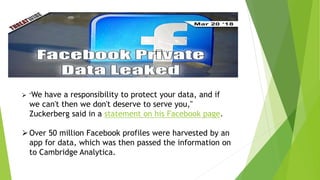
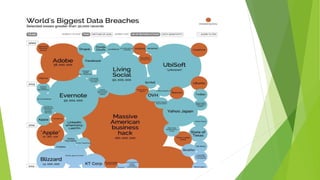
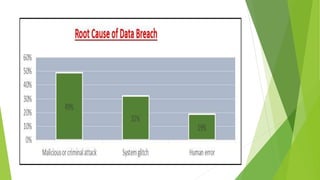
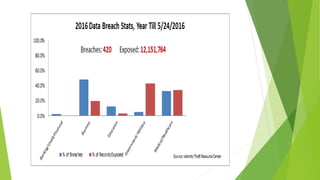
This document discusses data leakage detection techniques. It begins with an introduction to data leakage and examples of how it occurs when data is shared with third parties. It then summarizes some of the largest data breaches of the 21st century. Existing data leakage detection techniques like watermarking and steganography are described along with their disadvantages. The document discusses future applications and scope in the area of data leakage detection and concludes that such techniques can help identify sources of data leaks while data is distributed.














![dx1=dct2(x1); dx11=dx1; //discrete cosine transform
dx2=dct2(x2); dx22=dx2;
dx3=dct2(x3); dx33=dx3;
load m.dat
g=10; // to decide water-marking limit
[rm,cm]=size(m);
dx1(1:rm,1:cm)=dx1(1:rm,1:cm)g*m;
dx1(1:rm,1:cm)=dx1(1:rm,1:cm)g*m;
dx1(1:rm,1:cm)=dx1(1:rm,1:cm)g*m;
figure,imshow(dx1);
figure,imshow(dx2);
figure,imshow(dx3);](https://image.slidesharecdn.com/dataleakagedetection-240313042012-810ea068/85/Data-leakage-detbxhbbhhbsbssusbgsgsbshsbsection-pdf-20-320.jpg)








