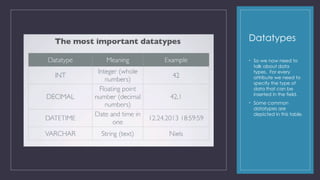
This document covers essential topics in data modeling, including data types, relationships, and normalization for physical data models. It discusses the importance of specifying data types for attributes, the implementation of primary and foreign keys, and how relationships are represented through intermediate tables to facilitate many-to-many relationships. Additionally, it provides practical assignments related to creating physical data models and emphasizes the importance of adherence to naming standards and constraints in database design.