Embed presentation
Download to read offline




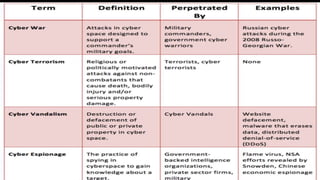
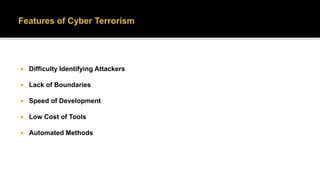
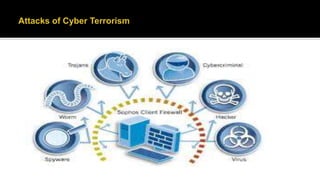

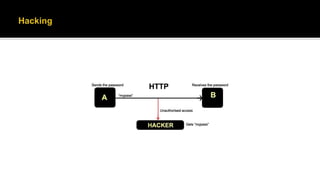
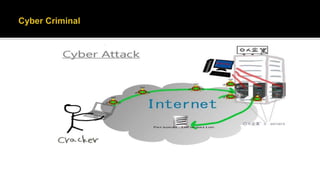






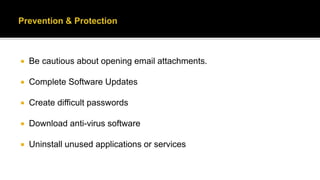


This document defines cyber terrorism and discusses attacks, effects, and protections. Cyber terrorism is defined as the premeditated use of disruptive activities against computers and networks to cause harm or further social, ideological, religious, political, or similar objectives. Cyber attacks are difficult to identify due to a lack of boundaries, speed of development, low cost of tools, and automated methods. Examples of cyber attacks include hacking systems, introducing viruses, website defacing, and denial-of-service attacks. Protections include being cautious of emails, keeping software updated, using strong passwords, using antivirus software, and uninstalling unused applications.



















