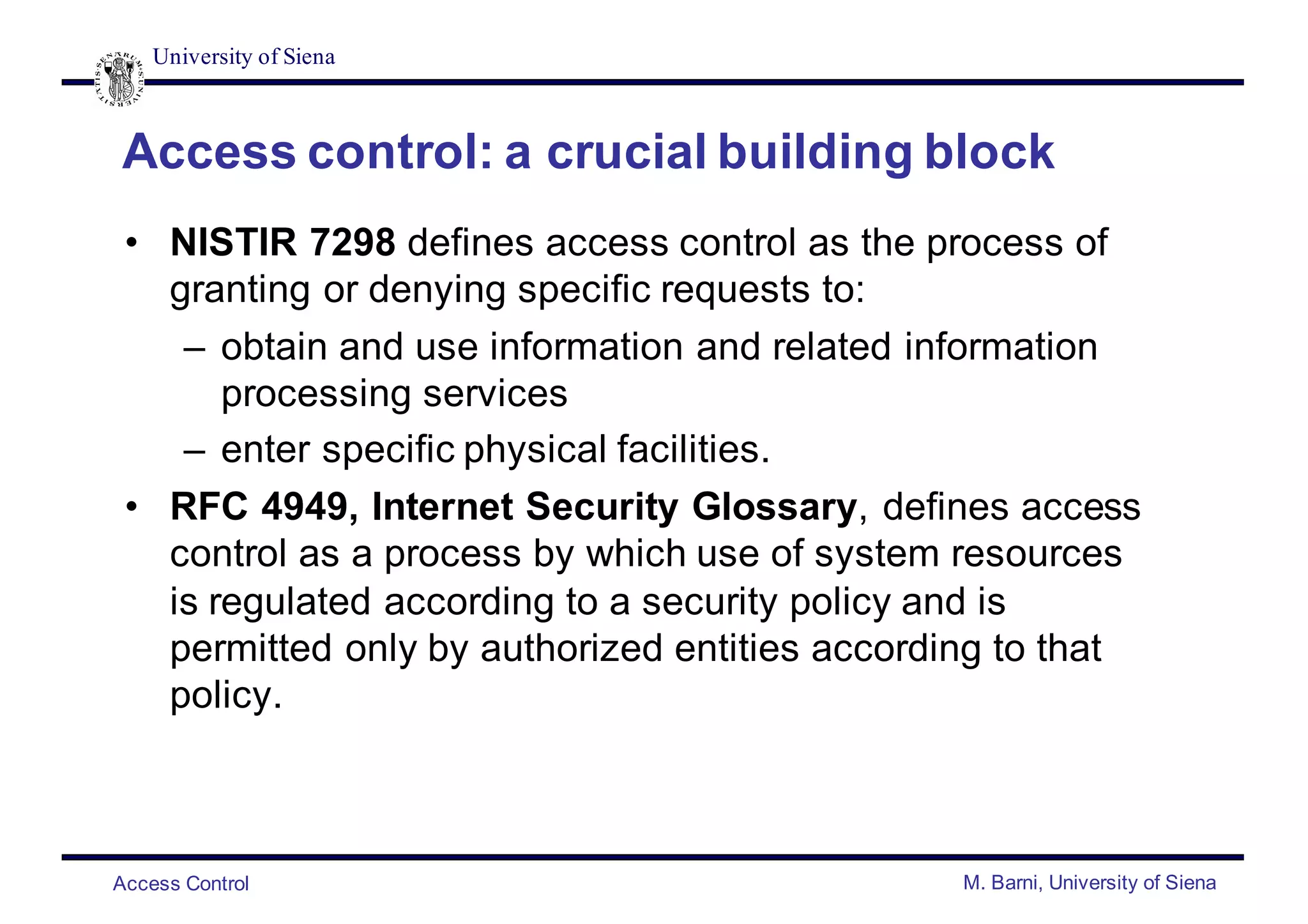
This document discusses access control and provides an overview of different access control models. It defines access control as the process of regulating use of system resources according to a security policy. The key points made are:
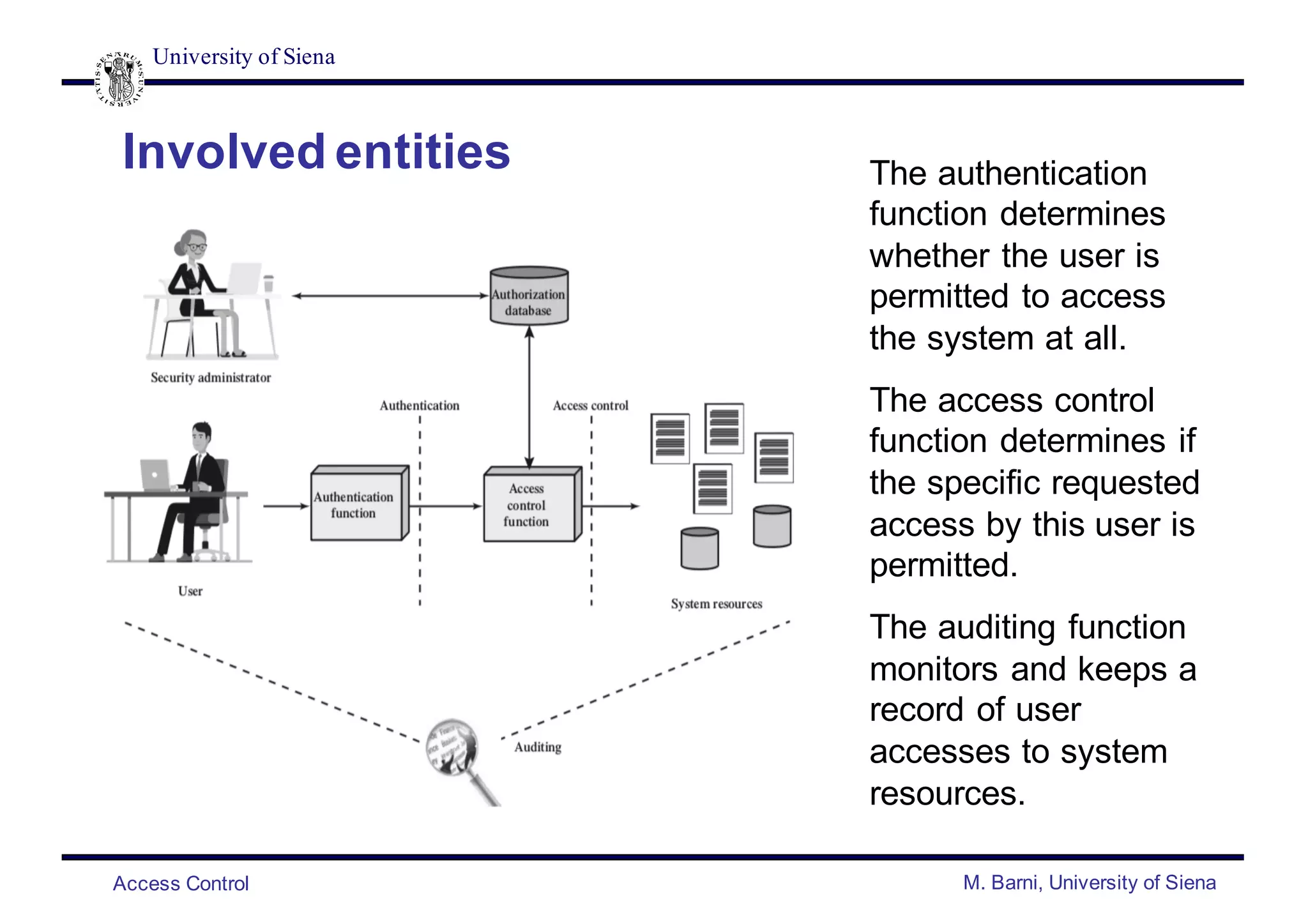
- Access control involves authentication, authorization, and auditing functions.
