Data Breaches Still Major Threat - Infographic from TNS August 2016
•
0 likes•100 views
Data breaches continue to hit the headlines globally. This infographic looks at how data breaches have evolved over the last year and the threat they pose to organizations globally.
Report
Share
Report
Share
Download to read offline
Recommended
More Related Content
Viewers also liked
Viewers also liked (6)
Similar to Data Breaches Still Major Threat - Infographic from TNS August 2016
Similar to Data Breaches Still Major Threat - Infographic from TNS August 2016 (20)
Detecting Frauds and Identifying Security Challenge | by Money2Conf

Detecting Frauds and Identifying Security Challenge | by Money2Conf
Istr number 23 internet security threat repor 2018 symantec

Istr number 23 internet security threat repor 2018 symantec
Symantec (ISTR) Internet Security Threat Report Volume 22

Symantec (ISTR) Internet Security Threat Report Volume 22
Supersized Security Threats – Can You Stop 2016 from Repeating?

Supersized Security Threats – Can You Stop 2016 from Repeating?
Combating Cybersecurity Challenges with Advanced Analytics

Combating Cybersecurity Challenges with Advanced Analytics
Adjusting Your Security Controls: It’s the New Normal

Adjusting Your Security Controls: It’s the New Normal
Recently uploaded
Recently uploaded (20)
Neuro-symbolic is not enough, we need neuro-*semantic*

Neuro-symbolic is not enough, we need neuro-*semantic*
De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...

De-mystifying Zero to One: Design Informed Techniques for Greenfield Innovati...
НАДІЯ ФЕДЮШКО БАЦ «Професійне зростання QA спеціаліста»

НАДІЯ ФЕДЮШКО БАЦ «Професійне зростання QA спеціаліста»
FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf

FIDO Alliance Osaka Seminar: Passkeys and the Road Ahead.pdf
Assuring Contact Center Experiences for Your Customers With ThousandEyes

Assuring Contact Center Experiences for Your Customers With ThousandEyes
From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...

From Daily Decisions to Bottom Line: Connecting Product Work to Revenue by VP...
Quantum Computing: Current Landscape and the Future Role of APIs

Quantum Computing: Current Landscape and the Future Role of APIs
When stars align: studies in data quality, knowledge graphs, and machine lear...

When stars align: studies in data quality, knowledge graphs, and machine lear...
Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...

Empowering NextGen Mobility via Large Action Model Infrastructure (LAMI): pav...
Accelerate your Kubernetes clusters with Varnish Caching

Accelerate your Kubernetes clusters with Varnish Caching
Exploring UiPath Orchestrator API: updates and limits in 2024 🚀

Exploring UiPath Orchestrator API: updates and limits in 2024 🚀
To Graph or Not to Graph Knowledge Graph Architectures and LLMs

To Graph or Not to Graph Knowledge Graph Architectures and LLMs
Essentials of Automations: Optimizing FME Workflows with Parameters

Essentials of Automations: Optimizing FME Workflows with Parameters
Unpacking Value Delivery - Agile Oxford Meetup - May 2024.pptx

Unpacking Value Delivery - Agile Oxford Meetup - May 2024.pptx
In-Depth Performance Testing Guide for IT Professionals

In-Depth Performance Testing Guide for IT Professionals
Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...

Slack (or Teams) Automation for Bonterra Impact Management (fka Social Soluti...
Data Breaches Still Major Threat - Infographic from TNS August 2016
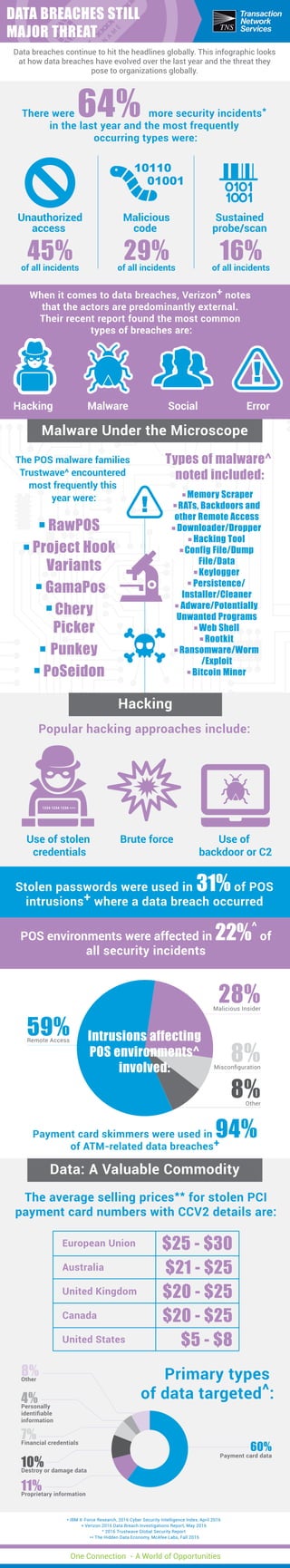
- 1. 45%of all incidents Popular hacking approaches include: Payment card skimmers were used in 94% of ATM-related data breaches+ Stolen passwords were used in 31% of POS intrusions+ where a data breach occurred POS environments were affected in 22%^ of all security incidents The average selling prices** for stolen PCI payment card numbers with CCV2 details are: Malware Under the Microscope Data: A Valuable Commodity Hacking * IBM X-Force Research, 2016 Cyber Security Intelligence Index, April 2016 + Verizon 2016 Data Breach Investigations Report, May 2016 ^ 2016 Trustwave Global Security Report ** The Hidden Data Economy, McAfee Labs, Fall 2015 There were 64% more security incidents* in the last year and the most frequently occurring types were: Unauthorized access The POS malware families Trustwave^ encountered most frequently this year were: Types of malware^ noted included: 29%of all incidents Malicious code 16%of all incidents Sustained probe/scan Hacking Use of stolen credentials Use of backdoor or C2 Brute force Malware Social Error When it comes to data breaches, Verizon+ notes that the actors are predominantly external. Their recent report found the most common types of breaches are: RawPOS Project Hook Variants GamaPos Chery Picker Punkey PoSeidon - Memory Scraper - RATs, Backdoors and other Remote Access - Downloader/Dropper - Hacking Tool - Config File/Dump File/Data - Keylogger - Persistence/ Installer/Cleaner - Adware/Potentially Unwanted Programs - Web Shell - Rootkit - Ransomware/Worm /Exploit - Bitcoin Miner Remote Access Malicious Insider Misconfiguration Other 59% 28% 8% 8% Payment card data 60% Other 8% Personally identifiable information 4% Financial credentials 7% Destroy or damage data 10% Proprietary information 11% Intrusions affecting POS environments^ involved: $25 - $30 $21 - $25 $20 - $25 $20 - $25 $5 - $8 European Union Australia United Kingdom Canada United States Primary types of data targeted^: 1234 1234 1234 **** Data breaches continue to hit the headlines globally. This infographic looks at how data breaches have evolved over the last year and the threat they pose to organizations globally. DATA BREACHES STILL MAJOR THREAT One Connection - A World of Opportunities