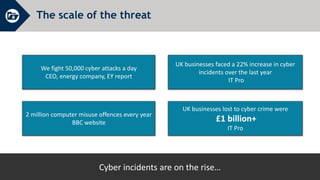
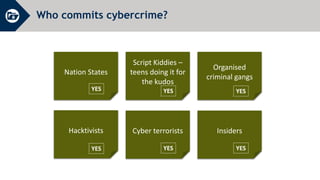
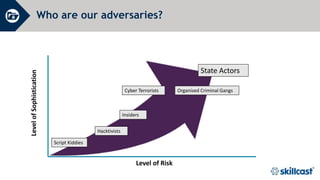
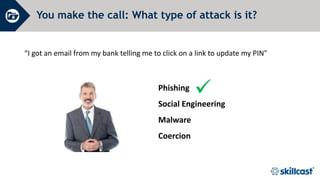
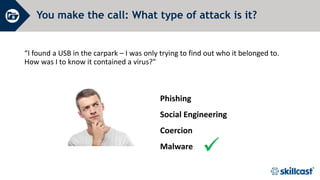
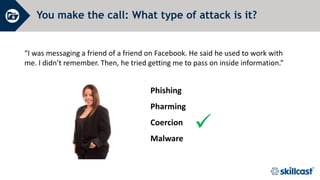
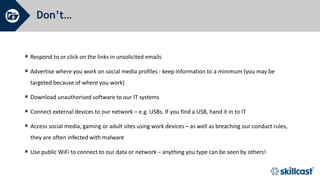
The document discusses essential cyber security training objectives, including understanding threats, identifying adversaries, and recognizing security incidents. It provides insights on the rise of cyber incidents, the motivations behind cybercrime, and various attack techniques used. The training emphasizes the importance of adhering to the company’s cyber security policy to mitigate risk and ensure data protection.
![Cyber Security
Training Presentation
[name] [date]](https://image.slidesharecdn.com/cyber-security-training-presentation-q320-240703135834-78c3c8f2/85/cyber-security-training-presentation-q320-ppt-1-320.jpg)










![Next steps
Call _____ on _____ if you need information or guidance
Call _____ on _____ if you need to raise concerns
Access self-study courses on our e-learning portal for further training [or
optionally – Complete your mandatory training on our corporate e-learning
portal]](https://image.slidesharecdn.com/cyber-security-training-presentation-q320-240703135834-78c3c8f2/85/cyber-security-training-presentation-q320-ppt-20-320.jpg)