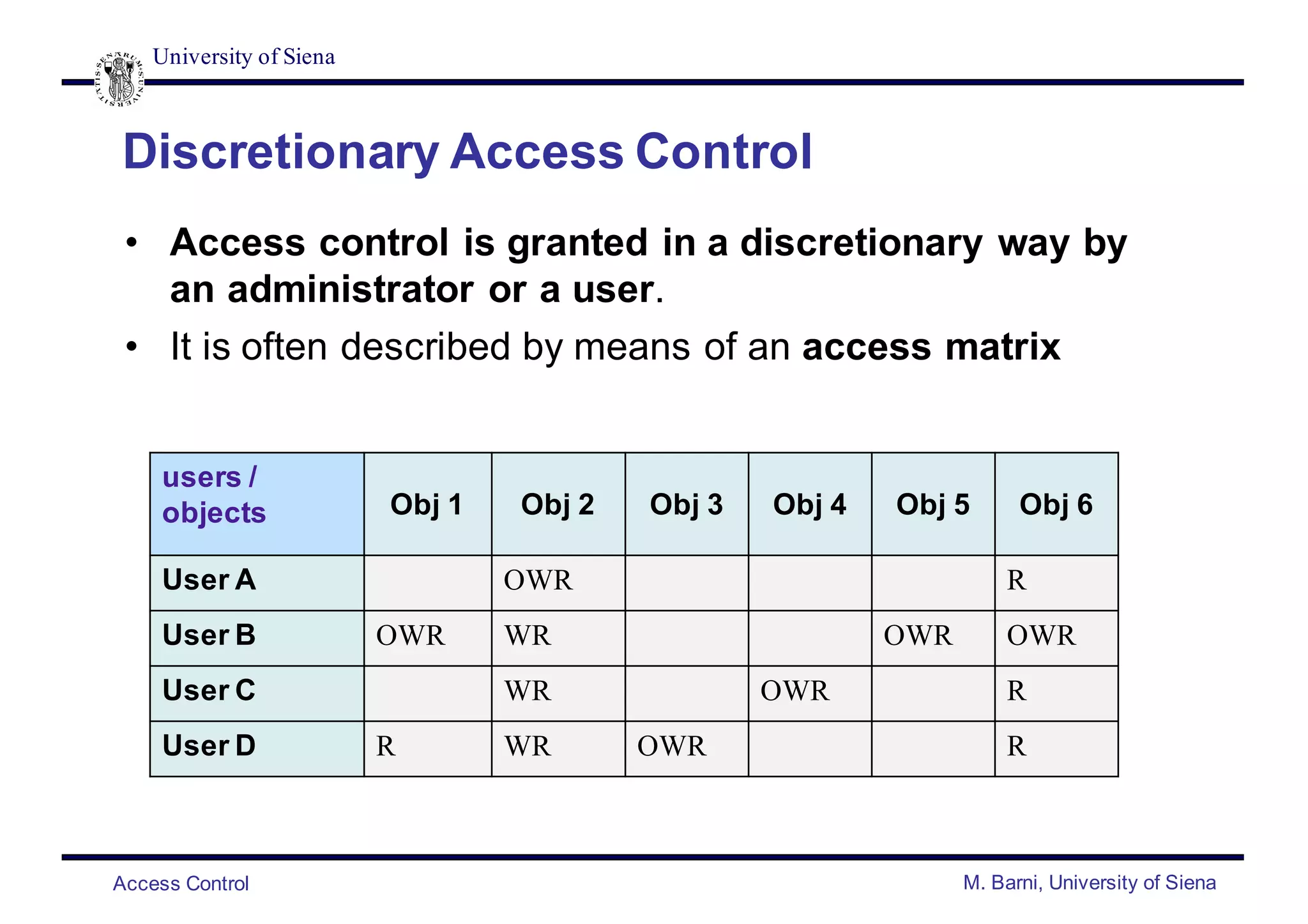
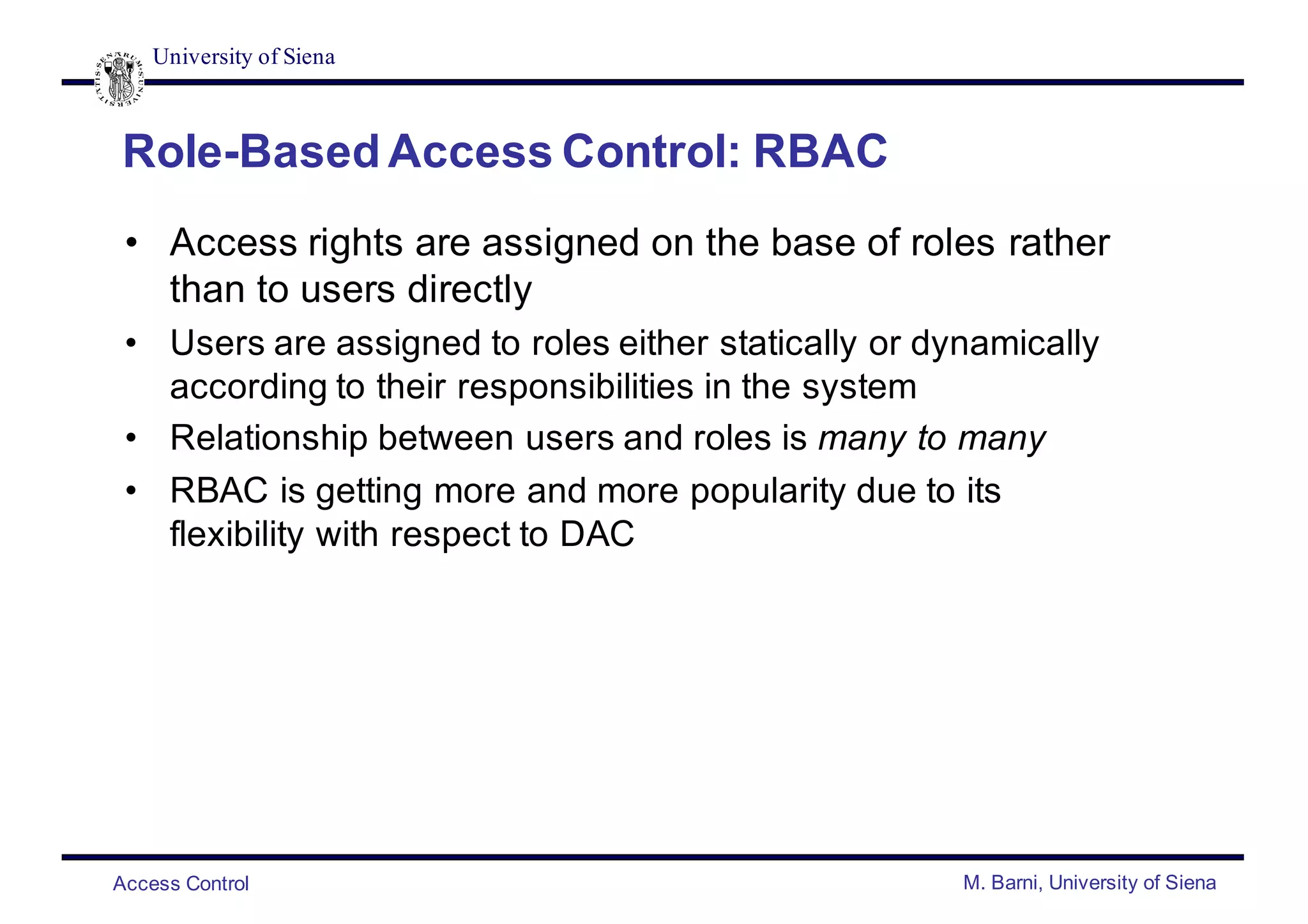
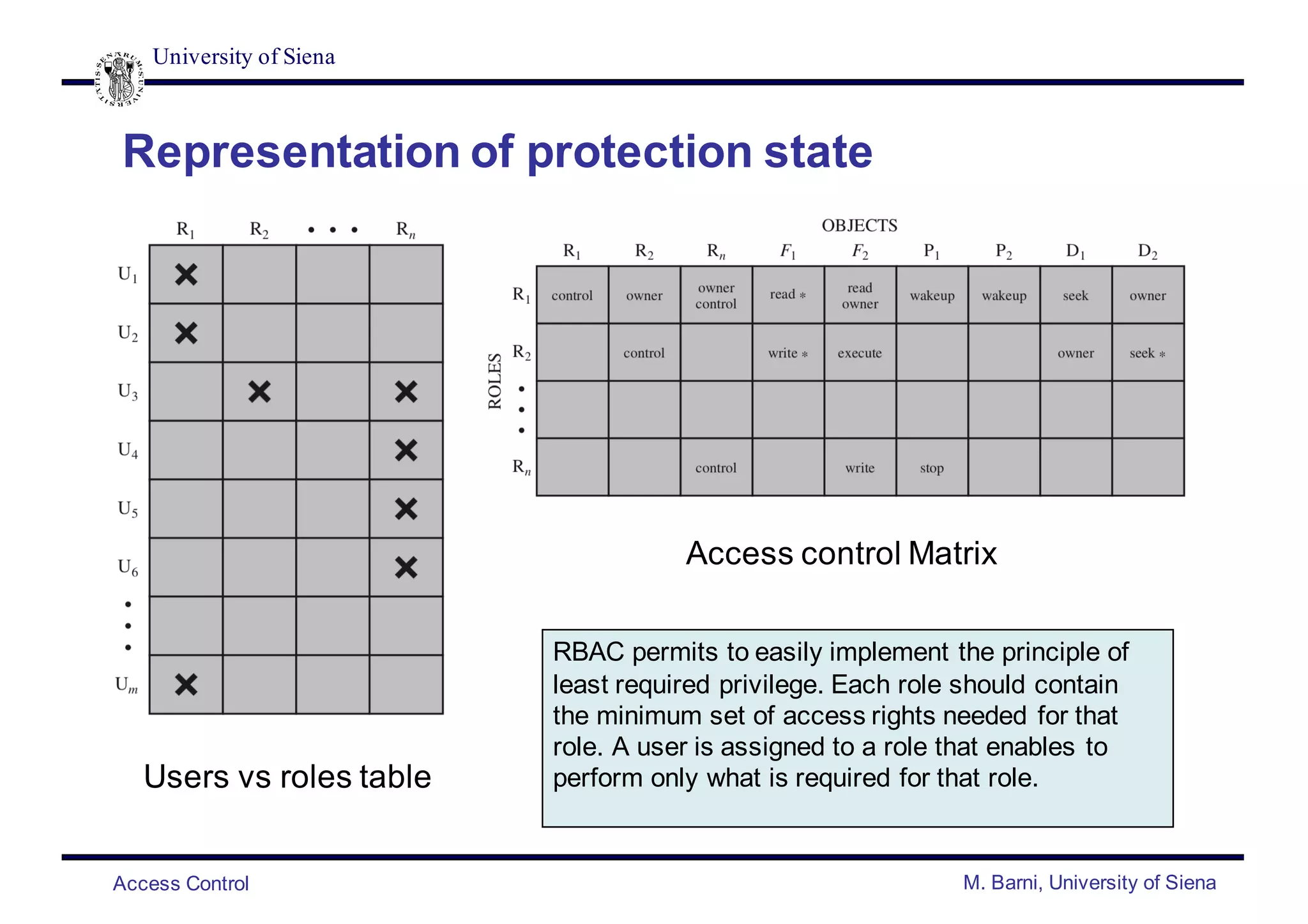
