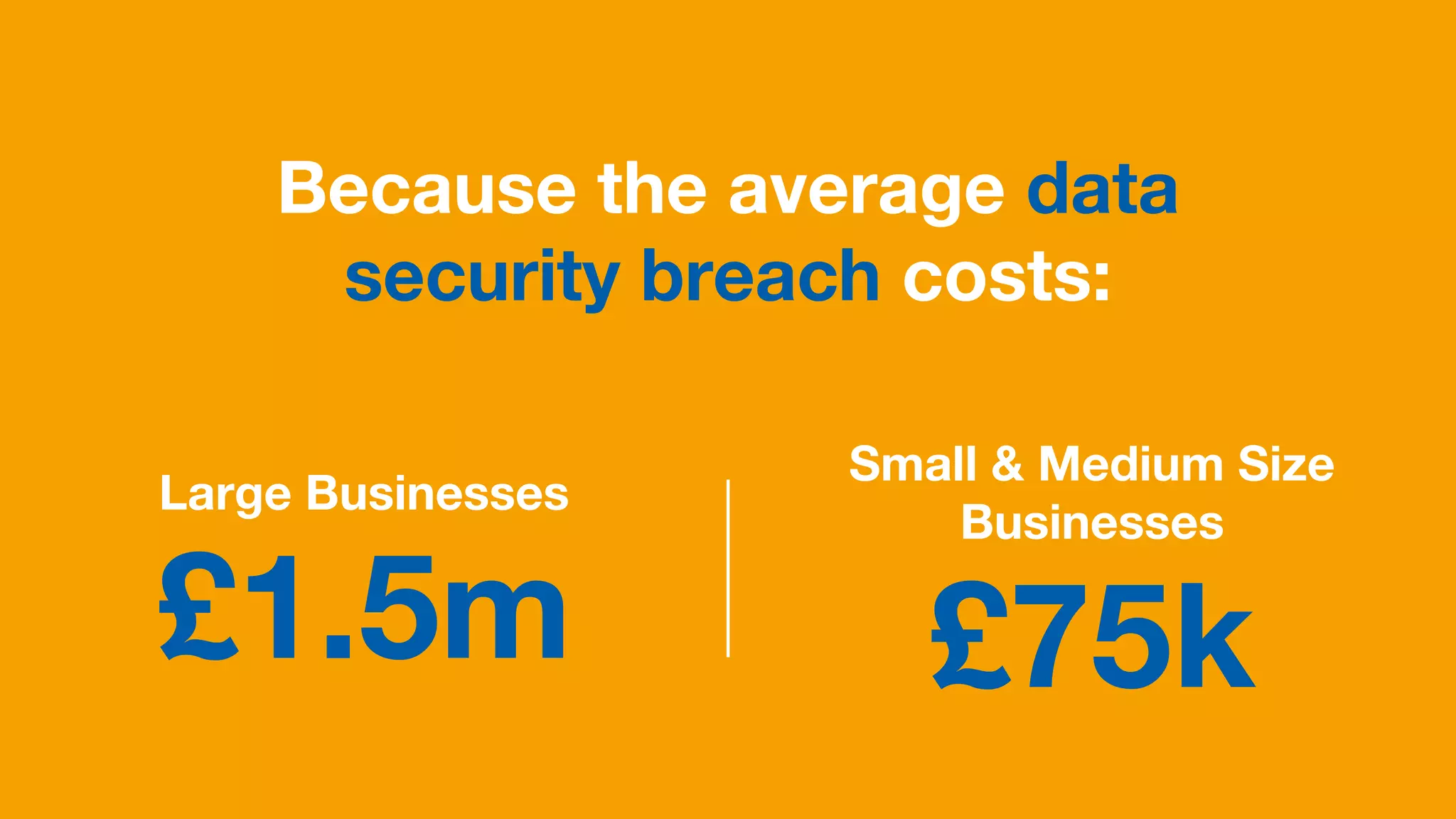
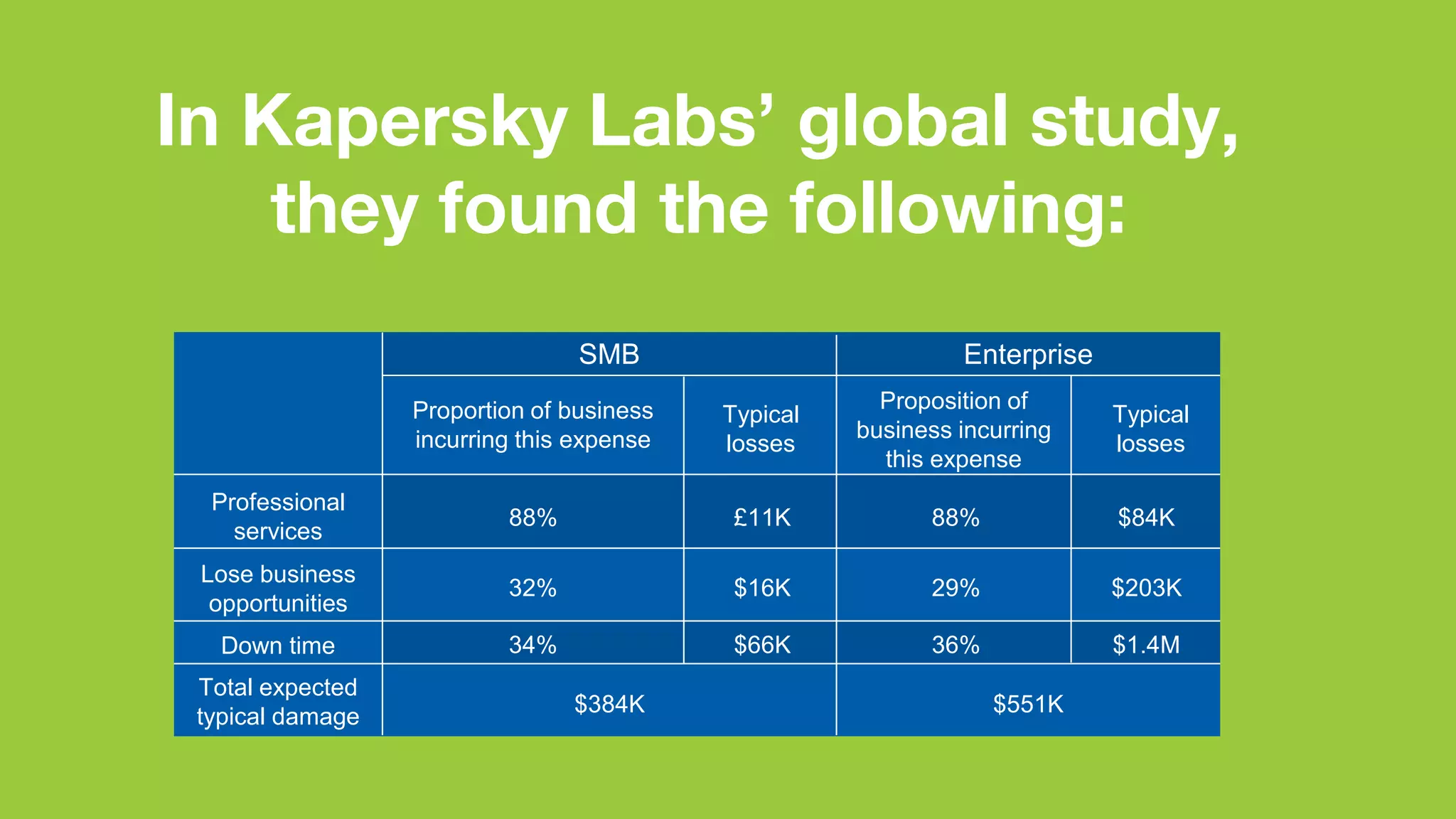
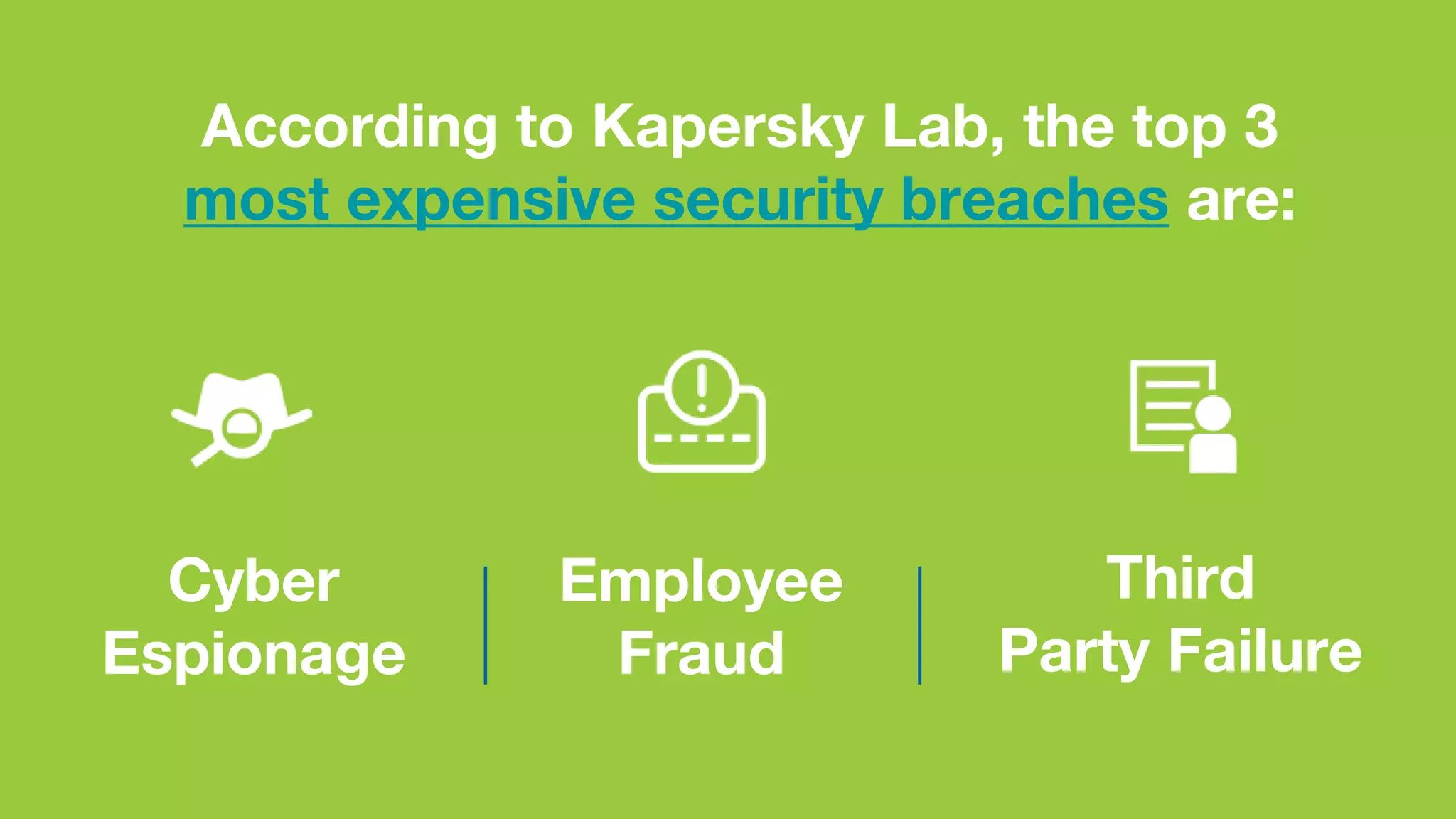
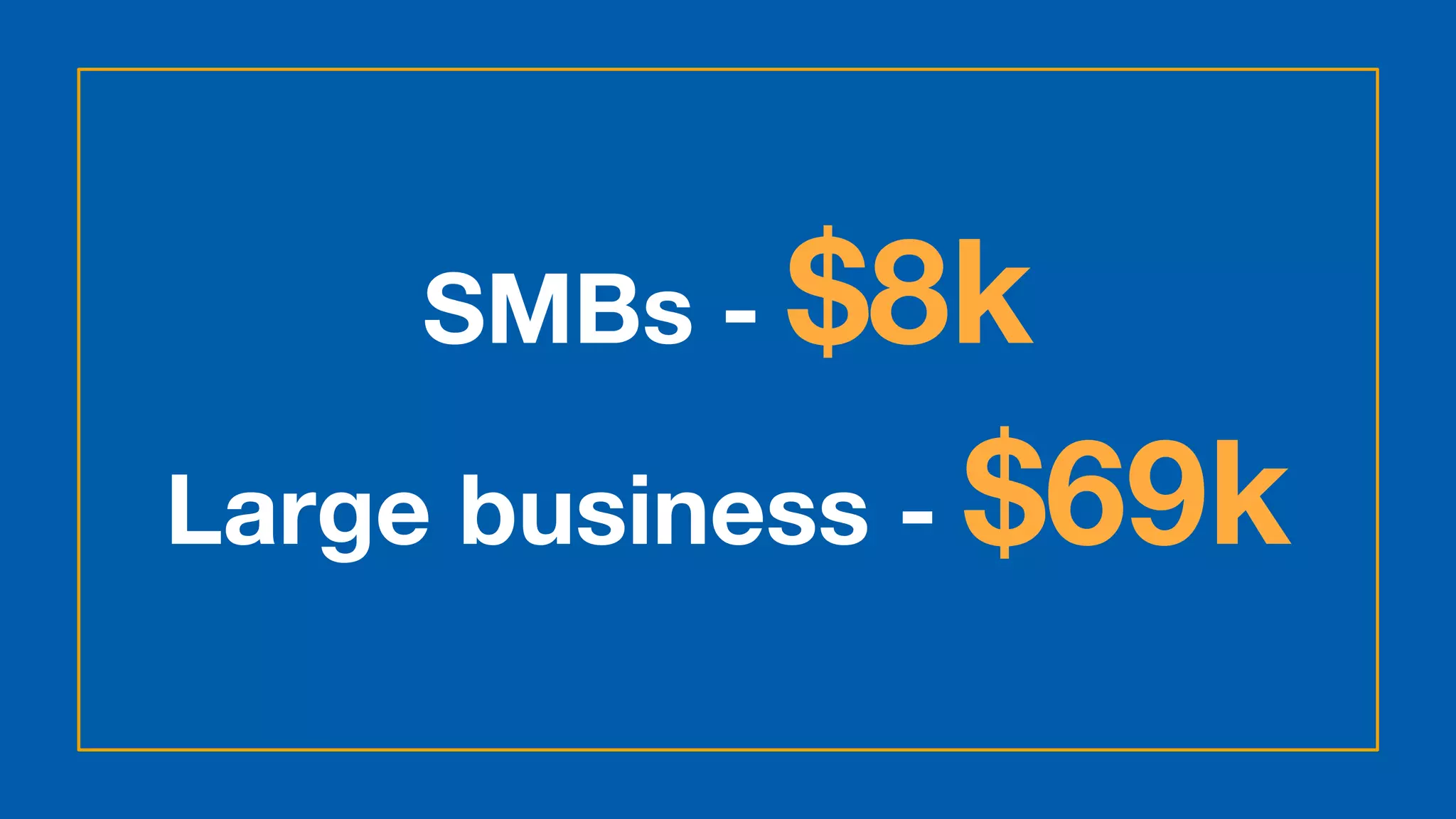
The document discusses the rising data security risks and their financial impact on businesses, highlighting that large businesses face costs averaging £1.5 million per breach while small to medium-sized businesses incur costs of around £75,000. A significant percentage of companies anticipate increased security incidents, prompting necessary changes in operations to mitigate potential downtime and financial losses. Key contributors to these breaches include employee fraud and cyber espionage, with recommendations on improving IT security practices and workforce training to prevent further issues.