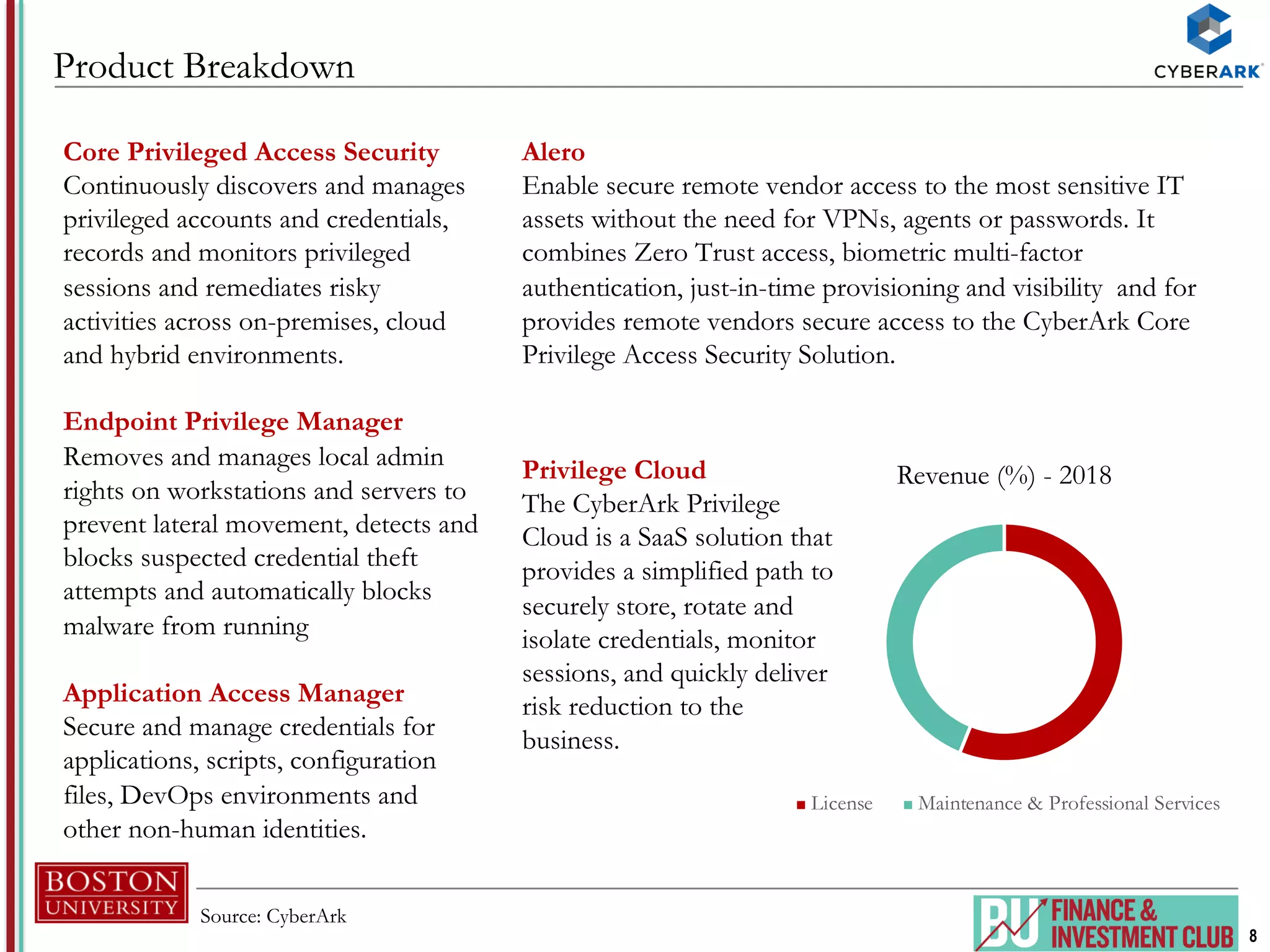
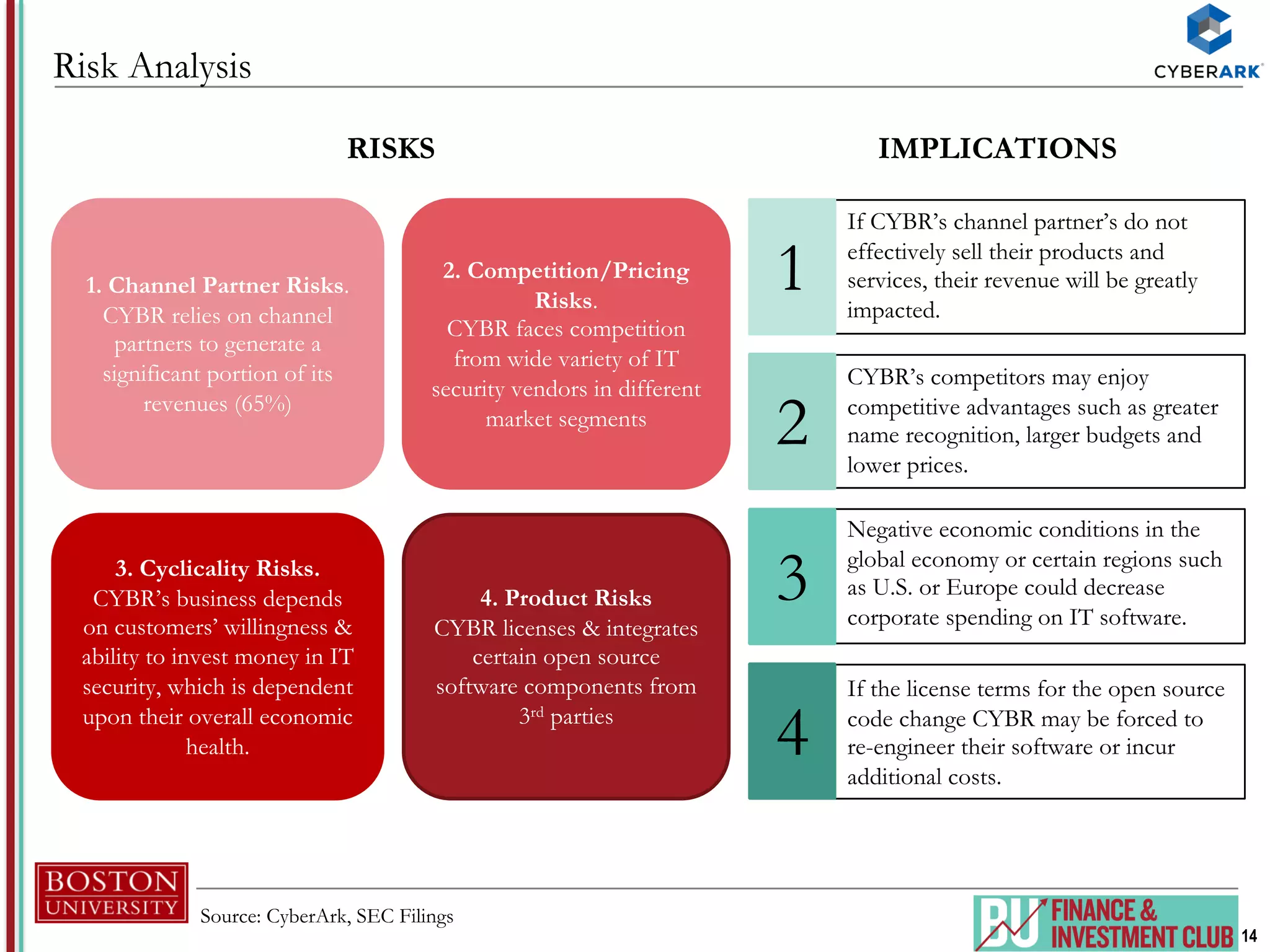
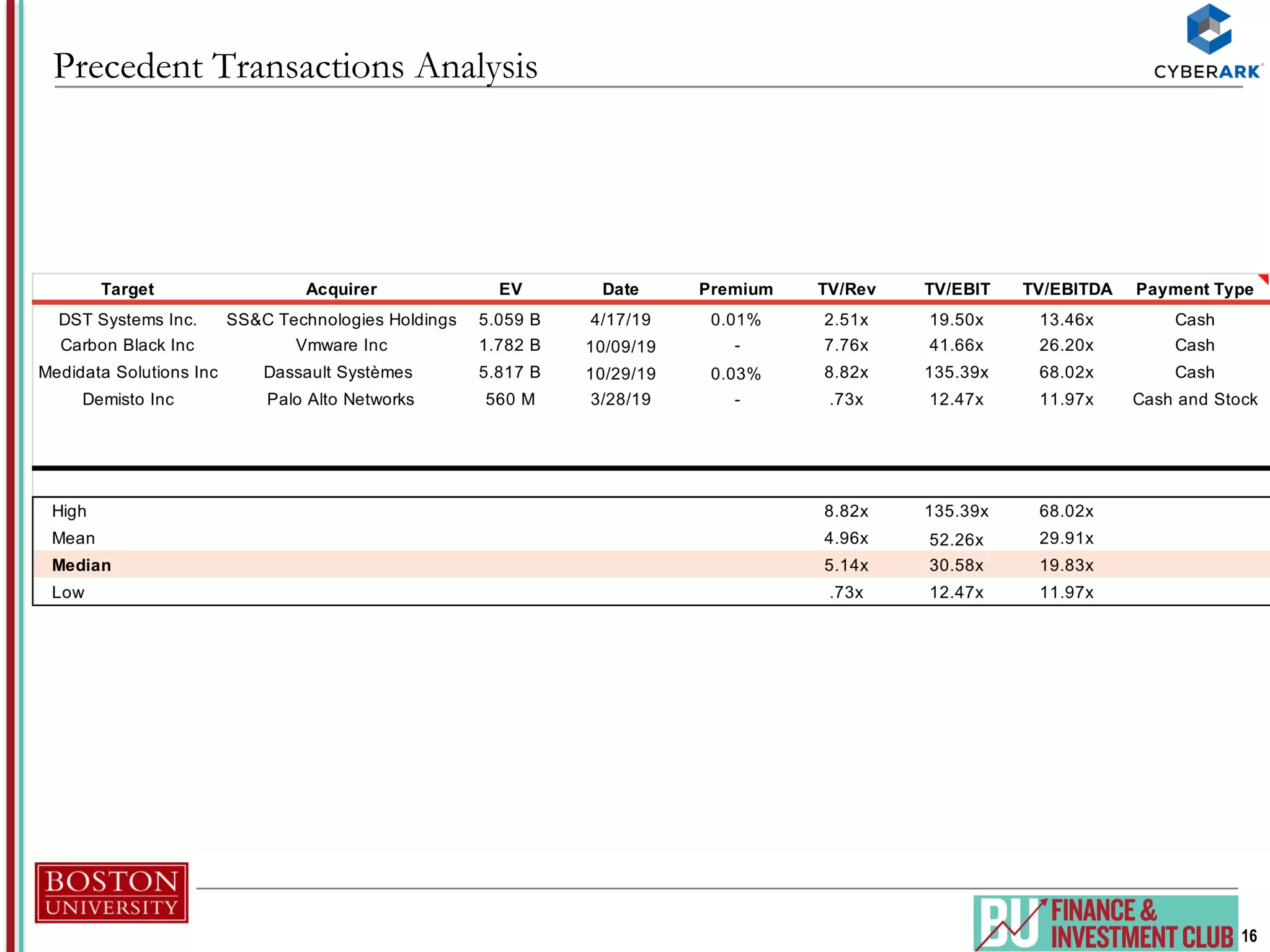