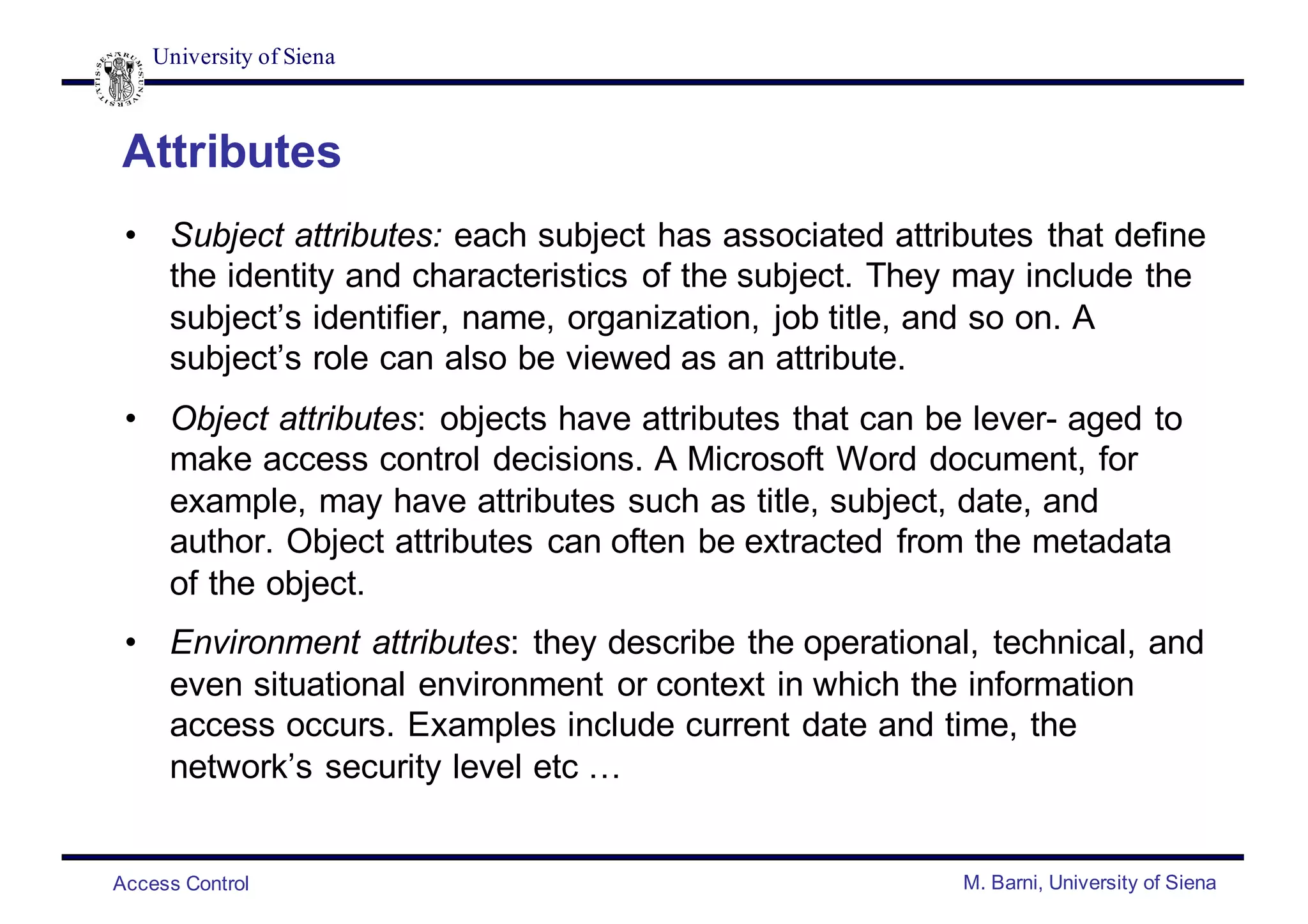
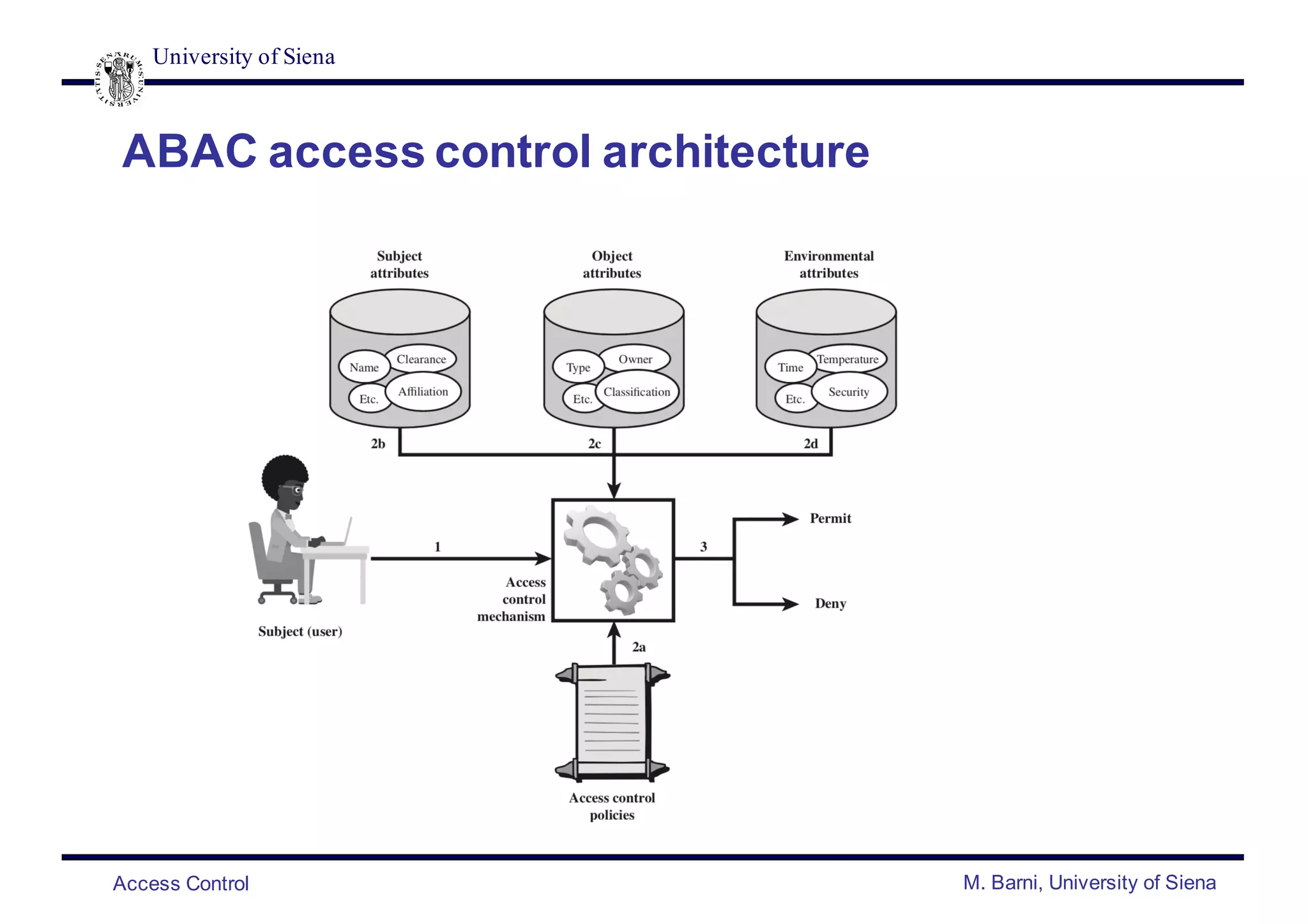
- Common access control policies include discretionary access control (DAC), mandatory access control (MAC), role-based access control (RBAC), and attribute-based access control (ABAC).
