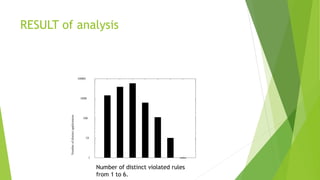
This document discusses cryptographic misuse in Android applications. It introduces Cryptolint, a tool that analyzes Android applications to detect typical cryptographic misuses. Cryptolint leverages the Androguard framework to extract control graphs from applications and check for violations of cryptographic best practices. The author analyzes over 11,000 Android applications and finds widespread cryptographic issues, with many applications improperly using static keys or non-random initialization vectors. Case studies of specific applications reveal real-world security vulnerabilities.