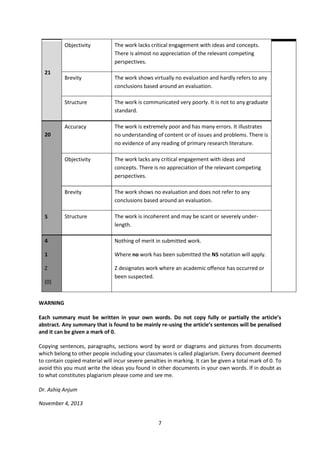
This document outlines a distributed systems assignment for students to design, implement, and monitor a private cloud. It consists of 5 tasks: 1) designing a private cloud architecture, 2) implementing the private cloud, 3) monitoring the private cloud, 4) developing a Facebook-like application to deploy on the private cloud, and 5) submitting a critical review of the design and implementation. Students will work in groups of about 4 but be individually assessed. The assignment aims to develop skills in distributed systems and providing feedback to improve expertise in designing robust and scalable distributed architectures.