 bk
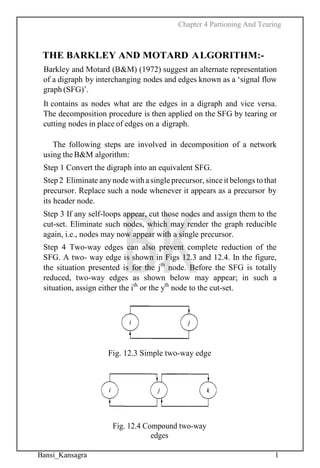
- 1. Chapter 4 Partioning And Tearing Bansi_Kansagra 1 THE BARKLEY AND MOTARD ALGORITHM:- Barkley and Motard (B&M) (1972) suggest an alternate representation of a digraph by interchanging nodes and edges known as a ‘signal flow graph (SFG)’. It contains as nodes what are the edges in a digraph and vice versa. The decomposition procedure is then applied on the SFG by tearing or cutting nodes in place of edges on a digraph. The following steps are involved in decomposition of a network using theB&M algorithm: Step 1 Convert the digraph into an equivalent SFG. Step 2 Eliminate any node with asingle precursor, sinceit belongs to that precursor. Replace such a node whenever it appears as a precursor by its header node. Step 3 If any self-loops appear, cut those nodes and assign them to the cut-set. Eliminate such nodes, which may render the graph reducible again, i.e., nodes may now appear with a single precursor. Step 4 Two-way edges can also prevent complete reduction of the SFG. A two- way edge is shown in Figs 12.3 and 12.4. In the figure, the situation presented is for the jth node. Before the SFG is totally reduced, two-way edges as shown below may appear; in such a situation, assign either the ith or the yth node to the cut-set. Fig. 12.3 Simple two-way edge Fig. 12.4 Compound two-way edges
- 2. Chapter 4 Partioning And Tearing Bansi_Kansagra 2 Step 5 If all other conditions fail to appear, select the node with the maximum number of output edges for cutting. Step 6 When SFG is totally reduced, the cut-set is found. Illustration 12.1 Using the Barkley and Motard (1972) method (B&M algorithm) for the decomposition of a maximal cyclic net (MCN), find out the streams that are to be teared (i.e., cut-set) for the digraph (Fig. 12.1) of a process: (decomposition is by a minimum number of tear streams, all of them assigned unit weight). Solution First reduction Eliminate any node with a single precursor, since it belongs to that precursor. Then, replace such a node whenever it appears as a precursor by its header node.
- 3. Chapter 4 Partioning And Tearing Bansi_Kansagra 3 Note Replace the nodes which are eliminated with their precursors. In the above table, (1) eliminate each node with only one precursor (i.e., remove nodes 1, 3, 5, 8 since these belong to that precursor) and (2) replace such nodes in all their occurrences in the list of precursors by their precursors, i.e., we need to replace node 3 with its precursor 2. Similarly, we replace node 5 with its precursor 7, node 1 with its precursor 2, and node 8 with its precursor 7. The remaining nodes are 2, 4, 6, and 7. (If nodes 1, 3, 5, 8 are removed.) The remaining nodes are shown above in which two ‘self- loops’ are formed at nodes 2 and 7. Now cut these nodes, remove them from the above table and repeat the same procedure. As a result, the SFG is totally reduced and the cut-set found consists of nodes 2 and 7 (where self-loops are formed) or equivalent streams 2 and 7 in the digraph of Fig. 12.1
- 4. Bansi_Kansagra 4 THE BASIC TEARING ALGORITHM:- This is also based on the concept of SFG. Pho and Lapidus (1973a, 1973b) presented an alternative algorithm which offers the advantage of assigning any arbitrary weights (weigh each stream with a number reflecting the probable degree of difficulty that can be encountered in an iterative procedure to converge) to the edges or streams of a digraph. It locates the cut-set of tear streams by minimizing the sum of their weights. This is equivalent to finding minimum weights of tear streams when all of them are assigned unit weights. The features of the basic tearing algorithm (BTA) are as given below: 1. The reduced digraph (one that excludes feed and product streams) is first converted into an equivalent SFG. 2. Information on the SFG is provided to the algorithm in the form of an adjacent matrix. 3. Ineligible nodes arefound according tothefollowing criterion: If theweight of node i is greater than or equal to the sum of weights of non-zero elements in the first rows of the matrix, then that node is ineligible. 4. The reduction of ineligible node I is performed as follows: Shift the elements of column I to those columns in row I containing non-zero elements forming a Boolean sum. Make row I and column I null. 5. Primarily the cut node is found by locating a self-loop. 6. If no ineligible nodes are found, then two-way edges are searched. 7. When all attempts fail, the branch and bound method is ultimately applied to totally reduce the SFG. The algorithm is shown in Fig. 12.5.
