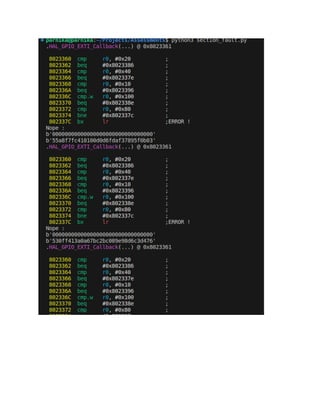
The document outlines a task for embedded security analysis focused on side channel analysis and fault injection to retrieve a hidden flag from an ELF file for an STM32 processor. It describes the requirements, tasks involved including setup, binary analysis, implementation of techniques using specific tools, and documenting the findings. Evaluation criteria include understanding of concepts, practical application, and successful retrieval of the hidden flag.




![from Crypto.Cipher import AES
from rainbow.generics import rainbow_arm
def f_aes(e, key, input_):
e.reset()
# mode : 0xb = MODE_ENC | MODE_AESINIT_ENC | MODE_KEYINIT
e['r0'] = 0xb
# struct_aes
struct_aes_p = 0xcafe0000
e[struct_aes_p] = 0
# struct is huge so we need to map another page
e[struct_aes_p + e.PAGE_SIZE] = 0
e['r1'] = struct_aes_p
# key
key_p = 0xcafe1000
e[key_p] = key
e['r2'] = key_p
# input
input_p = 0xcafe2000
e[input_p] = input_
e['r3'] = input_p
# output
output_p = 0xdead0000
e[output_p] = 0
# ARM calling convention : 4th+ parameter is on stack
e[e['sp']] = output_p
# rest stays to 0
e.start(e.functions['HAL_GPIO_EXTI_Callback'] | 1, 0)
if e['r0']:
print('ERROR !')
res = e[output_p:output_p + 16]](https://image.slidesharecdn.com/cypherockassessment1-231123203531-a3ce4207/85/Cypherock-Assessment-1-pdf-6-320.jpg)
![aes_c = AES.new(key, AES.MODE_ECB)
ref = aes_c.encrypt(input_)
if ref != res:
print("Nope :")
print(hexlify(res))
print(hexlify(ref))
return res
import secrets
def randbytes(n):
return secrets.token_bytes(n)
if __name__ == "__main__":
e = rainbow_arm(print_config=Print.Code | Print.Functions,
trace_config=TraceConfig(register=HammingWeight()))
e.load('stm.elf')
e.setup()
return_addr = 0
# map it to prevent an unmapped fetch exception
e[return_addr] = 0
key = b"xd9" * 16
traces = []
for i in range(5):
print(".", end='')
f_aes(e, key, randbytes(16))
traces.append(np.fromiter(map(lambda event:
event["register"], e.trace), dtype=np.float32))
traces = np.array(traces)
traces += np.random.normal(0, 1, size=traces.shape)
v = plot(traces, dontrun=True)
v.multiple_select(0)
v.run()](https://image.slidesharecdn.com/cypherockassessment1-231123203531-a3ce4207/85/Cypherock-Assessment-1-pdf-7-320.jpg)
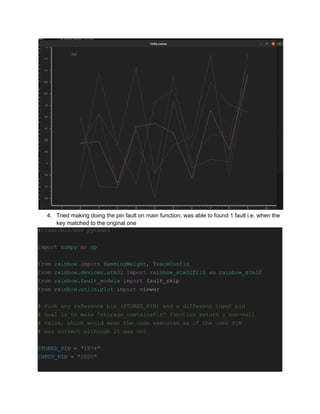
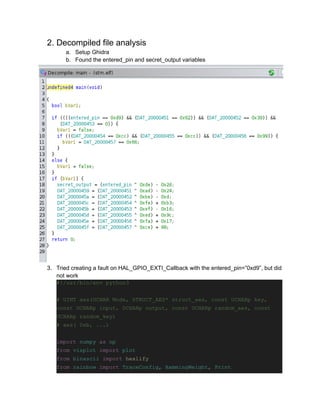
![print("Setting up emulator")
e = rainbow_stm32()
e.load("stm.elf")
e.setup()
def result(u):
""" Test whether execution was faulted """
return u['r0'] != 0 and u['pc'] == 0xaaaaaaaa
# as in the side-channel example, this is the location of the reference
# pin in Flash
e[0x08008110 + 0x189] = bytes(STORED_PIN + "x00", "ascii")
# Pick any address for the input pin...
e[0xcafecafe] = bytes(INPUT_PIN + "x00", "ascii")
N = 57
total_faults = 0
total_crashes = 0
fault_trace = [0] * N
crash_trace = [0] * N
print("Loop on all possible skips")
print("r0 should be 0 at the end of the function if no fault occurred")
for i in range(1, N):
e.reset()
# The first fault might not actually work depending
# on the value of r5 when calling. Remove comment to observe
# e['r5'] = 0x60000000
e['r0'] = 0xcafecafe
e['lr'] = 0xaaaaaaaa
pc = 0
try:](https://image.slidesharecdn.com/cypherockassessment1-231123203531-a3ce4207/85/Cypherock-Assessment-1-pdf-10-320.jpg)
![# Run i instruction, then inject skip, then run
pc = e.start_and_fault(fault_skip, i, e.functions['main'],
0xaaaaaaaa, count=100)
except RuntimeError:
# Fault crashed the emulation
total_crashes += 1
crash_trace[i] = 1
d = e.disassemble_single(pc, 4)
e.print_asmline(pc, d[2], d[3])
pc += d[1]
print("crashed")
continue
except IndexError:
pass
# Print current instruction
d = e.disassemble_single(pc, 4)
e.print_asmline(pc, d[2], d[3])
pc += d[1]
if result(e):
# Successful fault
total_faults += 1
fault_trace[i] = 1
print(" <-- r0 =", hex(e['r0']), end="")
print(f"n=== {total_faults} faults found ===")
print(f"=== {total_crashes} crashes ===")
# get an 'original' side channel trace
e = rainbow_stm32(trace_config=TraceConfig(register=HammingWeight(),
instruction=True))
e.load("stm.elf")
e.setup()
e['r0'] = 0xcafecafe
e['lr'] = 0xaaaaaaaa
e.start(e.functions['main'], 0xaaaaaaaa)](https://image.slidesharecdn.com/cypherockassessment1-231123203531-a3ce4207/85/Cypherock-Assessment-1-pdf-11-320.jpg)
![trace = np.array([event["register"] for event in e.trace if "register" in
event], dtype=np.uint8)
fault_trace = trace.max() - np.array(fault_trace,
dtype=np.uint8)[:trace.shape[0]] * trace.max()
viewer([event["instruction"] for event in e.trace], np.array([trace,
fault_trace]))](https://image.slidesharecdn.com/cypherockassessment1-231123203531-a3ce4207/85/Cypherock-Assessment-1-pdf-12-320.jpg)