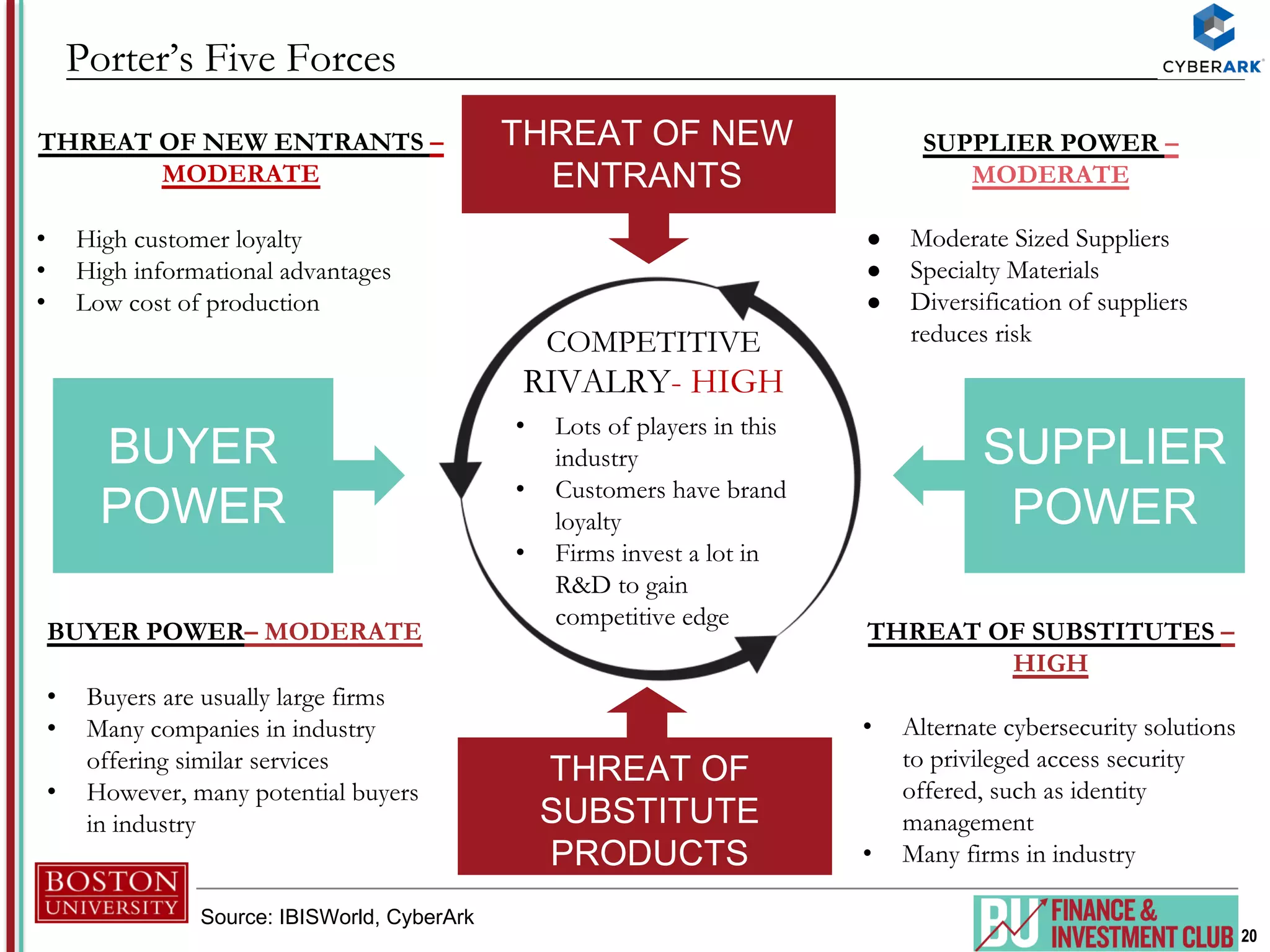
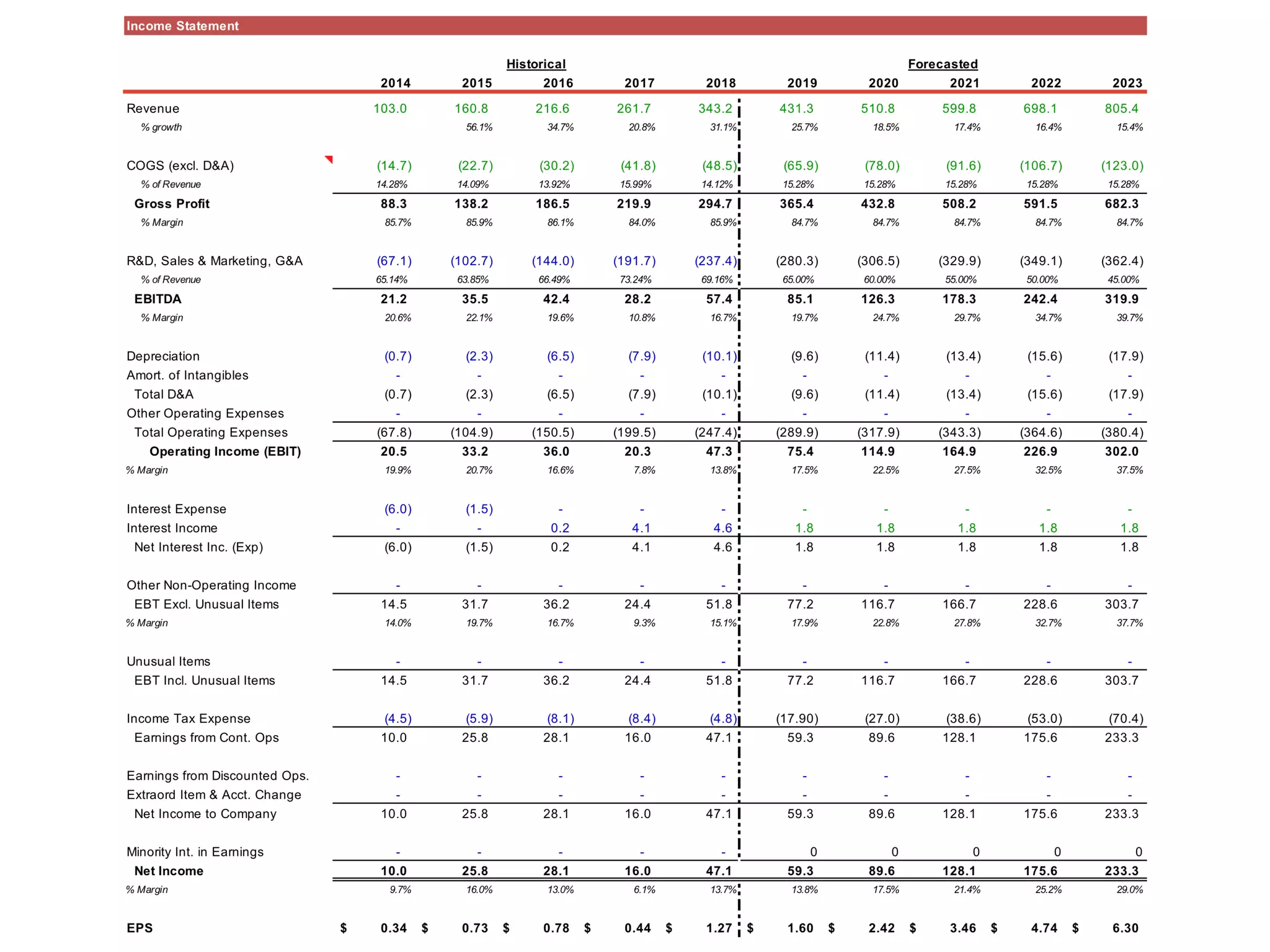
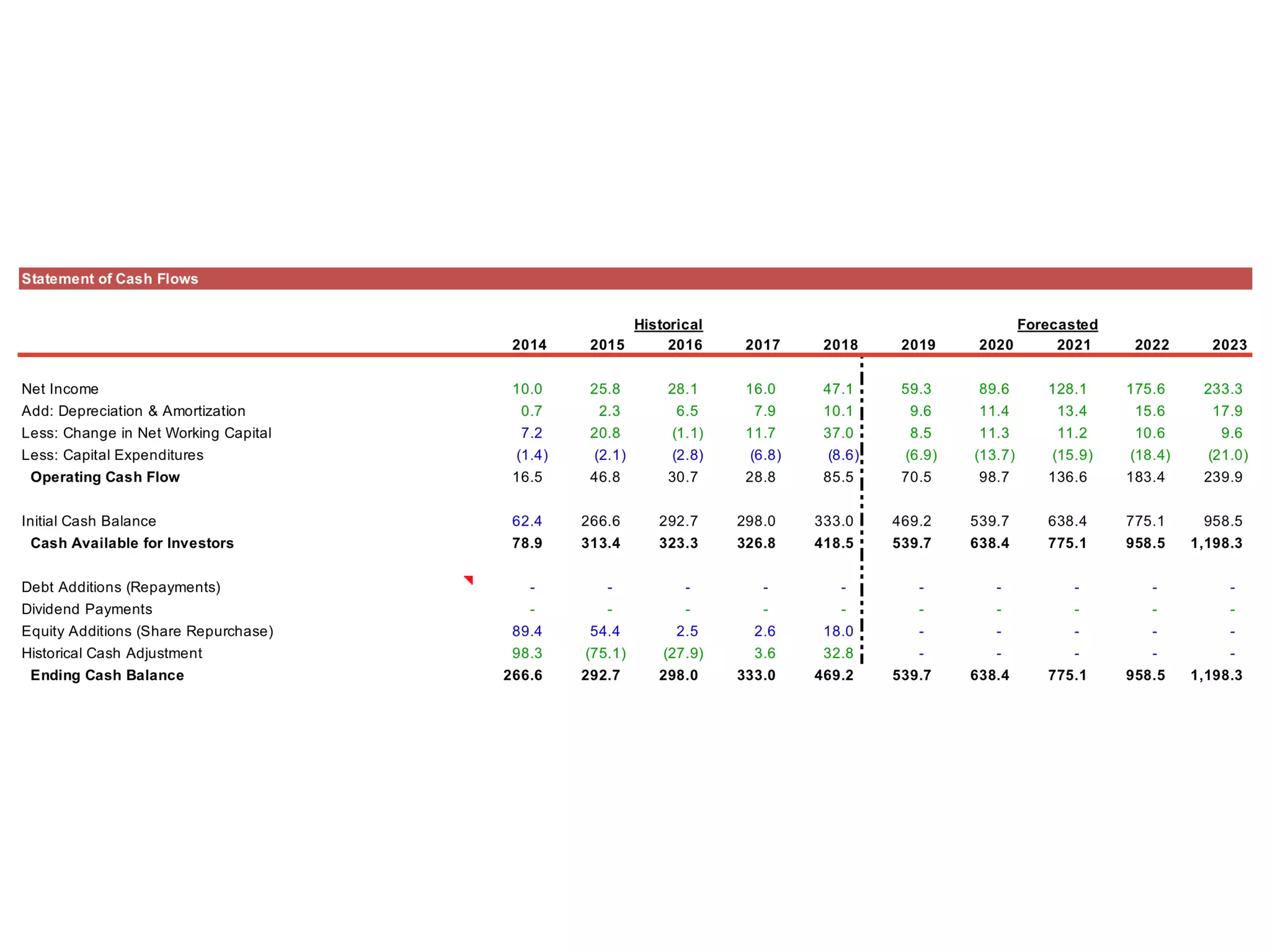
