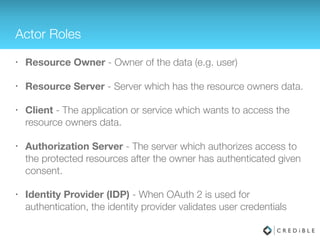
The document provides an overview of data synchronization patterns in mobile application design, focusing on data formats, protocols, security, and privacy. It discusses the efficiency of synchronization methods, examples of ecosystems (open vs. closed), and the importance of security measures like authentication and authorization, including OAuth 2.0 flows. Additionally, it offers practical implementation insights through API examples and security practices.










































![User Authorization w/ Roles
Users mapped to Roles
@RolesAllowed(["ROLE_CLIENT"])
class EventController {
...
@RolesAllowed([“ROLE_ADMIN"])
void save() {}
...
}
Resources Secured by Role](https://image.slidesharecdn.com/datasyncpatternsmobile-codemashcopy-160108191300/85/Data-Synchronization-Patterns-in-Mobile-Application-Design-43-320.jpg)

















![Event API
URI Method Body (JSON) Response
/register POST Registration Cmd Registration Cmd
/login POST Login Cmd OAuth Token
/events/{id} GET n/a Event
/events POST Event n/a
/events[?syncToken=token] GET n/a List<Event>](https://image.slidesharecdn.com/datasyncpatternsmobile-codemashcopy-160108191300/85/Data-Synchronization-Patterns-in-Mobile-Application-Design-62-320.jpg)
![Event API
URI Method Body (JSON) Response
/register POST Registration Cmd Registration Cmd
/login POST Login Cmd OAuth Token
/events/{id} GET n/a Event
/events POST Event n/a
/events[?syncToken=token] GET n/a List<Event>](https://image.slidesharecdn.com/datasyncpatternsmobile-codemashcopy-160108191300/85/Data-Synchronization-Patterns-in-Mobile-Application-Design-63-320.jpg)



![Event API
URI Method Body (JSON) Response
/register POST Registration Cmd Registration Cmd
/login POST Login Cmd OAuth Token
/events/{id} GET n/a Event
/events POST Event n/a
/events[?syncToken=token] GET n/a List<Event>](https://image.slidesharecdn.com/datasyncpatternsmobile-codemashcopy-160108191300/85/Data-Synchronization-Patterns-in-Mobile-Application-Design-67-320.jpg)
![Securing Resources
• Resources secured by url pattern match
class OAuth2ServerConfiguration {
public void configure(ResourceServerSecurityConfigurer resources) {
resources
.resourceId('event-api')
}
public void configure(HttpSecurity http) throws Exception {
http
.authorizeRequests()
.antMatchers("/register", "/login").permitAll()
.anyRequest().authenticated()
}
}
@RolesAllowed(["ROLE_CLIENT"])
class EventController {
...
}
• Authorization based on role](https://image.slidesharecdn.com/datasyncpatternsmobile-codemashcopy-160108191300/85/Data-Synchronization-Patterns-in-Mobile-Application-Design-68-320.jpg)




