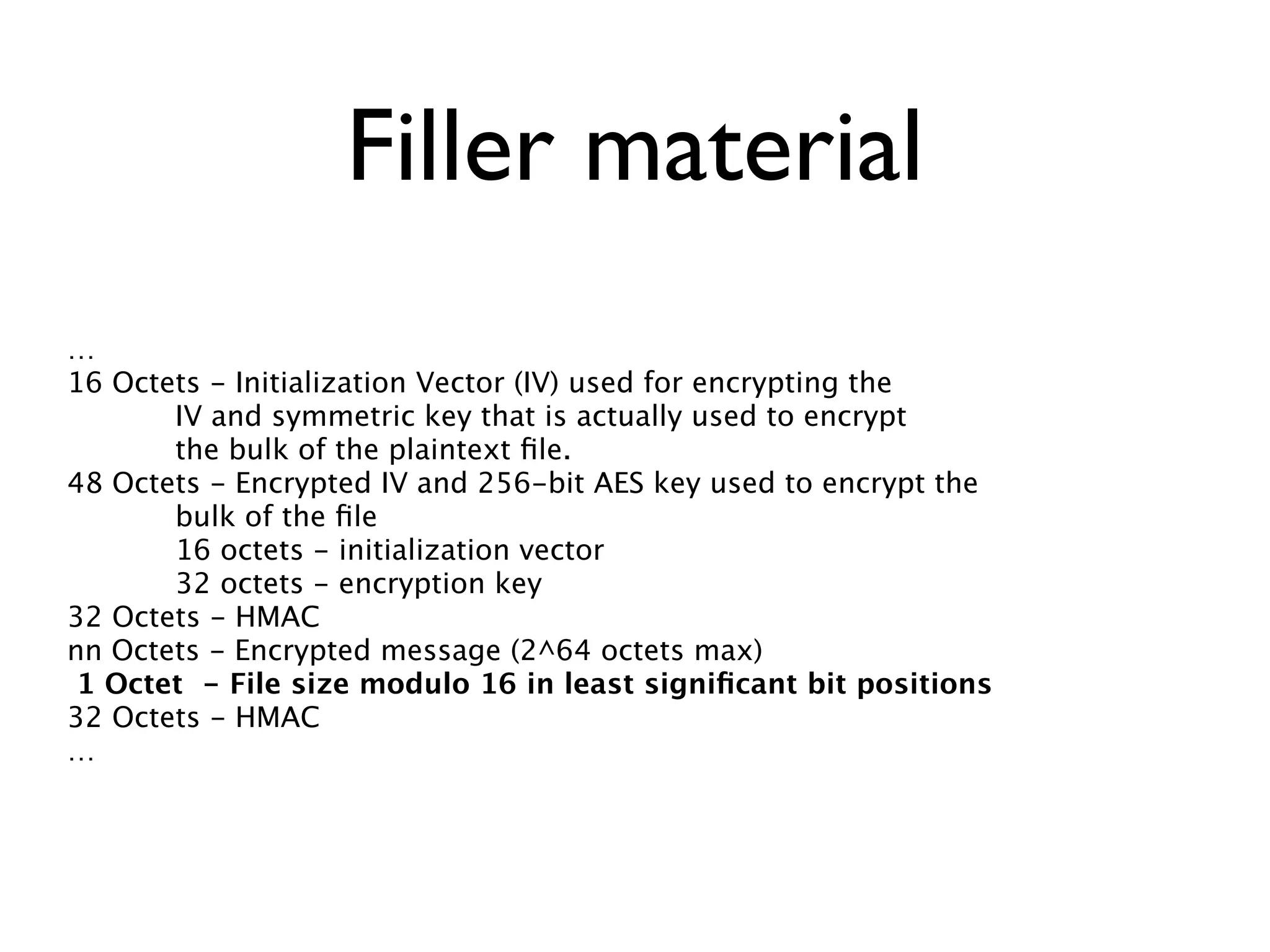
- The document discusses cryptographic storage for smartphone data, specifically the aescrypt format and software which allows encrypted storage of secret files on phones and across backups.
