Embed presentation





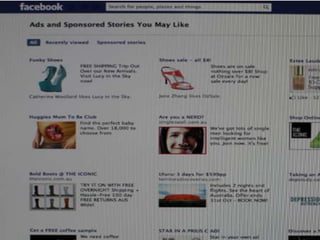



Cookies are small files stored on a user's computer that allow websites to personalize content for individual users based on their interests and provide targeted advertisements. While cookies can improve users' experiences by making websites load faster and be tailored to their preferences, they also enable user tracking and pose privacy risks if personal information is accessed without permission.