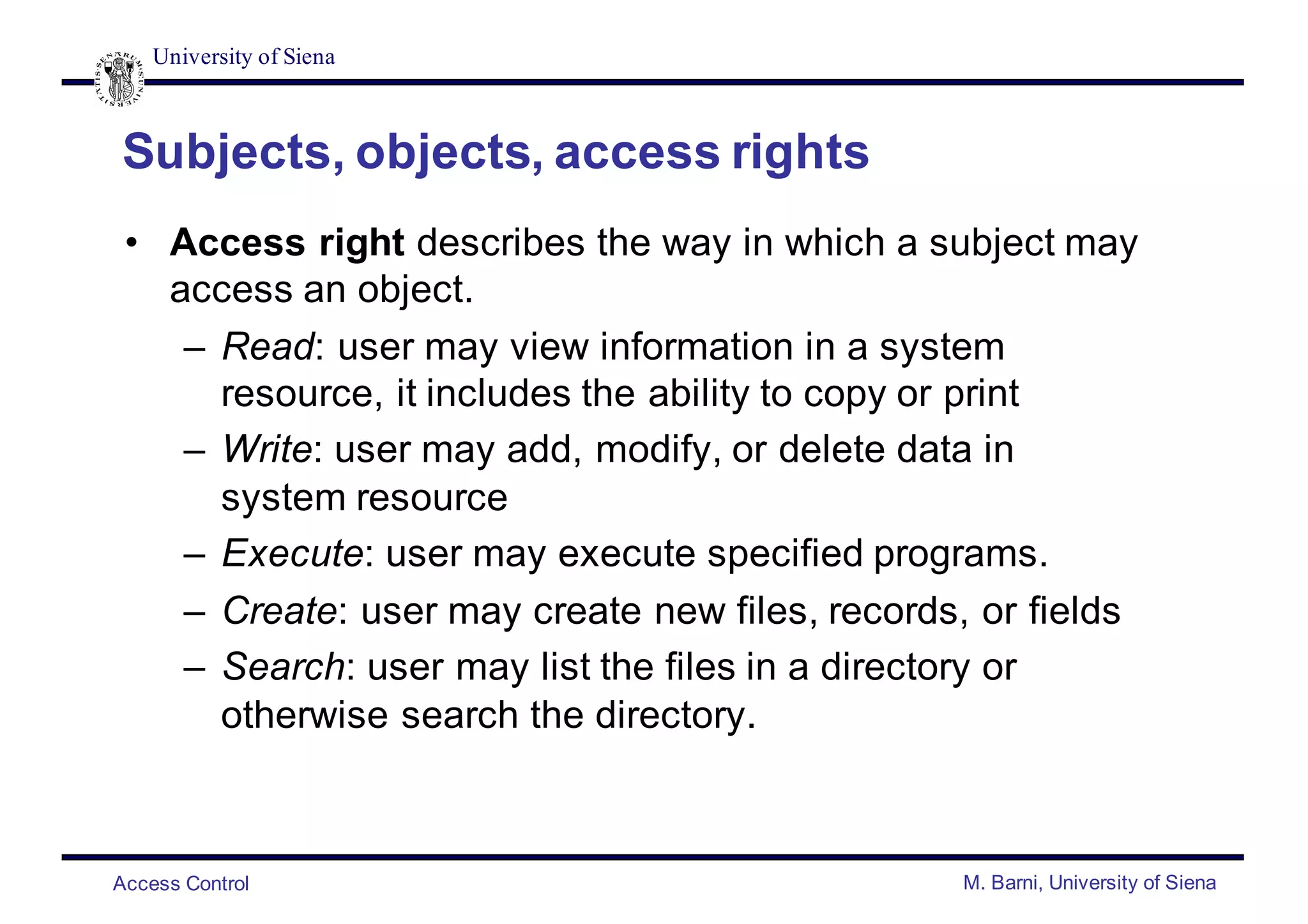
- DAC and MAC policies control access based on user identity and access rules or security labels/clearances. RBAC and ABAC control access based on user roles or attributes.
- ABAC provides a flexible approach that can implement other models as special





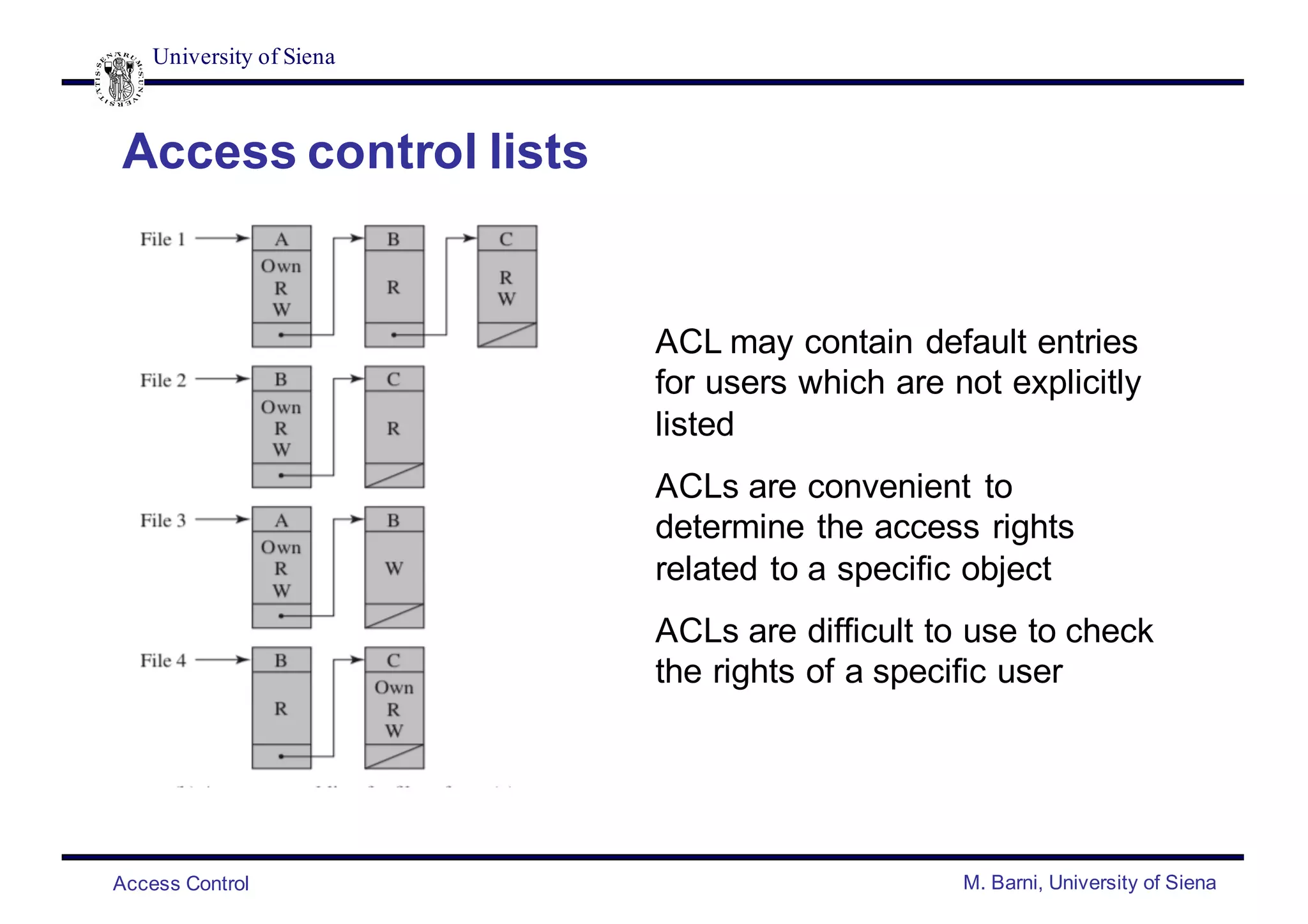