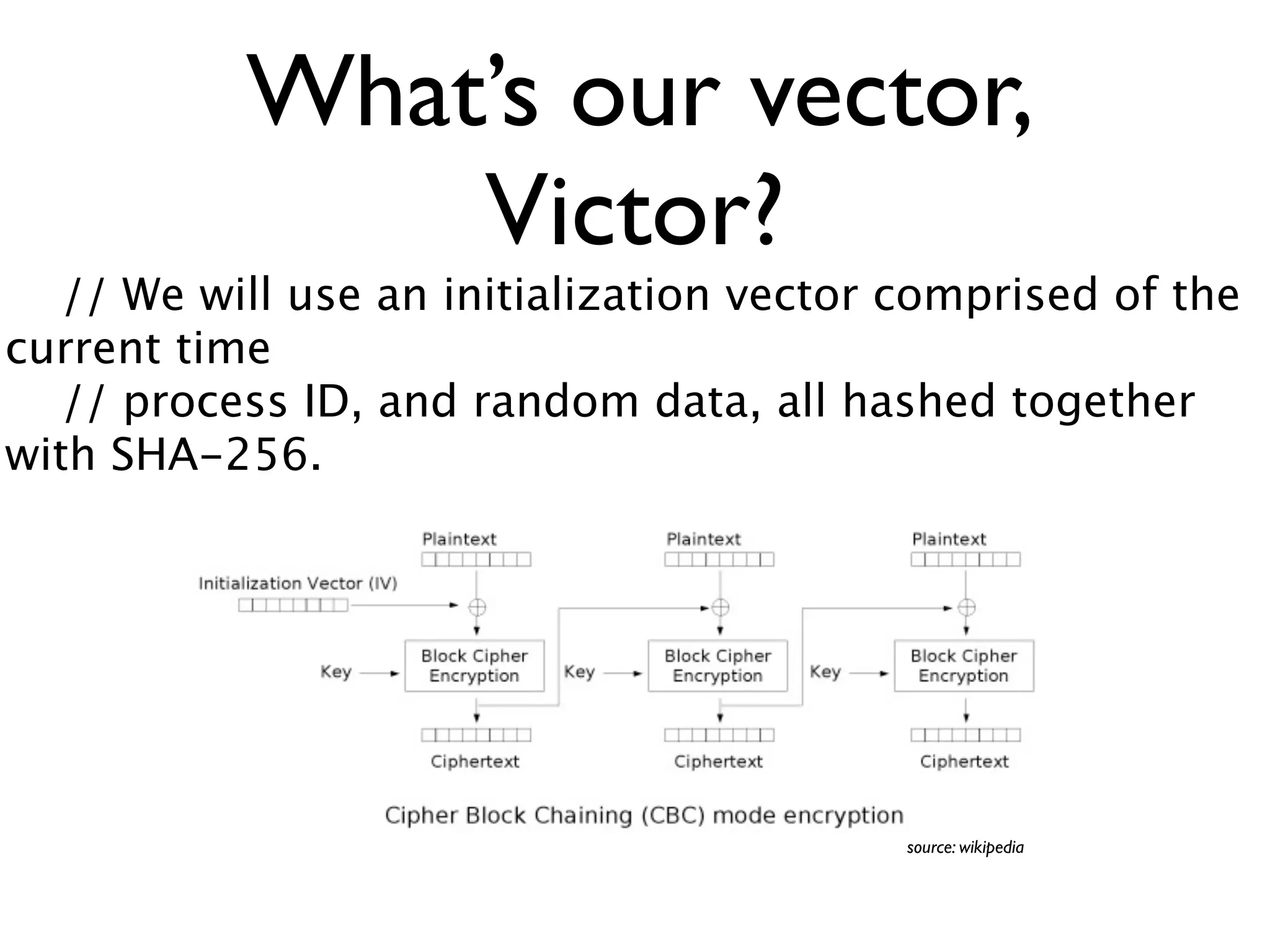
- Aescrypt uses a randomly generated initialization vector and password hashes to encrypt the bulk of files with AES-256, and includes metadata and integrity checks without revealing secret information.
- The key derived from hashing the password is used to encrypt an actual encryption key, to provide an additional layer of protection in case the derived key is compromised.




![Nut[the problem]shell](https://image.slidesharecdn.com/cryptostorage-110324085925-phpapp01/75/Crypto-storage-6-2048.jpg)
![Nut[the problem]shell
• Want to store data](https://image.slidesharecdn.com/cryptostorage-110324085925-phpapp01/75/Crypto-storage-7-2048.jpg)
![Nut[the problem]shell
• Want to store data
• But it must be secret](https://image.slidesharecdn.com/cryptostorage-110324085925-phpapp01/75/Crypto-storage-8-2048.jpg)
![Nut[the problem]shell
• Want to store data
• But it must be secret
• if the phone is stolen](https://image.slidesharecdn.com/cryptostorage-110324085925-phpapp01/75/Crypto-storage-9-2048.jpg)
![Nut[the problem]shell
• Want to store data
• But it must be secret
• if the phone is stolen
• if the iTunes backup is stolen](https://image.slidesharecdn.com/cryptostorage-110324085925-phpapp01/75/Crypto-storage-10-2048.jpg)
![Nut[the problem]shell
• Want to store data
• But it must be secret
• if the phone is stolen
• if the iTunes backup is stolen
• It must be tamper-proof](https://image.slidesharecdn.com/cryptostorage-110324085925-phpapp01/75/Crypto-storage-11-2048.jpg)
![Nut[the problem]shell
• Want to store data
• But it must be secret
• if the phone is stolen
• if the iTunes backup is stolen
• It must be tamper-proof
• …to some extent](https://image.slidesharecdn.com/cryptostorage-110324085925-phpapp01/75/Crypto-storage-12-2048.jpg)