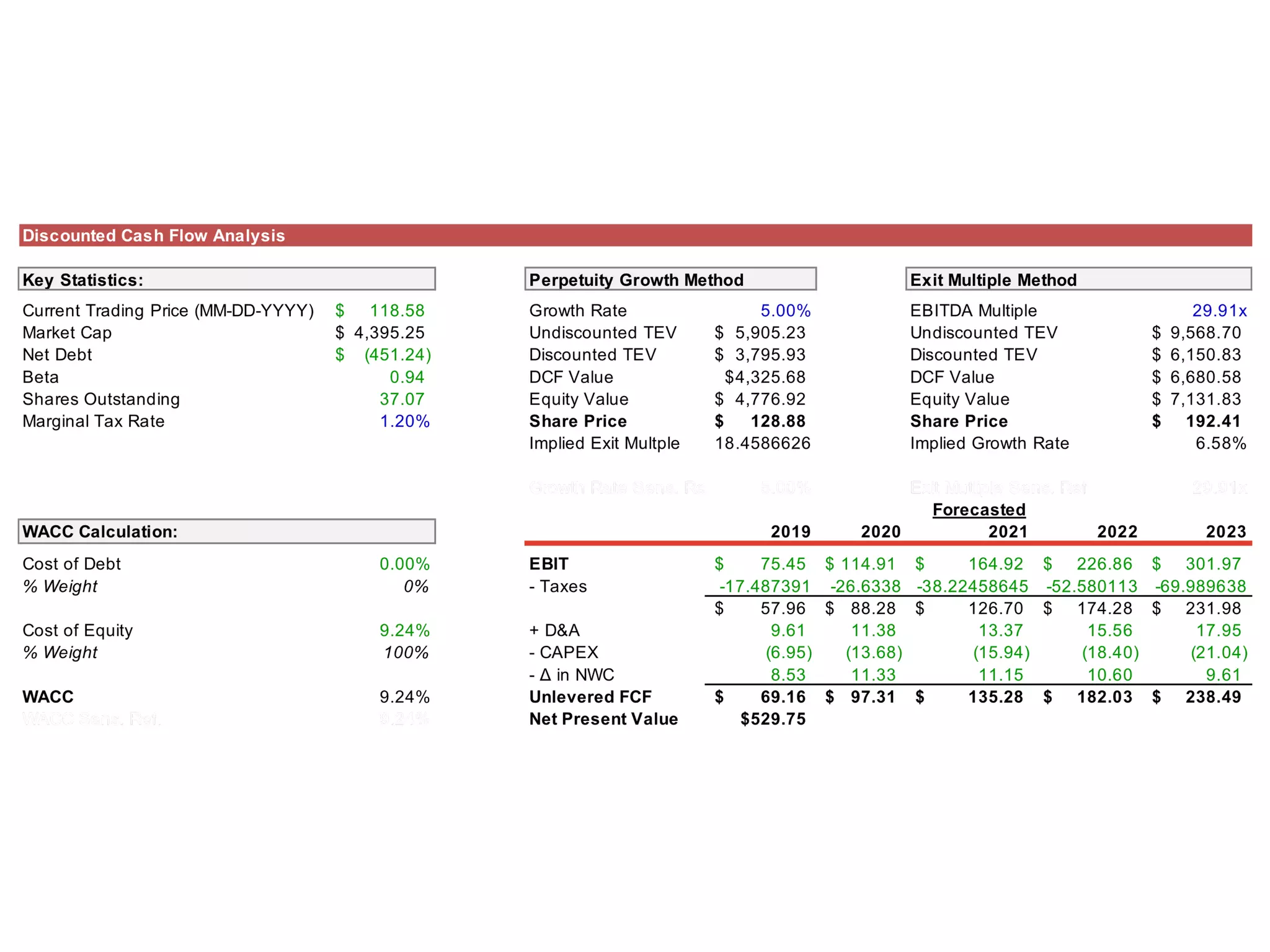
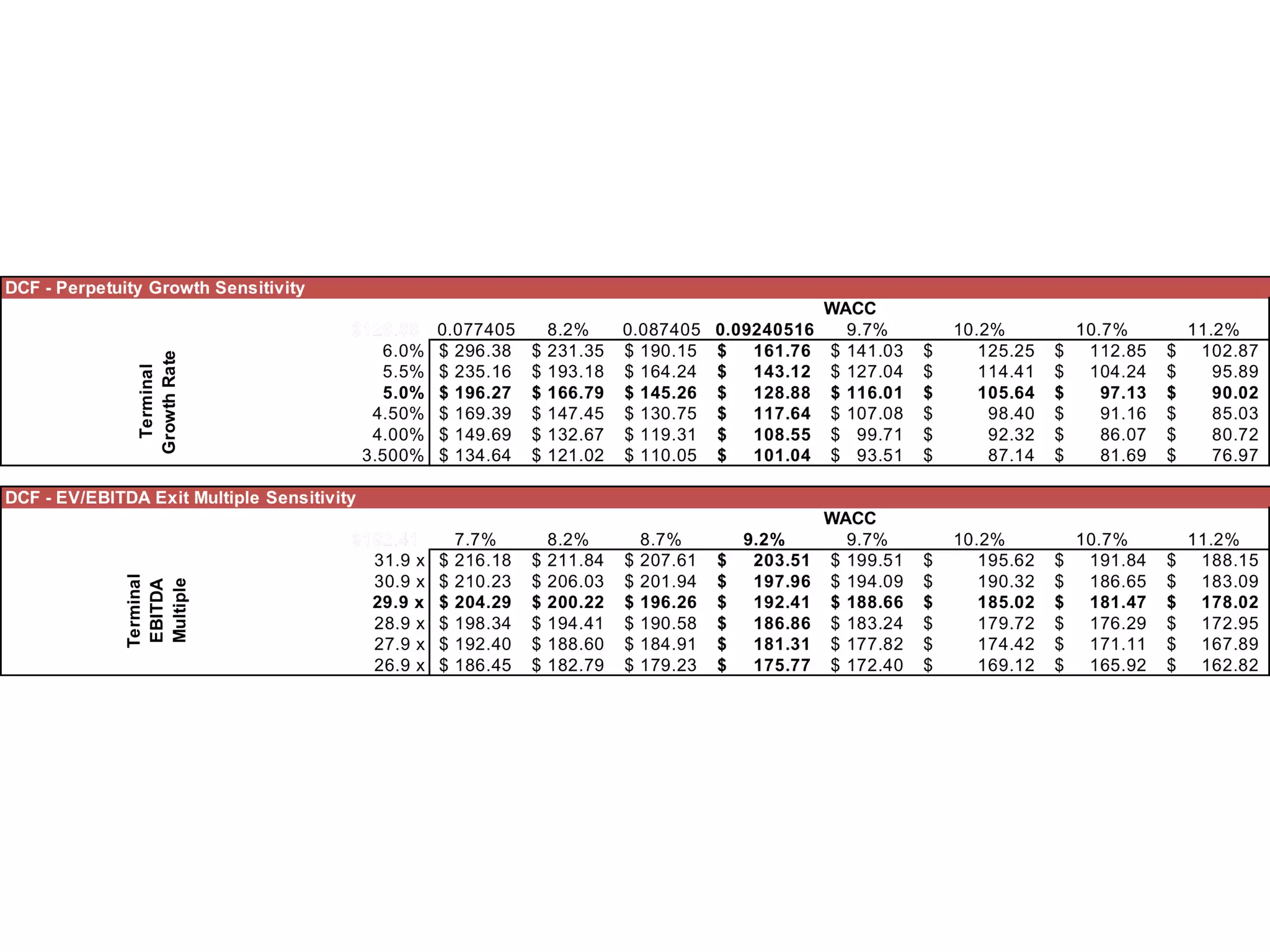
The document provides an analysis of CyberArk (ticker: CYBR), highlighting its position as a leader in privileged access security within the cybersecurity industry, with a recommendation to buy based on a target price of $151.11, indicating a 27.4% upside potential from the current trading price of $118.58. It outlines industry drivers such as the increase in cybercrime and rising corporate and government spending on cybersecurity, along with CyberArk's innovative products and strong customer base, comprising over 50% of Fortune 500 companies. Key risks include reliance on channel partners and competition within the industry, affecting revenue generation.