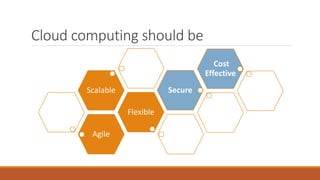
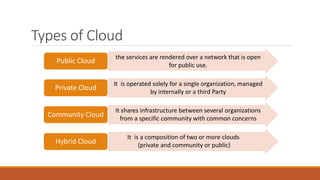
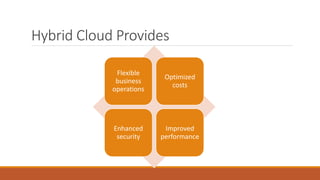
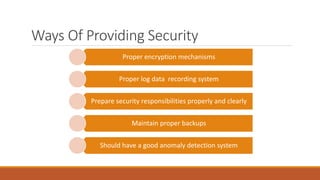
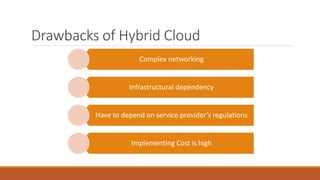
The document discusses data security in hybrid cloud computing, detailing the various types of clouds (public, private, community, hybrid) and their characteristics. It highlights security concerns such as identity management, physical security, availability, application security, privacy, and legal issues, while emphasizing the importance of proper encryption and logging mechanisms. Additionally, it notes drawbacks including complex networking and high implementation costs.