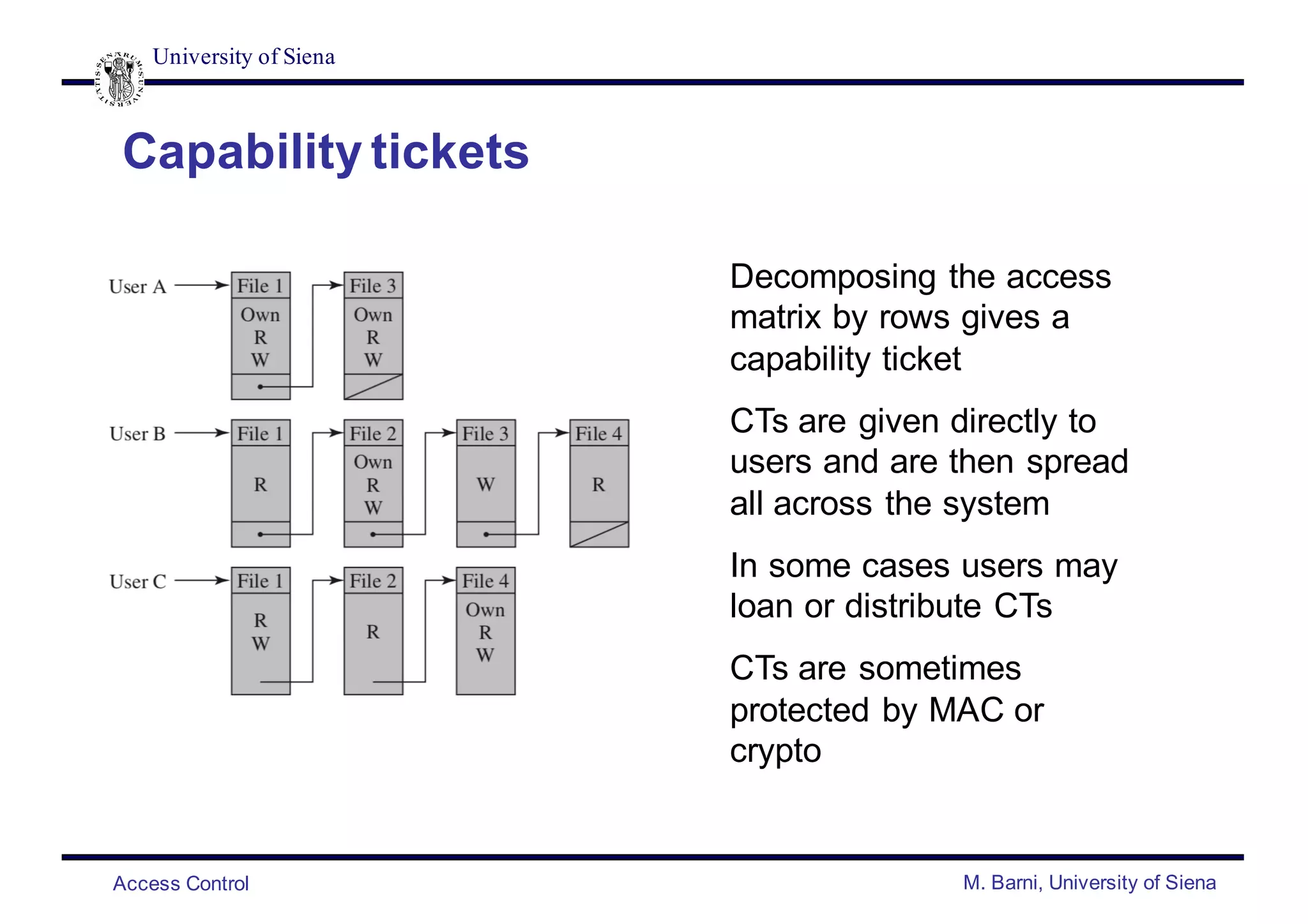
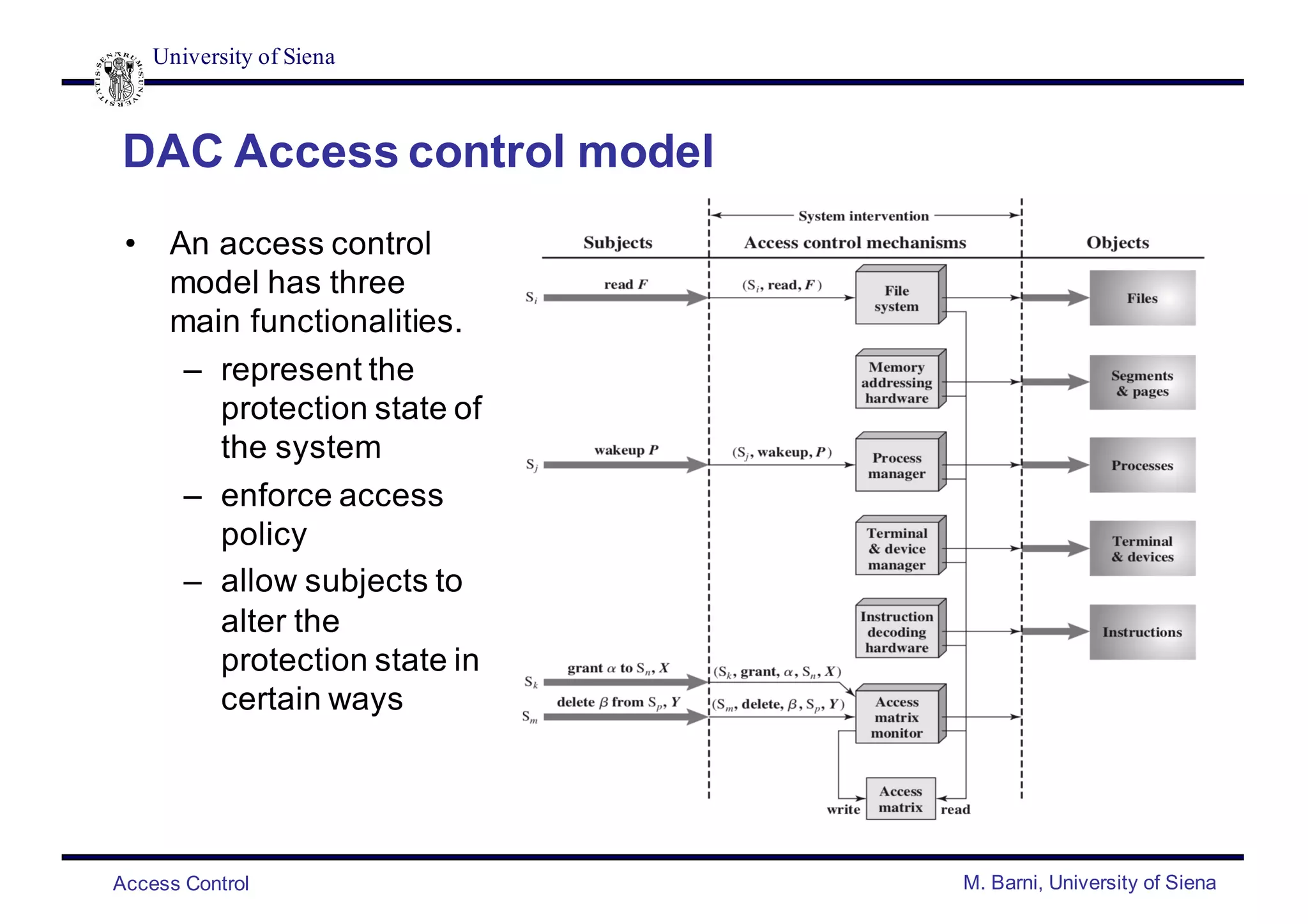
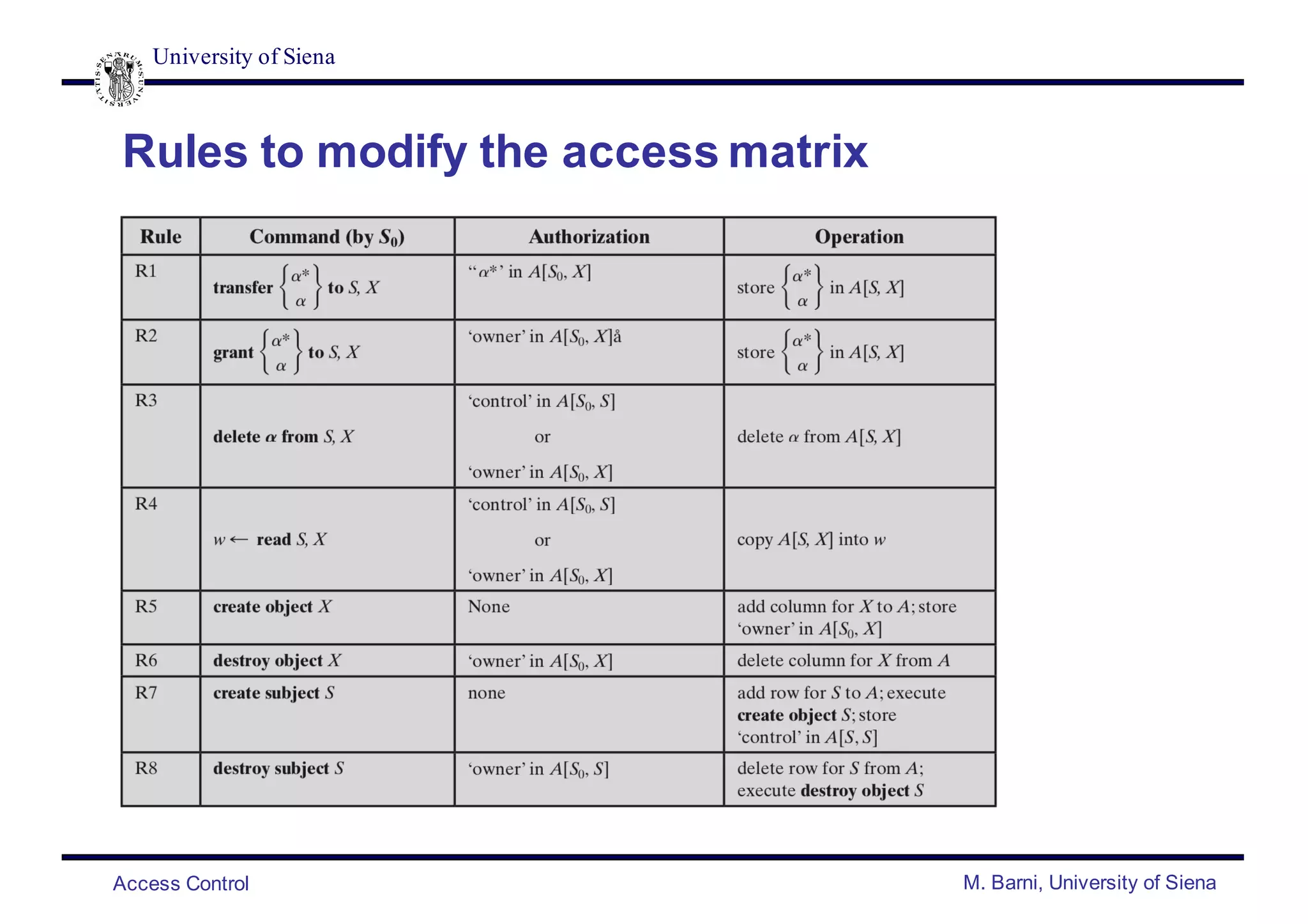

![University of Siena
Access Control M. Barni, University of Siena
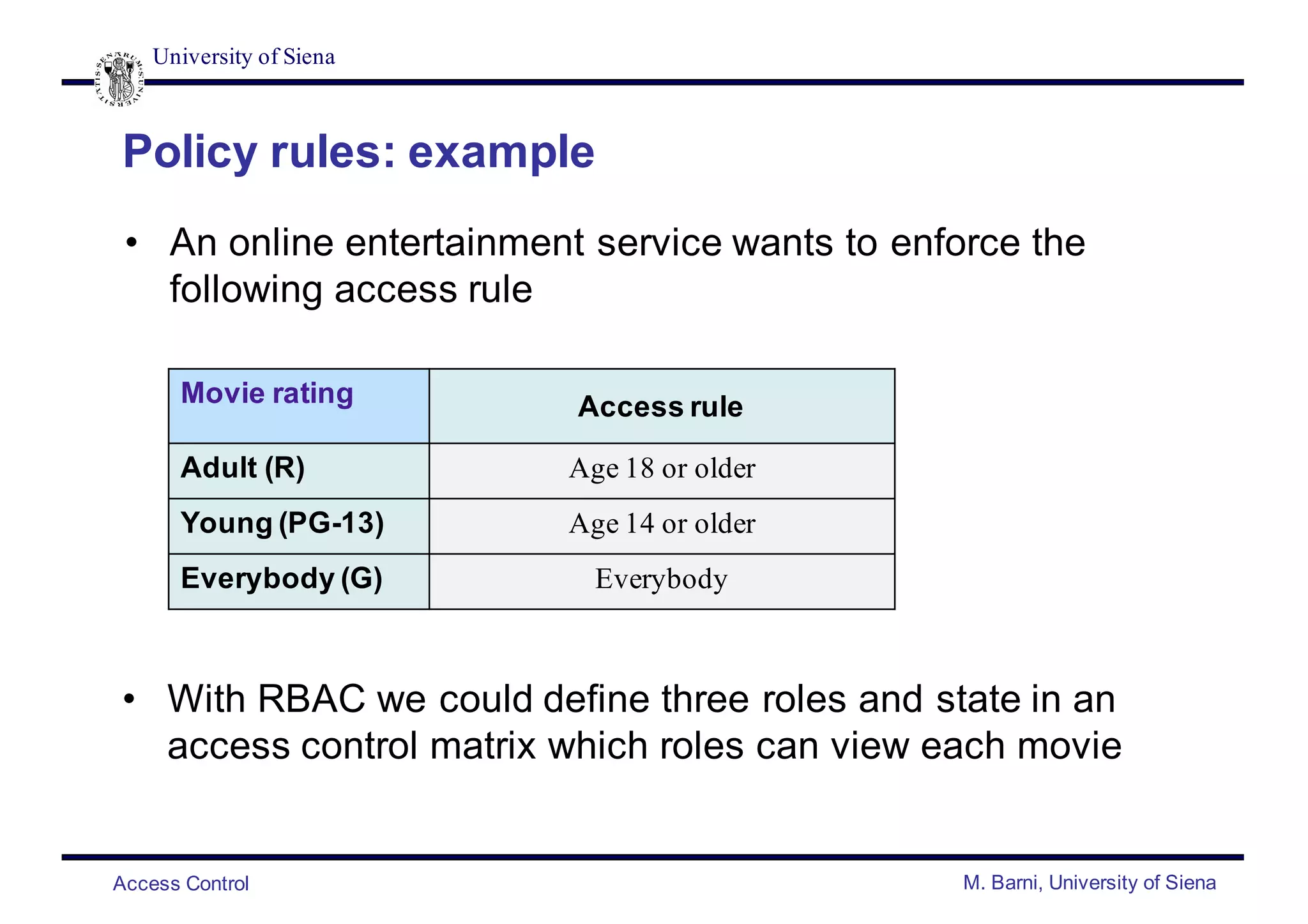
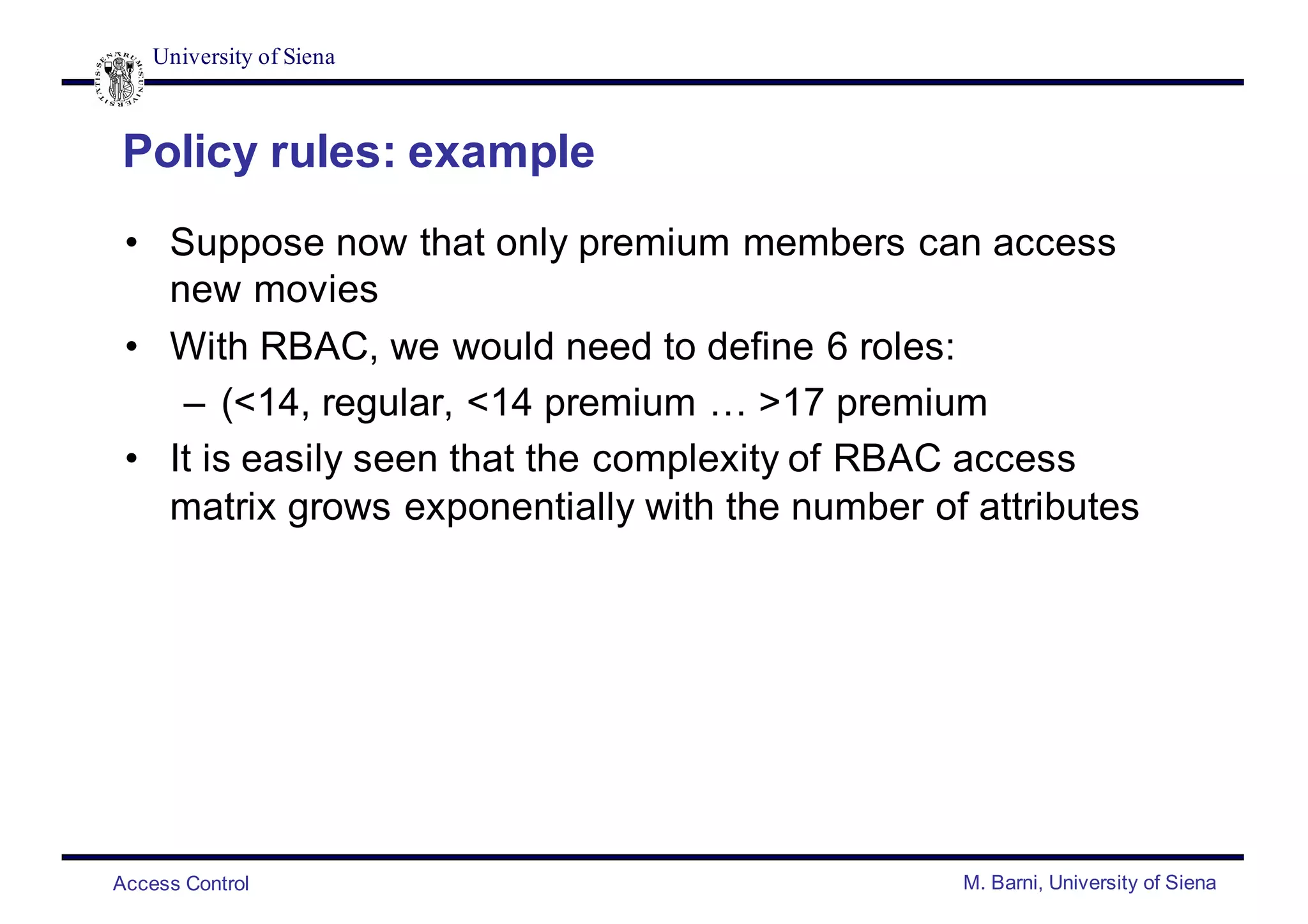
Policy rules: example
• With ABAC we can define the following attributes and
policy rule
Subject/
Object
Attributes Values
User Age [1-100]
Movie Rating {R, PG-13, G}](https://image.slidesharecdn.com/cybersecaccesscontrol-230226154833-38507ba1/75/CyberSec_AccessControl-pdf-20-2048.jpg)
![University of Siena
Access Control M. Barni, University of Siena
Policy rules: example
• With ABAC everything is much simpler
Subject/Object Attributes Values
User Age [1-100]
User Subscription {Regular, Premium}
Movie Release {New release, old release}
Movie Rating {R, PG-13, G}
• Think about a new rule according to which regular users can
access new movies in promotional periods](https://image.slidesharecdn.com/cybersecaccesscontrol-230226154833-38507ba1/75/CyberSec_AccessControl-pdf-22-2048.jpg)
